-
Notifications
You must be signed in to change notification settings - Fork 3
/
Copy pathconcat.js
155 lines (136 loc) · 785 KB
/
concat.js
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
const en = [{"id":436,"question":"What is the octal representation of a hexadecimal fraction F1B0.C?","answer_label":"170660.6","answer_id":5984},{"id":437,"question":"When two unbiased coins are tossed and an unbiased six-sided die is rolled at the same time, what is the probability that at least one coin shows heads and the die shows an even number?","answer_label":"3/8","answer_id":5989},{"id":438,"question":"Which of the following expressions in postfix notation is equivalent to an expression 2+5×3+4 in infix notation? Here, the operator ‘×’ has higher precedence than ‘+’.","answer_label":"2 5 3 × + 4 +","answer_id":5995},{"id":439,"question":"Analog audio data is being sampled and converted to 8-bit digital audio data using the PCM method, then transmitted in 64,000 bits per second. What is the sampling interval in microseconds?","answer_label":"125","answer_id":5998},{"id":440,"question":"When Bubble sort algorithm is used, how many exchange operations are required to sort the following numbers in ascending order? 9, 2, 13, 21, 3, 0","answer_label":"9","answer_id":6002},{"id":441,"question":"There are two boxes; the first box contains two green balls and three red balls; the second box contains three green balls and two red balls. A boy randomly selects a box from the two, and then randomly picks a ball from that box. If the ball is red, what is the probability that he selected the first box?","answer_label":"3/20","answer_id":6004},{"id":442,"question":"Which of the following is an appropriate explanation of symmetric multiprocessing (SMP)?","answer_label":"Several CPU cores have schedules for their own tasks, with priorities set by the\noperating system with equal access to the memory and system resources.","answer_id":6010},{"id":443,"question":"To determine an effective address from the value recorded in the address part of instruction, various addressing modes are used. Which of the following modes uses the value of the address part as an effective address?","answer_label":"Absolute addressing","answer_id":6012},{"id":444,"question":"Which of the following is a memory device that stores programs or data in factories, and only has the read operation for the stored programs or data?","answer_label":"Mask ROM","answer_id":6018},{"id":445,"question":"Which of the following is an appropriate role of a device driver?","answer_label":"It directly controls the hardware according to requests from an application program.","answer_id":6021},{"id":446,"question":"Which of the following is the RAID level that can recover data from the other disks, with a minimum of two-disk configuration?","answer_label":"RAID 1","answer_id":5941},{"id":447,"question":"There exists a system composed of two processing devices. What is the difference in availability between the system that works when either of the devices functions normally and the one when both devices function normally? Here, the availability for both devices is 0.9, and factors other than the processing devices can be ignored.","answer_label":"0.18","answer_id":5934},{"id":448,"question":"Which of the following is an appropriate characteristic of a web system implemented in a three-layer client/server system configuration?","answer_label":"A business process is executed on the server side, and the client software displays the\nresult on a screen according to the HTML coding.","answer_id":5924},{"id":449,"question":"In input/output management, which of the following is an appropriate function of a buffer?","answer_label":"Reducing the difference in processing speed by establishing a special area of memory\nbetween an input/output device and a processing device","answer_id":5931},{"id":450,"question":"Which of the following is the backup method that requires the longest time to backup but the shortest time to restore?","answer_label":"Full backup","answer_id":5937},{"id":451,"question":"In UNIX, which of the following is a function that links the standard output of a command directly to the standard input of another command?","answer_label":"Pipe","answer_id":5946},{"id":452,"question":"Which of the following is an appropriate explanation of optimization in a compiler?","answer_label":"Analyzing the source code and generating an object code with an improved run-time\nprocessing efficiency","answer_id":5960},{"id":453,"question":"Which of the following is a logic gate combination that provides an output 1 when both inputs are 0?","answer_label":"NOR or XNOR","answer_id":5966},{"id":454,"question":"Which of the following uses a flip-flop circuit in a memory cell?","answer_label":"SRAM","answer_id":5971},{"id":455,"question":"Which of the following is used to control the visual styles of HTML documents, such as text sizes, text colors, or page layout?","answer_label":"CSS","answer_id":5973},{"id":456,"question":"In a DBMS, which of the following functions decides the schema?","answer_label":"Definition function","answer_id":5976},{"id":457,"question":"The attributes of the relation “OrderRecord” have the functional dependency (1) to (6) below. Normalization is performed with these functional dependencies up to the third normal form, and the decomposition into the relations “Product,” “Customer,” “Order,” and “OrderDetails” are performed. Which of the following is appropriate for the relation “OrderDetails”? Here, {X, Y} represents a combination of the attributes X and Y, and X → Y represents that X functionally determines Y. The solid underline represents a primary key.\n\n OrderRecord (OrderNumber, OrderDate, CustomerNumber, CustomerName,\n ProductNumber, ProductName, Quantity, UnitSalesPrice)\n\n[Functional dependency]\n (1) OrderNumber, → OrderDate\n (2) OrderNumber, → CustomerNumber\n (3) CustomerNumber → CustomerName\n (4) {OrderNumber, ProductNumber} → Quantity\n (5) {OrderNumber, ProductNumber} → UnitSalesPrice\n (6) ProductNumber → ProductName","answer_label":"OrderDetails (OrderNumber, ProductNumber, Quantity, UnitSalesPrice)","answer_id":5983},{"id":458,"question":"Which of the following is an appropriate description of the mapping between the relational model and relational database as its implementation?","answer_label":"A relation is mapped to a table.","answer_id":5957},{"id":459,"question":"When a storage location is to be calculated from a key value, which of the following methods enables the same calculation result to be obtained from different key values?","answer_label":"Hash index","answer_id":5954},{"id":460,"question":"Which of the following can change the deadlock state of the transaction back to the normal state?","answer_label":"Rollback","answer_id":5950},{"id":461,"question":"Which of the following is located at layer 3 of the OSI basic reference model, and performs path selection and packet relay for an end-to-end communication?","answer_label":"Network layer","answer_id":5921},{"id":462,"question":"When a PC connected to a LAN is starting up, which of the following protocols is used to automatically assign an IP address to the PC?","answer_label":"DHCP","answer_id":5916},{"id":463,"question":"Which of the following describes an IPv6 feature not existing in IPv4?","answer_label":"128-bit addressing is introduced for the IP address space.","answer_id":5912},{"id":464,"question":"In TCP/IP network, which of the following is a combination of information that identifies a TCP connection?","answer_label":"IP address, Port number","answer_id":5909},{"id":465,"question":"Which of the following is a form of malware that requires a host in order to propagate from one computer to another?","answer_label":"Viruses","answer_id":5905},{"id":469,"question":"Which of the following is an appropriate terminology concerning the behavior that documents retrieved from distinct origins are isolated from each other?","answer_label":"Same-Origin Policy","answer_id":5903},{"id":470,"question":"When a mirror port is prepared to allow a LAN analyzer to be used to investigate the cause of a network failure, which of the following is a point to consider?","answer_label":"Since the LAN analyzer can display the packets that pass through the network, it is\nnecessary to pay attention to misuse or abuse such as wiretapping.","answer_id":5898},{"id":471,"question":"Which of the following is an appropriate term for an organized and highly skilled team, whose mission is to continuously monitor and improve the organization’s security posture while preventing, detecting, analyzing, and responding to cyber security incidents with the aid of both technology and well-defined processes and procedures?","answer_label":"Security Operations Center (SOC)","answer_id":5895},{"id":472,"question":"Which of the following is the most appropriate description of polymorphism in object oriented design?","answer_label":"It is the provision of a single interface to entities of different types.","answer_id":5891},{"id":473,"question":"In the development process, which of the following is an activity that should be performed in software architectural design?","answer_label":"Transforming the requirements for the software item into an architecture that describes\nits top-level structure and identifies the software components","answer_id":5887},{"id":474,"question":"Which of the following is the most appropriate description of stack-trace in relation to debugging a program?","answer_label":"A trace of call stack methods/functions/subroutines","answer_id":5880},{"id":475,"question":"Which of the following is an appropriate description concerning a state transition test in a system integration test?","answer_label":"A method that checks whether a system behaves according to the designed combinations\nof events and internal states.","answer_id":5877},{"id":476,"question":"Which of the following is a method for analyzing a source and object codes, and extract program specifications and design information?","answer_label":"Reverse engineering","answer_id":5875},{"id":477,"question":"According to the ISO/IEC 12207 (Systems and software engineering – Software life cycle processes (SLCP)), the Software Implementation Process has the following lower-level processes:\n\n 1) Construction Process\n 2) Requirements Analysis Process\n 3) Architectural and Detailed Design Process\n 4) Integration and Testing process\n\nWhich of the following is an appropriate order for the Software Implementation Process?","answer_label":"2) -> 3) -> 1) -> 4)","answer_id":5869},{"id":478,"question":"According to PMBOK, which of the following processes is included in the Executing Process Group?","answer_label":"Process of auditing the quality requirements and the results from quality control\nmeasurements to ensure that appropriate quality, standards and operational definitions\nare properly implemented","answer_id":5864},{"id":479,"question":"Which of the following is an appropriate description of “Lead” relationship in project time management?","answer_label":"It is the amount of time by which a successor activity can be advanced with respect to a\npredecessor activity.","answer_id":5860},{"id":480,"question":"Company A is going to launch a new software product and the sales team then has to demonstrate it to the customers. There is a risk that the sales team does not understand the product and cannot provide good demonstrations. As a consequence, the sales team will make fewer sales and there will be less revenue for the company. So, the management decided to provide good training for the sales team. Which of the following is the best method to manage the risk?","answer_label":"Risk mitigation","answer_id":5858},{"id":481,"question":"Which of the following is an appropriate purpose of using a Work Breakdown Structure (WBS) in a software development project?","answer_label":"To decompose a development task into smaller sub-tasks of a manageable size, and\norganize them into a hierarchical structure","answer_id":5853},{"id":482,"question":"Which of the following device is used for protecting power supply circuits, communication devices, or other equipment from the overvoltage and the over current generated from the overvoltage?","answer_label":"SPD","answer_id":5850},{"id":483,"question":"Which of the following is an appropriate precaution to be observed when monitoring the use of the capacity and performance of an online system in the capacity management process of IT service management?","answer_label":"Multiple measurement items such as the response time and CPU utilization are\nmonitored on a regular basis.","answer_id":5845},{"id":484,"question":"According to ITIL, which of the following is a description of a virtual service desk among the characteristics of a service desk organization?","answer_label":"By using communication technology, services can be provided from a single service\ndesk as observed by the user, even if the service desk staff members are distributed\nacross multiple regions.","answer_id":5796},{"id":485,"question":"In an information security audit, which of the following is a check item for confirming availability?","answer_label":"Interruption duration to be managed so that the standard of the SLA specifying the\ninterruption duration can be satisfied","answer_id":5841},{"id":486,"question":"Which of the following situation is judged as appropriate when conducting an audit on a Business Continuity Plan (BCP)?","answer_label":"An emergency contact list of employees is created and updated to the latest version.","answer_id":5837},{"id":487,"question":"Which of the following is an explanation of Enterprise Architecture (EA)?","answer_label":"It is a technique to analyze each business operation and information system through the\nfour (4) systems of business, data, application, and technology and reexamine it from the\nviewpoint of total optimization.","answer_id":5833},{"id":488,"question":"Which of the following is an explanation of a project organization?","answer_label":"It is formed only for a certain period of time to solve a given problem, and it is dissolved\nwhen the problem is solved.","answer_id":5830},{"id":489,"question":"Which of the following is a purpose of Business Process Management (BPM) in corporate activities?","answer_label":"Continuous improvement of business processes","answer_id":5826},{"id":490,"question":"Which of the following descriptions corresponds to the CSR procurement?","answer_label":"Indicating procurement standards that consider the environment, human rights, etc., and\nrequesting suppliers to comply with these","answer_id":5822},{"id":491,"question":"The RFP is presented to each vendor that has responded to an RFI. Which of the following should be done beforehand to proceed fairly with the future vendor selection processes?","answer_label":"Establishing processes of selection such as setting evaluation standards or weighting\nrules of conformity to the request items.","answer_id":5817},{"id":492,"question":"Which of the following is a marketing technique used to provide incentives for distributors by applying conditions such as kickbacks and rebates, and increase the demands of consumers?","answer_label":"Push strategy","answer_id":5814},{"id":493,"question":"The sales price of products is decided according to the different sales price setting methods.\nWhich of the following approaches sets a high sales price by using the consumer psychology that high quality equals to high price?","answer_label":"Prestige pricing","answer_id":5811},{"id":494,"question":"Which of the following is an appropriate explanation of the technology S-curve?","answer_label":"It represents the process of technology progress. It shows that technology advances\nslowly at the beginning and then advances rapidly; thereafter, its progress gently\nbecomes stagnant.","answer_id":5806},{"id":495,"question":"Which of the following is an example of Consumer Generated Media (CGM)?","answer_label":"A website such as a blog and SNS, etc. through which an individual transmits\ninformation to the general public about the evaluation of products, etc. that he/she has\nused","answer_id":5803},{"id":496,"question":"Which of the following indicates a price setting method based on the cost plus approach?","answer_label":"Deciding the price by incorporating the desired margin with reference to the\nmanufacturing cost and business expenses","answer_id":5793},{"id":497,"question":"To secure transparency of business administration, which of the following is a concept that supervises and monitors a company ’ s activities from the perspective of questions such as for whom the company runs its business, what the structure of the top management is like, and whether the organization has self-improvement capabilities?","answer_label":"Corporate governance","answer_id":5789},{"id":498,"question":"Which of the following items should be put under “Liabilities and Stockholder’s Equity” in a balance sheet?","answer_label":"Common stock","answer_id":5785},{"id":499,"question":"Which of the following type of financial statements shows the financial position of an enterprise at a particular point of time?","answer_label":"Balance sheet","answer_id":5780},{"id":500,"question":"Which of the following is the role of a CIO?","answer_label":"To make a computerization strategy from a corporate level perspective, and confirm and\nevaluate its consistency with business strategy","answer_id":5777},{"id":501,"question":"For logical variables p and q, which of the following is a logical expressions that evaluates to true for any values of p and q?\n","answer_label":"b","answer_id":5595},{"id":502,"question":"What is the Hamming distance of bit strings 10101 and 11110?","answer_label":"3","answer_id":5592},{"id":503,"question":"A candy box contains four flavors of candies: 6 lemon-flavored, 12 strawberry-flavored, 8 orange-flavored, and 4 grape-flavored. When a candy is randomly chosen from the box, what is the probability that it is either lemon- or orange-flavored?","answer_label":"7/15","answer_id":5587},{"id":504,"question":"A vehicle travels along a circle in the figure below. Two sensors L and R are attached to the left and right rear wheels, whose revolution speeds are independently controlled. Sensors L and R are photo reflective sensors, whose values change according to the ratio of black and white regions they pass over. If the ratio increases, the sensor value decreases, and if the ratio decreases, the sensor value increases. Which of the following is an appropriate control for ensuring that the vehicle travels along the black outline of the circle? Here, if the values of the two sensors match, the revolution speeds of the motors return to the initial speed.\n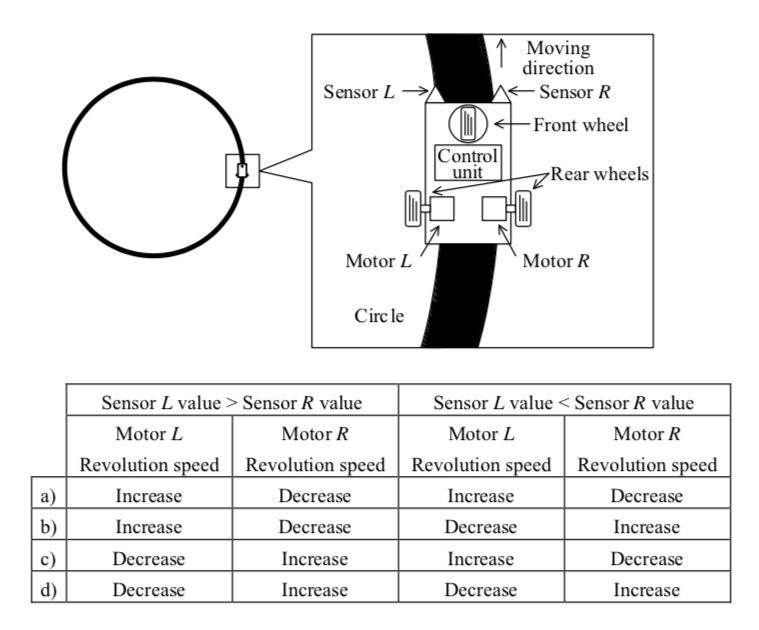","answer_label":"b","answer_id":5583},{"id":505,"question":"What is the result after evaluation of the following postfix expression? Here, symbols +, −, ×, and ÷ represent the arithmetic operators of addition, subtraction, multiplication, and division, respectively.\n5 4 6 + × 493÷ + ×","answer_label":"350","answer_id":5581},{"id":506,"question":"Two stack operations are defined:\nPUSH n: Pushes a data (integer value n) to the stack.\nPOP: Pops a data from the stack.\nFor an empty stack, which of the following is the result of performing stack operations in the sequence below?\nPUSH1 → PUSH5 → POP → PUSH7 → PUSH6 → PUSH4 → POP → POP → PUSH3\n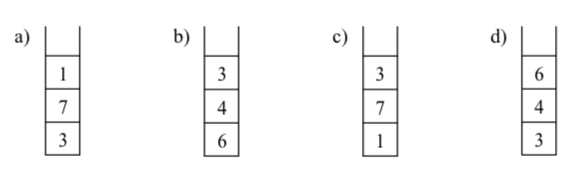","answer_label":"c","answer_id":5576},{"id":507,"question":"In a table search, which of the following is a characteristic of the search technique known as hashing?","answer_label":"The storage locations of data are determined based on the function values of their keys.","answer_id":5572},{"id":508,"question":"The binary search algorithm is used to search for a given item when items are sorted. If the number of items is 1 million, which of the following is the closest to the maximum number of comparisons required to find the item?","answer_label":"20","answer_id":5567},{"id":509,"question":"In object-oriented programming, which of the following is an explanation of overriding that achieves polymorphism?","answer_label":"A feature that allows a class to provide a specific implementation of a method that is already provided by one of its super classes","answer_id":5562},{"id":510,"question":"A CPU has a clock frequency of 2.0 GHz. When the instructions consist of three types, as shown in the table below, what is the approximate CPU performance in MIPS?\n\n| Type | Execution time (clocks) | Frequency of appearance (%) |\n| -------- | -------- | -------- |\n| Instruction 1 | 15 | 40 |\n| Instruction 2 | 10 | 20 |\n| Instruction 3 | 10 | 40 |","answer_label":"167","answer_id":5560},{"id":516,"question":"There exists a device with an MTBF of forty-five (45) hours and an MTTR of five (5) hours. What is the availability of a system that connects two (2) such devices in series?","answer_label":"0.81","answer_id":5554},{"id":517,"question":"Which of the following is an appropriate explanation of a memory leak?","answer_label":"Part of main memory reserved during operation is not released because of a bug in the OS or an application, and as a result, the usable area of main memory decreases.","answer_id":5552},{"id":518,"question":"An operating system (OS) chooses a process for CPU execution based on a scheduling algorithm. Consider four processes, P1, P2, P3, and P4, and their corresponding arrival times along with their burst times shown in the table below. Which of the following is the correct combination of waiting times for the processes to be executed in the First-Come-First-Serve (FCFS) scheduling algorithm? Here, the arrival time is the time at which a process arrives in the ready queue, the burst time is the time required by a process for CPU execution, and the waiting time is the period of time spent by a process in the ready queue for CPU to start the execution.\n(Unit: millisecond)\n\n| Process | Arrival time | Burst Time |\n| -------- | -------- | -------- |\n| P1 | 0 | 6 |\n| P2 | 2 | 4 |\n| P3 | 4 | 9 |\n| P4 | 5 | 7 |\n\n\n\n\n| | P1 | P2 | P3 | P4 |\n| -------- | -------- | -------- | -------- |-------- |\n| a) | 0 | 2 | 4 | 5 |\n| b) | 0 | 4 | 6 | 14 |\n| c) | 6 | 4 | 9 | 7 |\n| d) | 6 | 6 | 13 | 12 |","answer_label":"b","answer_id":5547},{"id":519,"question":"Which of the following is an explanation of an absolute path name in a file system?","answer_label":"The path name from the root directory to the target file","answer_id":5544},{"id":520,"question":"Which of the following is the main purpose of optimization by a compiler?","answer_label":"To reduce the execution time of a program","answer_id":5540},{"id":521,"question":"Which of the following is the average cycles per instruction (CPI) of a computer that can execute 1 billion instructions per second with a clock rate of 2.4 GHz?","answer_label":"2.4","answer_id":5536},{"id":522,"question":"The figure shows the storage sequence of instructions fetched by a processor. Which of the following corresponds to a?\n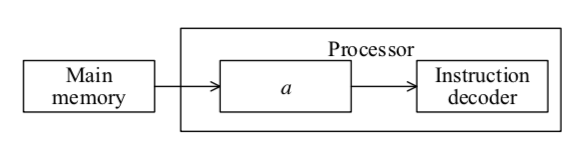","answer_label":"Instruction register","answer_id":5532},{"id":524,"question":"When two computers have been prepared, and the computer in use fails, which of the following is the system that continues processing by promptly switching to the backup computer that has started the same online processing programs as those on the currently- used computer in advance, and is on standby?","answer_label":"Hot standby system","answer_id":5527},{"id":525,"question":"Which of the following is essential to realizing a fault-tolerant system?","answer_label":"Providing redundancy in the system configuration to minimize the impact from any failure of parts so that processing can be continued without affecting the overall system","answer_id":5525},{"id":527,"question":"Which of the following is the OSS that is provided as an integrated development environment for software?","answer_label":"Eclipse","answer_id":5519},{"id":528,"question":"Which of the following is a sequential circuit that has two (2) stable states?","answer_label":"Flip-flop","answer_id":5516},{"id":529,"question":"Which of the following is an appropriate description of flash memory?","answer_label":"Data can be electronically erased in block units.","answer_id":5507},{"id":531,"question":"Which of the following is an equivalent representation of the circuit below where only NAND gates are used?\n\n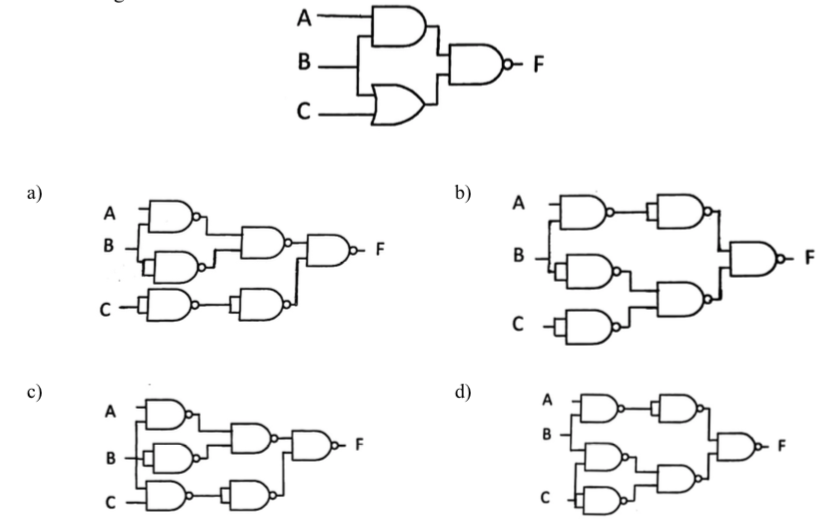","answer_label":"b","answer_id":5511},{"id":536,"question":"When an order data shown below is entered, which of the following is the data validation that is performed to determine whether the order date is on or before the business day on which the data is entered?\n\n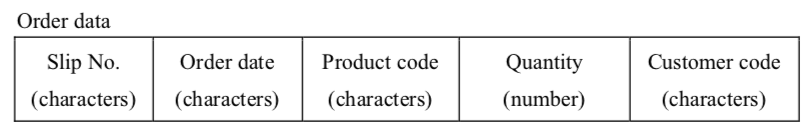","answer_label":"Logical check","answer_id":5500},{"id":537,"question":"Which of the following is the most appropriate explanation of augmented reality (AR)?","answer_label":"By seamlessly interweaving a computer-generated information with the physical world, the viewer can perceive it as an immersive aspect of the real environment.","answer_id":5496},{"id":538,"question":"Of the functions provided by a DBMS, which of the following is a means for achieving protection for data confidentiality?","answer_label":"Managing the data access rights of users","answer_id":5492},{"id":539,"question":"In a relational database, which of the following is the appropriate purpose for defining a foreign key?","answer_label":"To provide a constraint to maintain referential consistency between the records of related tables","answer_id":5487},{"id":540,"question":"Which of the following is an SQL statement that gives the same result as the SQL statement that is described below for the “Product” table and the “Inventory” table? Here, the underlined part indicates the primary key.