-
Notifications
You must be signed in to change notification settings - Fork 2
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Added support for changing master password
- Loading branch information
Showing
30 changed files
with
737 additions
and
73 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
|
|
@@ -858,6 +858,8 @@ Commands: | |
| create-user | ||
|
|
||
| update-user | ||
|
|
||
| change-user-password | ||
|
|
||
| delete-user | ||
|
|
||
|
|
@@ -1019,9 +1021,11 @@ You can update your user profile using CLI as follows: | |
|
|
||
| You can update your user profile using REST APIs as follows: | ||
| ```bash | ||
| ./target/release/plexpass -j true --master-username charlie | ||
| --master-password *** --name "Charles" --email "[email protected]" | ||
| curl -k https://localhost:8443/api/v1/users/me | ||
| --header "Content-Type: application/json; charset=UTF-8" | ||
| --header "Authorization: Bearer $AUTH_TOKEN" -d '{"user_id"...}' | ||
| ``` | ||
|
|
||
| #### 11.5.3 Docker CLI | ||
|
|
||
| You can update your user profile using docker CLI as follows: | ||
|
|
@@ -1040,6 +1044,38 @@ You can also update your user profile using web UI as displayed in following scr | |
| The UI allows you to view/edit user profile, manage security-keys for multi-factor authentication and generate API tokens: | ||
| 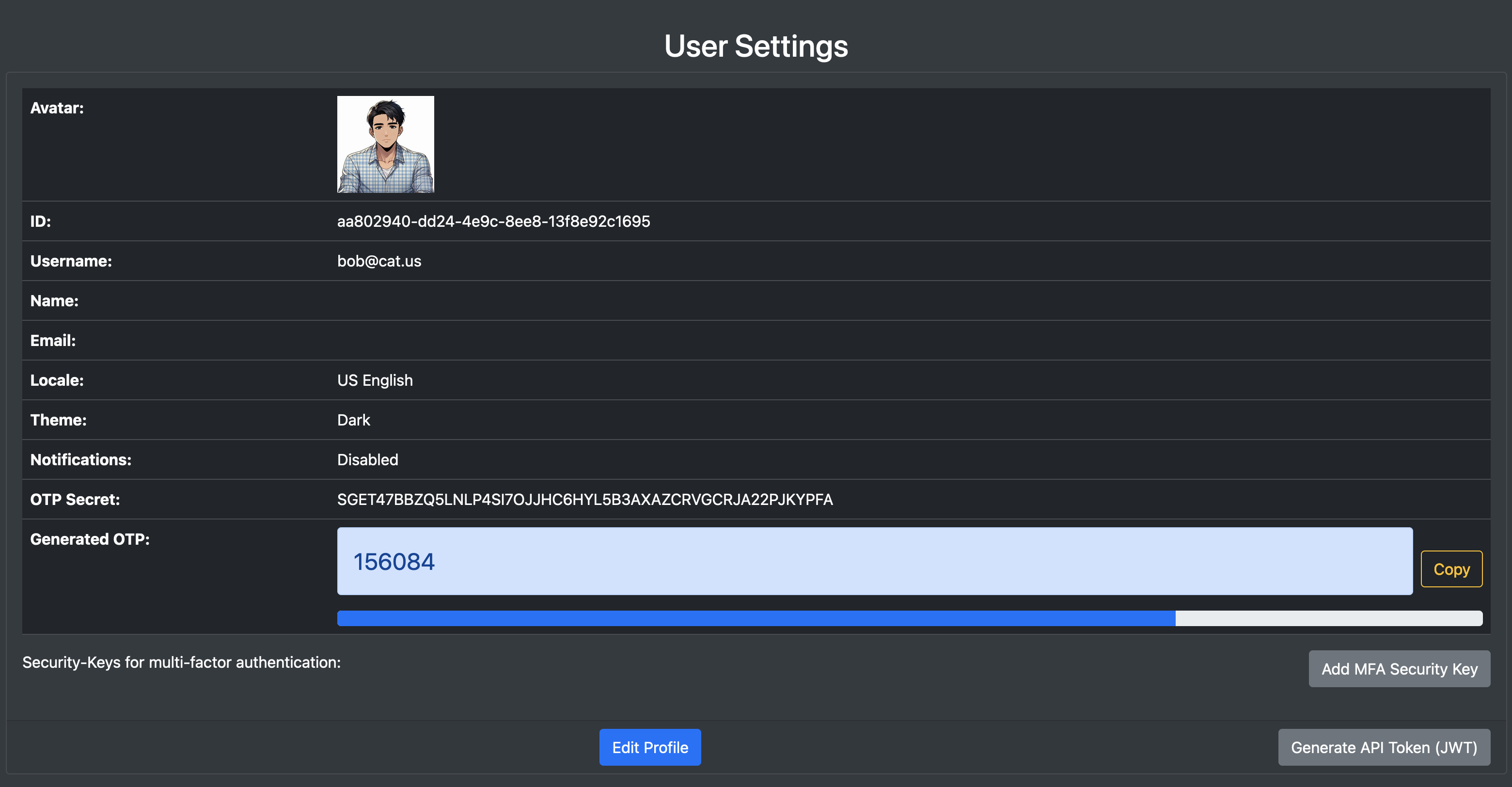 | ||
|
|
||
| ### 11.5b Update User Password | ||
|
|
||
| #### 11.5b.1 Command Line | ||
|
|
||
| You can update your user password using CLI as follows: | ||
| ```bash | ||
| ./target/release/plexpass -j true --master-username [email protected] --master-password ** \ | ||
| change-user-password --new-password ** --confirm-new-password ** | ||
| ``` | ||
| #### 11.5b.2 REST API | ||
|
|
||
| You can update your user password using REST APIs as follows: | ||
| ```bash | ||
| curl -k https://localhost:8443/api/v1/users/me | ||
| --header "Content-Type: application/json; charset=UTF-8" | ||
| --header "Authorization: Bearer $AUTH_TOKEN" -d '{"old_password": "*", "new_password": "*", "confirm_new_password": "*"}' | ||