\n\nSELECT ProductNumber FROM Product\n WHERE ProductNumber NOT IN (SELECT ProductNumber FROM Inventory)\n\n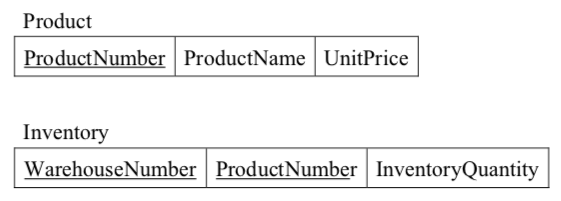","answer_label":"SELECT ProductNumber FROM Product WHERE NOT EXISTS (SELECT ProductNumber FROM Inventory WHERE Product.ProductNumber = Inventory.ProductNumber)","answer_id":5485},{"id":542,"question":"Which of the following is a file where values before and after an update of the database are written and saved as the update history of the database?","answer_label":"Log file","answer_id":5481},{"id":543,"question":"Which of the following is an appropriate description of the lock operation that is used for the concurrency control of a transaction?","answer_label":"For a resource on which a shared lock is acquired, the acquisition of a new shared lock by another transaction is permitted.","answer_id":5474},{"id":544,"question":"Which of the following is the device that operates only at the physical layer of the OSI model?","answer_label":"Repeater","answer_id":5471},{"id":545,"question":"Which of the following is the maximum theoretical data rate (in Mbps) achievable in the IEEE 802.11n network?","answer_label":"600","answer_id":5469},{"id":546,"question":"Which of the following is an architecture that decouples the network control and forwarding functions, enabling the network control to become directly programmable and the underlying infrastructure to be abstracted for applications and network services?","answer_label":"Software-defined networking","answer_id":5461},{"id":547,"question":"In telecommunication, which of the following is a standard for wireless broadband communication for mobile devices and data terminals?","answer_label":"LTE","answer_id":5455},{"id":548,"question":"Which of the following is an e-mail header field that is removed during the message transfer using SMTP?","answer_label":"Bcc","answer_id":5450},{"id":549,"question":"Which of the following is an attack that threatens the “integrity” of information?","answer_label":"Falsification of a web page","answer_id":5447},{"id":550,"question":"Which of the following is the purpose of using a message digest in a message authentication code?","answer_label":"To confirm that there is no falsification of a message","answer_id":5444},{"id":551,"question":"Which of the following is a role that a PKI certification authority performs as a reliable third party?","answer_label":"Issuing a digital certificate that certifies the public key of a user or server","answer_id":5441},{"id":552,"question":"Which of the following is a description of a directory traversal attack?","answer_label":"By specifying a file including the path name, the attacker illegally reads an unauthorized file.","answer_id":5434},{"id":583,"question":"There exists a device with an MTBF of forty-five (45) hours and an MTTR of five (5) hours. What is the availability of a system that connects two (2) such devices in series?","answer_label":"0.81","answer_id":1831},{"id":609,"question":"In ISO/IEC 27000:2018 (Information Security Management Systems – Overview and Vocabulary), which of the following is defined as the “property that an entity is what it claims to be”?","answer_label":"Authenticity","answer_id":5431},{"id":610,"question":"Which of the following is the purpose of port scanning when an attacker intrudes into the system?","answer_label":"To investigate if there is a service that can be attacked at the preliminary investigation stage","answer_id":5427},{"id":611,"question":"Which of the following is a description that corresponds to two-factor authentication?","answer_label":"Authentication is performed by using the iris and a password.","answer_id":5425},{"id":612,"question":"Which of the following is the combination of processes that constitutes risk assessment?","answer_label":"Risk identification, risk analysis, and risk evaluation","answer_id":5420},{"id":613,"question":"Which of the following is the malware that is used to gain unauthorized privileged access, hide its own presence, and to perform malicious activities in a computer system?","answer_label":"Rootkit","answer_id":5416},{"id":614,"question":"Which of the following is a method for preventing an SQL injection attack?","answer_label":"Preventing input characters from being interpreted as characters that have a special meaning in an inquiry or operation on the database","answer_id":5413},{"id":615,"question":"In object orientation, which of the following is the name of being able to use the attributes and functions of a class in a subclass of that class?","answer_label":"Inheritance","answer_id":5407},{"id":616,"question":"In the development process, which of the following is an activity that should be performed in software architecture design?","answer_label":"Converting the requirements for a software item into an architecture that represents the top-level structure and identifies software components","answer_id":5402},{"id":617,"question":"Which of the following is the testing technique that uses the different unique combination of input conditions to check whether the corresponding result is delivered based on the design rules as specified for the system?","answer_label":"Decision table testing","answer_id":5399},{"id":618,"question":"Which of the following is an appropriate test to ensure that the interfaces and linkages between different parts of software work properly?","answer_label":"Integration test","answer_id":5395},{"id":619,"question":"Among eXtreme Programming (XP) practices, which of the following is adopted to improve program quality in program development through smooth communication between programmers by exchanging their roles and checking each other’s work?","answer_label":"Pair programming","answer_id":5391},{"id":620,"question":"Screens are created for a system that is composed of a total of 100 screens. The breakdown of the 100 screens classified on the basis of size and complexity is shown below.\n\nNumber of screens with a “Small” size and “Low” complexity: 30 \nNumber of screens with a “Medium” size and “Medium” complexity: 40 \nNumber of screens with a “Large” size and “Medium” complexity: 20 \nNumber of screens with a “Large” size and “High” complexity: 10\n\nIf the total number of person-days for creating all screens is estimated by using the number of person-days for creation shown in the table below, how many person-days are required? Here, a review and revision of all the screens requires five (5) person-days, and project management requires 20% of the total person-days, including the person-days for review and revision.\n\n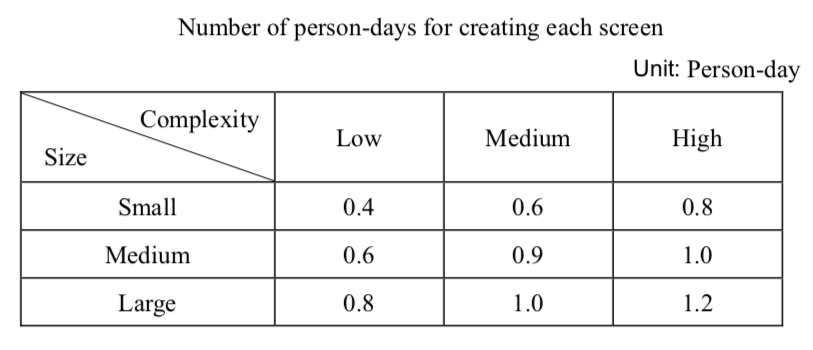","answer_label":"102","answer_id":5389},{"id":621,"question":"Which of the following is the technique for estimating activity durations where past information is statistically analyzed and various coefficients are determined?","answer_label":"Parametric estimate","answer_id":5384},{"id":622,"question":"Which of the following is the critical path of the project activities shown in the figure below?\n\n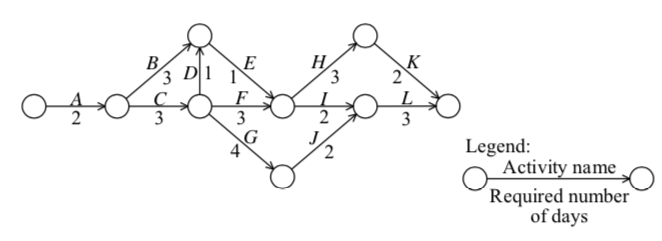","answer_label":"A->C->G->J->L","answer_id":5381},{"id":623,"question":"In order to analyze the trend of issues that occur in a project, the number of issues by management item, such as the stakeholders, cost, schedule, quality, etc., are arranged in order starting with the highest number of issues in the form of a bar graph, and a diagram is prepared in which the number of issues accumulated in this order are superimposed in the form of a line graph. Which of the following is this diagram?","answer_label":"Pareto diagram","answer_id":5376},{"id":623,"question":"In order to analyze the trend of issues that occur in a project, the number of issues by management item, such as the stakeholders, cost, schedule, quality, etc., are arranged in order starting with the highest number of issues in the form of a bar graph, and a diagram is prepared in which the number of issues accumulated in this order are superimposed in the form of a line graph. Which of the following is this diagram?","answer_label":"Pareto diagram","answer_id":5376},{"id":624,"question":"IT services are provided under the following conditions in the SLA. What is the maximum number of hours of downtime in a month that can satisfy the SLA?\n(Conditions of the SLA)\nThe number of business days per month is 30.\nThe service hours are from 7 AM to 11PM o'clock on a business day. \nThe required availability is 99% or more.\nOther required time, such as maintenance time, can be ignored.","answer_label":"4.8","answer_id":5372},{"id":625,"question":"In IT service management, which of the following is a problem management activity that performed proactively?","answer_label":"Analyzing the occurrence trend of incidents and proposing measures that prevent an incident from occurring in the future","answer_id":5366},{"id":626,"question":"Among the structures and the characteristics of a service desk organization, which of the following is a description of a local service desk?","answer_label":"By locating a service desk near the users, it is possible to provide support for users who speak different languages or come from different cultures, and to provide support for VIPs by dedicated staff.","answer_id":5362},{"id":627,"question":"Which of the following is an appropriate activity for a system auditor?","answer_label":"The auditor points out items that need to be improved regarding problems found during the investigation.","answer_id":5360},{"id":628,"question":"Among the implementation structures of a system audit, which of the following is the most important to avoid from the standpoint of the independence of a system auditor?","answer_label":"Mr. A of the general affairs department, who was appointed as a member of the audit team, audits the status of entrance and exit control for the general affairs department together with other team members.","answer_id":5354},{"id":629,"question":"In an information security audit, which of the following is a check item for confirming availability?","answer_label":"Managing and maintaining the level of SLA that defines downtime","answer_id":5352},{"id":630,"question":"Which of the following is an explanation of SCM (Supply Chain Management)?","answer_label":"The sequence of business operations, from purchasing and production to sales and distribution, is reexamined across companies in view of total optimization, so as to minimize inventory and accelerate delivery.","answer_id":5349},{"id":631,"question":"Concerning computerization costs, which of the following is the cost that indicates the running cost?","answer_label":"The maintenance cost of information-processing equipment, such as a server","answer_id":5345},{"id":632,"question":"Which of the following is an explanation of BPM?","answer_label":"To incorporate the management cycle of analysis, design, execution, and improvement into business processes in order to continuously execute improvement and revision of business processes","answer_id":5340},{"id":633,"question":"Which of the following is an explanation of SaaS?","answer_label":"It is a service where the user uses the functions of application software via the Internet only when necessary.","answer_id":5334},{"id":634,"question":"Which of the following should be undertaken in order to eliminate the “digital divide”?","answer_label":"Increasing learning opportunities for information literacy, and preparing an environment to further facilitate the use of information & telecommunications equipment and information services","answer_id":5331},{"id":635,"question":"Which of the following is an explanation of the non-functional requirements definition?","answer_label":"It clearly identifies the quality requirements, technical requirements, and operational requirements necessary to implement business requirements.","answer_id":5329},{"id":636,"question":"Which of the following is an external factor concerning an in-house product identified using SWOT analysis?","answer_label":"Threats owing to a new entry","answer_id":5325},{"id":637,"question":"According to the “competitive strategy” proposed by Philip Kotler, which of the following describes a company that has no high market share, but has the strategic aim to increase income and acquire a unique position by focusing management resources on particular products and services?","answer_label":"Market nicher","answer_id":5321},{"id":638,"question":"Which of the following is a technique for separating company activities into core activities and support activities for each business function, and analyzing which activities generate the profit derived from the products and services provided to customers?","answer_label":"Value chain analysis","answer_id":5317},{"id":639,"question":"Which of the following is an explanation of knowledge management?","answer_label":"Knowledge scattered across an enterprise is shared to improve overall problem-solving capability.","answer_id":5312},{"id":640,"question":"Which of the following is an explanation of CAD?","answer_label":"Using a computer to create product design drawings from attribute data concerning product shape, composition, etc.","answer_id":5308},{"id":641,"question":"Which of the following performs processing according to steps (1) through (3)?\n(1) Based on the types and quantities, as well as the parts list of the product to be manufactured within a future fixed period of time, the required quantity of components is calculated.\n(2) The net order quantity of each component is calculated from the amount of inventory that can be allocated.\n(3) The ordering time for the components is determined with consideration for the manufacturing or procurement lead time.","answer_label":"MRP","answer_id":5305},{"id":642,"question":"Which of the following is an explanation of EDI?","answer_label":"The exchange of business transaction data between computers (including terminals) over the Internet on the basis of standard protocols","answer_id":5301},{"id":643,"question":"Which of the following is the procurement process that enables suppliers to bid against one another on the Internet in order to sell their products or services under the conditions specified by a general customer?","answer_label":"Reverse auction","answer_id":5296},{"id":644,"question":"Which of the following is an appropriate method to forecast the amount of revenue during an upcoming promotion at a store, based on historical data?","answer_label":"Regression analysis","answer_id":5293},{"id":645,"question":"Which of the following is an appropriate explanation of a scatter diagram?","answer_label":"It is a chart used to determine if a relationship, pattern, or trend exists between two numeric attributes.","answer_id":5286},{"id":646,"question":"When a company sells a product at 17 dollars per unit, and the fixed costs and the variable costs are as shown in the tables below (in dollars), how many units does the company have to sell to earn a profit of 42,000 dollars?\n\nFixed costs:\n| Administration costs | 130,000 |\n| --- | --- |\n| R&D costs | 10,000|\n\nVariable costs per unit:\n| Raw material costs | 4 |\n| --- | --- |\n| Administration costs | 3 |","answer_label":"18,200","answer_id":5285},{"id":647,"question":"Which of the following inventory evaluation methods calculates the inventory unit price by dividing the total purchase amount by the total quantity of items purchased at the end of the accounting period?","answer_label":"Periodic average method","answer_id":5281},{"id":648,"question":"Which of the following is an appropriate description of the scope of software protection under Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"Both source programs and object programs are protected.","answer_id":5276},{"id":709,"question":"For an eight-bit integer x represented in two’s complement format, which of the following yields the value of 5x? Here, the overflow or underflow can be ignored in this multiplication.","answer_label":"Shift x to the left by 2 bits, then add the initial value of x to it.","answer_id":5271},{"id":710,"question":"How many four-digit decimal numbers are made from four (4) different digits between 0 and 9? Here, a four-digit decimal number has a non-zero leading digit.","answer_label":"4536","answer_id":5268},{"id":711,"question":"What is the value of the postfix expression below when variables A, B, C, and D have values 4, 3, 5, and 6, respectively? Here, symbols ‘+’, ‘-’, ‘x’, and ‘÷’ represent the arithmetic operators of addition, subtraction, multiplication, and division, respectively.\nA B 2 x + D B ÷ C x -","answer_label":"0","answer_id":5263},{"id":712,"question":"Which of the following is an appropriate explanation of the feedback control?","answer_label":"It performs a control so that the output matches the target.","answer_id":5259},{"id":713,"question":"Which of the following is a binary search tree?\n\n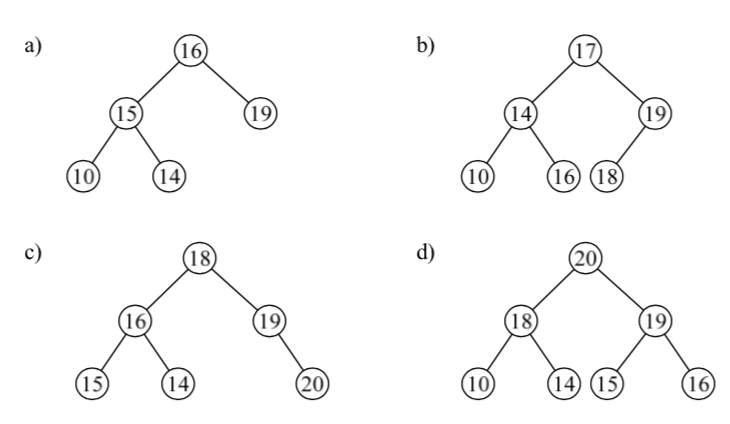","answer_label":"b","answer_id":5255},{"id":714,"question":"When the procedure described below is executed in sequence for an empty stack and empty queue, what is the value assigned to variable x? Here, the functions used in the procedure are defined as follows:\n(Function definitions)\npush(y): pushes data y onto the top of the stack.\npop(): removes the data from the top of the stack and returns it as the function value. enq(y): inserts data y at the tail of the queue.\ndeq(): removes the data from the head of the queue and returns it as the function value.\n\n(Procedure)\n\t\t\tpush(a)\n\t\t\tpush(b)\n\t\t\tenq(pop())\n\t\t\tenq(c)\n\t\t\tpush(d)\n\t\t\tpush(deq())\n\t\t\tx ← pop()","answer_label":"b","answer_id":5251},{"id":715,"question":"For a function f(x, y) defined below, what is the value of f(775, 527)? Here, x mod y represents the remainder after division of x by y.\n\nf(x, y): if y = 0 then return x else return f(y, x mod y)","answer_label":"31","answer_id":5247},{"id":716,"question":"The flowchart below shows the algorithm of concatenating two character strings in X and Y, with the resulting character string in Z. Which of the following is the appropriate pair of operations to insert in the blanks, A and B? Here, X and Y are character arrays of dimensions m and n, respectively, where the i-th character of each string is stored as the i-th element of the character array.\n\n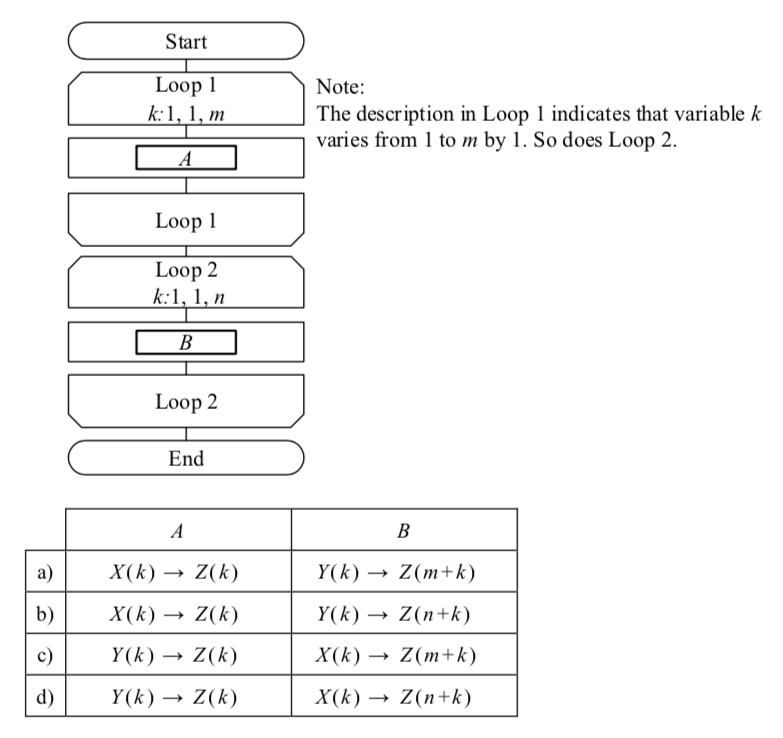","answer_label":"a","answer_id":5242},{"id":717,"question":"For a processor running at 50 MIPS, what is the average execution time per instruction?","answer_label":"20 ns","answer_id":5238},{"id":718,"question":"Which of the following is an appropriate characteristic of SRAM compared to DRAM? Here, SRAM and DRAM are compared in products manufactured in the same or similar semiconductor geometric process.","answer_label":"SRAM uses more transistors in a memory cell compared to DRAM.","answer_id":5237},{"id":719,"question":"In a memory system that has a cache memory, which of the following causes an increase in the average memory access time?","answer_label":"A decrease in the cache hit rate","answer_id":5231},{"id":720,"question":"There exists a storage system in which one (1) block is composed of eight (8) sectors of 500 bytes each, and the storage area is block-wise allocated to the files. When a 2,000-byte file and 9,000-byte file are to be saved, what is the total number of sectors that is allocated to these two (2) files? Here, the sectors that are occupied by the directory information and other such management information can be ignored.","answer_label":"32","answer_id":5229},{"id":721,"question":"Which of the following is an appropriate description concerning the recording method of RAID5?","answer_label":"It distributes the data over multiple hard disk drives, writes the data in units of blocks, and distributes and writes the parity on multiple hard disk drives.","answer_id":5223},{"id":723,"question":"A system has devices with availability R, connected as shown in the figure below. Which of the following is the expression that represents the availability of the entire system? Here, a parallel connection only requires either of the two devices to be functional, whereas a series connection requires both the devices to be functional.\n\n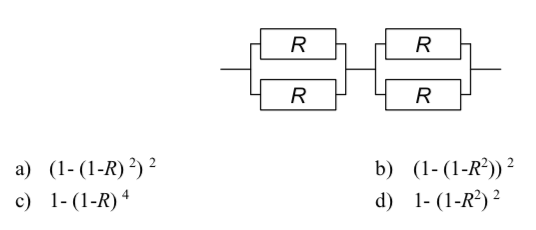","answer_label":"a","answer_id":5218},{"id":724,"question":"Which of the following is an appropriate explanation of paging?","answer_label":"A method of memory management in which the virtual memory space and real memory space are divided into fixed-length blocks for management","answer_id":5217},{"id":725,"question":"Which of the following is a method that performs data transfer between the main memory and a low-speed output device via a high-speed auxiliary storage device to increase the throughput of the entire system?","answer_label":"Spooling","answer_id":5212},{"id":726,"question":"In the figure below, data are sent continuously for T seconds from the send task to the receive task. When the volume of the data sent per second is S and volume of the data received per second is R, which of the following is an appropriate relational expression for buffer size L for a buffer that does not overflow? Here, the transmission speed for the send task is faster than the transmission speed for the receive task, and there is sufficient time between the transmissions.\n\n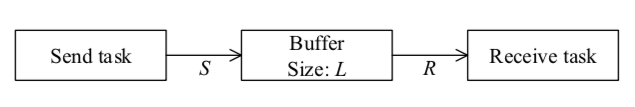","answer_label":"L≥(S-R)×T","answer_id":5209},{"id":727,"question":"On a virtual memory computer, the number of pages that can be allocated to the real memory is three (3), and the two (2) algorithms of FIFO and LRU are used for selecting the page to be removed. When a page reference string shown below accesses the three (3) pages, which of the following is an appropriate combination of the number of page replacement operations? Here, the three (3) pages are initially empty and filling of an empty page is not considered as a page replacement operation.\n\n 1, 3, 2, 1, 4, 5, 2, 3, 4, 5\n\t\t\t\t\t\n","answer_label":"b","answer_id":5203},{"id":728,"question":"A real-time OS performs preemptive scheduling on a priority basis and schedules two (2) tasks A and B. When A has a higher priority than B, which of the following is an appropriate task management by the real-time OS?","answer_label":"When A is launched during the execution of B, B is assigned a “ready” status and A is executed.","answer_id":5198},{"id":729,"question":"Which of the following is an appropriate explanation of the function of an actuator?","answer_label":"It changes an electrical control signal that is supplied by a computer into a mechanical motion.","answer_id":5195},{"id":730,"question":"Which of the following is an appropriate example of utilizing an RFID?","answer_label":"Identification and management of personnel or items by using a very small wireless chip","answer_id":5191},{"id":731,"question":"Which of the following is a logical expression that is equivalent to the logic circuit shown below?\n\n","answer_label":"A OR B","answer_id":5188},{"id":732,"question":"For a given data, the check digit is calculated with the method below and is appended to the original data. When the given data are 7394, what is the result? Here, the weight is 1234 and base number is 11.\n(1) For each digit of the data, calculate the product with the digit at the same radix of the weight; then calculate the sum of the products.\n(2) Calculate the remainder of dividing the sum by the base number.\n(3) Subtract the remainder from the base number; then take the one’s place of the result as\nthe check digit.","answer_label":"73940","answer_id":5182},{"id":733,"question":"In 3D computer graphics, which of the following is an explanation of hidden-line removal or hidden-surface removal in rendering?","answer_label":"For the target object, only the portion that is viewable from a specified viewpoint is rendered.","answer_id":5180},{"id":734,"question":"An employee works for a department, which can be located in multiple regions. Three tables EMP, DEPT, and DEPT_LOCS are created as shown below for recording the employee, department, and department location data, respectively.\n\n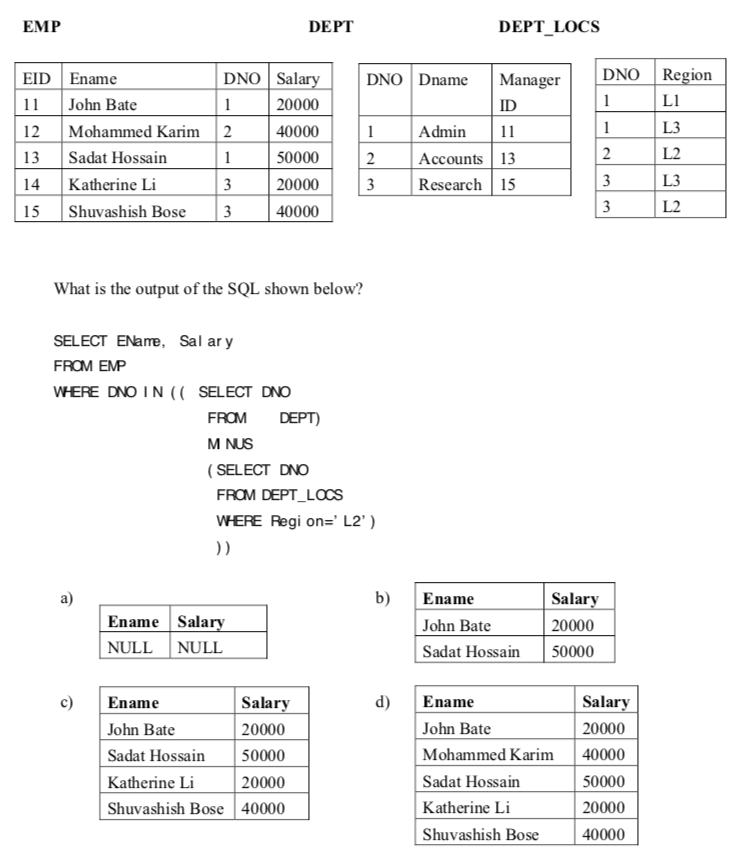","answer_label":"b","answer_id":5175},{"id":735,"question":"In an SQL statement, which of the following is a constraint that is specified with FOREIGN KEY and REFERENCES?","answer_label":"Referential constraint","answer_id":5173},{"id":736,"question":"In a client/server system, which of the following is the mechanism that reduces the network load between the client and server by placing the frequently used commands on the DBMS on the server in advance?","answer_label":"Stored procedure","answer_id":5168},{"id":737,"question":"Which of the following is a characteristic to guarantee that the result of an update transaction is either performed completely or canceled as if nothing happened?","answer_label":"Atomicity","answer_id":5162},{"id":738,"question":"Which of the following is the process that is executed periodically to prevent reducing the access efficiency of the database?","answer_label":"Reorganization","answer_id":5160},{"id":739,"question":"In IPv4, which of following describes the NAT function of a router that connects some computers to the Internet?","answer_label":"It converts between private and global IP addresses.","answer_id":5155},{"id":740,"question":"Which of the following is a feature of a switching hub (layer 2 switch) network device?","answer_label":"It forwards a received packet only to its LAN port connected to a device with the packet’s destination MAC address.","answer_id":5152},{"id":741,"question":"Which of the following is the network routing and addressing mechanism that is used in\nIPv6 but not in IPv4?","answer_label":"Anycast","answer_id":5146},{"id":742,"question":"In an IPv4 network with subnet mask 255.255.255.224, what is the maximum number of host addresses assigned?","answer_label":"30","answer_id":5145},{"id":743,"question":"Which of the following is a protocol that uses TCP as its transport layer protocol?","answer_label":"TELNET","answer_id":5140},{"id":744,"question":"The IP address of Server X prepared by an attacker was stored in a DNS cache server of Company B as the IP address corresponding to the FQDN of the web server of Company A. Which of the following users will be unintentionally guided to Server X because of this attack? Here, each employee of Company A and Company B performs name resolution by using the DNS cache server of his/her own company.","answer_label":"An employee of Company B who wishes to access the web server of Company A","answer_id":5136},{"id":745,"question":"Which of the following is a description of a directory traversal attack?","answer_label":"An attacker specifies a file by using the path name and illegally views a file that is not intended for viewing by the administrator.","answer_id":5133},{"id":746,"question":"Which of the following is a description of a brute force attack by which an attempt is made to find the key of private key cryptography?","answer_label":"Finding the key by testing all key combinations sequentially when a set of plaintext and ciphertext is given","answer_id":5127},{"id":747,"question":"Which of the following is an explanation of the time stamp service in information security?","answer_label":"It is a service that certifies that electronic data certainly exist on a particular date and time and that the data have not been falsified since that date and time.","answer_id":5123},{"id":748,"question":"Which of the following is an encryption algorithm for public key cryptography?","answer_label":"RSA","answer_id":5120},{"id":749,"question":"Which of the following is a security attack that prevents users from accessing their accounts?","answer_label":"Denial of Service","answer_id":5115},{"id":750,"question":"Which of the following is an appropriate description of a botnet?","answer_label":"A collection of internet-connected devices, including IoT devices, infected and controlled by a common type of malware","answer_id":5110},{"id":751,"question":"An attacker captures unencrypted network traffic with a tool and later analyzes it offline to learn about the information contained in those transmissions. Which of the following is this attack?","answer_label":"Sniffing attack","answer_id":5109},{"id":752,"question":"Which of the following is the technique of actually attempting an attack and intrusion on a system to detect the security-related vulnerabilities of a computer or network?","answer_label":"Penetration test","answer_id":5102},{"id":753,"question":"As shown in the figure below, an application on a client accesses the data of the database on a server via database connection programs. Which of the following is a measure for preventing the leakage of the commands and execution results transmitted between the application and database?\n\n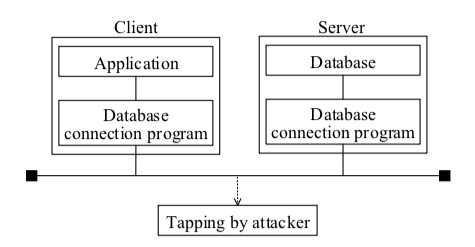","answer_label":"Encrypting the communication between the database connection programs","answer_id":5099},{"id":754,"question":"In the UML class diagram, which of the following represents the relationship between the classes as shown in the figure below?\n\n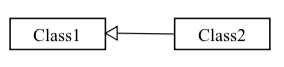","answer_label":"Generalization","answer_id":5097},{"id":755,"question":"Which of the following is an explanation of encapsulation in object orientation?","answer_label":"Combination of the data and procedures that operate the data into a single object, and their concealment from outside the object","answer_id":5091},{"id":756,"question":"Which of the following can generally be called a subclass of an “automobile” based on the concept of object orientation?","answer_label":"Truck","answer_id":5089},{"id":757,"question":"In the flowchart below, what is the minimum number of test cases that satisfies the decision condition coverage (branch coverage)?\n","answer_label":"2","answer_id":5083},{"id":758,"question":"Among the software development activities, which of the following corresponds to refactoring, which is also emphasized in agile development?","answer_label":"To improve the maintainability of a software, the internal structure of a program is changed without any change in the external specifications.","answer_id":5078},{"id":759,"question":"Which of the following is an appropriate explanation of the PERT diagram as shown in the figure below?\n\n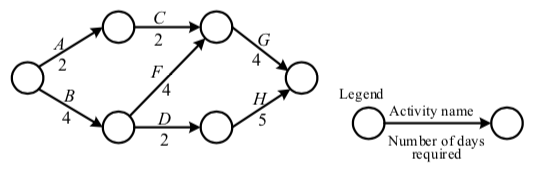","answer_label":"When the activity F becomes unnecessary, the project will end 1 day earlier.","answer_id":5076},{"id":760,"question":"By using the triangular distribution formula of the three-point estimation technique, which of the following is the expected duration (in days) required for an activity? The estimations are as shown below.\nConditions – Estimations for the activity duration\nCase 1: Two (2) days. If an experienced employee is assigned for this activity.\nCase 2: Four (4) days. If a general employee is assigned for this activity.\nCase3: Twelve (12) days. If an unexperienced employee is assigned for this activity.","answer_label":"6","answer_id":5072},{"id":761,"question":"A project is planned to complete in 12 months and the budget for the completion of the project is $100,000. After six months, it is found that $60,000 are spent, but only 40% of the work is completed. If the Cost Performance Index (CPI) is not changed, what is the estimated amount (in dollars) required to complete the remaining tasks of the project?","answer_label":"90,000","answer_id":5068},{"id":762,"question":"Which of the following is an appropriate cost estimation technique that estimates the cost of an activity or project using the historical data from a similar project?","answer_label":"Analogous estimating","answer_id":5062},{"id":763,"question":"Which of the following is the most appropriate description concerning a backup method for data in a new system?","answer_label":"In consideration of a possible increase in the response time in the business processes, the backup schedule is adjusted so that it does not overlap with the business processes.","answer_id":5058},{"id":764,"question":"For servers, the total cost of ownership (TCO) is calculated over a period of 5-years. The purchase price of the servers is $120,500 and the other annual costs are listed as below.\n\n| Area of Cost | Annual Cost ($) |\n| -- | -- |\n| Insurance | 2,030 |\n| Maintenance | 1,000 |\n| Repair (average) | 700 |\n| Registration | 270 |\n\nWhat is the TCO of the servers (in dollars)?","answer_label":"140,500","answer_id":5056},{"id":765,"question":"In ITIL, the reduction in the index value expressing the maintainability is cited as an example of a KPI (Key Performance Index) in availability management. Which of the following corresponds to such an index?","answer_label":"Mean time to restore service","answer_id":5052},{"id":766,"question":"Which of the following is the system audit implementation structure that should be avoided from the standpoint of independence of the system auditors?","answer_label":"A person in the general affairs department, who is appointed as a member of the audit team, audits the status of the entrance and exit control in the general affairs department, together with the other members.","answer_id":5048},{"id":767,"question":"Which of the following is an appropriate activity that is undertaken by a system auditor who audits access control?","answer_label":"Confirmation of the management status of the access control concerning the data","answer_id":5042},{"id":768,"question":"Which of the following is subject to system audits that evaluate and verify the internal control related to IT?","answer_label":"The methods for ensuring accuracy in the processes of input and update of a database performed by the sales department","answer_id":5038},{"id":769,"question":"Which of the following is a case that enables the customer support operations at a call center to improve the quality by applying a pattern recognition function or machine learning function to the accumulated data?","answer_label":"Deriving the most appropriate response in real time from the related materials and all the previous support history according to the content of the inquiry made by a customer","answer_id":5034},{"id":770,"question":"When an UML is used for business modeling, which of the following is the diagram that can represent a workflow such as the execution sequence of the business processes and branching based on conditions?","answer_label":"Activity diagram","answer_id":5030},{"id":771,"question":"Which of the following is a description of the SOA?","answer_label":"A concept of constructing a system by considering the software functions as components called services and combining them","answer_id":5026},{"id":772,"question":"Which of the following is a scheme where the user establishes a connection to the system of a service provider via the Internet and makes online use of only the necessary functions of the applications provided by the service provider at the necessary time?","answer_label":"SaaS","answer_id":5023},{"id":773,"question":"A company chooses products and services that are acknowledged as actively addressing environmental concerns. What is this initiative called?","answer_label":"Green procurement","answer_id":5020},{"id":774,"question":"When a developmental process of utilizing big data is classified into the four (4) stages below, which of the following is an example that corresponds to the fourth stage?\n(Developmental stages of big data utilization)\nStage 1: Confirmation of facts in the past and present (what was it before?)\nStage 2: Interpretation of the past and present status (why have/had it be so?)\nStage 3: Prediction of the occurrence of a possible event in the future (what is it likely to\nbe?)\nStage 4: Development into a future activity (what should be done?)","answer_label":"Based on the big data, cases of operational errors made by users and increase in the failure rate due to such cases are estimated and the user interface is improved to make it less likely to cause operational errors.","answer_id":5015},{"id":775,"question":"In a growth matrix proposed by Ansoff, which of the following is a strategy for expanding a business with an existing product in an existing market?","answer_label":"Market penetration","answer_id":5012},{"id":776,"question":"Which of the following is a characteristic of the growth stage in a product life cycle?","answer_label":"The market starts to understand the worth of the product. Both the product line and channel need to be expanded. This stage sees an increase in the sales and also requires investment.","answer_id":5009},{"id":777,"question":"Which of the following marketing approaches is for the push strategy?","answer_label":"A manufacturer does his/her best to predict what customers want before producing an item or service.","answer_id":5003},{"id":778,"question":"Which of the following can take advantage of the cell production method?","answer_label":"Products that require flexible production to produce a variety of types","answer_id":5000},{"id":779,"question":"Which of the following is not appropriate as an application example of the IoT (Internet of Things)?","answer_label":"A computer that independently performs file management, arithmetic and logic operations, printing processing, and other tasks without accessing a server to avoid the security problems on the Internet","answer_id":4994},{"id":780,"question":"Which of the following is a description of CGM (Consumer Generated Media)?","answer_label":"It enables the delivery of the digital contents prepared by an individual to a viewer or audience and its sharing between the users.","answer_id":4991},{"id":781,"question":"Which of the following is a description of the long tail?","answer_label":"The accumulated sales of the product groups that are not selling well account for a percentage that cannot be ignored against the total sales in Internet shopping.","answer_id":4989},{"id":782,"question":"Which of the following is a use case of deep learning to improve the performance of an in-car device?","answer_label":"By the acquisition and processing of numerous images, the driver assistance system can distinguish between a pedestrian and vehicle more reliably.","answer_id":4984},{"id":783,"question":"Which of the following is a major role of a CIO?","answer_label":"The CIO creates a plan for optimizing the effect of investment on the information resources of the entire company to support the business strategy when a computerization strategy is established.","answer_id":4978},{"id":784,"question":"Which of the following is a characteristic of the OJT?","answer_label":"Because the boss or a senior associate imparts hands-on knowledge and technical education by staying close to practical affairs, the required competency can be acquired.","answer_id":4975},{"id":785,"question":"Which of the following is a description of the ABC analysis?","answer_label":"It arranges products in the order of high sales or high gross profit, divides into levels based on the cumulative ratio, and then plans to increase the volume of the sales of products at the high levels.","answer_id":4971},{"id":786,"question":"Which of the following is a financial statement that represents the assets, liabilities, and net assets of a company at a certain point of time and indicates the financial situation of the company?","answer_label":"Balance sheet","answer_id":4966},{"id":787,"question":"Which of the following is a method for making decisions on the basis of the sum of the future cashflows discounted by a discount rate?","answer_label":"Net Present Value Method (NPV)","answer_id":4963},{"id":788,"question":"Which of the following is a criminal act related to a computer virus according to the Convention on Cybercrime?","answer_label":"A person who finds a virus that is created by a stranger stores the virus for the purpose of subsequently running it on another person’s computer.","answer_id":4960},{"id":789,"question":"For an 8-bit binary number, which of the following sets the middle 4 bits to 1s while inverting the remaining bits?","answer_label":"Performing a bitwise NAND operation with 11000011","answer_id":4955},{"id":790,"question":"Which of the following is logically equivalent to the expression below? Here A, B, C, and D are integers, ‘<’ is a less-than operator, and ‘≤’ is a less-than-or-equal-to operator.\nnot ((A ≤ B) or (C < D))","answer_label":"(B<A) and (D≤C)","answer_id":4952},{"id":791,"question":"There are 16 cards numbered from 1 to 16. When four cards are randomly chosen at the same time, what is the probability that all of them are even?","answer_label":"1/26","answer_id":4946},{"id":792,"question":"For two sets A and B of cardinalities 3 and 2, how many maps from A to B exist?","answer_label":"8","answer_id":4944},{"id":793,"question":"The expression shown below is written in postfix (reverse Polish) notation. What is the value of this expression? Here, the numbers are in decimal, and the symbols ‘+’, ‘−’, ‘’, and ‘/’ represent addition, subtraction, multiplication, and division operators.\n100 5 6 2 + * 12 4 / − − 36 −","answer_label":"27","answer_id":4940},{"id":794,"question":"For a two-dimensional integer array a, whose element a ( i, j) is of value 2i + j, what is the value a(a(1,1) × 2, a(2, 2) + 1)?","answer_label":"19","answer_id":4937},{"id":795,"question":"Which of the following is the addressing mode where the instruction contains the address and the address is modified by a value from another register?","answer_label":"Indexed addressing mode","answer_id":4931},{"id":796,"question":"Which of the following is the computer architecture where processors execute multiple instruction streams on multiple data streams in parallel?","answer_label":"MIMD","answer_id":4926},{"id":797,"question":"Which of the following is an appropriate explanation of memory interleaving?","answer_label":"It allows CPU to access different banks of the main memory simultaneously.","answer_id":4922},{"id":798,"question":"Which of the following is an appropriate role for a device driver?","answer_label":"It directly controls hardware according to requests from an application program.","answer_id":4919},{"id":799,"question":"Which of the following is an appropriate term to describe the phenomenon when files produced in the process of saving are scattered to different parts of the whole hard disk rather than in continuous clusters?","answer_label":"Fragmentation","answer_id":4915},{"id":800,"question":"Which of the following is the most appropriate explanation of grid computing?","answer_label":"A computing task is distributed to several computers in the network to attain the computational capacity.","answer_id":4910},{"id":801,"question":"Consider a RAID 0 (i.e., block-level striping without parity or mirroring) system with two disks; when data is distributed evenly across the two disks and both disks have a failure rate of 0.1%, what is the overall failure rate (as a percentage) of this RAID system? Here, the overall failure rate refers to the probability that the system fails to obtain data from either of the disks.","answer_label":"0.1999","answer_id":4908},{"id":802,"question":"Which of the following is an appropriate description concerning MTBF and MTTR?","answer_label":"MTBF of a system increases through preventive maintenance.","answer_id":4904},{"id":803,"question":"In virtual memory management, which of the following page replacement methods replaces the page for which the most time has passed since it was last used?","answer_label":"LRU","answer_id":4901},{"id":804,"question":"The methods for representing the results of syntactic analysis in a compiler include quadruplet format.\n(Operator, Operand 1, Operand 2, Result)\nThis format indicates that the application of the operator to operand 1 and operand 2 outputs the result. For which of the following expressions does the series of quadruplets below represent the syntactic analysis? Here, T1, T2, and T3 indicate temporary variables.\n\n(*,B,C,T1 )\n(/,T1 ,D,T2 )\n(+,A,T2 ,T3 )","answer_label":"A+B*C/D","answer_id":4894},{"id":805,"question":"ABC company applies a three-generation backup policy. The ABC company’s system automatically performs full back up on the 10th, 17th, and 25th of each month. If the latest back up was performed on 17th September, what is the date that the oldest information was backed up?","answer_label":"25th August","answer_id":4891},{"id":806,"question":"Which of the following is a method that performs integration of the modules that configure a program during execution of the program?","answer_label":"Dynamic linking","answer_id":4886},{"id":807,"question":"Which of the following is a characteristic of DRAM?","answer_label":"The memory cell structure is simple, so high integration is possible and a low price per bit can be achieved.","answer_id":4884},{"id":808,"question":"Which of the following is an appropriate explanation of clipping in 3D graphics processing?","answer_label":"It is a method to selectively enable or disable rendering operations within a defined region of interest.","answer_id":4878},{"id":809,"question":"Which of the following is a database design that consists of multiple tables, with rows and columns that are linked together through matching data stored in each table?","answer_label":"Relational database","answer_id":4877},{"id":810,"question":"Which of the following is an appropriate explanation of schema in RDBMS?","answer_label":"It is a set of data definitions, such as the nature of data, the format of data, and the relation with other data.","answer_id":4872},{"id":811,"question":"Which of the following is an appropriate normalization form (NF) used in a relational database in which every non-prime attribute must be dependent only on the primary key, and no non-prime attribute is dependent on another non-prime attribute?","answer_label":"3NF","answer_id":4868},{"id":812,"question":"Among the phases of database design, which of the following phases involves the creation of an ER diagram?","answer_label":"Conceptual design of databases phase","answer_id":4862},{"id":813,"question":"Which of the following is a routable IP address in the Internet?","answer_label":"172.40.77.4","answer_id":4859},{"id":814,"question":"Among the seven layers of the OSI basic reference model, which layer is responsible for forwarding packets, including routing them through intermediate routers?","answer_label":"The network layer","answer_id":4855},{"id":815,"question":"Which of the following is an Internet service that translates a domain name such as www.itpec.org into its corresponding IP address?","answer_label":"DNS","answer_id":4851},{"id":816,"question":"Which of the following is an appropriate description of the netstat utility?","answer_label":"It displays active TCP connections.","answer_id":4846},{"id":817,"question":"Alan would like to send an encrypted message to Bob using an asynchronous encryption scheme. Which of the following must occur before Alan sends the encrypted message to Bob? Here, Alan has already proven to Bob with the digital signature that Alan is the person who sends the message to Bob.","answer_label":"Bob provides his public key to Alan.","answer_id":4845},{"id":818,"question":"Which of the following is an appropriate term associated with the fraudulent action of impersonating an authorized person?","answer_label":"Spoofing","answer_id":4836},{"id":819,"question":"An attacker calls a corporate help desk, masquerading as an employee who has lost their password. The help desk staff resets the password to the company default \"password1.\" The attacker then uses this password to access the company network and information in the server. What is this type of attack called?","answer_label":"Social engineering","answer_id":4833},{"id":820,"question":"A man-in-the-middle attack happens when an attacker intercepts communication and spoofs the identities of either of the two parties involved. How can such an attack be effectively countered?","answer_label":"Such an attack can be countered by having an authentication through a digital signature before accepting someone's public key.","answer_id":4827},{"id":821,"question":"Bob and Alice encrypt all of their communications with each other. Because of the high level of sensitivity of the information they are sharing, they have implemented a cryptographic mechanism that offers secrecy to their messages. However, the trade-off of this encryption is that it is impossible for Bob or Alice to be 100% sure that they are communicating with each other, nor can they be 100% certain of the integrity of the content of the messages. Which of the following types of encryption methods are Bob and Alice using?","answer_label":"One-time pad","answer_id":4824},{"id":822,"question":"A user has just received a file named “image.jpg.”\nWhen inspected more closely, it is revealed that the file name is actually “image.jpg .exe,” with spaces between the fake .jpg suffix and the real .exe suffix.\nWhich of the following is the most appropriate term used to describe this type of attack?","answer_label":"Trojan horse","answer_id":4819},{"id":823,"question":"A data backup system must support restoring all transactions until 5 minutes before a disaster happens. What type of goal is this?","answer_label":"Recovery point objective","answer_id":4815},{"id":824,"question":"Which of the following is an appropriate test to verify the efficacy of security measures by attempting an actual intrusion?","answer_label":"Penetration test","answer_id":4812},{"id":825,"question":"Which of the following is an appropriate method to prevent a buffer overflow attack?","answer_label":"Performing the boundary check on all string variables in the program to confirm that the length of the input string does not exceed the size of the designated variable","answer_id":4809},{"id":826,"question":"Companies usually provide a means for their mobile workforce to access the corporate network securely over the Internet through insecure channels such as open wireless networks in hotels or coffee shops. Which of the following is the appropriate technology that can be used for this purpose?","answer_label":"VPN (Virtual Private Network)","answer_id":4805},{"id":827,"question":"Which of the following are components of a UML2.x (including 2.0 and later versions) state diagram?","answer_label":"State and Transition","answer_id":4801},{"id":828,"question":"Which of the following is an appropriate description concerning test data for the black box testing?","answer_label":"Test data is created based on external specification.","answer_id":4796},{"id":829,"question":"According to the Capability Maturity Model Integration, which is the final stage and has the highest level of maturity?","answer_label":"Optimized","answer_id":4792},{"id":830,"question":"According to PMBOK, which of the following combinations of processes pertains to project integration management?\nA. Control costs\nB. Develop project charter\nC. Direct and manage project work\nD. Identify risks\nE. Manage communications\nF. Perform integrated change control","answer_label":"B, C, F","answer_id":4788},{"id":1602,"question":"In order to sort the sequence “98, 12, 4, 56, 34, 23” in ascending order by Bubble Sort algorithm, how many exchange operations are required?","answer_label":"9","answer_id":7537},{"id":1603,"question":"When data is read into a processor and there are no hits in the cache memory, which of the following is the action that the cache memory control unit performs?","answer_label":"The required data is read from main memory to cache memory by using the block\r\ntransfer mechanism.","answer_id":7540},{"id":1604,"question":"Which of the following statement is true for DMA Controller?","answer_label":"DMA controller enables data transfer directly between input/output devices and the\r\nmemory while the CPU can perform some other operations.","answer_id":7543},{"id":1605,"question":"Consider a disk drive that has a capacity of 8 GB. The drive has 5 platters with two surfaces, 10,000 tracks per surface and 200 sectors per track. How many bytes are in each sector? Here, 1GB is 1,000,000,000 bytes","answer_label":"400","answer_id":7549},{"id":1606,"question":"Which of the following is the concept of a fail-safe design?","answer_label":"When the system determines that there is a fault in the sensor for detecting if someone\r\nhas entered the working envelope or work area, the robot arm is stopped forcibly.","answer_id":7554},{"id":1607,"question":"Which of the following is an appropriate description concerning the reliability of a computer system?","answer_label":"Preventive maintenance of systems is performed to increase MTBF","answer_id":7557},{"id":1608,"question":"In a paged virtual memory, the LRU method is adopted for the page replacement algorithm. When the page frame allocated to the main memory is 4, which of the following page is to be replaced when page 6 is accessed if the pages are accessed in the order of page 1, 2, 3, 4, 5, 2, 1, 3, 2, 6? Here, no page exists in the main memory in the initial state.","answer_label":"5","answer_id":7562},{"id":1609,"question":"A real-time OS, which performs preemptive scheduling based on priority, schedules the tasks A and B. When A has a higher priority than B, which of the following is an appropriate action that is performed by the real-time OS?","answer_label":"When A is launched during the execution of B, B is put into a “ready” state and A is\r\nexecuted.","answer_id":7563},{"id":1610,"question":"Which of the following is an appropriate explanation of the spooling function?","answer_label":"The overall processing power of a system is enhanced by performing data transfer\r\nbetween the main storage and low-speed input/output devices via auxiliary storage\r\ndevices.","answer_id":7570},{"id":1611,"question":"Which of the following is an explanation of an absolute path name of a file system?","answer_label":"It is the path name from the root directory up to the target file.","answer_id":7573},{"id":1612,"question":"Which of the following is an appropriate explanation of DRAM?","answer_label":"It is memory that needs to be refreshed, and is used for main memory in a PC.","answer_id":7575},{"id":1613,"question":"Which of the following is the standard used to describe the look and formatting of markup language documents such as HTML and XHTML?","answer_label":"CSS","answer_id":7580},{"id":1614,"question":"In the process of creating animation, which of the following is used to incorporate the natural movement of objects, humans and animals, by using sensors and video cameras?","answer_label":"Motion capture","answer_id":7585},{"id":1615,"question":"Among the descriptions concerning database models, which of the following is an appropriate explanation of the network model?","answer_label":"Its records can have multiple parent records and multiple child records.","answer_id":7590},{"id":1616,"question":"In the operation of a relational database, which of the following is an appropriate explanation of projection?","answer_label":"Only specific columns are extracted from a table","answer_id":7592},{"id":1617,"question":"Which of the following is the role of DNS in a TCP/IP network?","answer_label":"IP addresses are mapped to domain names, host names, and other such information.","answer_id":7598},{"id":1618,"question":"In OSI basic reference model, what devices are used for segmentation or coupling of Physical layer, Data Link layer and Network layer respectively?","answer_label":"Repeater, Bridge, Router","answer_id":7601},{"id":1619,"question":"In TCP/IP networks, which command uses the ICMP “Echo”, “Echo Reply” and “Destination Unreachable” messages to test the reachability of the communication partner ?","answer_label":"ping","answer_id":7606},{"id":1620,"question":"Which application protocol must support UDP as its transport layer protocol?","answer_label":"DNS","answer_id":7607},{"id":1621,"question":"Which of the following is an appropriate explanation of POP3 used in e-mail systems?","answer_label":"It is a protocol used to receive e-mail messages from the mailbox of a mail server.","answer_id":7613},{"id":1622,"question":"Which of the following is the most appropriate case example of social engineering?","answer_label":"A phone call was made to a helpdesk of a computer center. By using the personal\r\ninformation scavenged from a trash bin, the caller convinces the helpdesk staff that\r\nhe/she is a legitimate user, in order to have the password initialized and then break into\r\nthe system","answer_id":7616},{"id":1623,"question":"Which of the following is a purpose of using message digest in a message authentication code?","answer_label":"To confirm that there is no falsification of a message","answer_id":7621},{"id":1624,"question":"Which of the following is an attack that threatens the “integrity” in information security?","answer_label":"Falsification of a Web page","answer_id":7624},{"id":1625,"question":"Which of the following is an explanation of SQL injection?","answer_label":"It is an attack where a command for performing a malicious query or operation in the\r\ndatabase is entered when there is a problem in a Web application, and the data of the\r\ndatabase is modified or acquired without authorization.","answer_id":7628},{"id":1626,"question":"Which of the following is an appropriate operation in user authentication that uses an IC card and PIN?","answer_label":"When an IC card is delivered, the PIN is not enclosed, but is notified to the user through\r\nanother channel.","answer_id":7634},{"id":1627,"question":"In a database that manages user information, there exists an application that searches for user information and displays it. In terms of security management, which of the following is an appropriate level of privilege for access to the database to be assigned to this application? Here, the scope of each privilege is as below.