| ``` | ||
| #### 11.5b.3 Docker CLI | ||
|
|
||
| You can update your user profile using docker CLI as follows: | ||
| ```bash | ||
| docker run -e DEVICE_PEPPER_KEY=$DEVICE_PEPPER_KEY | ||
| -e DATA_DIR=/data -v $PARENT_DIR/PlexPassData:/data | ||
| -j true --master-username [email protected] --master-password ** \ | ||
| change-user-password --new-password ** --confirm-new-password ** | ||
| ``` | ||
|
|
||
| #### 11.5b.4 Web UI | ||
|
|
||
| You can also update your user password from user settings using web UI as displayed in following screenshot: | ||
| 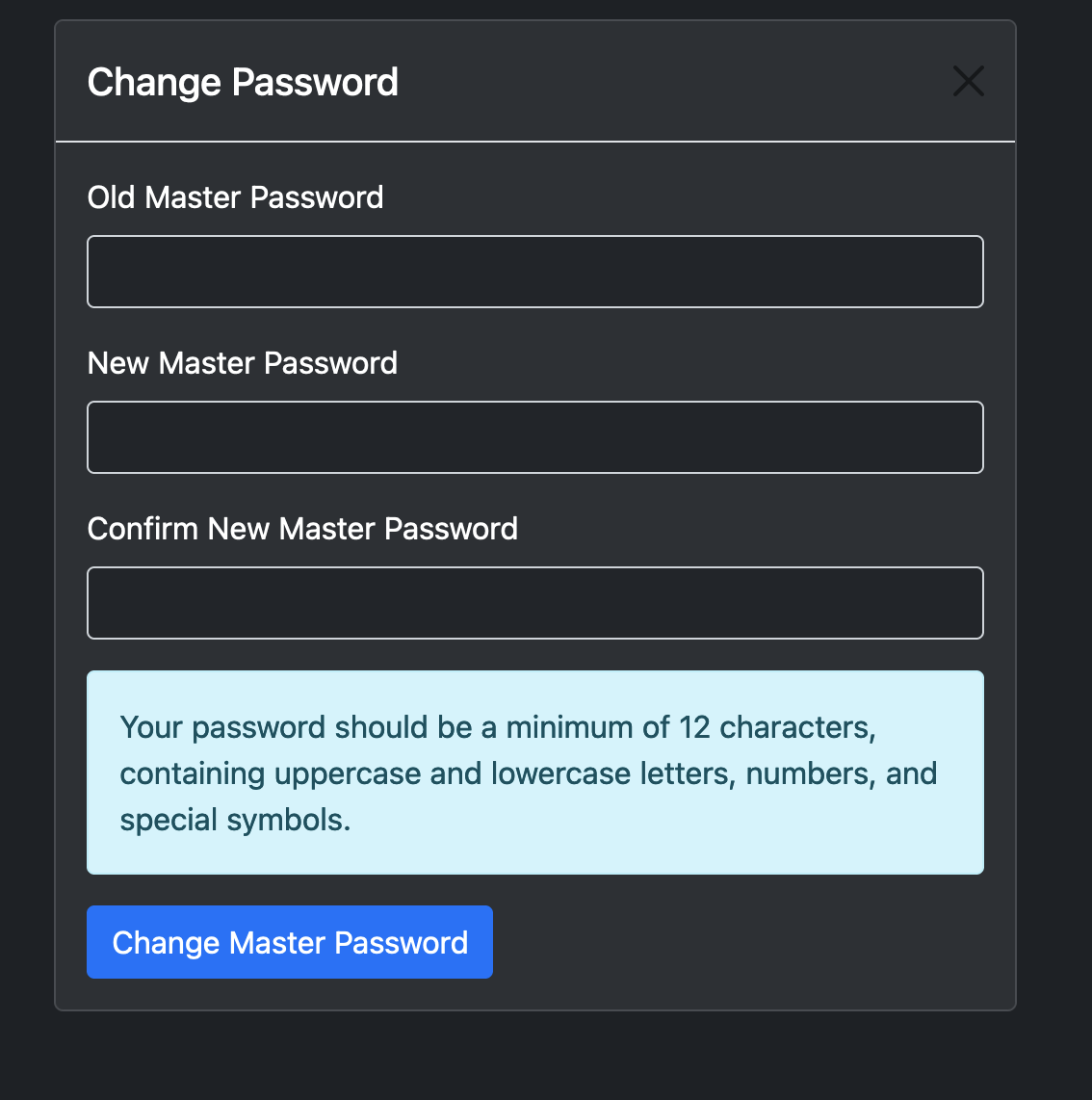 | ||
|
|
||
| ### 11.6 Creating Vaults | ||
|
|
||
| PlexPass automatically creates a few Vaults upon registration but you can create additional vaults as follows: | ||
|
|
||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
|
|
@@ -20,6 +20,14 @@ def test_00_signin_without_signup(self): | |
| resp = requests.post(SERVER + '/api/v1/auth/signin', json = data, headers = headers, verify = False) | ||
| self.assertTrue(resp.status_code == 200 or resp.status_code == 401) # should throw 401 if user doesn't exist | ||
|
|
||
| def test_00_signup_george(self): | ||
| headers = { | ||
| 'Content-Type': 'application/json', | ||
| } | ||
| data = {'username': '[email protected]', 'master_password': '[email protected]$Goat551'} | ||
| resp = requests.post(SERVER + '/api/v1/auth/signup', json = data, headers = headers, verify = False) | ||
| self.assertTrue(resp.status_code == 200 or resp.status_code == 409) | ||
|
|
||
| def test_01_signup_alice(self): | ||
| headers = { | ||
| 'Content-Type': 'application/json', | ||
|
|
@@ -66,7 +74,7 @@ def test_05_update_user(self): | |
| 'Authorization': 'Bearer ' + JWT_TOKEN, | ||
| } | ||
|
|
||
| data = {'user_id':USER_ID, 'version':VERSION, 'username': '[email protected]', 'name': 'Bill', 'email': 'bill@nowhere', 'icon': 'stuff'} | ||
| data = {'user_id':USER_ID, 'version':VERSION, 'username': '[email protected]', 'name': 'Bill', 'email': 'bill@nowhere'} | ||