\n\n[Scope of privilege]\nReference privilege: Records can be referred to.\nUpdate privilege: Records can be registered, changed, and deleted.\nAdministrator privilege: Tables can be referenced, registered, changed, and deleted.","answer_label":"Reference privilege","answer_id":7636},{"id":1628,"question":"When a biometric authentication system is installed, which of the following is the most appropriate point to be considered?","answer_label":"Adjusting the system in consideration of both the probability of incorrectly rejecting an authorized user and the probability of incorrectly accepting an unauthorized user","answer_id":7639},{"id":1629,"question":"Which of the following technology is the most suitable to divide the whole company network into the networks by department?","answer_label":"VLAN (Virtual Local Area Network)","answer_id":7645},{"id":1630,"question":"There exists an OS that can independently set the reading, writing, or execution rights for a file as the attribute information of the file. One bit is used for each of these three rights to set whether they are permitted or not. When these three bits are set using an octal value from 0 through 7, which of the following is an appropriate description considering the trial results below?\n\n [Trial results]\n (i) When 0 is set, reading, writing, and execution are not permitted.\n (ii) When 3 is set, reading and writing are permitted, but execution is not permitted.\n (iii) When 7 is set, reading, writing, and execution are permitted.","answer_label":"When 4 is set, only execution is permitted.","answer_id":7648},{"id":1631,"question":"Which of the following is the most suitable system for a design using a state transition diagram?","answer_label":"An operations measurement system for system resources, which measures the operational\r\nstatus of the system resources, and generates a report","answer_id":7654},{"id":1632,"question":"Among UML 2.x, (including 2.0 and later versions) diagrams, which of the following is the most appropriate diagram that can gives a graphic overview of the actors involved in a system, different functions needed by those actors and how these different functions are interacted?","answer_label":"Use Case diagram","answer_id":7658},{"id":1633,"question":"Which of the following is an appropriate description of how to design test cases for a black box test?","answer_label":"Test cases are designed according to the program’s functional specifications and\r\ninterface specifications.","answer_id":7659},{"id":1634,"question":"Which of the following is the purpose of a stress test?","answer_label":"To confirm the operation at the limits of processing capability that is required for a\r\nsystem","answer_id":7664},{"id":1635,"question":"Which of the following is the process of changing a software system in such a way that it does not alter the external behavior of the code yet improves its internal structure?","answer_label":"Refactoring","answer_id":7668},{"id":1636,"question":"Which of the following is an explanation of the spiral model in system development?","answer_label":"This model has four phases: Planning, Risk Analysis, Engineering and Evaluation. A\r\nsoftware project repeatedly passes through these phases in iterations","answer_id":7673},{"id":1637,"question":"Which of the following is an appropriate tool that implements a deliverable-oriented decomposition of a project into smaller components?","answer_label":"Work Breakdown Structure (WBS)","answer_id":7678},{"id":1638,"question":"An IT service is provided under the conditions described below. In order to meet the SLA, which of the following is the maximum allowable downtime (in hours) per month during service hours? Here, the number of business days in a month is 30, and there is no planed service outage for a reason of maintenance or something similar during the service hours.\n\n [Conditions of the SLA]\n • Service hours: 8 a.m. to 10 p.m. on business days\n • Availability: 99.5% or more","answer_label":"2.1","answer_id":7680},{"id":1639,"question":"According to ISO/IEC 20000-1, which of the following is an activity in the PDCA of the Service Delivery Processes?","answer_label":"Evaluating the projected capacity and performance for service requests, new\r\ntechnologies, and upgrade procedures","answer_id":7685},{"id":1640,"question":"According to ISO/IEC 20000-1, which of the following is the appropriate processes that contain change management, configuration management, and release and deployment management?","answer_label":"Control processes","answer_id":7687},{"id":1641,"question":"Which of the following is a measure that enables an operator to surely recognize the occurrence of a system fault?","answer_label":"To provide functions to sound an alarm or light indicator lamps, linked to an alarm or\r\nother message sent to the system console","answer_id":7694},{"id":1642,"question":"Which of the following is an appropriate description concerning an interview conducted during a system audit?","answer_label":"Efforts are made to get documents and records that support the information which has\r\nbeen obtained from the departments under audit through the interview","answer_id":7695},{"id":1643,"question":"Which of the following is an appropriate description concerning the role of a system auditor?","answer_label":"It is to assure the preparation and operations regarding the control of the information\r\nsystem or to give advice on these, from a standpoint of professional standpoint\r\nindependent from the audit target","answer_id":7699},{"id":1644,"question":"Which of the following is an appropriate explanation of BPO?","answer_label":"Contracting out all business processes of a company’s specific department, such as an\r\nadministrative department or call center, to an external service provider, together with\r\nthe operations of a business system","answer_id":7703},{"id":1645,"question":"Which of the following is the cloud-computing service model that allows users to install operating-system images and their application software on the system?","answer_label":"Infrastructure as a service (IaaS)","answer_id":7708},{"id":1646,"question":"According to the ISO/IEC 12207, the activities of the requirements definition process include stakeholder identification, requirements identification, requirements evaluation, and requirements agreement. Among these activities, which of the following is a task that is implemented in requirements identification?","answer_label":"Eliciting requirements from stakeholders, and clarifying constraints and operational\r\nscenarios","answer_id":7713},{"id":1647,"question":"Which of the following is an explanation of the green procurement (sustainable procurement)?","answer_label":"It refers to a preferential purchase of products and services that exert a lower\r\nenvironmental burden","answer_id":7717},{"id":1648,"question":"Which of the following is a technique that is used to identify and evaluate the internal and external factors that are helpful or harmful to the objectives of business organizations or projects?","answer_label":"SWOT analysis","answer_id":7721},{"id":1649,"question":"Which of the following is a technique for classifying company activities into primary activities and support activities, and analyzing which activities generate the profit of the products or services provided to customers?","answer_label":"Value chain analysis","answer_id":7726},{"id":1650,"question":"Which of the following is an explanation of the core competence?","answer_label":"It refers to the predominant abilities in the business area of the company, which cannot\r\nbe imitated by competitors.","answer_id":7730},{"id":1651,"question":"Which of the following is a description of the growth stage of the product life cycle?","answer_label":"It is the stage at which sales increase rapidly. The market becomes active and the\r\ncompetition intensifies because of new market participants.","answer_id":7734},{"id":1652,"question":"Among the different business systems supported by technology, which of the following analyzes routes of distribution, tracking and load tendency?","answer_label":"TMS","answer_id":7737},{"id":1653,"question":"Which of the following is an explanation of the strategy map that is used in the balanced score card?","answer_label":"It shows the cause-and-effect relationship between issues, countermeasures, and goals,\r\non the basis of the four perspectives that consist of finance, customer, internal business\r\nprocess, and learning and growth.","answer_id":7740},{"id":1654,"question":"Which of the following is an appropriate explanation of the concurrent engineering?","answer_label":"A technique that executes processes such as product design and production planning in\r\nparallel during the new product development procedure","answer_id":7745},{"id":1655,"question":"Which of the following is an explanation of CAD?","answer_label":"By using computers, creating drawings of the product design from attribute data\r\nconcerning product shape, composition, etc","answer_id":7748},{"id":1656,"question":"Peter plans to open his own coffee shop. He uses break-even analysis to evaluate the feasibility. He needs to rent a coffee making machine at 20 dollars per day. The average cost of coffee ingredients is 0.40 dollars per cup and the cost of a plastic cup is 0.10 dollars. He sets a price at 1.50 dollars per cup. What is the sales revenue a day at the break-even point?","answer_label":"30","answer_id":7753},{"id":1657,"question":"There is an enterprise whose current liabilities valued 2,400 dollars and the current assets valued 5,000 dollars including inventory assets valued 200 dollars. What is an acid test ratio (in percentage) of the enterprise?","answer_label":"200","answer_id":7757},{"id":1658,"question":"Break-even point of the new product is 12,000 units a month. Fixed cost is 800,000 dollars a month and variable cost is 20 dollars per unit. Based on the information above, which of the following is a selling price of the new product?","answer_label":"86.67","answer_id":7761},{"id":1659,"question":"Which of the following is an appropriate description of the protection scope of software under the WTO’s Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"Both source programs and object programs are protected by the agreement","answer_id":7765},{"id":1756,"question":"In the binary tree shown below, where is the position for a new node of value 17? Here, each circle represents a node of the tree and the number in the circle represents its value.\n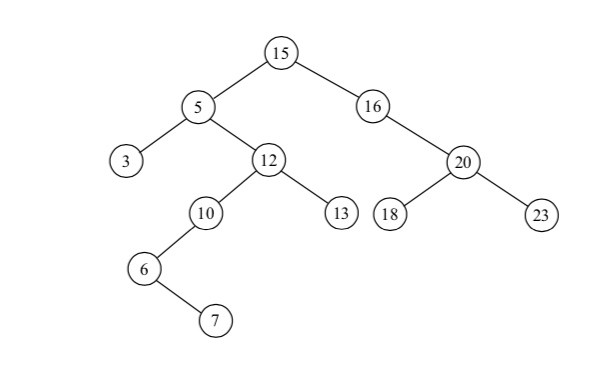","answer_label":"Left child of 18","answer_id":8232},{"id":1757,"question":"Which of the following is the output of the flowchart below?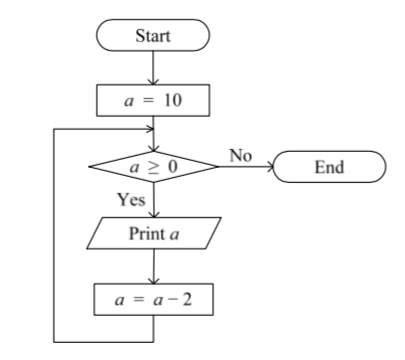","answer_label":"10 8 6 4 2 0","answer_id":8237},{"id":1758,"question":"A recursive function f (n) is defined as follows for any natural number n. What is the value f (5)?","answer_label":"15","answer_id":8241},{"id":1759,"question":"Round robin (with a time allocation of 3 seconds) is used as a scheduling method for three processes in the order of P1, P2, and P3, shown in the table below. What is the total waiting time (in seconds) of P3 that elapses before its execution completes? Here, the arrival time is the time at which a process joins the ready queue.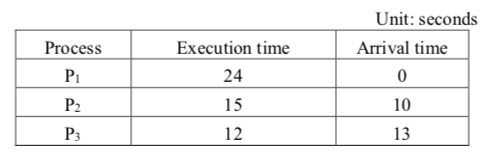","answer_label":"35","answer_id":8243},{"id":1760,"question":"Which of the following is the logical circuit that generates “1” as the output signal Z, only when the input signals X and Y have the same value?\n","answer_label":"c","answer_id":8249},{"id":1761,"question":"Which of the following logic circuits meets the condition described below?\n\n(Condition)\nA light is turned on and off by using switches A and B located at the top and bottom of the stairs. The light can be turned on and off by using one switch, regardless of the status of the other switch.\n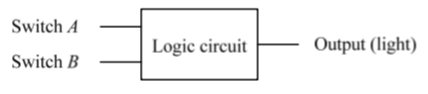","answer_label":"XOR","answer_id":8254},{"id":1762,"question":"Which of the following SQL statements for the table “ShipmentRecord” obtains the largest value?\n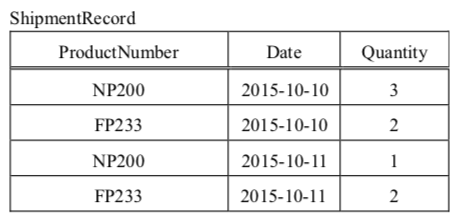","answer_label":"SELECT COUNT(*) FROM ShipmentRecord","answer_id":8256},{"id":1763,"question":"In an IPv4 network, which of the following is the correct combination of an IP address class, its IP address range, and a subnet mask?\n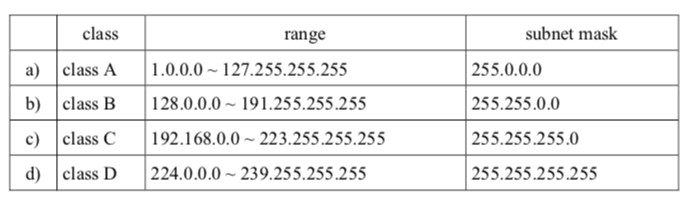","answer_label":"b","answer_id":8260},{"id":1764,"question":"As shown in the list below, there are three types of coupling. Which of the following is the most appropriate combination of the type of coupling?\n\nCoupling A: One module passes an element of control to the other module.\nCoupling B: One module passes the data structure as a parameter to the other module. Coupling C: Two modules have access to the same global data.\n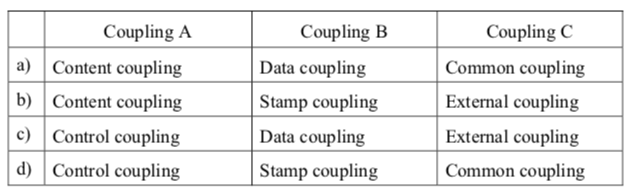","answer_label":"d","answer_id":8266},{"id":1765,"question":"When a software component is tested, which of the following is an appropriate combinations of X and Y ?\n\nX : It calls the software component to be tested.\nY : It is called from the software component to be tested.\n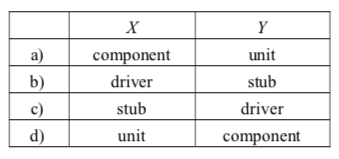","answer_label":"b","answer_id":8268},{"id":1766,"question":"According to PMBOK, which of the following is an appropriate explanation concerning the scope creep in project scope management?","answer_label":"The uncontrolled expansion to product or project scope without adjustments to time,\ncost, and resources.","answer_id":8274},{"id":1767,"question":"As shown in the arrow diagram below, there is a project consisting of eight activities A through G. Which of the following is the appropriate combination of the earliest finish time (EFT) and latest start time (LST) of activity G?\n","answer_label":"c","answer_id":8277},{"id":1768,"question":"According to EVM (Earned Value Management), the budget of a software development project is $10,000 and the project duration is planned for 10 weeks. After 4 weeks, it is revealed that only 30% of the work has been completed against a cost of $4,200. What is the cost performance index?","answer_label":"0.714","answer_id":8282},{"id":1769,"question":"According to the ISO/IEC 20000-1, which of the following is a service delivery process that the service provider shall agree the services to be delivered and shall agree a catalogue of services with the customer?","answer_label":"Service level management","answer_id":8286},{"id":1770,"question":"According to ITIL, which of the following is an activity or process in the Service Transition?","answer_label":"Implementing multiple strategies such as web seminars, newsletters, and visualization in transferring knowledge","answer_id":8290},{"id":1771,"question":"Which of the following is an appropriate description of the relationship between a record of an incident and a record of a problem in IT service management?","answer_label":"The cross-referenced information of the incident that acts as the beginning of the record\nof the problem is included in the record of the problem.","answer_id":8294},{"id":1772,"question":"Which of the following is an appropriate activity that is undertaken by a system auditor who audits access control?","answer_label":"Confirmation of the management status of access control concerning data","answer_id":8295},{"id":1773,"question":"Which of the following is a checkpoint during audit of a control for reducing the risk of system trouble during the application of a software patch?","answer_label":"System operation is properly checked before commencing full-time operations.","answer_id":8301},{"id":1774,"question":"When data sheets issued by a business operations department are entered in a system in an information system department, which of the following is an appropriate task executed by the information system department?","answer_label":"To enable the business operations department to check the processing results of each data sheet, the processing results list is sent to the business operations department.","answer_id":8304},{"id":1775,"question":"Which of the following is an appropriate feasibility evaluation when checking whether the lifetime benefits of the proposed information system is greater than its lifetime costs?","answer_label":"Economic feasibility","answer_id":8307},{"id":1776,"question":"Which of the following is a usage scenario for the adoption of UML as a technique for visualizing business processes?","answer_label":"To represent processes from multiple viewpoints, some purpose-specific modeling methods are used, and each model is depicted by using standardized notation rules for object modeling.","answer_id":8313},{"id":1777,"question":"Among the “four categories” of the enterprise architecture, which of the following completes the list after business architecture, technology architecture, and application architecture?","answer_label":"Data architecture","answer_id":8316},{"id":1778,"question":"Which of the following is an appropriate explanation of EMS?","answer_label":"It refers to the contract production of electronic devices, etc. ordered by other manufacturers.","answer_id":8321},{"id":1779,"question":"Which of the following is an explanation of green procurement?","answer_label":"It refers not only to the fulfillment of the requirements of quality and price, but also to the preferential purchase of products and services that exert a lower environmental burden from companies working towards a reduction in environmental burden.","answer_id":8323},{"id":1780,"question":"Which of the following is an appropriate description of an RFI?","answer_label":"It is a document used to request information concerning computerization from prospective suppliers such as system vendors.","answer_id":8330},{"id":1781,"question":"Companies are classified based on their competitive position in the market. There are typically four types: leader, challenger, follower, and nicher. Which of the following is an appropriate characteristic of the strategy of a leader?","answer_label":"Proposing a new product and its usage method to the consumer to expand the total demand while maintaining or expanding the market share","answer_id":8334},{"id":1782,"question":"Which of the following is a marketing technique to create demands from consumers by using advertisements that improve the brand image of a company or a product?","answer_label":"Pull strategy","answer_id":8337},{"id":1783,"question":"PEST analysis is used for analyzing the external environment in determining a business strategy. What are the external environmental factors the PEST analysis analyzes?","answer_label":"Politics, Economics, Society, Technology","answer_id":8339},{"id":1784,"question":"Which of the following is an explanation of the IoT (Internet of Things)?","answer_label":"It refers to the installation of communication functionality to various objects, in addition to information and communication devices, and enabling automatic recognition or remote measurement by connecting these to the Internet, to achieve high-level decision-making services and automated control through the collection and analysis of large volumes of data.","answer_id":8346},{"id":1785,"question":"Which of the following is an explanation of benchmarking used for corporate management?","answer_label":"It refers to a qualitative and quantitative understanding of a company’s own products, services, and operation through comparison with those of competitors or advanced companies.","answer_id":8347},{"id":1786,"question":"Which of the following is an explanation of the long tail?","answer_label":"It is effective in reducing the risk of opportunity loss in an online shop that uses the Internet by lining up a broad range of items, including products for which sales opportunities are few.","answer_id":8354},{"id":1787,"question":"Which of the following performs processing according to steps (1) through (3)?\n\n(1) Based on the types and quantities as well as the parts list of the product planned to be manufactured in a fixed period of time in the future, the required quantity of components is calculated.\n\n(2) The net order quantity of each component is calculated from the amount of inventory that can be allocated.\n\n(3) The ordering time of the components is determined while considering the manufacturing and procurement lead time.","answer_label":"MRP (Material Requirements Planning)","answer_id":8358},{"id":1788,"question":"Which of the following is the procurement process that enables suppliers to bid against one another on the Internet to sell their products or services under the conditions specified by a general customer?","answer_label":"Reverse auction","answer_id":8361},{"id":1789,"question":"Which of the following is a management organization that has a characteristic of both project and functional organizations to flexibly respond to changes in the business environment?","answer_label":"Matrix organization","answer_id":8366},{"id":1790,"question":"Company A has two media plans. One plan is for a series of 30-second radio advertisements (ads) and the other is for 60-second TV ads. Exposure is rated in points. The company is considering an exposure of at least 60 points in the city and at most 40 points outside the city. The table below shows the cost and exposure of both TV and radio ads. Which of the following is the set of expressions that can determine the number of media ads to minimize the total cost?\n\n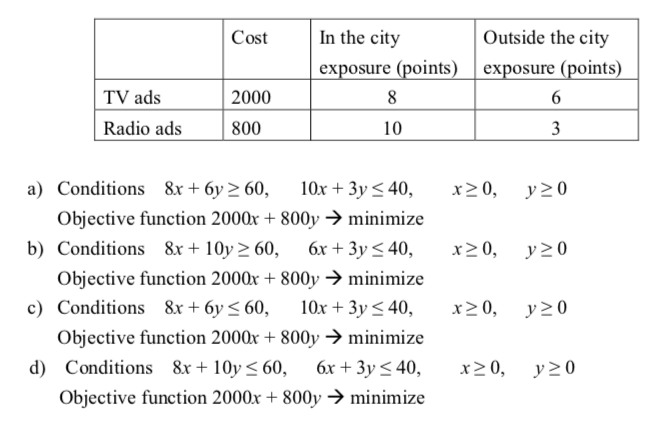","answer_label":"b","answer_id":8368},{"id":1791,"question":"When the FIFO method is applied to the purchase and selling record shown below, what is the inventory value at the end of March?\n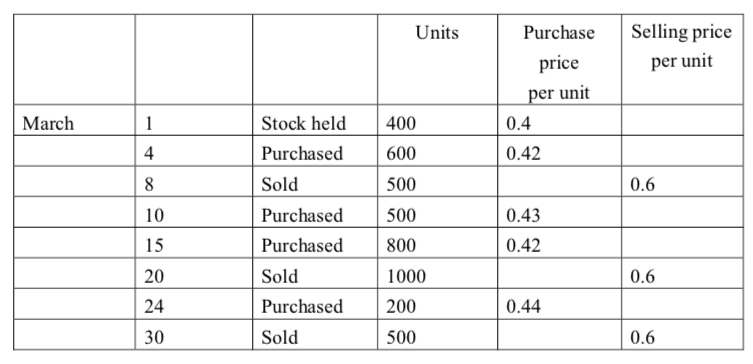","answer_label":"214","answer_id":8371},{"id":1793,"question":"Which of the following is a method of making decisions based on the discount rate at which the net present value of the payback amount and the investment amount are equal?","answer_label":"Internal Rate of Return method","answer_id":8379},{"id":1794,"question":"Which of the following is not protected by “copyright” that is based on the World Trade Organization’s Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"Programming language and its conventions","answer_id":8385},{"id":1796,"question":"Which of the following is the appropriate binary fraction that is equivalent to the decimal value 5.525? Here, the binary string enclosed in parentheses is repeated infinitely.","answer_label":"101.100(0011)","answer_id":8394},{"id":1797,"question":"When three apples are removed at random from a box that contains four green apples and eight red apples, what is the probability that the first two apples are green and the third (or last) apple is red? Here, once an apple is removed, it is not put back into the box.","answer_label":"4/55","answer_id":8397},{"id":1798,"question":"For a balanced binary search tree, which of the following is the asymptotic time complexity of the search operation for a set of “n2n” data elements? Here, “O( )” denotes the order of the algorithm’s running time, and “n ” is sufficiently large.\n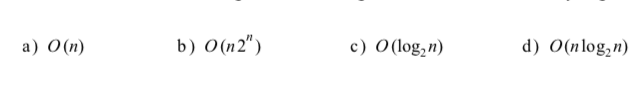","answer_label":"a","answer_id":8399},{"id":1799,"question":"When the condition and inferences are given as shown below, which of the following is the appropriate combination that supports the validity of the two inferences?\nCondition: Inference 1: Inference 2:\nIf it rains, then the street will be wet.\nThe street is not wet, and therefore, it did not rain. It did not rain, and therefore, the street is not wet.\n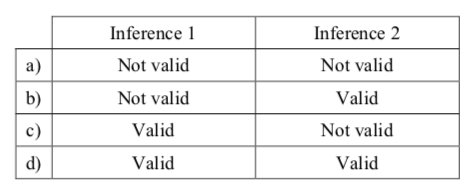","answer_label":"c","answer_id":8405},{"id":1800,"question":"As shown below, there is a binary search tree where each node contains a country name and is ordered alphabetically so that Mongolia comes before Philippines, Myanmar comes before Philippines but after Mongolia, and so on. Which of the following is the appropriate order of the country names that can create this binary search tree by inserting each country name in an empty tree?\n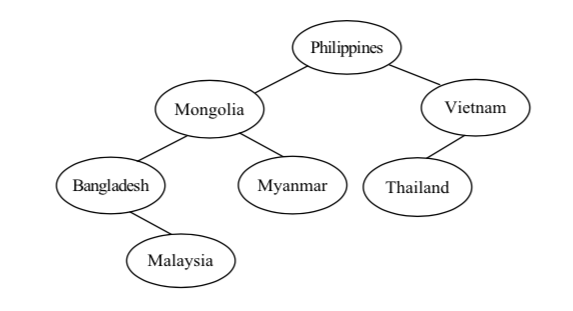","answer_label":"Philippines, Vietnam, Mongolia, Thailand, Bangladesh, Myanmar, Malaysia","answer_id":8410},{"id":1801,"question":"In a real time system, which of the following is the data structure that is most suitable for the scheduling of multiple tasks with different priority levels?","answer_label":"Linked list","answer_id":8413},{"id":1802,"question":"When the function M(n) is defined as shown below, what is the value of M(97)?\n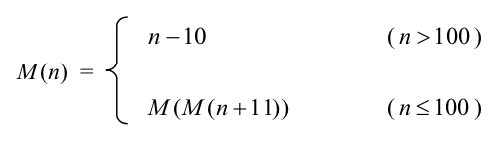","answer_label":"91","answer_id":8417},{"id":1803,"question":"As shown in the table below, there are five items A through E. Each item cannot be divided into smaller pieces. When a knapsack with a maximum volume of 7 units is available for carrying the items, which of the following is a set of items to be packed in the knapsack so that the total price can be maximized?\n","answer_label":"B,E","answer_id":8421},{"id":1804,"question":"As shown in the table below, there are a total of 86 coins that are composed of five types of coins. Of those 86 coins, 60 coins are picked up so that the total value can be maximized. What is the total value in dollars? Here, 100 cents are equivalent to 1 dollar.\n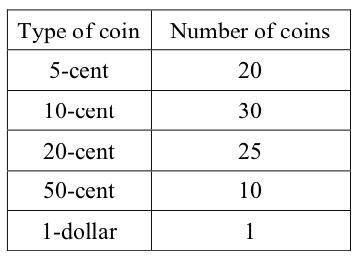","answer_label":"13.4","answer_id":8426},{"id":1805,"question":"As shown the figure and table below, there are two types of CPUs X and Y that have the same configuration except that the access times of cache memory and main memory are different from each other. All other conditions of the two CPUs are the same.\nWhen a certain program is executed on both CPU X and CPU Y, the processing time of each CPU is the same. Under these conditions, what is the hit ratio of the cache memory? Here, there are no effects from other than CPU processing.\n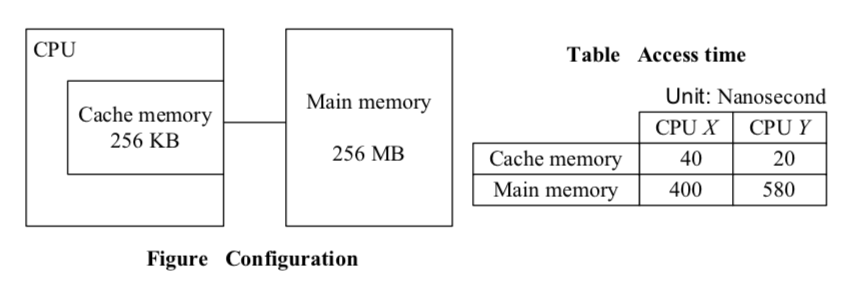","answer_label":"0.90","answer_id":8428},{"id":1806,"question":"There exists a system that requires the execution of 800,000 instructions per transaction. When the processor performance is 200 MIPS and the utilization rate of the processor is 80%, what is the processing power in transactions per second?","answer_label":"200","answer_id":8432},{"id":1807,"question":"Which of the following is an appropriate purpose of the parity check of a memory module?","answer_label":"To detect the occurrence of an error during reading","answer_id":8436},{"id":1808,"question":"Which of the following is an appropriate explanation of a capacitive touch panel?","answer_label":"An electric field is formed on the surface, and the touched position is detected on the basis of the change in the surface electric charge.","answer_id":8439},{"id":1809,"question":"Which of the following is the most appropriate method for the implementation of a fault tolerant system?","answer_label":"The system is multiplexed with two or more computers instead of using a single computer.","answer_id":8445},{"id":1810,"question":"Which of the following is the most appropriate explanation of a benchmark test for a computer system?","answer_label":"The processing performance of a system is compared with other systems in terms of scores obtained by executing software for measurement.","answer_id":8449},{"id":1811,"question":"There exist the same two devices, each with an MTBF of 45 hours and an MTTR of 5 hours. What is the availability of a system that connects these two devices in series?","answer_label":"0.81","answer_id":8451},{"id":1812,"question":"Among the descriptions concerning process scheduling, which of the following is an appropriate explanation of the round robin method?","answer_label":"CPU resources are allocated to the first executable process in the queue when an interval-timer interrupt is generated.","answer_id":8457},{"id":1813,"question":"When SRT (Shortest Remaining Time), also known as SRTF (Shortest Remaining Time First), is used as a scheduling method for three processes P1 through P3 shown in the table below, what is the total waiting time (in seconds) of P2 that elapses before its execution completion?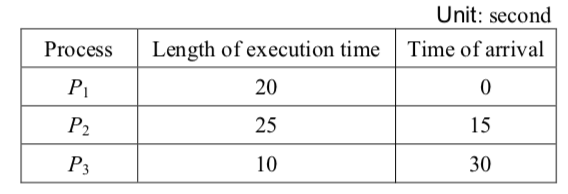","answer_label":"15","answer_id":8461},{"id":1814,"question":"Which of the following is an explanation of the function of an archiver that is one of the data management utilities?","answer_label":"Compiling several files into one file, or returning a file to its original condition in order to perform data backup and distribution","answer_id":8463},{"id":1815,"question":"Which of the following is an appropriate explanation of optimization in a compiler?","answer_label":"Generating an object code with improved run-time processing efficiency by analyzing the source code","answer_id":8470},{"id":1816,"question":"Which of the following is classified as a function of a static test tool?","answer_label":"Detecting an error in a program by analyzing the source code","answer_id":8472},{"id":1817,"question":"The logic circuit below shows a JK flip-flop. Which of the following is the appropriate truth table for the JK flip-flop. Here, the state of each output signal is affected only when the clock signal CLK changes from 0 to 1. “No Change” means that each output signal maintains its previous state, and “Toggle” means that each output signal switches (or toggles) its state “from 0 to 1” or “from 1 to 0.”\n","answer_label":"a","answer_id":8475},{"id":1818,"question":"A D/A (digital-to-analog) converter with a resolution of 8 bits generates the output voltage 0 volts for the digital input value 0, and the output voltage 2.5 volts for the digital input value 128. When the lowest one bit of the digital input value is changed, which of the following is the change (in volts) of the output voltage that is generated by the D/A converter?","answer_label":"2.5/128","answer_id":8479},{"id":1819,"question":"Which of the following is a memory module that uses a flip-flop circuit in a memory cell?","answer_label":"SRAM","answer_id":8486},{"id":1820,"question":"Which of the following is the function of a human interface that is used for reducing the number of operations of a user who frequently performs routine work?","answer_label":"A macro function by which a series of commands is grouped together","answer_id":8490},{"id":1821,"question":"Which of the following is a tag-based very flexible image file format that can be lossless or lossy, and is widely used for the interchange of digital image data among graphic artists, photographers, and the publishing industry?","answer_label":"TIFF","answer_id":8494},{"id":1822,"question":"In a relational database table, which of the following is a column or a combination of columns whose values are defined by the primary key of another table in order to maintain referential integrity in the database?","answer_label":"Foreign key","answer_id":8496},{"id":1823,"question":"There is a record that consists of eight attributes a through h as shown below. The primary key of the record is the combination of attributes a and b. Attributes h, c, and f\ncan be determined by attributes a, b, and e respectively. Which of the following is the third normal form of this record?\n\n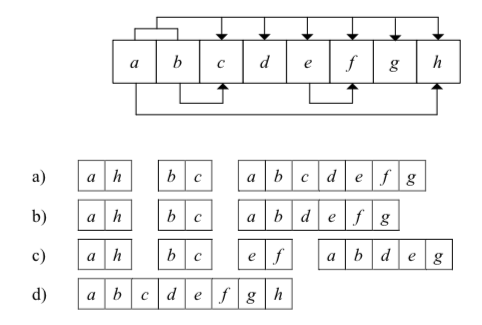","answer_label":"c","answer_id":8501},{"id":1824,"question":"Which of the following is an appropriate description of the ACID (Atomicity, Consistency, Isolation, and Durability) properties that are considered to be the key transaction processing features of a database management system (DBMS)?","answer_label":"Durability refers to the guarantee that once the user has been notified of success, the transaction persists, and is not undone.","answer_id":8505},{"id":1825,"question":"When there are two relational database tables A and B as shown below, which of the following is the appropriate table that shows the result of the relational operation A ÷ B ?\n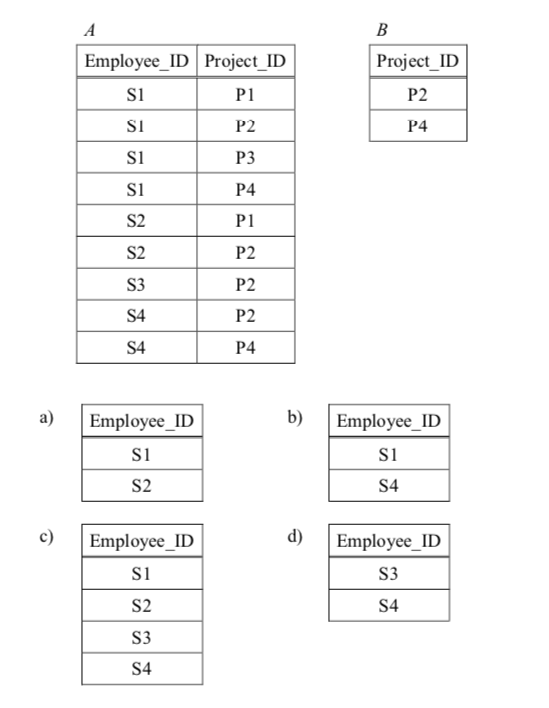","answer_label":"b","answer_id":8508},{"id":1826,"question":"For the “Product” table shown below, a transaction that executes the SQL statement below terminates abnormally because of the occurrence of a deadlock. Which of the following is the “Product” table after the abnormal termination? Here, other transactions use the “Product” table as reference but do not update it.\n","answer_label":"b","answer_id":8512},{"id":1827,"question":"In the Internet environment, a computer is able to send the ping command “ping 11.22.33.44” to the web server (e.g., www.xyz.com) of Company XYZ and then receive an echo reply message successfully. Also, the computer is able to browse the website by using URL “http://11.22.33.44”, but cannot browse the same website by using “http://www.xyz.com”. In the OSI basic reference model, which of the following is the layer that is most likely to be responsible for such a problem?","answer_label":"Application layer","answer_id":8515},{"id":1828,"question":"In the IPv4 addressing scheme, when the subnet mask \"255.255.255.224\" is used for Class C, which of the following is the maximum number of effective hosts per subnet, excluding the network and broadcast addresses?","answer_label":"30","answer_id":8520},{"id":1830,"question":"A system administrator has a plan to monitor a network in order to evaluate which employees are using an excessive amount of bandwidth on peer-to-peer sharing services. Which of the following is the most appropriate technique for achieving such a purpose?","answer_label":"Packet sniffing","answer_id":8528},{"id":1831,"question":"Which of the following is an appropriate description concerning “HTTP cookie”?","answer_label":"HTTP cookies are used to contain data sent from a web server as plain text only.","answer_id":8532},{"id":1832,"question":"In the context of information security defined by ISO/IEC 27001, which of the following is the property of safeguarding the accuracy and completeness of information assets?","answer_label":"Integrity","answer_id":8538},{"id":1833,"question":"Which of the following is an appropriate characteristic of MAC (Message Authentication Code) that is used to authenticate a message and provide its integrity in cryptography?","answer_label":"It is constructed from cryptographic hash functions.","answer_id":8540},{"id":1834,"question":"Which of the following is a characteristic of the hash function that is used for a digital signature?","answer_label":"It is difficult to restore an original message from the message digest.","answer_id":8544},{"id":1835,"question":"Which of the following is the salami technique that is used in computer crime?","answer_label":"It is a technique where theft is performed in small increments from many assets so that this fraudulent behavior is not noticed.","answer_id":8550},{"id":1836,"question":"Mr. X sends an e-mail to Mr. Y by using the Internet. The contents of the e-mail must be kept confidential, so Mr. X uses public key cryptography to encrypt the e-mail. Which of the following is the key that is used to encrypt the contents of the e-mail?","answer_label":"Mr. Y ’s public key","answer_id":8554},{"id":1837,"question":"Which of the following is the security attack that is used for an illegal attempt to manipulate the people of an organization into divulging the password and confidential information under the pretext of an emergency?","answer_label":"Social engineering","answer_id":8556},{"id":1838,"question":"Which of the following is a feature that is incorporated by an attacker to enter the network or server of a company?","answer_label":"Back door","answer_id":8559},{"id":1839,"question":"Which of the following is an explanation of BYOD (Bring Your Own Device)","answer_label":"An employee brings his or her own personal terminal to the office to use for work, which causes an increase in security risks such as virus infections caused by inadequate security settings.","answer_id":8564},{"id":1840,"question":"Which of the following is a mechanism by which a company or organization centrally manages the usage status of smartphones or such other devices that are lent to its staff members by making integrated settings according to the security policy, or by delivering business applications?","answer_label":"MDM (Mobile Device Management)","answer_id":8570},{"id":1841,"question":"Which of the following is an appropriate preventive measure against malware that is taken on a client PC?","answer_label":"In order that no virus exploits a vulnerability and infects a PC, revised software modules or patches are appropriately applied to the OS and applications.","answer_id":8574},{"id":1842,"question":"In the UML diagram shown below, which of the following is described in the blank box?\n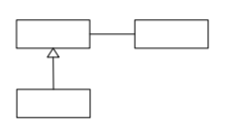","answer_label":"Class name","answer_id":8577},{"id":1843,"question":"In object-oriented development, it is possible to make settings such that the user is not affected even if the internal structure of an object is changed. Thus, it is possible to create a situation where the user of an object is not necessarily aware of the internal structure of the object. Which of the following is the term that represents the concept of implementing such development?","answer_label":"Encapsulation","answer_id":8580},{"id":1844,"question":"In software development, which of the following is an appropriate explanation of a test that uses stubs?","answer_label":"When a top-down test is performed, a dummy lower-level module that is called by the upper-level module is prepared to stand in for an unfinished portion of the program.","answer_id":8585},{"id":1845,"question":"Which of the following is an appropriate explanation of the state transition diagram that is used for requirements analysis and design in system development?","answer_label":"The triggers that change the state, such as the passage of time and the change in control\nsignal, and the operations performed as a result are described.","answer_id":8590},{"id":1846,"question":"Among the software development activities, which of the following is an explanation of refactoring?","answer_label":"In order to improve the maintainability of a program, its internal structure is modified without any change of the external specifications.","answer_id":8591},{"id":1847,"question":"Each letter (i.e., P, D, C, and A) of the “PDCA” cycle used for progress management of system development and quality management of software is the first letter of the corresponding word. Which of the following is the word that is represented by the third letter “C”?","answer_label":"Check","answer_id":8597},{"id":1848,"question":"Which of the following is the critical path of the project activities shown in the arrow diagram below?\n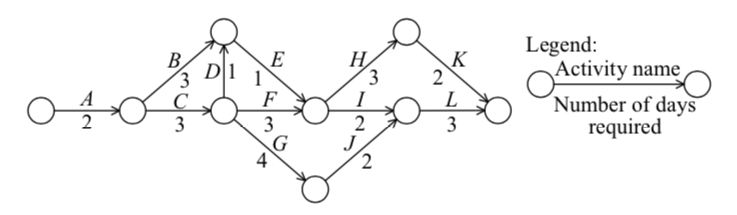","answer_label":"A→C→G→J→L","answer_id":8602},{"id":1849,"question":"According to ITIL (IT Infrastructure Library), CSA (Configuration Status Accounting) is the recording and reporting of all current and historical data concerned with each CI\n(Configuration Item) throughout its life-cycle. activity that is performed as part of CSA?","answer_label":"Performing integrated change control","answer_id":8606},{"id":1850,"question":"According to “A Guide to the Project Management Body of Knowledge” (PMBOK Guide), which of the following is the knowledge area that includes the processes and activities to identify, define, combine, unify, and coordinate the various processes and project management activities within the Project Management Process Groups?","answer_label":"Project integration management","answer_id":8608},{"id":1851,"question":"Which of the following is the most appropriate characteristic of the “big bang” migration method that is one of the system migration methods?","answer_label":"The problems that occur during migration to the new system have a big impact.","answer_id":8614},{"id":1852,"question":"Which of the following is an explanation of a “known error” in IT service management?","answer_label":"A problem whose root cause is already identified or for which a workaround exists","answer_id":8616},{"id":1853,"question":"Which of the following decimal values is equivalent to a hexadecimal fraction 0.B1?\n\n","answer_label":"d","answer_id":8622},{"id":1854,"question":"Alice and Mary take a math exam. The probability of passing this exam for Alice and Mary is 2/3 and 3/5, respectively. What is the probability that at least one of them will pass the exam?","answer_label":"13/15","answer_id":8626},{"id":1855,"question":"What is the distribution of arrival rate in an M/M/1 queuing model","answer_label":"Poisson distribution","answer_id":8630},{"id":1856,"question":"Typical list data type implementations are either array based or pointer based. Which of the following describes a characteristic of array-based implementations?","answer_label":"Regardless of the actual number of elements in a list, some space may remain unused as\nthe space for storing the maximum number of elements is pre-allocated.","answer_id":8634},{"id":1857,"question":"In a CPU with a four (4) stage pipeline composed of fetch, decode, execute, and write back, each stage takes 10, 6, 8, and 8 ns, respectively. Which of the following is an approximate average instruction execution time in nanoseconds (ns) in the CPU? Here, the number of instructions to be executed is sufficiently large. In addition, the overhead for the pipelining process is negligible, and the latency impact from all hazards is ignored.","answer_label":"10","answer_id":8637},{"id":1858,"question":"Which of the following is the computer architecture where a processor executes the same\nInstruction on multiple data?","answer_label":"SIMD","answer_id":8641},{"id":1859,"question":"Which of the following is an addressing mode that provides an offset to the program counter (PC) content to determine the address of the operand?","answer_label":"Relative addressing mode","answer_id":8646},{"id":1860,"question":"Which of the following is used to translate a logical address generated by a CPU into a physical address?","answer_label":"Memory Management Unit (MMU)","answer_id":8649},{"id":1861,"question":"Which of the following is an appropriate description concerning cache memory?","answer_label":"Multiprocessors where each has a cache memory need to synchronize values within the\ncache to maintain coherency.","answer_id":8652},{"id":1862,"question":"Which of the following is an appropriate description of throughput?","answer_label":"Spooling, which involves temporarily saving the output to a printer in a hard disk, is\nuseful in improving throughput.","answer_id":8657},{"id":1863,"question":"Which of the following is the mean time between failures (MTBF) value of the entire system where unit A and unit B are connected in series and both units operate as one system? The MTBF value of unit A and unit B is 200 and 300 hours, respectively.","answer_label":"250","answer_id":8660},{"id":1864,"question":"When the multiplicity of processing is increased in the virtual memory of a computer system, page-in and page-out operations occur very frequently, and the response speed of the system decreases suddenly. What is this phenomenon called?","answer_label":"Thrashing","answer_id":8666},{"id":1865,"question":"A company performs a full backup every Sunday night and differential backups every night other than Sunday night. If the failure occurs on Wednesday morning, which of the following backups is least needed to restore the system?","answer_label":"The latest full and the latest differential backups from Tuesday.","answer_id":8669},{"id":1866,"question":"Which of the following is an appropriate explanation for a non-preemptive scheduling Method?","answer_label":"A task cannot move to a running state until another task in the running state either moves to the waiting state by itself or finishes.","answer_id":8671},{"id":1867,"question":"According to the Open Source Definition by OSI (Open Source Initiative), which of the following is the appropriate description concerning open source licensing?","answer_label":"The license requires that the source code of a program must be made available either for free or at a reasonable reproduction cost.","answer_id":8678},{"id":1868,"question":"Which of the following is a sequential circuit that has two (2) stable states?","answer_label":"Flip-flop","answer_id":8680},{"id":1869,"question":"Which of the following is an explanation of texture mapping?","answer_label":"It represents surface characteristics by pasting an image onto the surface of a\nthree-dimensional object.","answer_id":8686},{"id":1870,"question":"Which of the following is an appropriate purpose for adopting a three-layer schema architecture for DBMS?","answer_label":"To derive a new table from a source table through a relational operation as if the new table actually existed","answer_id":8688},{"id":1871,"question":"Which of the following is more suitable for outline fonts than for bitmap fonts?","answer_label":"To enlarge characters by a given scale factor","answer_id":8694},{"id":1872,"question":"Which of the following is an appropriate method used to remove data redundancy in relational database systems?","answer_label":"Normalization","answer_id":8698},{"id":1873,"question":"In a relation schema R = ( A, B, C, D, E ) , the following functional dependencies are held:\n\nA → BC\n\nCD → E\n\nB → D\n\nE → A\n\nWhich of the following is a combination of two candidate keys for R ?","answer_label":"A and E","answer_id":8699},{"id":1874,"question":"Which of the following is the main purpose of transaction support in a database management system?","answer_label":"To ensure that either all the updates corresponding to a given transaction are made or\nnone of them is made","answer_id":8703},{"id":1875,"question":"Which of the following is a data link layer function that enables receivers to control the amount of data to be received from the senders?","answer_label":"Flow control","answer_id":8709},{"id":1876,"question":"TCP/IP is a layered set of communication protocols consisting of the Network Interface layer, the Internet layer, the Transport layer, and the Application layer. Which of the following is a combination of the Transport layer protocols?","answer_label":"TCP, UDP","answer_id":8714},{"id":1877,"question":"Which of the following is responsible for converting a domain name to a corresponding IP address?","answer_label":"DHCP server","answer_id":8715},{"id":1878,"question":"Which of the following is an appropriate description of Transmission Control Protocol (TCP)?","answer_label":"It is an end-to-end protocol but does not have any mechanism for congestion control.","answer_id":8720},{"id":1879,"question":"On the Internet, sometimes when one tries to load a Web page by specifying a URL like http://www.jitec.ipa.go.jp/, the page does not show up and an error page is shown instead.\nHowever, one can browse this page correctly by specifying its IP address like this: http://118.151.146.137/. Which of the following TCP/IP layer is responsible for this Problem?","answer_label":"Application layer","answer_id":8723},{"id":1880,"question":"Which of the following is a technique that is classified as social engineering?","answer_label":"Acquiring a password by calling a user and pretending to be a system administrator","answer_id":8727},{"id":1881,"question":"When Mr. A , who has a digital certificate, uses an e-mail to place an order with store B , he uses his own private key and digitally signs the e-mail. Store B then uses Mr. A ’s public key to confirm the signature. Which of the following can be achieved using this method? Here, only Mr. A can use his private key.","answer_label":"It can be confirmed that the order arriving at store B is an order from Mr. A.","answer_id":8732},{"id":1882,"question":"Which of the following is a description of measures against information leakage?","answer_label":"The contents of the hard disk of a notebook PC are encrypted.","answer_id":8737},{"id":1883,"question":"Which of the following is a purpose of using a WAF (Web Application Firewall)?","answer_label":"An attack on a vulnerability attributed to a Web server and a Web application is blocked.","answer_id":8739},{"id":1884,"question":"Which of the following is an explanation of the pattern-matching method used by antivirus software?","answer_label":"A virus is detected through comparison with the signature of an already-known virus.","answer_id":8746},{"id":1885,"question":"Which of the following can be implemented with the functions of HTTPS (HTTP over SSL/TLS)?","answer_label":"Encryption of communication between a Web server and a browser","answer_id":8748},{"id":1886,"question":"According to ISO/IEC 25010 (Systems and software engineering - Systems and software Quality Requirements and Evaluation (SQuaRE) - System and software quality models), which of the following is an appropriate quality characteristic that means the degree to which a product or system provides functions that meet stated and implied needs when used under specified conditions?","answer_label":"Functional suitability","answer_id":8751},{"id":1887,"question":"In unit testing, which of the following activities is part of “white box testing”?","answer_label":"Condition testing","answer_id":8756},{"id":1888,"question":"Which of the following is a mechanism that allows several subclasses of a common parent class to override the same method with different behaviors?","answer_label":"Polymorphism","answer_id":8762},{"id":1889,"question":"The integration test for a software that is composed of a set of modules arranged in a hierarchical structure is performed from a low-level module. In such a case, which of the following is a test module used as a substitute for a higher level module?","answer_label":"Driver","answer_id":8763},{"id":1890,"question":"Which of the following is a term for the process of generating a Unified Modeling Language (UML) class diagram from a program?","answer_label":"Reverse engineering","answer_id":8770},{"id":1891,"question":"Which of the following is an action that is carried out during the work breakdown structure (WBS) creation process in project scope management?","answer_label":"Subdividing the work hierarchically","answer_id":8774},{"id":1892,"question":"A company is creating a development plan for job A. The first developer can perform this job alone in 10 days. Moreover, the first developer can perform this job in 6 days with the second developer. How many days will be required for the second developer to perform this job alone? Here, owing to communication, the work efficiency for each developer is reduced by 10% and the decimal needs to be rounded up.","answer_label":"12","answer_id":8777},{"id":1893,"question":"According to ISO/IEC 20000-1 (Information technology - Service management -\nPart 1: Service management system requirements), which of the following is an appropriate\ndescription of problem management?","answer_label":"It is a process used to identify the root cause of an incident, minimize the adverse impact\nof the incident, and prevent it from occurring again.","answer_id":8780},{"id":1894,"question":"Which of the following term indicates the amount of data transactions allowed to be lost\nafter a downtime occurs?","answer_label":"Recovery Point Objective (RPO)","answer_id":8784},{"id":1895,"question":"In the Information Technology Infrastructure Library (ITIL), lowering an indicator that represents maintainability is given as an example of a key performance indicator (KPI) for availability management. Which of the following corresponds to this indicator?","answer_label":"Mean time to restore services","answer_id":8789},{"id":1896,"question":"Among the items to be written into an audit report by a system auditor, which of the following deviates from the scope of work of an auditor?","answer_label":"Ordering improvements","answer_id":8792},{"id":1897,"question":"When software asset management is audited, which of the following is the most appropriate point to be checked?","answer_label":"Checking to see whether evidence, such as a software license certificate, is properly\nRetained","answer_id":8796},{"id":1898,"question":"Which of the following is an appropriate sequence of procedure for creating a business Model?