| resp = requests.put(SERVER + '/api/v1/users/' + USER_ID, json = data, headers = headers, verify = False) | ||
| self.assertEqual(200, resp.status_code) | ||
|
|
||
|
|
@@ -89,5 +97,40 @@ def test_07_get_user_without_token(self): | |
| resp = requests.get(SERVER + '/api/v1/users/' + USER_ID, headers = headers, verify = False) | ||
| self.assertEqual(401, resp.status_code) | ||
|
|
||
| def test_08_signin_george(self): | ||
| global USER_ID | ||
| global JWT_TOKEN | ||
| headers = { | ||
| 'Content-Type': 'application/json', | ||
| } | ||
| data = {'username': '[email protected]', 'master_password': '[email protected]$Goat551'} | ||
| resp = requests.post(SERVER + '/api/v1/auth/signin', json = data, headers = headers, verify = False) | ||
| self.assertEqual(200, resp.status_code) | ||
| USER_ID = json.loads(resp.text)['user_id'] | ||
| JWT_TOKEN = resp.headers.get('access_token') | ||
|
|
||
| def test_09_change_password(self): | ||
| headers = { | ||
| 'Content-Type': 'application/json', | ||
| 'Authorization': 'Bearer ' + JWT_TOKEN, | ||
| } | ||
|
|
||
| data = {'old_password': '[email protected]$Goat551', 'new_password': '[email protected]$Goat5511', 'confirm_new_password': '[email protected]$Goat5511'} | ||
| resp = requests.put(SERVER + '/api/v1/users/' + USER_ID + '/change_password', json = data, headers = headers, verify = False) | ||
| self.assertEqual(200, resp.status_code) | ||
|
|
||
| def test_10_signin_george_with_new_password(self): | ||
| global USER_ID | ||
| global JWT_TOKEN | ||
| headers = { | ||
| 'Content-Type': 'application/json', | ||
| } | ||
| data = {'username': '[email protected]', 'master_password': '[email protected]$Goat5511'} | ||
| resp = requests.post(SERVER + '/api/v1/auth/signin', json = data, headers = headers, verify = False) | ||
| self.assertEqual(200, resp.status_code) | ||
| USER_ID = json.loads(resp.text)['user_id'] | ||
| JWT_TOKEN = resp.headers.get('access_token') | ||
|
|
||
|
|
||
| if __name__ == '__main__': | ||
| unittest.main() | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Oops, something went wrong.