\n\nA. Associating a business process with an existing organization\n\nB. Clarifying a business process\n\nC. Associating a business process with an information system\n\nD. Clarifying a data class (information model)\n\nE. Associating a business process with a data class","answer_label":"B → D → E → C → A","answer_id":8800},{"id":1899,"question":"Which of the following is an appropriate combination of layers managed by vendors when using IaaS?","answer_label":"Virtualization, Servers, Storage, Networking","answer_id":8806},{"id":1900,"question":"An apparel manufacturing and selling company is evaluated by value chain analysis. When activities in the company are classified into inbound logistics, productions, outbound logistics, sales/marketing, and services, which of the following is classified as inbound logistics?","answer_label":"Activity to order material, carry out inspections, and manage inventory","answer_id":8808},{"id":1901,"question":"A company has planned to provide a product with a fixed cost of $128,000, a variable cost per unit of $48, and a selling price per unit of $80. Which of the following is the point of sales ($) to become break-even?","answer_label":"320000","answer_id":8812},{"id":1902,"question":"Which of the following is a criminal act related to a computer virus according to the Convention on Cybercrime?","answer_label":"A person who found a virus that was created by a stranger stores the virus for the purpose that he/she can later run it on another person’s computer.","answer_id":8817},{"id":1903,"question":"Which of the following is an explanation of consumer generated media (CGM)?","answer_label":"It enables the distribution of digital content that an individual reader creates, and it enables sharing of such content between users.","answer_id":8820},{"id":2015,"question":"Which of the following is an appropriate method of authenticating users by using a password?","answer_label":"The password is converted to a hash value and registered, and the password entered during\nauthentication is converted by the hash function and compared.","answer_id":9220},{"id":2016,"question":"When malware that has made a successful intrusion into a PC communicates with a command-and-control server on the Internet, which of the following is a reason for using the TCP port number 80 as the destination port in most cases?","answer_label":"As this port is used for browsing websites, there is a high probability that communication\nis allowed by the firewall.","answer_id":9222},{"id":2017,"question":"Which of the following is an appropriate description of risk assessment?","answer_label":"The priority order of the response to risks is determined by the size of the risk based on\nthe expected amount of loss and occurrence probability.","answer_id":9229},{"id":2018,"question":"There is a network that is divided into three (3) segments, namely, an external segment, a demilitarized zone (DMZ), and an internal network by one (1) firewall. In the network, when a service for users is published on the Internet by using a system consisting of a Web server and a database (DB) server containing critical data, which of the following is the most appropriate method of server installation for protecting important data from unauthorized access from the Internet? Here, only a specific protocol is allowed for communication between the external segment and the DMZ, and between the DMZ and the internal network by the firewall, and communication between the external segment and the internal network is not allowed","answer_label":"The Web server is installed in the DMZ, and the DB server is installed in an internal\nnetwork","answer_id":9233},{"id":2019,"question":"Which of the following is the most appropriate sentence describing the difference between intermediate COCOMO and COCOMO II?","answer_label":"Intermediate COCOMO consists of one overall model based on lines of code, whereas\nCOCOMO II consists of three different models, depending on the available knowledge\nof product to be built.","answer_id":9234},{"id":2020,"question":"Which of the following is subject to system audits that evaluate and verify internal control related to IT?","answer_label":"The methods for ensuring accuracy in the processes of input and update of the database\nbeing done by the sales department","answer_id":9238},{"id":2021,"question":"Which of the following is an appropriate description of cloud computing?","answer_label":"It is a model for enabling ubiquitous, convenient, on-demand access to a shared pool of\nconfigurable computing resources","answer_id":9244},{"id":2022,"question":"Which of the following is a work that is performed when nonfunctional requirements are defined?","answer_label":"Creating development criteria and standards based on programming language used in\nsystem development","answer_id":9247},{"id":2023,"question":"Which of the following is an appropriate explanation of the “Question mark” product in the product portfolio management (PPM) matrix?","answer_label":"It needs significant investments to nurture owing to a small rate of market share and a\nhigh rate of market growth.","answer_id":9252},{"id":2024,"question":"Which of the following is a price-setting method based on cost-plus pricing?","answer_label":"On the basis of manufacturing cost and operating expenses, the price is set by\nincorporating a desired margin.","answer_id":9255},{"id":2025,"question":"Which of the following is an explanation of an e-marketplace?","answer_label":"It is a method in which many sellers and buyers meet in a market set up on the Internet\nand trade directly without an intermediate distributor.","answer_id":9258},{"id":2026,"question":"Which of the following is an explanation of a smart grid?","answer_label":"It is a system that aims at the utilization of recyclable energy, supply of stable electric\npower, and optimum demand adjustment through the integrated control of power\ngeneration and power consumption based on communication and information-processing\ntechnology.","answer_id":9262},{"id":2027,"question":"There is a language defined by a context-free grammar with the production rules below:\n\nE $\\to$ T + E | T\n\nT $\\to$ F * T | F\n\nF $\\to$ ( E ) | C\n\nC $\\to$ 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 \n\nIn this grammar, non-terminals are E, T, F, and C; terminals are parentheses, plus sign,\nasterisk, and numbers; E is the start symbol. Which of the following shows that the\nexpression 7 + 3 * (6 + 4) is a sentence of this language?","answer_label":"E $\\to$ 7 + 3 * (F + T)","answer_id":9266},{"id":2028,"question":"What is the value of the arithmetic expression resulting from an in-order traversal of the binary tree below?\n\n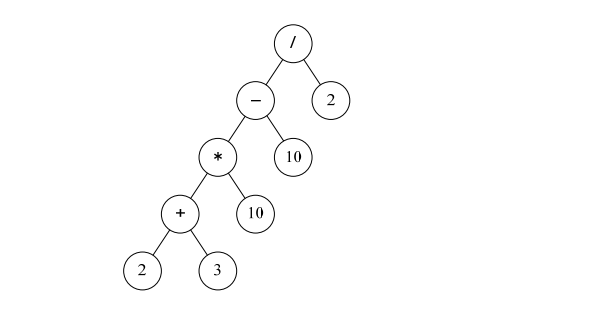","answer_label":"20","answer_id":9271},{"id":2029,"question":"Which of the following is a technique of segmenting and storing data on multiple hard disks as shown in the figure? Here, b0 through b15 show the sequence in which the data are stored to the data disks on a bit-by-bit basis. \n\n","answer_label":"Striping","answer_id":9277},{"id":2030,"question":"There is a system composed of two (2) CPUs, and the CPU that is not in use is assigned to a task for which there is an execution request. When two (2) tasks A and B are run on this system, these tasks exclusively use a common resource R. The figure below shows the usage periods of the CPUs and resource R for tasks A and B, and the order in which the tasks are run. When the execution of both the tasks is started simultaneously, how much time, in milliseconds, is required until the completion of processing of both the tasks? Here, both the CPU and resource R are available when tasks A and B are started.\n\n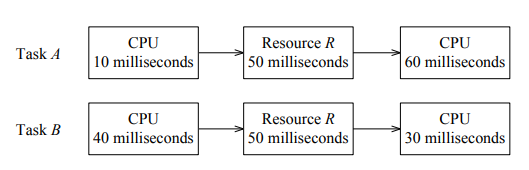","answer_label":"140","answer_id":9279},{"id":2031,"question":"Which of the following is an appropriate input for a common anode seven-segment display to display a character shown as output? Here, A represents the most significant bit (MSB) and G represents the least significant bit (LSB). \n\n","answer_label":"0110000","answer_id":9282},{"id":2032,"question":"Which of the following is a structural design pattern that allows classes with incompatible interfaces to work together and that can be implemented in either form in the two diagrams below?\n\n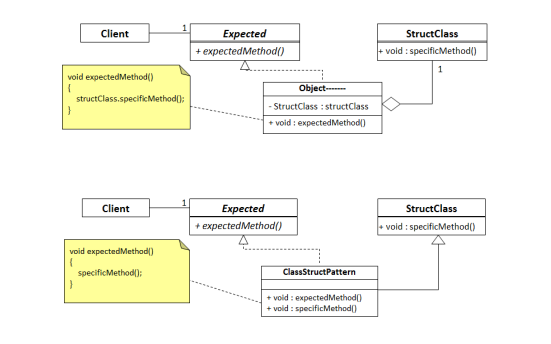","answer_label":"Adapter","answer_id":9286},{"id":2033,"question":"The arrow diagram below shows the original plan of a project.\n\n \n \nIf the project plan is changed as shown in the table below, which of the following impacts project completion date?\n\n\n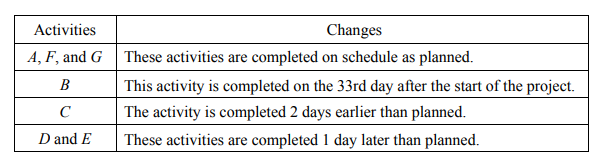","answer_label":"The project completion date is neither accelerated nor delayed","answer_id":9293},{"id":2034,"question":"Products A, B, C, and D are to be introduced to the market. The table below shows the expected profit for each product with three (3) sales forecasts (High, Medium, and Low) that are estimated to occur in accordance with the probability in the table. Which of the following is the product that is expected to make the highest profit according to the expected value principle? \n\n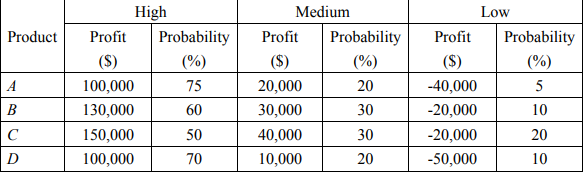","answer_label":"B","answer_id":9295},{"id":2035,"question":"With the carryover from the previous month and the quantity of inventory transactions for a product shown in the table below, what is the unit price of the product for the succeeding period using the periodic average method? \n\n","answer_label":"65.00","answer_id":9299},{"id":2036,"question":"The following inventory statement of Build-Up Property Company describes the status of the inventory since the beginning of the year 2014. If this company uses a first-in-first-out (FIFO) method for the inventory asset valuation, what is the inventory value at the end of the year 2014?\n\n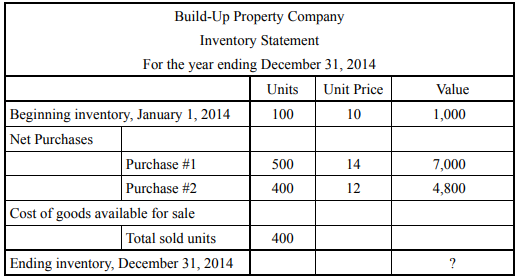","answer_label":"7,600","answer_id":9303},{"id":2037,"question":"Which of the following is the addressing mode where the operand of an instruction is used to point to the memory address that contains the address of the data to be operated upon?","answer_label":"Indirect addressing","answer_id":9308},{"id":2038,"question":"Which of the following is an appropriate characteristic of Bluetooth?","answer_label":"The short range (up to about 100 m) of wireless voice/data communication is defined.","answer_id":9312},{"id":2039,"question":"Among the RAID systems, which of the following should be used in cases where maximum storage capacity is required but data redundancy or fault tolerance is not a requirement?","answer_label":"RAID 0","answer_id":9314},{"id":2040,"question":"Which of the following is an appropriate explanation concerning a fault tolerant system?","answer_label":"A system that is designed so that the functions required for the overall system can\ncontinue to operate even in the event of a partial failure","answer_id":9320},{"id":2041,"question":"Which of the following is an appropriate explanation concerning a memory leak?","answer_label":"Part of main memory occupied during application execution is not released because of a bug of the application or OS, and the usable space of main memory decreases.","answer_id":9324},{"id":2042,"question":"In a white box test, which of the following is used to evaluate the proportion of lines of code that are executed?","answer_label":"Test coverage analysis","answer_id":9329},{"id":2043,"question":"When the source code based on OSS licensed under GPL is not released to the public, which of the following is regarded as a violation of the license?","answer_label":"A company obtains, modifies, and sells OSS through the company’s own operations or activities.","answer_id":9331},{"id":2044,"question":"A power supply unit has a rated output power of 500 watts and an efficiency of 80%. In order to obtain an output power of 500 watts from this power supply unit, how many watts is the minimum input power?","answer_label":"625","answer_id":9336},{"id":2045,"question":"Which of the following is an appropriate description concerning flash memory?","answer_label":"It can write data electrically and erase it electrically in units of blocks.","answer_id":9339},{"id":2046,"question":"Which of the following is an explanation concerning the morphing technique in computer animation?","answer_label":"In order to represent the smooth transformation in appearance from an image to another image, multiple intermediate images are created.","answer_id":9344},{"id":2047,"question":"Which of the following is an appropriate explanation concerning the data structure in a relational database?","answer_label":"Data is represented with one or more two-dimensional tables.","answer_id":9347},{"id":2048,"question":"In a relational database, there are two conditions that must be met as a primary key constraint. One condition is that there are no duplicate key values. Which of the following is another condition?","answer_label":"The primary key value must not be null.","answer_id":9353},{"id":2049,"question":"In computer networking, which of the following is the most appropriate technical term that means the variation in packet delay that causes the degradation of the QoS (Quality of Service) of real-time audio or video streaming service such as VoIP?","answer_label":"Jitter","answer_id":9356},{"id":2050,"question":"Which of the following is the network device that enables LANs to be interconnected at the physical layer of the OSI basic reference model?","answer_label":"Repeater","answer_id":9360},{"id":2051,"question":"Which of the following is a mechanism that enables a variety of information, such as still images, movies, and audio, to be sent via e-mail?","answer_label":"MIME","answer_id":9363},{"id":2052,"question":"In a TCP/IP network using IPv4 addresses, which of the following is a valid network address? Here, the number following a slash (/) is the number (in decimal) of bits allocated to represent the network number","answer_label":"210.11.190.192/26","answer_id":9369},{"id":2053,"question":"When security attacks to a computer system are classified into three categories (i.e., reconnaissance attack, access attack, and DoS attack), which of the following is classified as a reconnaissance attack?","answer_label":"Attempting to discover and map out systems, services, or vulnerabilities","answer_id":9370},{"id":2054,"question":"Which of the following is an appropriate explanation concerning the security attack that is classified as DNS cache poisoning?","answer_label":"Incorrect domain information is injected into the DNS server referenced by a PC, which leads the PC user to a fake Web server","answer_id":9376},{"id":2055,"question":"Which of the following is a method for preventing an SQL injection attack?","answer_label":"Ensuring that the input characters are not interpreted as characters that have a special meaning in an inquiry or operation to the database","answer_id":9378},{"id":2056,"question":"When the procedure below is performed in terms of security, which of the following can be done by recipient B, in addition to the detection of message falsification?\n\n[Procedure]\n\nProcess of sender A\n\n(1) A hash function is used to generate a digest from a message.\n\n(2) The sender’s secret signature generation key is used to generate a signature for the message from the digest generated in (1).\n\n(3) The message and the data generated in (2) are sent to recipient B. \n\nProcess of recipient B\n\n(4) A hash function is used to generate a digest from the received message.\n\n(5) The received data, the digest generated in (4), and sender A’s signature verification key are used to verify the signature.","answer_label":"Confirming that the message is from sender A","answer_id":9382},{"id":2057,"question":"Which of the following is the security attack that is shown in the procedure below?\n\n[Procedure]\n\n(1) An attacker creates a bogus Web site under the disguise of a financial institution.\n\n(2) The attacker pretends to be an employee of the financial institution and sends an e-mail that describes a URL leading to the bogus Web site.\n\n(3) The recipient of the e-mail trusts the e-mail and clicks on the URL. The recipient is then led to the bogus Web site.\n\n(4) The recipient does not notice that the Web site is bogus, and the entered authentication information is passed to the attacker.","answer_label":"Phishing","answer_id":9389},{"id":2058,"question":"Which of the following is regarded as risk sharing or risk transfer?","answer_label":"Distributing risk to other parties by purchasing insurance","answer_id":9391},{"id":2059,"question":"Which of the following is a method that is used for encrypting e-mail?","answer_label":"S/MIME","answer_id":9397},{"id":2060,"question":"Which of the following is the function that can be implemented with HTTPS?","answer_label":"Server authentication with an electronic certificate","answer_id":9400},{"id":2061,"question":"According to the ISO/IEC 25010 standard, the quality properties of a software product or system are categorized into eight characteristics: functional suitability, performance efficiency, compatibility, usability, reliability, security, maintainability, and portability. Which of the following is the appropriate explanation of “performance efficiency”?","answer_label":"Degree to which a product or system provides capabilities relative to the amount of resources used under stated conditions","answer_id":9403},{"id":2062,"question":"Which of the following is an appropriate deliverable that must be approved when the external design of a system is completed?","answer_label":"Screen layout","answer_id":9408},{"id":2063,"question":"In terms of the test coverage of a program module, which of the following is an appropriate explanation of the relationship between path coverage, branch coverage, and statement coverage?","answer_label":"100% path coverage implies both 100% branch coverage and statement coverage.","answer_id":9412},{"id":2064,"question":"When an integration test is performed by using the top-down approach, which of the following is particularly necessary?","answer_label":"Stub","answer_id":9417},{"id":2065,"question":"Which of the following is a characteristic of a project?","answer_label":"A project is both unique and temporary.","answer_id":9418},{"id":2066,"question":"Which of the following is an appropriate purpose of using a WBS (Work Breakdown Structure) in software development?","answer_label":"To decompose all development activities into smaller steps with a manageable size, and organize them into a hierarchical structure","answer_id":9423},{"id":2067,"question":"Which of the following is an explanation concerning a Pareto chart?","answer_label":"It is used to identify problems by sorting the classified items in descending order of frequency of occurrence and illustrating a bar chart with a cumulative line chart","answer_id":9426},{"id":2068,"question":"Which of the following is an appropriate policy for creating an SLA?","answer_label":"Setting a service level under the cost and needs of a service provider and its customers","answer_id":9433},{"id":2069,"question":"Among the management functions for service support, which of the following has the objective that aims to restore agreed service to the business as soon as possible or to respond to service requests?","answer_label":"Incident management","answer_id":9436},{"id":2070,"question":"Which of the following is the most appropriate description concerning a backup method for data","answer_label":"In consideration of a possible response delay in business processing, a backup schedule is adjusted so that it does not overlap with business processing.","answer_id":9438},{"id":2071,"question":"When software asset management is audited, which of the following is an appropriate point to be checked?","answer_label":"Checking to see if evidence, such as a software license certificate, is properly filed and retained","answer_id":9443},{"id":2072,"question":"Among the situations that are checked during an audit of the methods of transmitting highly confidential information to a business partner by e-mail, which of the following is an appropriate situation from the viewpoint of preventing information leakage?","answer_label":"A password is set for an attached file containing confidential information prior to being sent to the partner by e-mail, and the password is transferred in another way","answer_id":9446},{"id":2073,"question":"Which of the following is an appropriate activity that is undertaken by a system auditor who makes an audit of access control?","answer_label":"Verification of the management status of access control concerning data","answer_id":9453},{"id":2074,"question":"Among the architectures included in the “four domains” of the enterprise architecture, which of the following is the architecture other than business architecture, technology architecture, and application architecture?","answer_label":"Data architecture","answer_id":9455},{"id":2075,"question":"IT investment evaluation is performed as prior evaluation, interim evaluation, or post evaluation according to each stage of the planning, execution, and completion for an individual project. Which of the following is an explanation concerning “prior evaluation”?","answer_label":"Setting the performance objectives based on the purpose of investment, and providing the top management with information necessary for determining the feasibility of implementation","answer_id":9461},{"id":2076,"question":"Which of the following is the purpose of defining a business model at the planning stage of total optimization in an information strategy?","answer_label":"To organize the relationships between a company’s entire business operations and their utilized information, and establish a clear vision for the information system","answer_id":9464},{"id":2077,"question":"When a computerization plan is made, which of the following is an item to be considered?","answer_label":"Clarifying the cost and investment effect of the development, maintenance, and operations of the system","answer_id":9466},{"id":2078,"question":"Which of the following is an explanation concerning non-functional requirements definition?","answer_label":"It clearly defines the quality requirements, technical requirements, and operational requirements necessary to implement business requirements.","answer_id":9473},{"id":2079,"question":"Which of the following is an explanation concerning a franchise chain in the retail industry?","answer_label":"A form of organization where a head office allows its members to use the trademarks and signs, and also provides managerial training and assistance, at a fixed rate of compensation","answer_id":9475},{"id":2080,"question":"Which of the following is the primary purpose of implementing an ERP system that is used for business management?","answer_label":"To integrate all departments and functions across a company into a single computer system that can serve the entire company’s needs","answer_id":9479},{"id":2081,"question":"Which of the following is an appropriate explanation concerning product innovation in the management of technology?","answer_label":"Developing a new or differentiated product that is a key to success","answer_id":9482},{"id":2082,"question":"Among the various types of e-commerce transactions, which of the following is an appropriate example of B2C (i.e., “B to C”)?","answer_label":"Mr. B buys a book from an online shop owned by Company A.","answer_id":9487},{"id":2083,"question":"Which of the following is an explanation concerning EDI?","answer_label":"The exchange of business transaction data between computers over the Internet or other dedicated communication lines, in accordance with standard protocols","answer_id":9493},{"id":2084,"question":"Which of the following is an organization structure where employees report to both their individual immediate managers and a cross function leader and try to achieve coordination between program groups and centrally controlled groups of functional specialists?","answer_label":"Matrix organization","answer_id":9496},{"id":2085,"question":"Which of the following is an explanation concerning the accountability at an executive managerial level?","answer_label":"A management executive has responsibility for explaining the content and performance of business activities to shareholders and other interested parties.","answer_id":9499},{"id":2086,"question":"Which of the following is a case example that is suitable for ABC analysis?","answer_label":"The hot-selling products need to be analyzed on the basis of the sales value and gross profit of each product.","answer_id":9505},{"id":2087,"question":"When a single-license software package is purchased in a company, which of the following is an activity that is usually permitted in conformity with the concept of the WTO’s Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"Making a backup copy of software for the limited purposes, such as the licensee’s personal use or a temporary copy for maintenance","answer_id":9507},{"id":2088,"question":"Among the descriptions concerning personal data, which of the following is not an appropriate description from the viewpoint of “OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data”?","answer_label":"Personal data should be allowed to be acquired without announcing the acquisition of such data.","answer_id":9510},{"id":2170,"question":"There is a register where an integer value is stored in binary. Let x be a positive integer\nwhich is stored into the register, then perform the operations below.\n(1) Shift the content of the register to the left by 2 bits\n(2) Add x to the register.\nHow many times larger than the integer x is the content of the register?","answer_label":"5","answer_id":9801},{"id":2174,"question":"When three sets A, B and C are given, which of the following equalities holds? Here, ∪\nand ∩ are union and intersection symbols, respectively.","answer_label":"(A∩C)∪(B∩C) = (A∪B)∩C","answer_id":9816},{"id":2180,"question":"Which of the following bit strings is accepted by the automaton described in the state\ntransition diagram below? Here, each string is processed one bit at a time in sequence from\nthe left.\n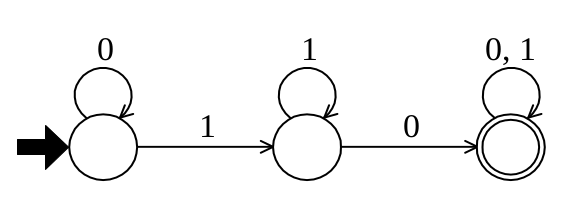","answer_label":"1010","answer_id":9837},{"id":2183,"question":"Which of the following is a binary search tree whose keys are numbers assigned to nodes in\nnatural order?\n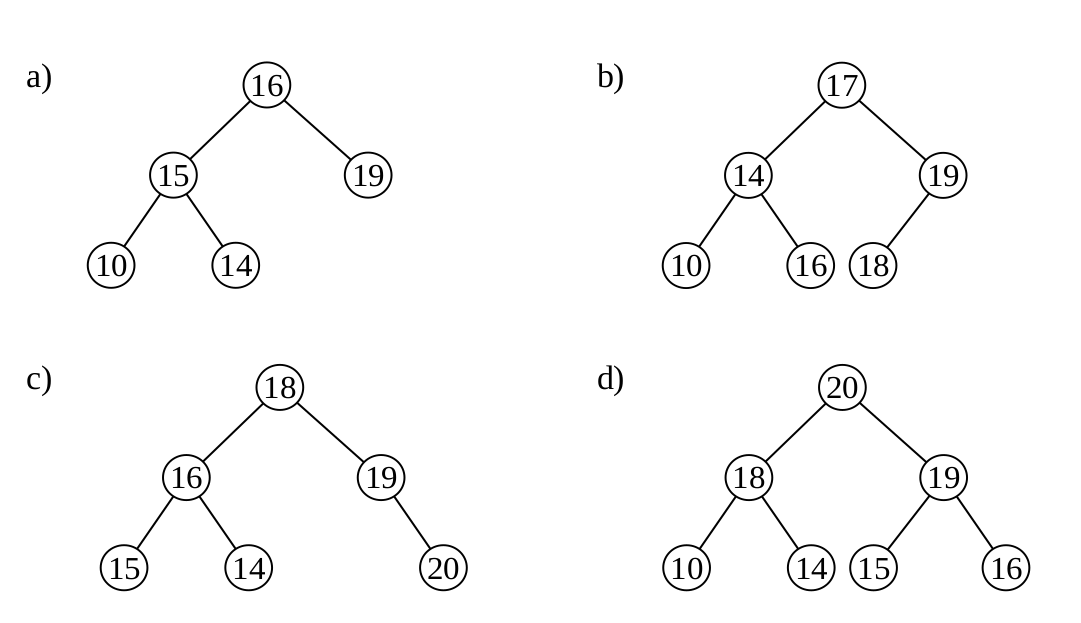","answer_label":"b","answer_id":9848},{"id":2185,"question":"Function F(n) is a recursively defined integer function that calculates the factorial of n for\nany non-negative integer n. Which of the following is an appropriate expression for the\nblank A?\n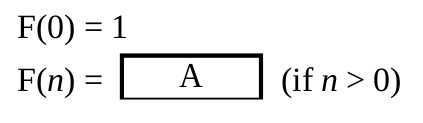","answer_label":"n × F(n - 1)","answer_id":9855},{"id":2186,"question":"What is the result of the procedure in the flowchart below, when x and y are positive\nintegers?\n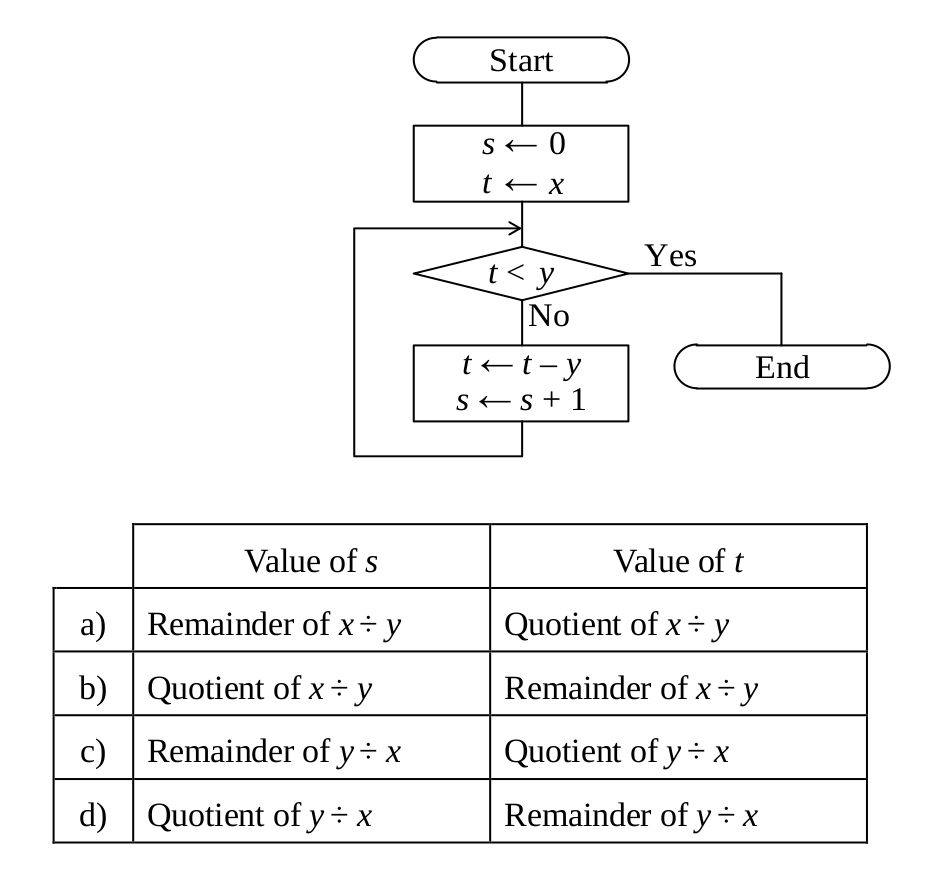","answer_label":"b","answer_id":9858},{"id":2191,"question":"For a multiprogramming switching procedure of processes shown in the figure below,\nwhich of the following is an appropriate combination of OS processing for A through C?\n","answer_label":"c","answer_id":9871},{"id":2194,"question":"The half adder in the diagram below adds two (2) single-digit binary numbers x and y,\nand produces z (the first digit of the sum) and c (the carry bit) as output. Which of the\nfollowing is the appropriate combination of gate devices A and B?\n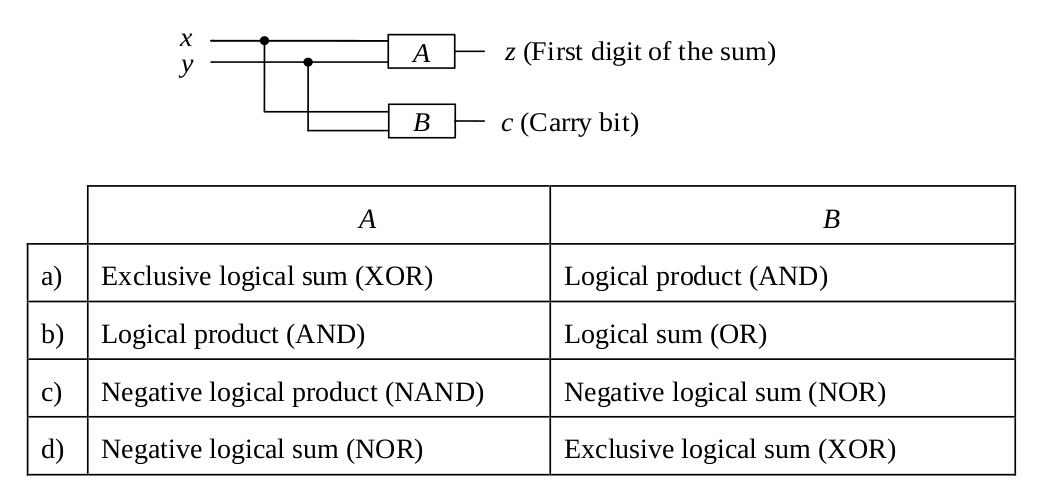","answer_label":"a","answer_id":9880},{"id":2195,"question":"Which of the following is equivalent to the logic circuit shown below?\n","answer_label":"c","answer_id":9886},{"id":2197,"question":"When ordering data in the format below is entered, which of the following is an\nappropriate check to examine whether the value of the Order date field is on a business day\nequal to or prior to the entering date?\n\n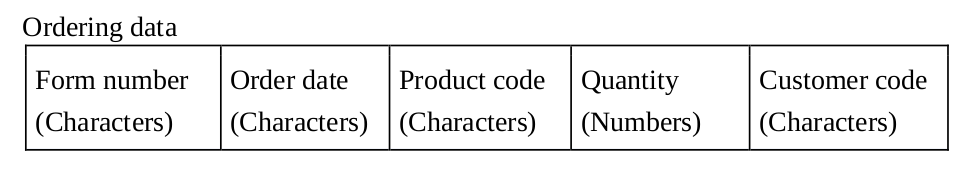","answer_label":"Logical check","answer_id":9894},{"id":2201,"question":"There is a “Delivery” table that has six (6) records. Which of the following is the\nfunctional dependency that is satisfied by this table? Here, “X → Y” indicates that X\nfunctionally determines Y.\n","answer_label":"Delivery_destination → Component_ID","answer_id":9908},{"id":2203,"question":"When the SQL statement shown below is executed on the “Employee” table and the\n“Department” table, which of the following is the result?\n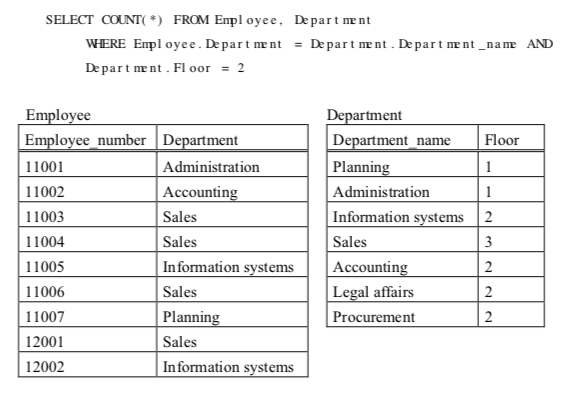","answer_label":"3","answer_id":9918},{"id":2208,"question":"In a TCP/IP network hierarchical model, what is the name for Equipment A that\nconnects two LAN segments at the Internet Layer?\n","answer_label":"Router","answer_id":9932},{"id":2209,"question":"A PC and a web server are communicating via HTTP. When a request packet is sent\nfrom the PC to the web server, which of the following combinations of port numbers does\nthe response packet have? Here, the source and the destination port numbers of the request\npacket are 50001 and 80 respectively.\n\n","answer_label":"a","answer_id":9934},{"id":2255,"question":"Which of the following is the purpose of analyzing business plans and competitive\nadvantages through portfolio management that uses the matrix shown in the figure?\n","answer_label":"To evaluate the position of the company’s business as the basis for setting an objective\nand prioritizing resource allocation","answer_id":10113},{"id":2259,"question":"The figure below is the work procedure of MRP (Material Requirements Planning), a\ntechnique of a production management system. Which of the following information to be\ninserted into A in the figure below is necessary for calculating the net requirements?\n","answer_label":"Inventory status (inventory amount, residual orders, in-process quantity)","answer_id":10123},{"id":2343,"question":"Which of the following is the work that is performed when non-functional requirements are defined?","answer_label":"Creating the technical requirements for the development criteria and standards\naccording to the programming language used in system development","answer_id":10448},{"id":2345,"question":"Which of the following is an explanation of core competence?","answer_label":"Predominant abilities that cannot be imitated by competitors in a company’s area of\nactivity","answer_id":10456},{"id":2350,"question":"Which of the following is an explanation of an affinity diagram?","answer_label":"It is a method by which the collected information is categorized on the basis of a\nmutual relationship, and the problems to be resolved are clarified.","answer_id":10476},{"id":2767,"question":"If a given bit string contains at least one 1-bit, the algorithm below leaves the rightmost 1-bit unchanged but makes all the others 0. For example, if the given bit string is 00101000, the result will be 00001000. Which of the following is the appropriate logical peration to be filled in D?\nStep 1: By regarding the given bit string A as an unsigned binary number, let B be the result of subtracting 1 from A.\nStep 2: Calculate the XOR (exclusive logical sum) of A and B, and let C be the result.\nStep 3: Calculate the  of A and C, then set the result back to A.","answer_label":"AND (logical product)","answer_id":12067},{"id":2768,"question":"When 4-bit signed numbers in 2's complement are used, which of the following operations will cause either an overflow or an underflow?","answer_label":"Subtract B from A when A is 0111 and B is 1010.","answer_id":12073},{"id":2769,"question":"When two unbiased dice are rolled one by one, what is the probability that either the first one is 2 or the sum of the two is less than 5?","answer_label":"5/18","answer_id":12077},{"id":2770,"question":"A leap year is either a multiple of 4 but not a multiple of 100, or a multiple of 400. How many leap years are there from 1998 to 2110?","answer_label":"27","answer_id":12080},{"id":2771,"question":"Which of the following is the most appropriate description of a queue?","answer_label":"Data that is stored first is retrieved first.","answer_id":12083},{"id":2772,"question":"Binary search is used to search for an element from a sorted data of n elements.Which of the following is an expression that represents the order of computational complexity for this process?","answer_label":"log n","answer_id":12087},{"id":2773,"question":"In Java technologies, which of the following is the specification of creating reusable software components that have frequently used functionalities?","answer_label":"JavaBeans","answer_id":12093},{"id":2774,"question":"Which of the following best describes the characteristics of XML?","answer_label":"XML allows a tag to be defined in order for an easier data exchange between information systems over the network.","answer_id":12096},{"id":2775,"question":"Which of the following is the addressing method that references data in the main memory as shown in the figure below?\n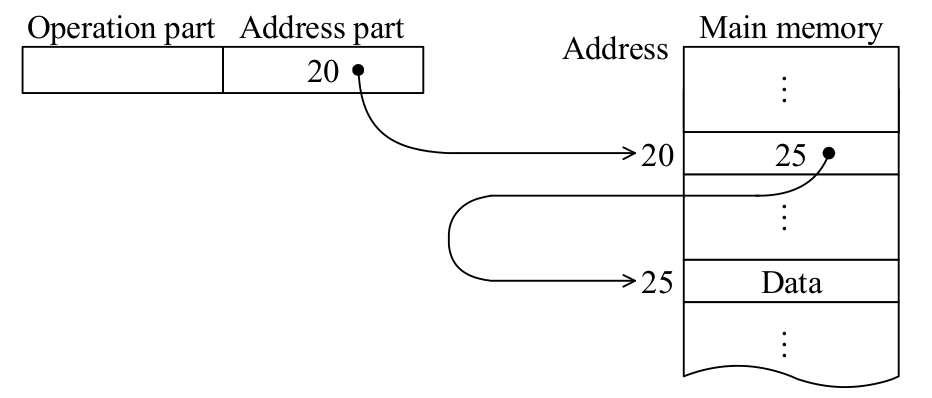","answer_label":"Indirect addressing","answer_id":12101},{"id":2776,"question":"Which of the following is classified as an internal interrupt?","answer_label":"An interrupt because of the operation of division by zero (0)","answer_id":12104},{"id":2777,"question":"ECC is used for error detection and correction in memory. If n + 2 redundant bits are required for a data bus with a width of 2 bits, how many redundant bits are required for a data bus with a width of 128 bits?","answer_label":"9","answer_id":12109},{"id":2778,"question":"Which of the following lists contain A through D in the order of shorter effective memory access time of the main memory?\n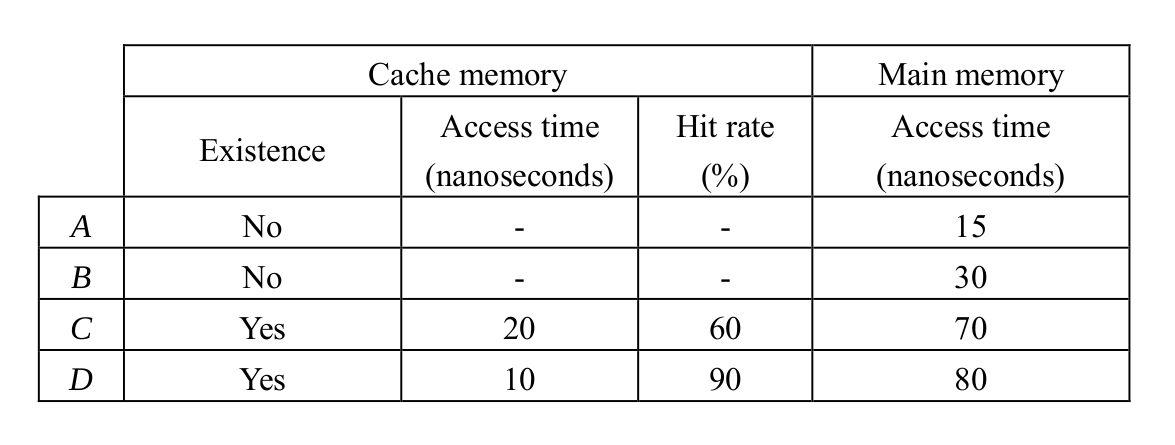","answer_label":"A, D, B, C","answer_id":12112},{"id":2779,"question":"Which of the following is an appropriate description of the reliability of computer systems?","answer_label":"Preventive maintenance of systems is performed to increase MTBF.","answer_id":12117},{"id":2780,"question":"A system is operated as a virtual machine environment with 20 physical machines. When the operating conditions are shown below, what is the minimum number of physical machine failures that causes the system to enter fall back operation?\n[Operating conditions]\n(1) If a physical machine fails, the virtual machines that were running on it are made to run evenly on all the other physical machines, and the resources that were used are distributed in the same way.\n(2) When there are 20 physical machines, 70% of the resources of all physical machines are used.\n(3) If the resources used on a single physical machine exceed 90%, the whole system enters fall back operation.\n(4) Conditions other than (1) through (3) above do not need to be considered.","answer_label":"5","answer_id":12122},{"id":2781,"question":"Which of the following is an appropriate graph that shows the relationship between CPU utilization and average response time in an online real-time system? Here, transactions occur according to a Poisson distribution, and the processing time for a transaction follows an exponential distribution.","answer_label":"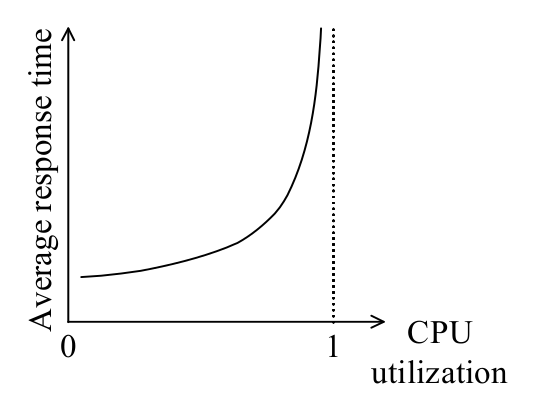","answer_id":12123},{"id":2782,"question":"Which of the following occurs when a program attempts to access a page that is mapped in the virtual address space, but is not located in the main memory? Here, the OS supports paging.","answer_label":"Page fault","answer_id":12128},{"id":2783,"question":"Which of the following is an appropriate explanation of spooling?","answer_label":"It temporarily saves output data for a low-speed device, such as a printer, to a high-speed hard disk, and then sends it to the intended device.","answer_id":12134},{"id":2784,"question":"In a paged virtual memory system, the LRU method is used in the page replacement algorithm. When the page frame assigned to the main memory is 4, and pages are accessed in the order of 1, 2, 3, 4, 5, 2, 1, 3, 2, 6, which of the following page is replaced at the time of accessing page 6? Here, no page exists in the main memory in the initial state.","answer_label":"5","answer_id":12138},{"id":2785,"question":"There is a system in which the print requests waiting for output are assigned to an available printer in an order of A, B, and C, and then the printer available first among the three (3) printers A through C of the same model. If the print time of each print request is 5, 12, 4, 3, 10, and 4 (minutes) in the order of the requests waiting for output, which of the following lists of printers is arranged in an order starting from the longest time assigned for printing? Here, all printers are available in the initial state.","answer_label":"A, B, C","answer_id":12139},{"id":2786,"question":"Which of the following is an open source integrated development environment that includes software and support tools for application development?","answer_label":"Eclipse","answer_id":12143},{"id":2787,"question":"Which of the following is a characteristic of DRAM and not of SRAM?","answer_label":"It has a simple memory cell structure, and thus the price per bit is low.","answer_id":12148},{"id":2788,"question":"Which of the following is a logical expression that is equivalent to the digital circuit shown in the figure below? Here, “•” is the logical product, “+” the logical sum, and “ 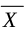\n ” the negation of X.\n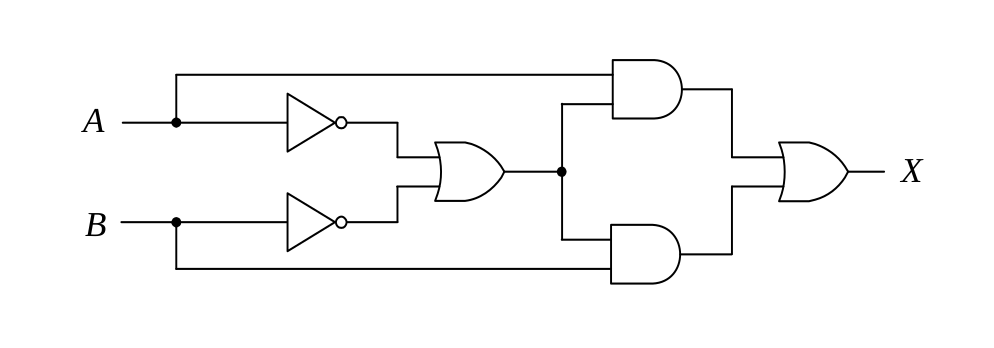","answer_label":"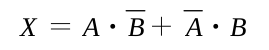","answer_id":12153},{"id":2789,"question":"Which of the following is the name of a phenomenon where multiple ON/OFF signals are generated within a few milliseconds after a push-button switch with a mechanical contact is pressed once?","answer_label":"Chattering","answer_id":12156},{"id":2790,"question":"Which of the following shows the path information from the front page of a web site to the current page, a user is currently viewing?","answer_label":"Breadcrumbs","answer_id":12159},{"id":2791,"question":"Which of the following is an explanation of the morphing technique in computer animation?","answer_label":"In order to represent a smooth transition between two images, multiple intermediate images are created for interpolation.","answer_id":12166},{"id":2792,"question":"When new naming conventions for data items are provided, which of the following problems cannot be avoided only by the naming conventions described below?\n[Naming conventions]\n(1) Always add a classification word such as the “name”, “code”, “number”, “amount”, or “date” at the end of the data item name, and set the data type determined for each classification word.\n(2) Create a dictionary in which data item names and their meanings are registered, and ensure that synonyms and homonyms do not occur.","answer_label":"The scope of the possible values of the data item “OrderAmount” varies according to the table.","answer_id":12169},{"id":2793,"question":"The data model shown in the figure below is implemented as three (3) tables. At this time, which of the following is an appropriate combination of A and B in the “Transfer” table in which the transaction of “the sales of 500 dollars to Company C are booked in the cash account on April 4, 2015” is recorded? Here, the data model is described in UML.\n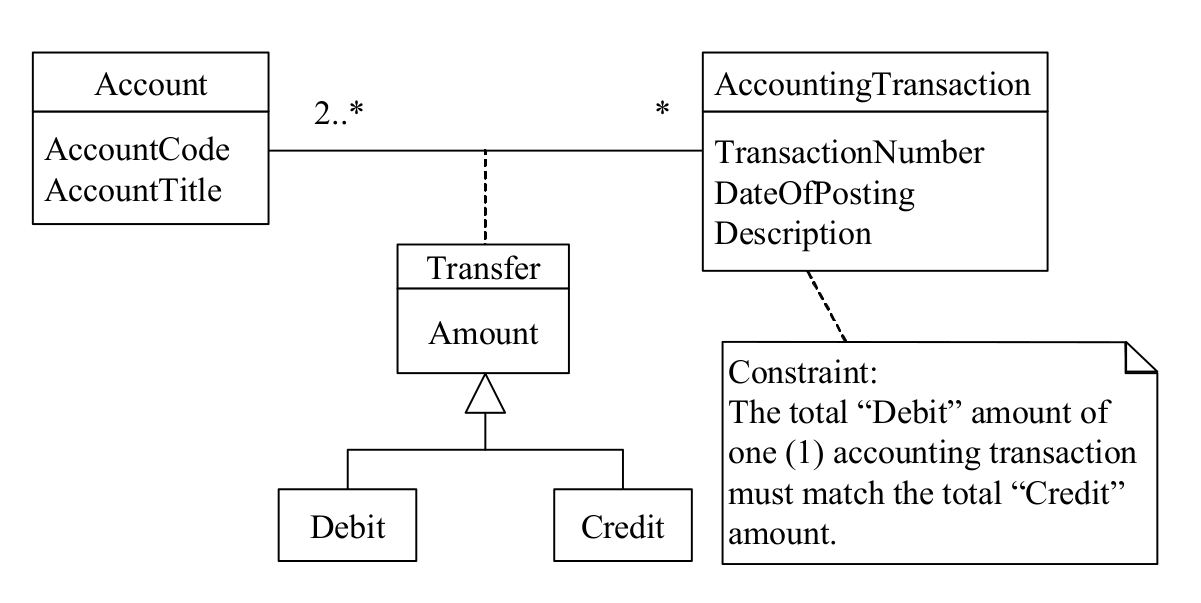\n\n","answer_label":"d","answer_id":12174},{"id":2794,"question":"In the process of table implementation, which of the following is an appropriate SQL statement that removes a column in an existing table?","answer_label":"ALTER TABLE table_name\n DROP COLUMN column_name","answer_id":12176},{"id":2795,"question":"When a manager is analyzing the sales of products in a supermarket, he makes a query to list all products with their sales amount, including the products that have no sales amount. Which of the following is an appropriate combination of statements to be filled in the boxes in the query? Here, the columns of Product and Sales are shown below.\n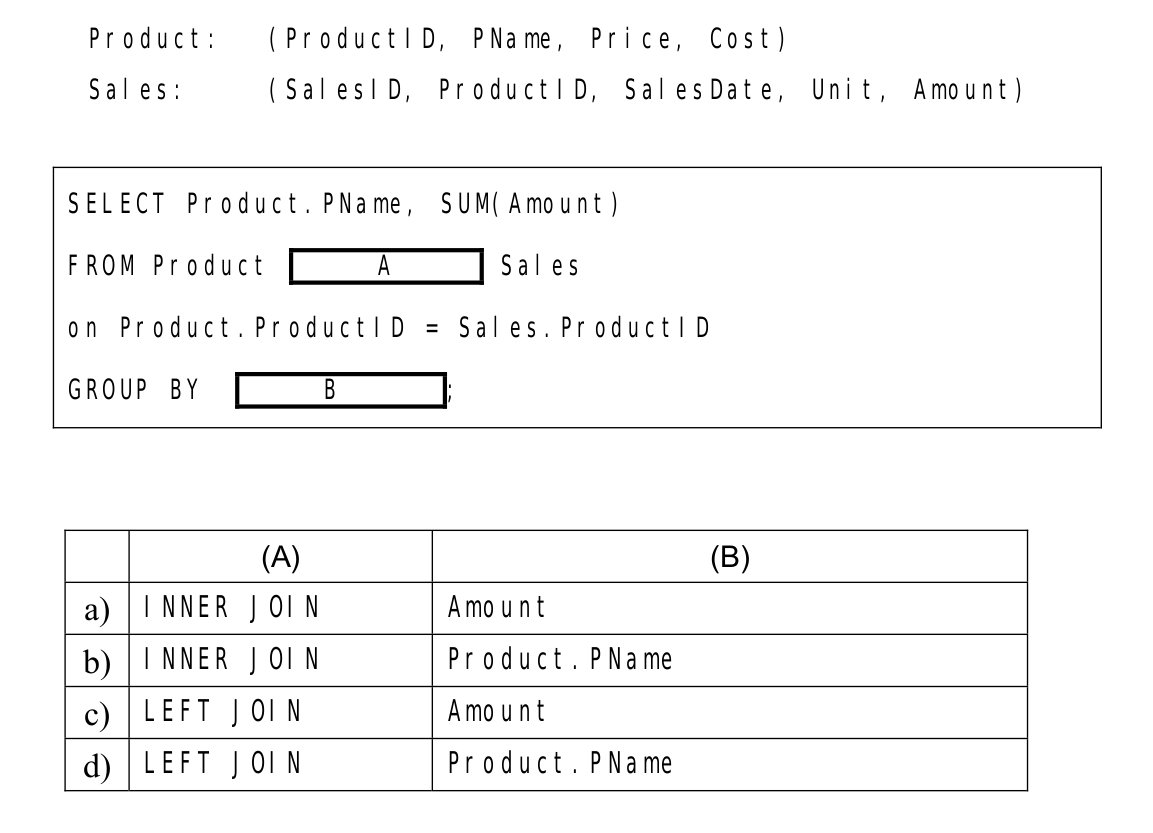","answer_label":"d","answer_id":12182},{"id":2796,"question":"Which of the following is an appropriate description of locks?","answer_label":"For a resource on which transaction T1 has acquired a shared lock, transaction T2 can acquire a shared, but not an exclusive, lock.","answer_id":12185},{"id":2797,"question":"In a CSMA/CD based LAN, which of the following is an appropriate description of the transmission operation performed by a network node?","answer_label":"Each node checks if the transmission medium is in use, and can transmit data if the medium is not in use. If a conflict is detected, a retransmission occurs after a random interval of time.","answer_id":12188},{"id":2798,"question":"Which of the following is an appropriate description of network devices?","answer_label":"A repeater extends transmission distances by amplifying signals between the segments of the same type.","answer_id":12193},{"id":2799,"question":"In a TCP/IP environment, which of the following is a standard for attaching image data to an email?","answer_label":"MIME","answer_id":12196},{"id":2800,"question":"Concerning email protocols, which of the following descriptions is correct?","answer_label":"IMAP allows the message to remain on the server even after it is downloaded to a local PC.","answer_id":12199},{"id":2801,"question":"In IPv6 networks, what is the length of an IP address in bits?","answer_label":"128","answer_id":12205},{"id":2802,"question":"Which of the following is a secure communication protocol that provides a hybrid cryptosystem where public key cryptography is used to transfer a shared private key securely to the other side, and private key cryptography is used to encrypt subsequent communications for the remaining session?","answer_label":"SSL/TLS (Secure Socket Layer/Transport Layer Security)","answer_id":12209},{"id":2803,"question":"In a meeting session, the security administrator provides a presentation regarding risks on social media and recommends that the attendees not give unnecessary personal information on social media websites. From which of the following attacks do the social media users effectively reduce the security risk most by following this recommendation?","answer_label":"Cognitive password attack","answer_id":12212},{"id":2804,"question":"Which of the following is an appropriate description of a Trojan horse used for security attacks in computing?","answer_label":"It is a rogue program that tricks users.","answer_id":12217},{"id":2805,"question":"Which of the following is an appropriate combination of the usage method of a signature key in a digital signature, and the purpose of a digital signature?","answer_label":"By the sender creating a digital signature with the signature key and attaching it to a message, the recipient can confirm the identity of the sender.","answer_id":12219},{"id":2806,"question":"Which of the following is an example of improper use of a key logger?","answer_label":"When Internet banking is used, it collects the password entered by the user.","answer_id":12224},{"id":2807,"question":"Biometric authentication includes a method of authentication by extracting physical characteristics, and a method of authentication by extracting behavior characteristics. Which of the following has behavior characteristics?","answer_label":"Performing authentication by extracting characteristics from the speed of and pressure on a pen when a signature is written","answer_id":12228},{"id":2808,"question":"Which of the following is the most effective method of detecting falsification of the contents of a web server?","answer_label":"The hash value of each file of the contents of the web server is stored and periodically compared with the hash value generated from each file.","answer_id":12232},{"id":2809,"question":"When a digital certificate has been installed in an in-house system accessed from a smartphone by an employee, which of the following can be checked using the in-house system?","answer_label":"Ensuring that the smartphone has been allowed to access the in-house system","answer_id":12237},{"id":2810,"question":"Which of the following is a technique where a system is actually attacked and an intrusion attempt is made in order to detect security-related vulnerabilities of a computer or network?","answer_label":"Penetration test","answer_id":12239},{"id":2811,"question":"Which of the following can be used to detect worms by using SHA-256 to calculate a hash value from a subject file, and then cross-checking this against a database of hash values from files containing specimens of known worms?","answer_label":"The same worm as a worm specimen","answer_id":12246},{"id":2812,"question":"Which of the following is the most appropriate explanation of the deployment diagram defined in UML 2.x (including 2.0 and later versions)?","answer_label":"It shows a static view of the run-time configuration of processing nodes, such as servers and clients, as well as the components that run on these nodes.","answer_id":12249},{"id":2813,"question":"In software development for small projects, which of the following is an appropriate explanation of test driven development (TDD)?","answer_label":"Development is done in increments of functionality where test cases are executed and the code is developed to pass the test cases before moving to the next increment.","answer_id":12253},{"id":2814,"question":"There is a program module that is executed only when the value of integer x is 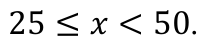 When this module is tested using the boundary value analysis, which of the following is an appropriate combination of values to be tested?","answer_label":"24, 25, 49, 50","answer_id":12255},{"id":2815,"question":"Which of the following is an appropriate category of system maintenance preformed for the purpose of modifying the system to cope with changes in the software environment (e.g.DBMS, Operating system)?","answer_label":"Adaptive maintenance","answer_id":12259},{"id":2816,"question":"Which of the following is an appropriate order of six phases used in every SDLC (Software Development Life Cycle) model?","answer_label":"","answer_id":12264},{"id":2817,"question":"According to PMBOK, which of the following is an appropriate explanation of project definition?","answer_label":"It is a temporary endeavor undertaken to create a unique product, service, or result.","answer_id":12269},{"id":2818,"question":"A project has been defined to contain the activities along with their required times for completion as shown in the table below. Which of the following is the critical path for this project?\n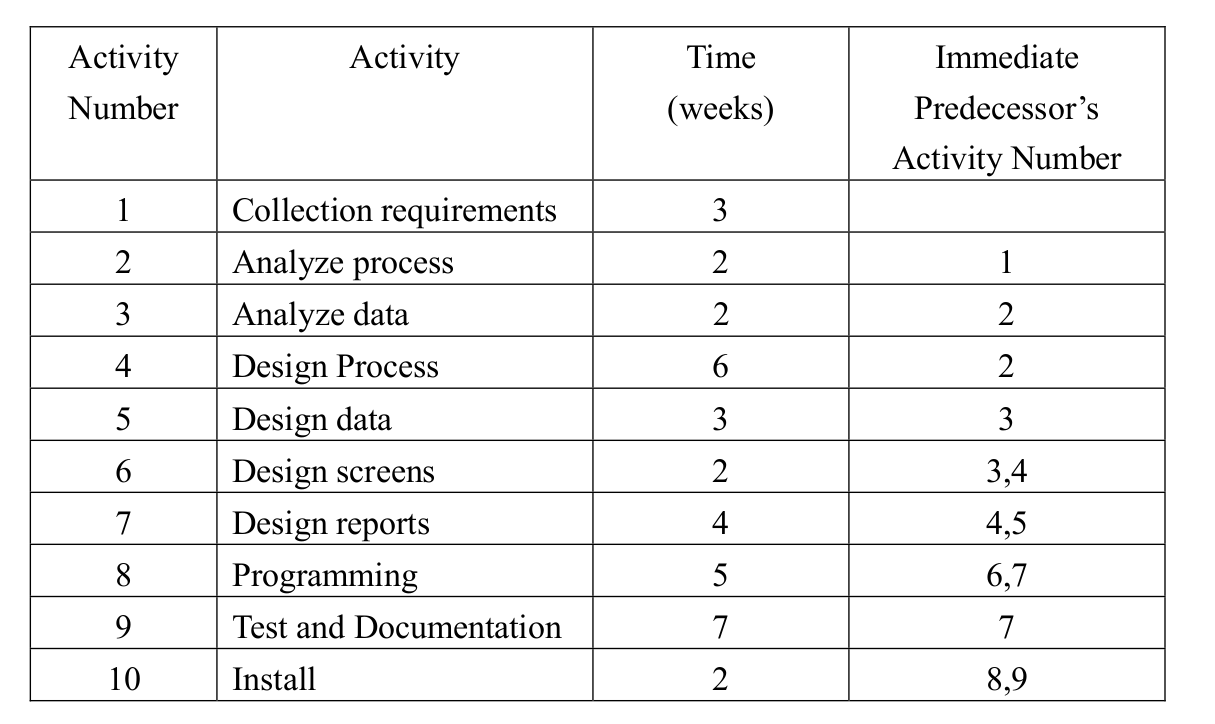","answer_label":"1-2-4-7-9-10","answer_id":12273},{"id":2819,"question":"In the Earned Value Management technique, which of the following is used to calculate the Cost Performance Index (CPI)?","answer_label":"Earned Value (EV) / Actual Cost (AC)","answer_id":12278},{"id":2820,"question":"According to PMBOK, which of the following is the project management knowledge area that includes the activities of make-or-buy decisions, development time and material contracts, and selection of sellers from bidders?","answer_label":"Project Procurement Management","answer_id":12282},{"id":2821,"question":"In order to check whether a system works normally, users in the system user department and operators in the system operations department jointly conduct operational testing prior to full operation. Which of the following is an appropriate description of the users should prioritize during testing?","answer_label":"Testing whether the system operates according to predetermined business procedures","answer_id":12286},{"id":2822,"question":"When data in the business operations department is entered in a data sheet by the information system department, which of the following is an appropriate task executed by the information system department?","answer_label":"To enable the business operations department to check the processing results of each data sheet, the processing results list is sent to the business operations department.","answer_id":12289},{"id":2823,"question":"Among the structures and characteristics of a service desk organization, which of the following is a description of a local service desk?","answer_label":"By deploying the service desk near the users, it is possible to provide services for users who have different languages and cultures or for VIPs by dedicated service staff.","answer_id":12292},{"id":2824,"question":"When a version management system for source code is installed, which of the following is an appropriate check point to be added for the confidentiality of the source code during the system audit?","answer_label":"The access control settings of the version management system are appropriate.","answer_id":12295},{"id":2825,"question":"Which of the following is an appropriate description of the implementation structure of a system audit?","answer_label":"In order to enable the person requesting the audit to issue improvement instructions on the basis of the audit report, the system auditor reports the audit results to the person requesting the audit.","answer_id":12300},{"id":2826,"question":"Which of the following is a check point for auditing control in relation to the accuracy of the processing logic of a spreadsheet?","answer_label":"The program of the spreadsheet is documented and verified.","answer_id":12305},{"id":2827,"question":"Which of the following is the purpose of BPM (Business Process Management) in the context of corporate activity?","answer_label":"Continual improvement of business processes","answer_id":12308},{"id":2828,"question":"When a workflow system is used for business improvement, which of the following is an appropriate effect that can be expected?","answer_label":"Processing speed for office procedures from document submission to approval can be improved.","answer_id":12312},{"id":2829,"question":"The table below shows the result of analyzing the daily activities of a sales representative. By implementing SFA (Sales Force Automation), the preparation time for customer visits can be reduced by 0.1 hours per customer visit. In order to increase the number of customer visits to six (6) per day without changing the total working hours and the hours per customer visit, how many hours must be reduced from “Other working time”?\n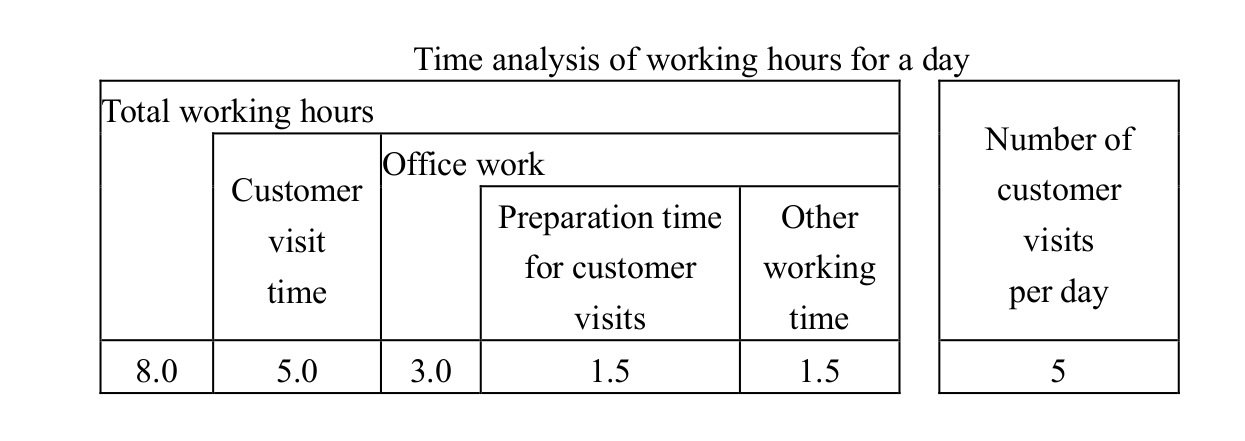","answer_label":"0.7","answer_id":12317},{"id":2830,"question":"Which of the following is an explanation of SOA?","answer_label":"It is a concept that considers the functions of software as components called services, and combines these services in order to develop application systems.","answer_id":12319},{"id":2831,"question":"Which of the following is an explanation of application architecture that configures enterprise architecture?","answer_label":"It systematically indicates the functions and configuration of a system supporting a business process.","answer_id":12325},{"id":2832,"question":"In the table shown below, the investment category and KPI have been arranged according to the investment purpose. Which of the following corresponds to investment purpose C ? Here, a) to d) are applied to any one of A to D.\n","answer_label":"Creation of business and establishment of competitive advantages","answer_id":12328},{"id":2833,"question":"A SWOT analysis is a technique that is used to identify and evaluate the internal and external factors that are advantageous or disadvantageous to achieve the objectives of the business or project. When a company’s situation is analyzed as shown in the table below, which of the following is the most appropriate combination that corresponds to the company’s Strengths that give the company advantages over others, Weaknesses that give the company disadvantages relative to others, Opportunities that are exploited for the company’s advantages, and Threats that cause troubles for the business or project?\n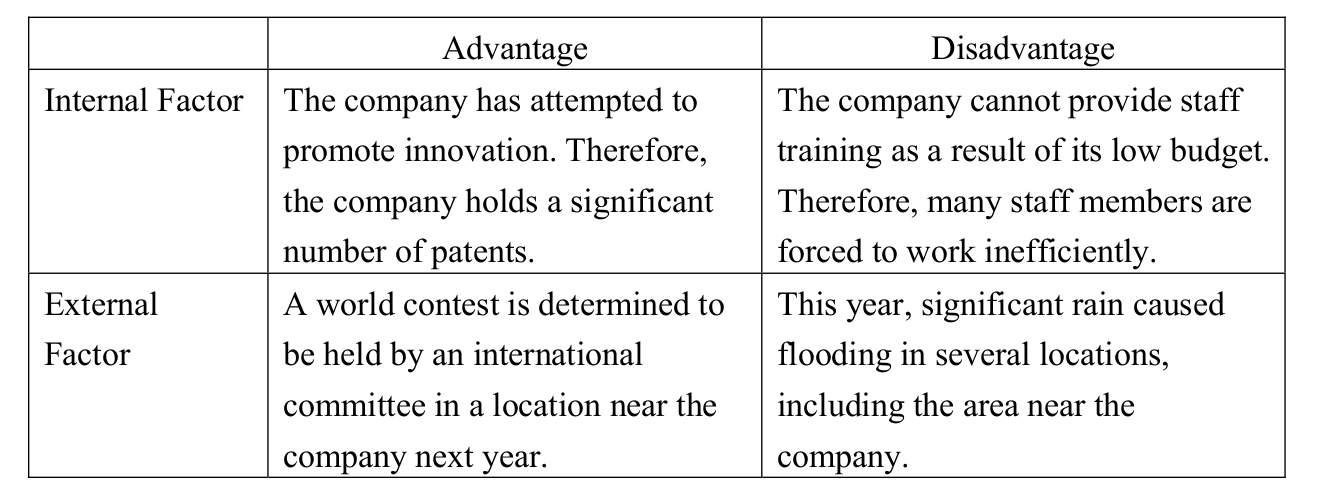\n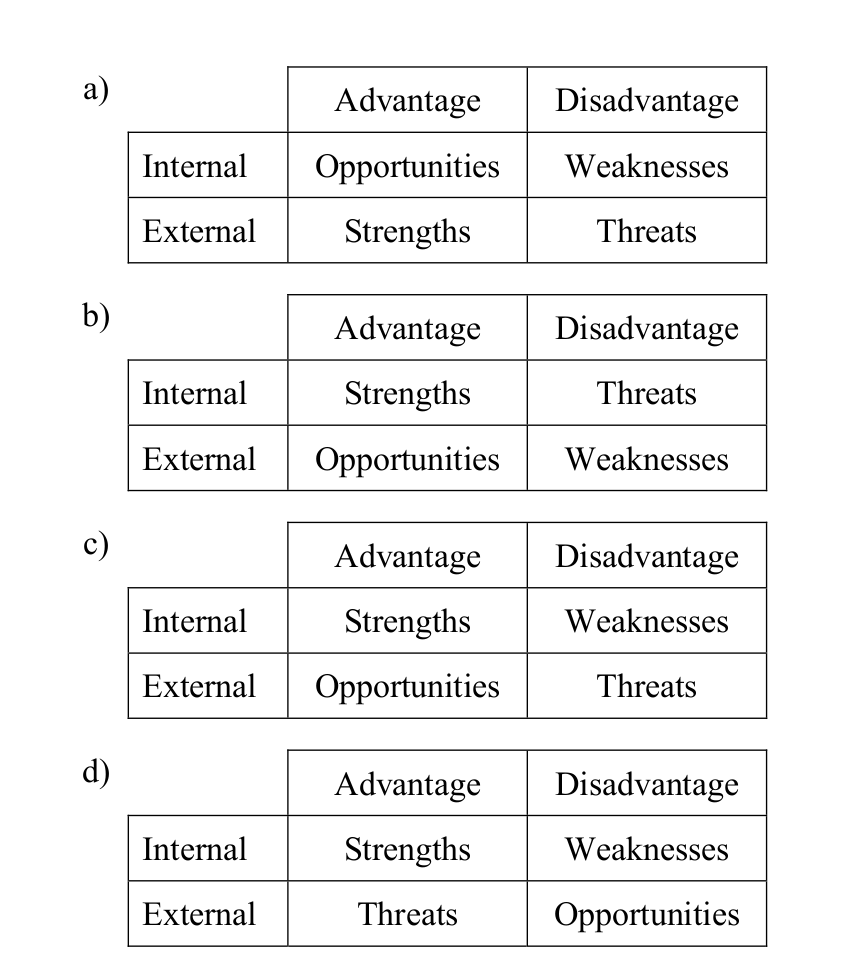","answer_label":"c","answer_id":12333},{"id":2834,"question":"According to the “competitive strategy” by Philip Kotler, which of the following is a company that has no high market share, but has the strategic aim of achieving high profits and acquiring a unique position by focusing management resources on particular products and services?","answer_label":"Market nicher","answer_id":12338},{"id":2835,"question":"Which of the following is an explanation of knowledge management?","answer_label":"Management which improves the overall problem-solving capability by sharing knowledge that is scattered across the enterprise","answer_id":12341},{"id":2836,"question":"Which of the following is a characteristic of an IC tag (RFID)?","answer_label":"An IC tag is resistant to dirt, and the recorded information can be read even from outside the container.","answer_id":12344},{"id":2837,"question":"In IT investment opportunities, when the investment effect of five (5) years is evaluated on the basis of ROI (Return On Investment), which of the following four (4) opportunities A through D has the greatest effect? Here, the IRR (Internal Rate of Return) is zero (0).\n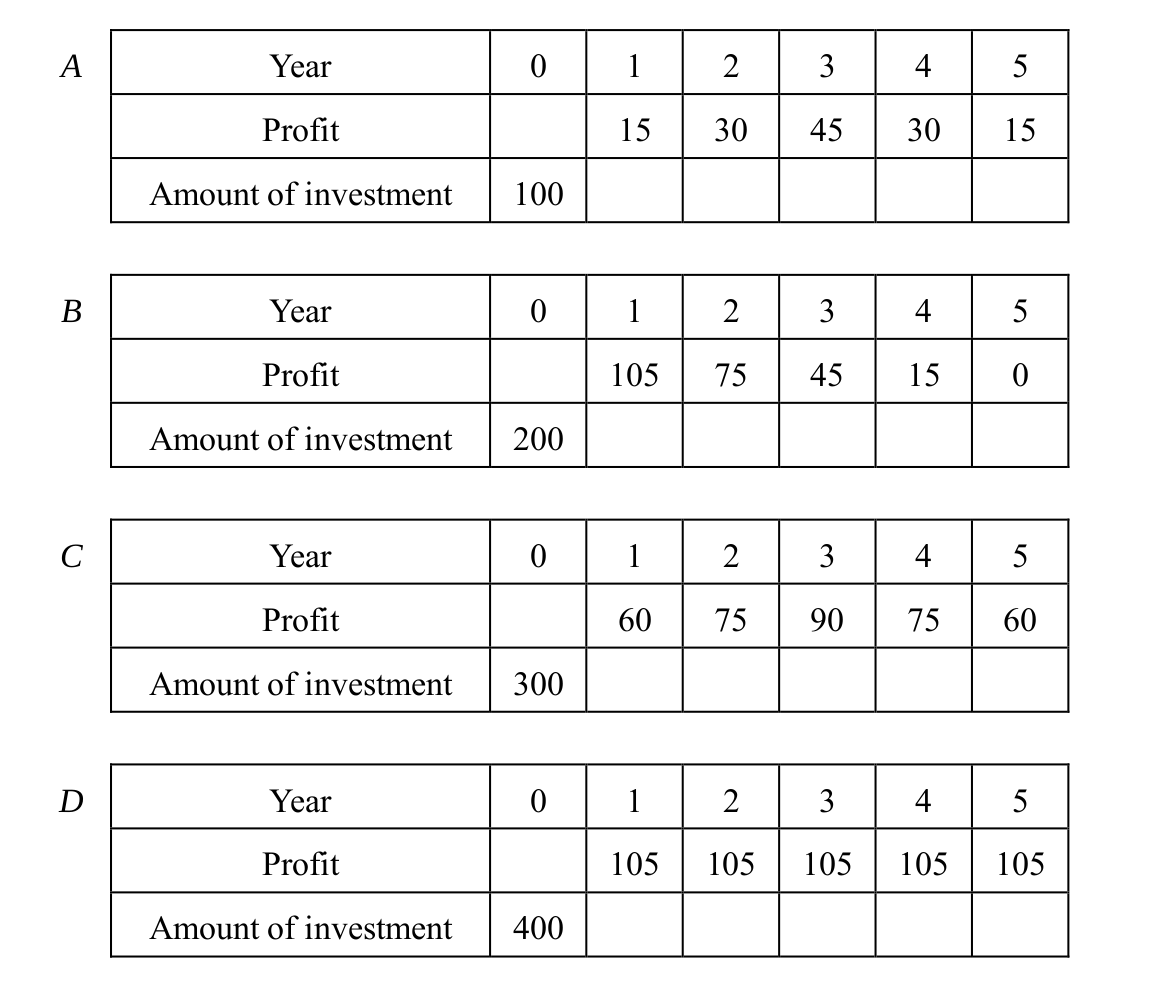","answer_label":"A","answer_id":12347},{"id":2838,"question":"Which of the following is an example of the use of social media in business?","answer_label":"A company sets up a site on the Internet for sharing opinions on matters such as the usage status of its products, which leads to improvement of the product.","answer_id":12352},{"id":2839,"question":"Which of the following is an appropriate explanation of tethering as a function of cell phones?","answer_label":"By using a cell phone as a modem or access point, data communication that uses a network, such as the Internet, is enabled on a PC, game console, or other such devices.","answer_id":12356},{"id":2840,"question":"Which of the following is a role that CIO is required to perform?","answer_label":"Promotion of use of IT services that maximizes business value.","answer_id":12362},{"id":2841,"question":"Among the measures that a company should adopt in order to fulfill social responsibility, which of the following is implemented in terms of the environment?","answer_label":"To develop an internal organization for the purpose of green purchasing.","answer_id":12363},{"id":2842,"question":"Which of the following can secure employment and create employment opportunities in an entire society by shortening the work hours per employee?","answer_label":"Work sharing","answer_id":12369},{"id":2843,"question":"Which of the following is an explanation of an ABC analysis method?","answer_label":"Products are arranged in order of high sales or high gross margins, and then products are divided into various levels by using the cumulative ratio. Following this, an increase in sales volume is planned for the products at the high levels.","answer_id":12372},{"id":2844,"question":"Three products, A, B, and C, are processed by two (2) machines, M1 and M2. Processing must be conducted in the order of M1 → M2. The time required for each machine to process each product is shown in the table below. Under these conditions, which of the following is the processing order of three (3) products that results in the shortest time from the beginning of the processing until all products are finished? Here, when M1 has processed a product, it can successively process another product.\n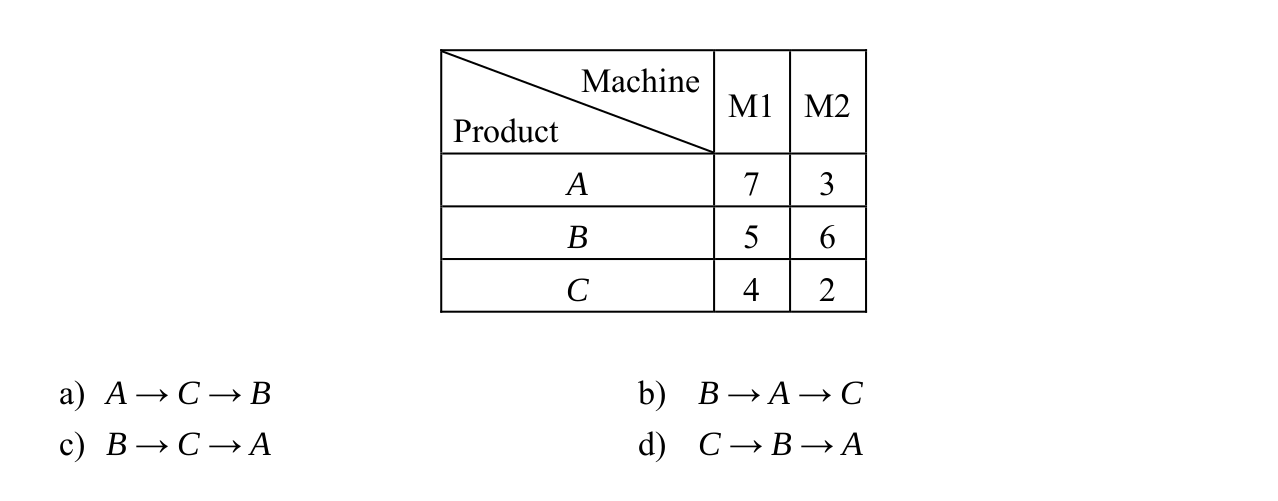","answer_label":"b","answer_id":12376},{"id":2845,"question":"Which of the following is a technique that discovers useful information and relationships from large amounts of customer and market data retained by a company?","answer_label":"Data mining","answer_id":12381},{"id":2846,"question":"Among the descriptions of personal data, which of the following is not an appropriate description from the viewpoint of “OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data”?","answer_label":"Personal data should be allowed to be acquired without announcing the acquisition of such data.","answer_id":12383},{"id":2910,"question":"Which of the following is a logical expression equivalent to the exclusive-OR operation\nof logical variables p and q? Here, “∨”, “∧”, and “¬” are OR, AND, and NOT operators,\nrespectively .","answer_label":"(p ∨ q) ∧ ¬(p ∧ q)","answer_id":12626},{"id":2911,"question":"Among the bit strings of length 4, how many of them either start with 1 or end with 00?","answer_label":"10","answer_id":12631},{"id":2912,"question":"A factory manufactures the same products in two production lines A and B, where 60% of the products are manufactured in A, and the remaining in B. Defective rates of the\nproducts manufactured in A and B are 2% and 1%, respectively. When a product was randomly chosen for inspection, it was found to be defective. What is the percent probability that the product was manufactured in A?","answer_label":"75","answer_id":12636},{"id":2913,"question":"Which of the following is the computational complexity of the Heapsort algorithm? Here,\nn is the number of elements to be sorted. All comparisons, swaps, and other needed\noperations can proceed in constant time.","answer_label":"O (n log n)","answer_id":12640},{"id":2914,"question":"A regular expression [A-Z]+[0-9]* represents a set of character strings. Which of the following character strings belongs to this set? Here, the regular expression follows the\nrules below. \n\n[A-Z] represents a single uppercase English character.\n[0-9] represents a single decimal digit.\n* indicates zero or more occurrences of the preceding element.\n+ indicates one or more occurrences of the preceding element.","answer_label":"ABCDEF","answer_id":12644},{"id":2915,"question":"Data A, B, C and D are entered as an input sequence. Which of the following is a possible output sequence by only using a single stack?","answer_label":"C, B, D, A","answer_id":12647},{"id":2916,"question":"For integers x and y (x > y ≥ 0), a function F(x, y) is defined as follows. What is the value F(231, 15)? Here, x mod y represents the remainder after division of x by y.\n","answer_label":"3","answer_id":12650},{"id":2917,"question":"Which of the following is an explanation of a recursive call?","answer_label":"To allow a function to use itself from within its body","answer_id":12653},{"id":2918,"question":"In a web environment, which of the following is the name of a program that runs on a web server and achieves dynamic processing?","answer_label":"Java servlet","answer_id":12658},{"id":2919,"question":"Which of the following is a special purpose register that stores the result of a comparison or the sign of the result of an arithmetic operation?","answer_label":"Flags register","answer_id":12662},{"id":2920,"question":"Which of the following is the addressing mode that references data in main memory as shown in the figure below?\n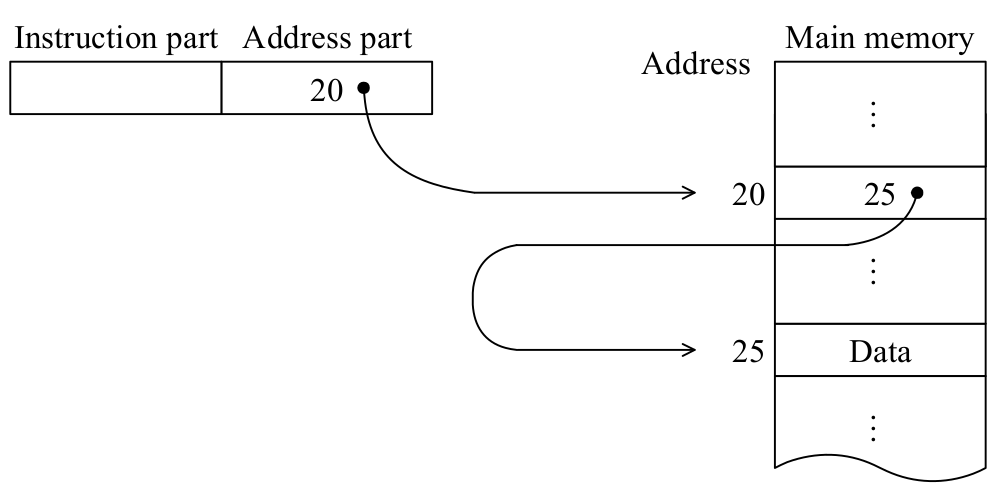","answer_label":"Indirect addressing","answer_id":12667},{"id":2921,"question":"When a 1-megabyte memory is connected to the MPU as shown in the figure below, what is the minimum number of signal lines (represented as n ) required by address buses? Here, the memory is accessed in units of bytes. In addition, 1 megabyte = 1,024 kilobytes and 1 kilobyte = 1,024 bytes.\n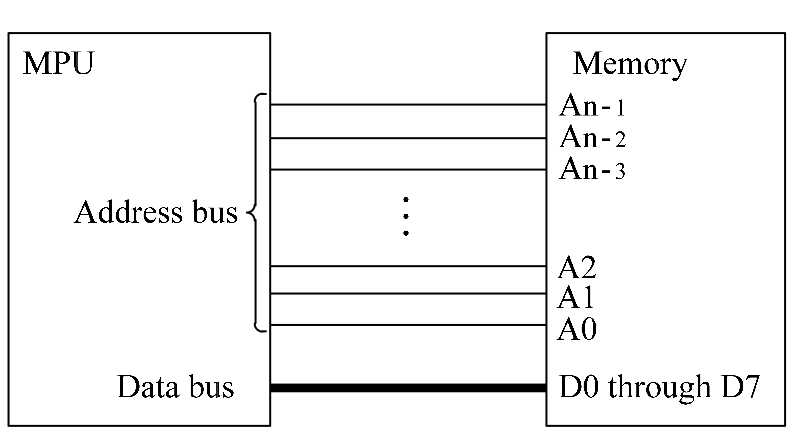","answer_label":"20","answer_id":12671},{"id":2922,"question":"Which of the following is an appropriate explanation of USB 3.0?","answer_label":"It uses a serial interface that has a 5 Gbps data transfer mode called super speed.","answer_id":12673},{"id":2923,"question":"Which of the following is an appropriate description of the effect of cache memory?","answer_label":"By reading data from main memory and storing it in cache memory, data transfer is performed at high speed when the CPU reads the same data later.","answer_id":12678},{"id":2924,"question":"Which of the following is an appropriate explanation of a benchmark test?","answer_label":"It executes a standard program selected in accordance with the usage purpose, and measures the system’s processing performance.","answer_id":12683},{"id":2925,"question":"As shown in the figure below, one (1) server, three (3) clients, and two (2) printers are connected via a LAN. This system prints data located on the server in response to instructions from the clients. When the availability of each device is as shown in the table below, which of the following is the expression that represents the availability of the system? Here, the system is considered available when the server, one (1) of the three (3) clients, and one (1) of the two (2) printers are running.\n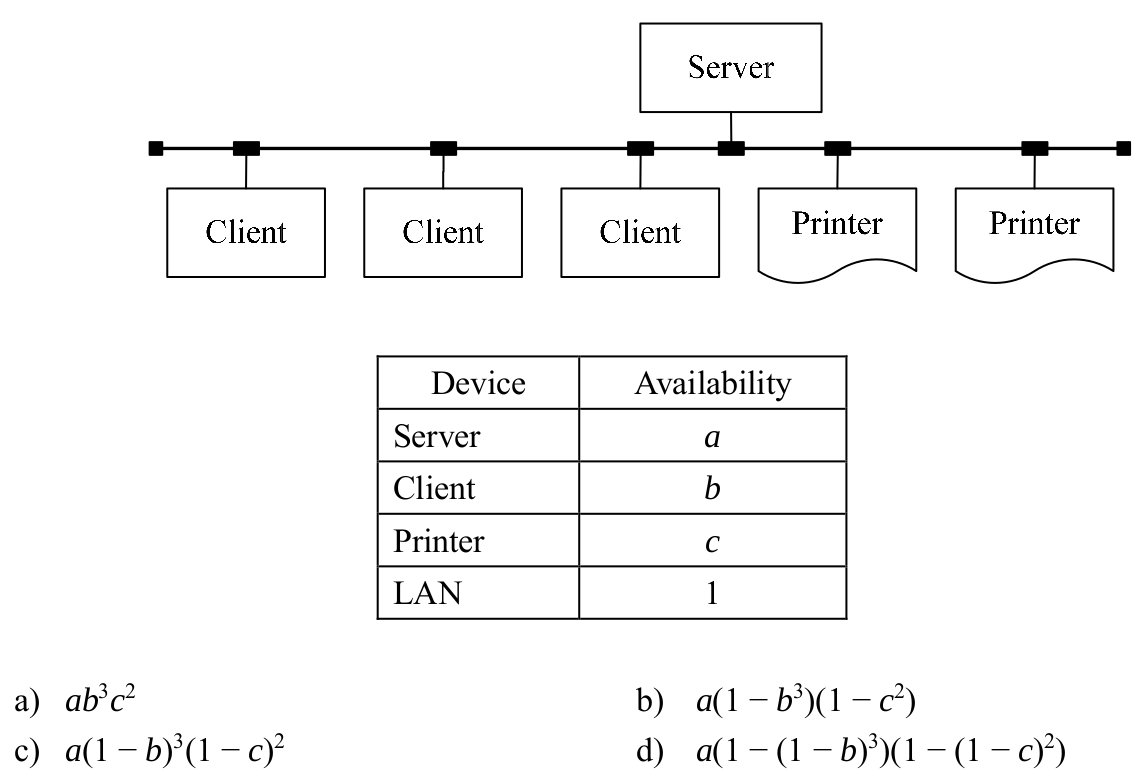","answer_label":"a(1-(1-b)³)(1-(1-c)²)","answer_id":12688},{"id":2926,"question":"As shown below, there is a set of processes, with the length of the CPU-burst time given in milliseconds, and the processes arrive in the order of P1, P2, P3, P4, and P5 with the arrival time of all processes at t = 0.\n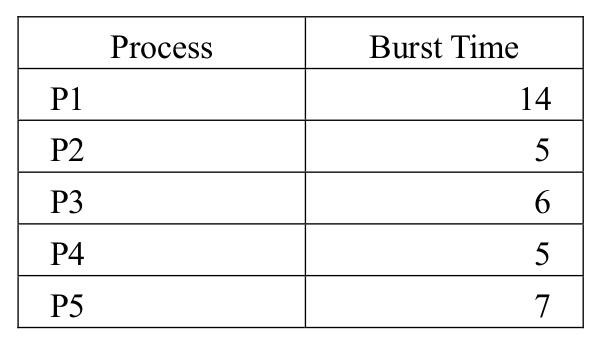\n\nWhich of the following is the average turnaround time of five (5) processes from P1 through P5 with the first-come first-served (FCFS) scheduling algorithm?","answer_label":"25","answer_id":12692},{"id":2927,"question":"Which of the following is an appropriate usage method of the priority-based preemptive scheduling that is used in an embedded real-time operating system?","answer_label":"It is used when tasks are processed according to their importance and urgency.","answer_id":12694},{"id":2928,"question":"Multiple directories named A and B are managed in the structure shown in the figure below. Which of the following is the case in which the current directory is moved so that “\\B\\A\\B” is the current directory? Here, the method for directory designation is as below, and → indicates the order of movement.\n \n[Method for directory designation]\n(1) A directory is referenced as “directory name\\ ··· \\directory name”, where the directories on the path are aligned and delimited with “\\” in sequence, followed by “\\” and the directory name.\n(2) The current directory is represented by “.” (a period).\n(3) The directory one (1) hierarchical level above is represented by “..” (two periods).\n(4) When a reference begins with a “\\”, it is assumed that the root directory is omitted at the leftmost position of the reference.\n(5) When a reference does not start with “\\”, “.”, or “..”, it is assumed that “.\\” is omitted from the leftmost position of the reference.\n\n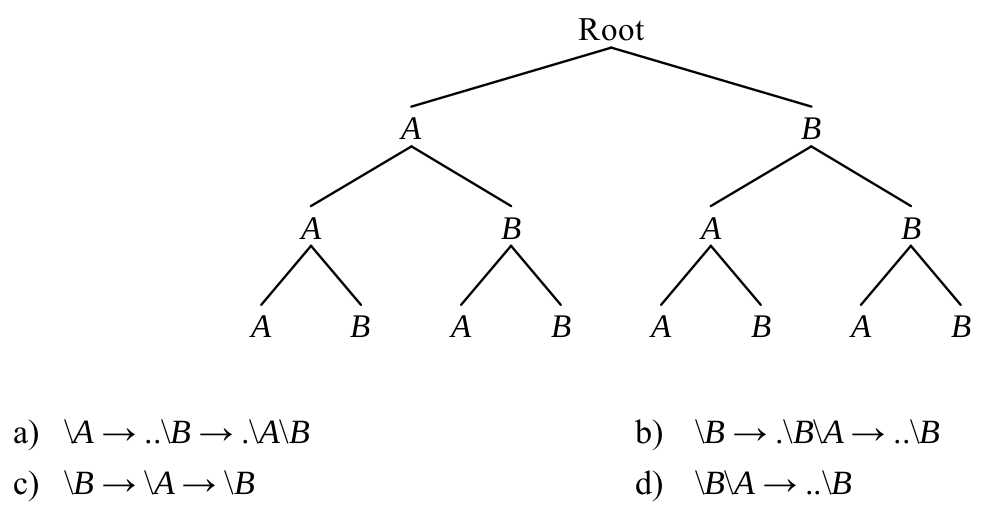","answer_label":"\\A → ..\\B → .\\A\\B","answer_id":12697},{"id":2929,"question":"In the virtual memory of a paging system, which of the following is a cause that increases the number of page fault occurrences?","answer_label":"An increase in access to a page that does not exist in main memory","answer_id":12702},{"id":2930,"question":"Which of the following is a criterion for a page to be replaced in a Least Recently Used (LRU) algorithm?","answer_label":"The last referenced time","answer_id":12708},{"id":2931,"question":"There is a logic circuit shown below. When the input values are A = 1, B = 0, and C = 1, which of the following is the combination of the values of E and Y?\n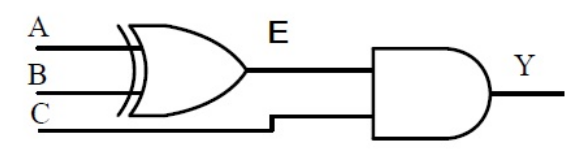","answer_label":"E = 1, Y = 1","answer_id":12712},{"id":2932,"question":"By using a sensor that detects changes in shape, the condition of infrastructure such as elevated highways can be monitored and maintained. Which of the following is a sensor that is used for this purpose?","answer_label":"Strain gage","answer_id":12715},{"id":2933,"question":"In a lighting circuit for an anode-common type LED with seven (7) segments, when 92 in hexadecimal is written out to the output port, which of the following is displayed? Here, P7 is the most significant bit (MSB), P0 is the least significant bit (LSB), and the LED lights up when the port output is 0.\n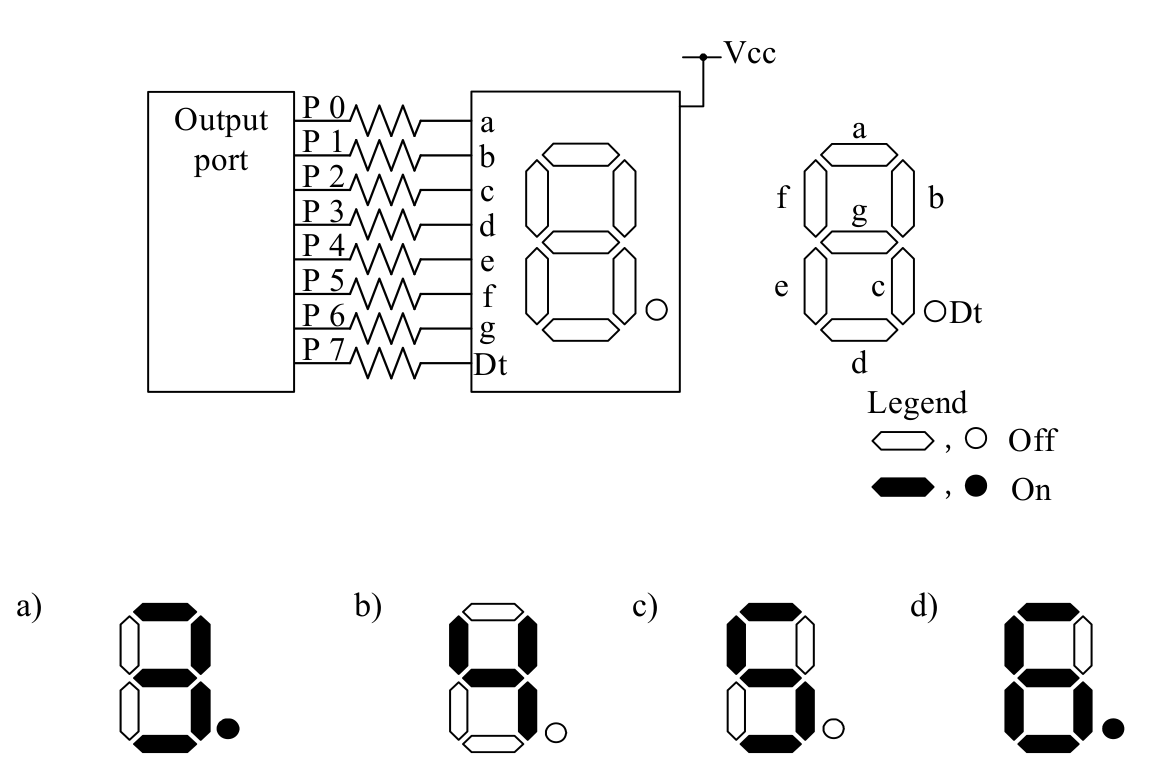","answer_label":"c","answer_id":12719},{"id":2934,"question":"Currently, the number of customers is 8,000 with annual increase rate of 20%. By assigning a fixed length code using 26 uppercase alphabet A- Z to each customer, what is the minimum code length required to accommodate all the customers for next three years?","answer_label":"3","answer_id":12721},{"id":2935,"question":"An audio signal is sampled 11,000 times per second while each sample is recorded as an 8-bit data. When a 512×10⁶ -byte capacity flash memory is used, what is the maximum number of minutes to record such data?","answer_label":"775","answer_id":12727},{"id":2936,"question":"“a → b” represents the fact that when the value of attribute a is determined, the value of attribute b is determined uniquely. For example, “Employee number → Employee name” represents that when the employee number is determined, the employee name is determined uniquely. Based on this notation, when the relations between attributes a through j are established as shown in the figure below, which of the following is an appropriate combination of three (3) tables that defines the relations in a relational database?\n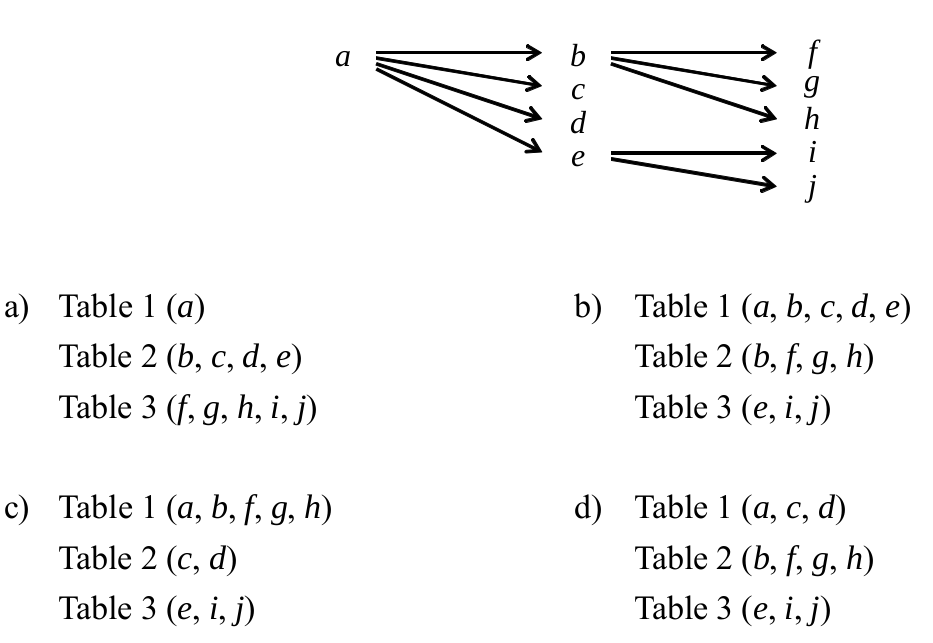","answer_label":"b","answer_id":12730},{"id":2937,"question":"The data model in the diagram below is implemented with three (3) tables. Which of the following is an appropriate combination of A and B in table “Transfer” that contains the record that indicates “500 dollars sales to Company X are posted to the cash account on April 4, 2017”? Here, the data model is described in UML.\n","answer_label":"d","answer_id":12736},{"id":2938,"question":"After relations X and Y are joined, which of the following is (are) the relational algebra operation(s) to obtain relation Z?\n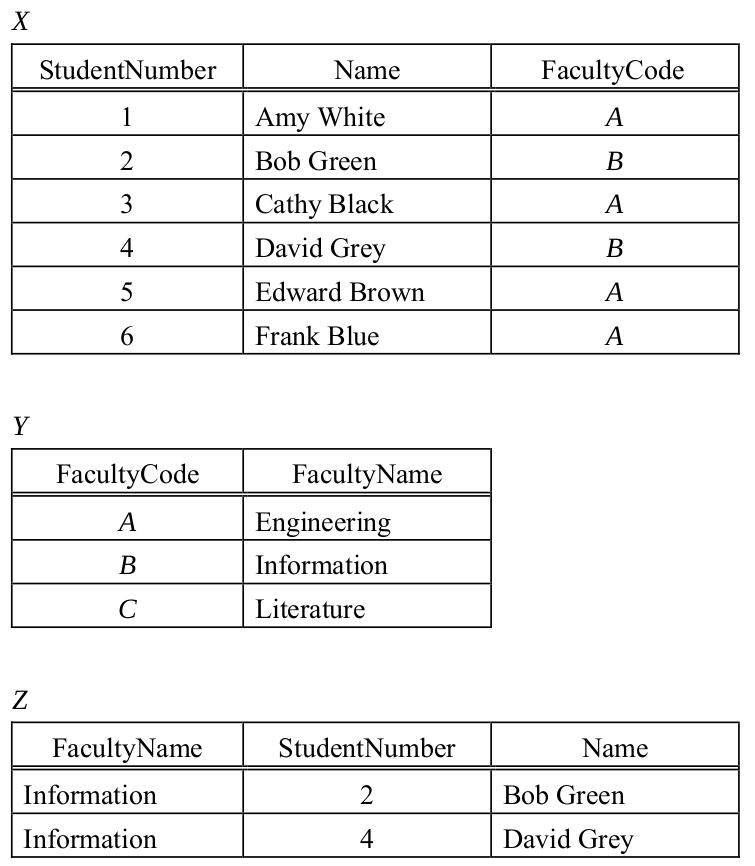","answer_label":"Projection and selection","answer_id":12737},{"id":2939,"question":"In a DBMS, when multiple transaction programs update the same database simultaneously, which of the following is a technology that is used to prevent logical contradictions?","answer_label":"Exclusive control","answer_id":12741},{"id":2940,"question":"As an example of the use of big data, which of the following is a process that uses statistical or other methods to obtain new knowledge (such as trends and patterns) from a large amount of data?","answer_label":"Data mining","answer_id":12746},{"id":2941,"question":"Which of the following is the most appropriate information for a router to determine the destination of an incoming packet?","answer_label":"Destination IP address","answer_id":12749},{"id":2942,"question":"In the OSI basic reference model, which of the following is the layer where bridges operate?","answer_label":"Datalink layer","answer_id":12755},{"id":2943,"question":"In TCP/IP, which of the following is an application layer protocol that enables a server to automatically configure its clients with network information such as IP addresses, the subnet mask and the default gateway address?","answer_label":"DHCP","answer_id":12758},{"id":2944,"question":"Which of the following is an appropriate explanation of SDN (Software-Defined Networking) that uses OpenFlow?","answer_label":"It is a network technology that logically decouples the functions for data transfer and route control, and is implemented with a combination of network devices specialized for data transfer and software-based route control.","answer_id":12762},{"id":2945,"question":"As shown below, multiple PCs are connected to the home network and they have access to the Internet through FTTH, and a global IP address is assigned to the WAN interface of device A. Which of the following is the function of device A that enables the PCs to use the Internet with this global IP address?\n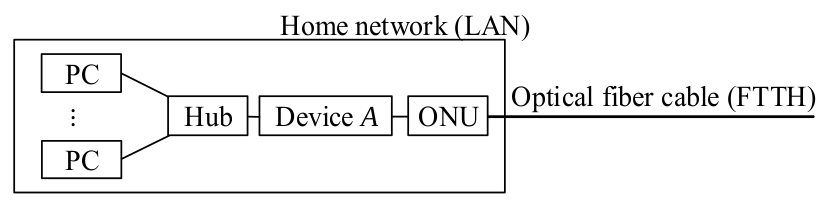","answer_label":"NAPT (IP Masquerade)","answer_id":12766},{"id":2946,"question":"Which of the following is a password attack that makes use of the possible combination of pre-computed hashes and passwords?","answer_label":"Rainbow table attack","answer_id":12771},{"id":2947,"question":"Which of the following is a spoofing attack?","answer_label":"An attack by masquerading as someone such as a superior person from an information systems department, or customer","answer_id":12775},{"id":2948,"question":"An administrator captures network packets and discovers that hundreds of ICMP packets have been sent to the host. However, it is not a particularly busy time of the day. Which of the following is the most likely the attack executed against the computer in this situation?","answer_label":"Denial of service","answer_id":12777},{"id":2949,"question":"Which of the following is a description of spyware?","answer_label":"A program that is installed on a PC against the user’s intention and collects information such as the user’s personal information and access history","answer_id":12783},{"id":2950,"question":"A security question is used to authenticate a user who forgets his/her password for a web system. After the correct answer is given, which of the following is the most appropriate process in terms of security?","answer_label":"Sending a URL that is difficult to guess to the user's pre-registered e-mail address so that the user can access a password reset page","answer_id":12787},{"id":2951,"question":"Which of the following is a role that a PKI certification authority performs as a reliable third party?","answer_label":"It issues a digital certificate that certifies a public key of a user or a server.","answer_id":12792},{"id":2952,"question":"Which of the following is an appropriate description concerning corporate security management when Software as a Service (SaaS) is used?","answer_label":"No system construction needs to be performed, and neither the definition of security requirements for application software development nor the design of storage volume for system logs is required.","answer_id":12794},{"id":2953,"question":"Which of the following is an appropriate description concerning BYOD and the associated information security risk?","answer_label":"An employee uses his or her own personal terminal for business purposes, which causes an increase in information security risks such as virus infections due to inadequate security settings.","answer_id":12799},{"id":2954,"question":"Between a client and a web server, which of the following is used for inspecting the data that is sent from the client to the web server and blocking attacks such as SQL injection?","answer_label":"WAF","answer_id":12804},{"id":2955,"question":"Which of the following is an appropriate description of honeypots?","answer_label":"Computer system designed to detect or counteract unauthorized access","answer_id":12806},{"id":2956,"question":"Which of the following is a module strength for the collection of multiple sequential functions, with internal passing of data?","answer_label":"Communicational strength","answer_id":12809},{"id":2957,"question":"Which of the following is the appropriate combination of Class and Object in Object Oriented Programming?\n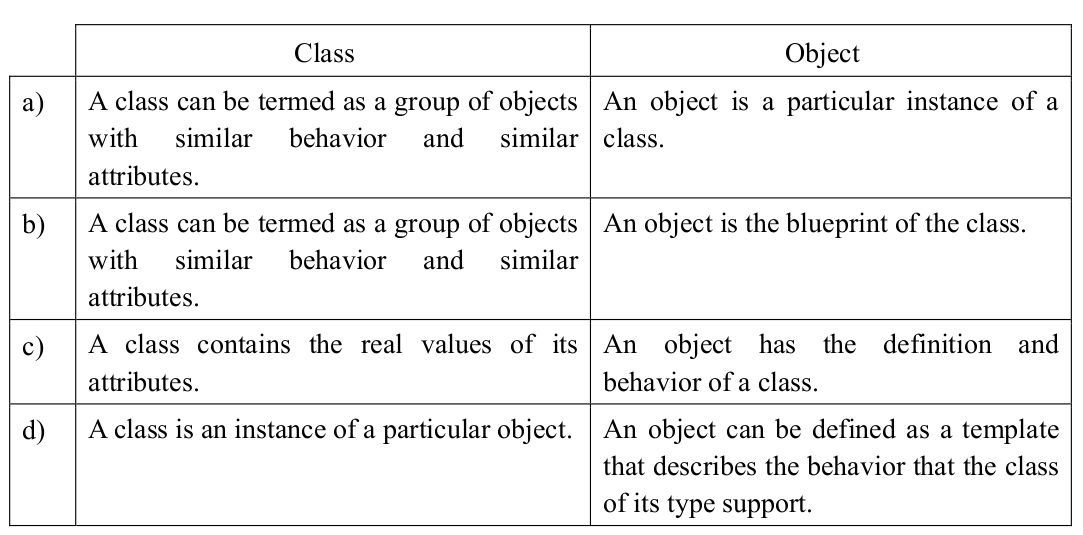","answer_label":"a","answer_id":12813},{"id":2958,"question":"Which of the following is an appropriate description concerning the black box test?","answer_label":"Even if the program to be tested contains redundant code, such code cannot be detected.","answer_id":12817},{"id":2959,"question":"Which of the following is an appropriate testing type to ensure that the interfaces and linkages between different parts of programs work properly?","answer_label":"Integration test","answer_id":12822},{"id":2960,"question":"Which of the following is an explanation of reverse engineering of software?","answer_label":"The existing software is analyzed, and its specification and structure are clarified.","answer_id":12826},{"id":2961,"question":"Which of the following is an appropriate description for group decision-making techniques used in an estimate activity durations process?","answer_label":"These are team-based approaches, such as brainstorming, the Delphi or nominal group techniques, which are useful for engaging team members to improve estimate accuracy and commitment to the emerging estimates.","answer_id":12831},{"id":2962,"question":"Which of the following is an appropriate description of the activities on the critical path of a project?","answer_label":"Any activity on the critical path is called a critical path activity.","answer_id":12833},{"id":2963,"question":"Which of the following is an appropriate cost estimation technique that uses parametric models to create an objective estimate based on each element size and the complexity of the system (e.g., number of input files, screens, etc.) to be built?","answer_label":"Function point method","answer_id":12839},{"id":2964,"question":"In order to determine the quality condition in a test process, it is necessary to analyze and evaluate the relationship between the number of completed test items and the cumulative number of bugs. Which of the following is the graph that indicates that the quality is becoming stable?\n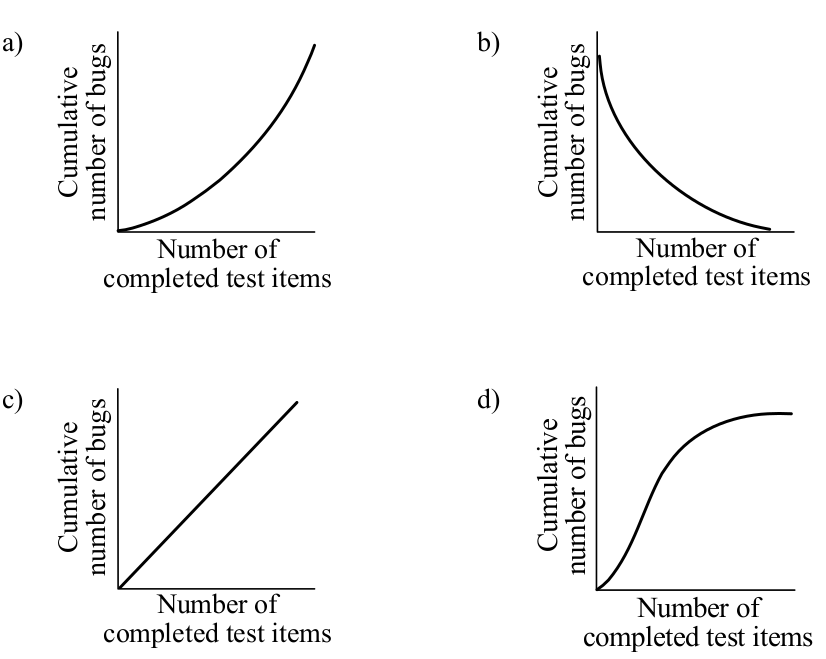","answer_label":"d","answer_id":12844},{"id":2965,"question":"When the development department and operations department of a system are organized separately, which of the following is an appropriate method of smoothly and effectively proceeding with the design and migration of a new service that needs system development?","answer_label":"The operations department also participates actively in the extraction of requirements concerning the system operations.","answer_id":12848},{"id":2966,"question":"In IT service management, which of the following is the most appropriate functional organization that provides a single point of contact and tries to provide rapid restoration of normal service operations to users?","answer_label":"Service desk","answer_id":12849},{"id":2967,"question":"Which of the following is an effective means of protecting an information system from the damage of over-voltage that occurs because of a lightning strike?","answer_label":"Connecting the communication cable and the computer through a surge protection device (SPD)","answer_id":12853},{"id":2968,"question":"Among the statuses found through auditing the operation management of the system operations, which of the following must be described in the audit report as a finding?","answer_label":"The operator decides a daily operation plan and approves it himself.","answer_id":12857},{"id":2969,"question":"Which of the following is the most appropriate description concerning an interview that is conducted by a system auditor?","answer_label":"The system auditor makes an effort to obtain documents and records that support the information obtained from the audited department during the interview.","answer_id":12864},{"id":2970,"question":"Which of the following is an explanation of audit work papers?","answer_label":"It is an execution record of the auditing procedure implemented by an auditor, and it forms the basis of the audit opinion.","answer_id":12868},{"id":2971,"question":"The table below shows the result of analyzing the activities of a sales representative on one (1) particular day. By installing Sales Force Automation (SFA), preparation time for customer visits can be reduced by 0.1 hours per customer visit. In order to increase the number of customer visits to six (6) per day without changing the total working hours and the hours per customer visit, how many hours must be reduced from “Other operation”?\n","answer_label":"0.7","answer_id":12871},{"id":2972,"question":"Which of the following is an explanation of SOA?","answer_label":"It is a system architecture that provides the components of a business process and its supporting IT infrastructure in the form of a service.","answer_id":12875},{"id":2973,"question":"Which of the following is an example of usage of big data by a company?","answer_label":"A large amount of text on various social media channels is analyzed, and the products are improved.","answer_id":12877},{"id":2974,"question":"Which of the following is an explanation of Business Intelligence (BI)?","answer_label":"It is a method of supporting the speedup of decision-making of a company by utilizing accumulated internal and external data through classification, processing, and analysis.","answer_id":12883},{"id":2975,"question":"Which of the following is the activity that translates the information gathered during analysis activities into a document as a set of requirements?","answer_label":"Requirement definition","answer_id":12887},{"id":2976,"question":"Which of the following is an explanation of green procurement?","answer_label":"It refers not only to the fulfillment of the requirements of quality and price but to the preferential purchase of products and services with the lower environmental burden from companies that work toward a reduction in their environmental impact.","answer_id":12889},{"id":2977,"question":"In SWOT analysis, which of the following is generally positioned as a threat?","answer_label":"Entry of strong companies in the market","answer_id":12893},{"id":2978,"question":"Which of the following is a leader strategy among the competitive strategies of a company?","answer_label":"Employing an omnidirectional strategy targeting all market customers with the aim of maintaining or improving profit and reputation, and securing optimum market share","answer_id":12899},{"id":2979,"question":"Which of the following is an explanation of Supply Chain Management (SCM)?","answer_label":"The sequence of business operations, from purchasing and production to sales and distribution, is reexamined within the company and among companies in view of total optimization, so as to accelerate delivery and minimize inventory.","answer_id":12904},{"id":2980,"question":"Which of the following is an appropriate example of a core technology?","answer_label":"It is an idling stop technology of an automobile engine that cannot be imitated by competitors.","answer_id":12907},{"id":2981,"question":"When trial production is performed for components to be loaded into electrical appliances, which of the following is the development method with the least overall cost? Here, the construction time of each process is six (6) months for the creation process, three (3) months for the modification process, and two (2) months for the evaluation process. Moreover, the cost per one (1) person-month is 6,000 dollars for the creation process, and 10,000 dollars for each of the modification process and evaluation process. However, costs other than the three (3) costs of the person-month cost, purchase cost, and outsourcing cost are not taken into consideration.\n","answer_label":"a","answer_id":12909},{"id":2982,"question":"The basic elements and examples of devices and services when IoT is used in the equipment maintenance tasks of a factory are compiled as shown below. When a) through d) correspond to any one of A through D, which of the following corresponds to A?\n","answer_label":"Temperature sensor for equipment","answer_id":12915},{"id":2983,"question":"Which of the following is a characteristic of MRP?","answer_label":"The number of required components is calculated based on the standard production plan of a product.","answer_id":12918},{"id":2984,"question":"Which of the following corresponds to (5) in an example of a model of an affiliate program shown below in Internet advertising? Here, (1) through (5) indicate the order of operations in the model, and each of (1), (2), (4), and (5) corresponds to one of a) through d).\n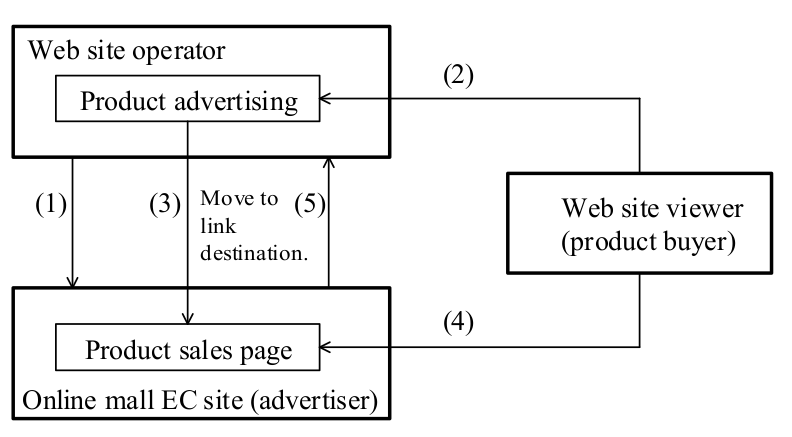","answer_label":"Pay a contingency fee in accordance with the sales of the product","answer_id":12923},{"id":2985,"question":"Which of the following is a part of total quality management?","answer_label":"Designing products and services that meet or exceed customers’ expectations","answer_id":12925},{"id":2986,"question":"When the weather tomorrow is sunny with 30% probability, cloudy with 50% probability, and rainy with 20% probability, which of the following strategies offers the highest expected value?\n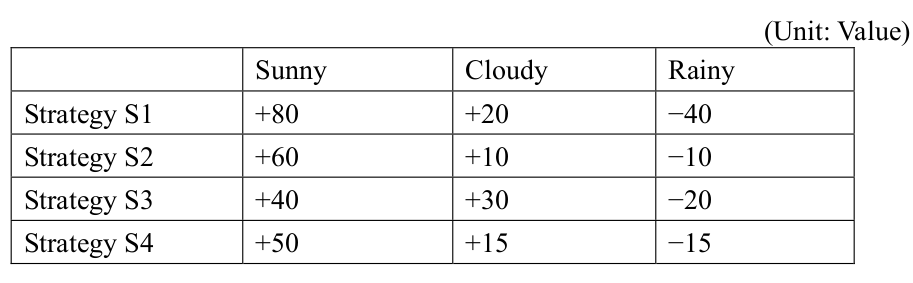","answer_label":"S1","answer_id":12929},{"id":2987,"question":"There are several quality control tools that have been used primarily for manufacturing and inspection departments. Which of the following sets two corresponding types of data on the vertical and horizontal axes, after which the measured values are plotted?","answer_label":"Scatter diagram","answer_id":12936},{"id":2988,"question":"Company Z is planning to start a new project of which the initial investment is 100 million dollars. It is expected to generate cash as shown in the following table. What is the payback period of the new project?\n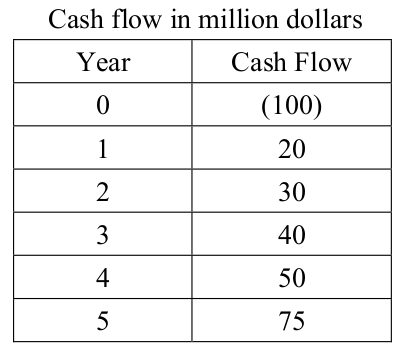","answer_label":"3.2","answer_id":12938},{"id":2989,"question":"Which of the following is an appropriate order of the workflow from transaction records to closing accounts?","answer_label":"Journal Book → General Ledger → Trial Balance Sheet→ Work Sheet → Financial Statements","answer_id":12943},{"id":3048,"question":"When F (v, w) is defined using standard predicate logic as shown below, which of the\nfollowing is the correct meaning of F (v, w)? Here, P (x, y) means “x is a parent of y ”,\nand W (x) means “x is a female”. In addition, “ ∃ x ∃ y P (x, y) ” means that there exist x\nand y such that P (x, y) is true.\n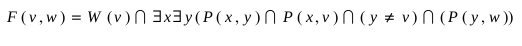","answer_label":"v is an aunt of w.","answer_id":13171},{"id":3170,"question":"Which of the following is the graph that is represented by the adjacency matrix A shown\nbelow? Here, an adjacency matrix is an n × n matrix in which both the element of row\ni and column j and another element of row j and column i become “1” when an edge\njoining the vertices V i and V j of a graph consisting of the “n ” number of vertices is\npresent, and “0” when the edge is not present.\n","answer_label":"d","answer_id":13674},{"id":3186,"question":"There is a three-dimensional array A starting with A[1, 1, 1] and ending with A[3, 5, 7],\nand consecutive integers starting with 0 are stored in ascending order. What is the\nmaximum value (in hexadecimal) of the integers that can be stored in the array? Here,\neach number in the answer list is written in radix notation.\n","answer_label":"a","answer_id":13726},{"id":3194,"question":"The flowchart below shows the algorithm that generates and prints a 4-digit decimal\nnumber where each digit is randomly generated and has a different decimal number.\nWhich of the following is the correct combination of expressions that can be inserted\ninto blanks A and B in the flowchart? Here, the function “random (0, 9)” is used to\ngenerate a random decimal integer from 0 through 9. The one-dimensional array “d”\nconsists of 10 elements d[0] through d[9].\n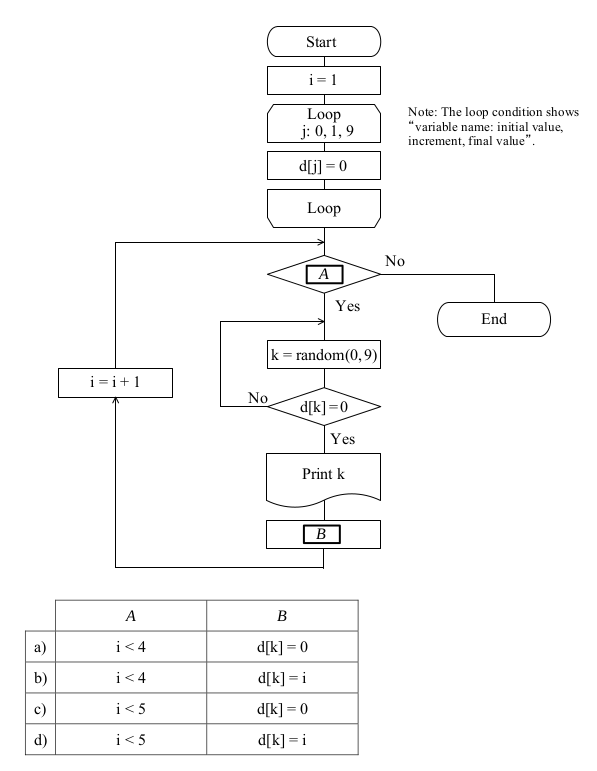","answer_label":"d","answer_id":13760},{"id":3201,"question":"Which of the following is the appropriate combination of characteristics of SRAM in\ncomparison with DRAM?\n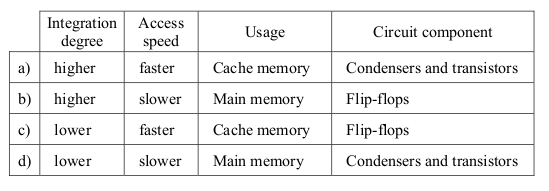","answer_label":"c","answer_id":13780},{"id":3210,"question":"Which of the following is the appropriate combination of indexes or indicators\nconcerning RAS (Reliability, Availability, and Serviceability)?\n","answer_label":"b","answer_id":13813},{"id":3213,"question":"","answer_label":"d","answer_id":13825},{"id":3217,"question":"A certain computer system runs in a multi-programming environment using a\nnon-preemptive “shortest job first” algorithm. In this system, when four CPU-bound\njobs P 1 through P 4 arrive at the job queue as shown in the table below, what is the\naverage waiting time (in minutes) of the four jobs in the queue? Here, the job queue is\nempty at the beginning, so the first job can be executed immediately after its arrival.\n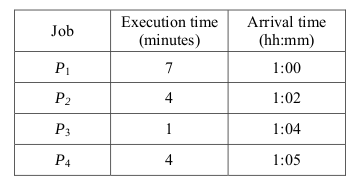","answer_label":"4.0","answer_id":13836},{"id":3225,"question":"In an LED lighting circuit with seven segments and one dot as shown below, when 6D\nin hexadecimal is written out to the output port, which of the following is displayed?\nHere, P7 is the most significant bit, P0 is the least significant bit, and each segment or a\nsmall dot of the LED lights up only when the corresponding bit is 1.\n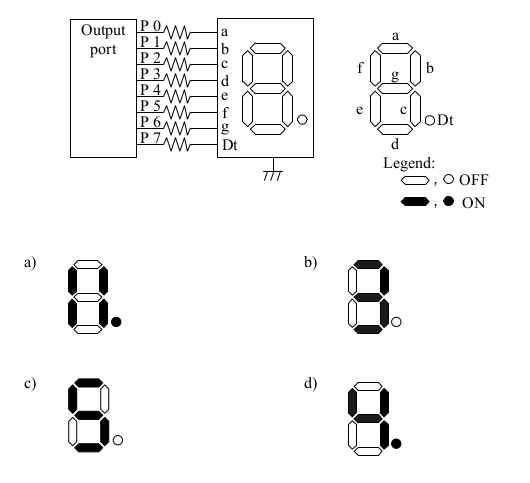","answer_label":"c","answer_id":13869},{"id":3226,"question":"Which of the following is an appropriate combination of Boolean expressions that are\nlogically equivalent to the logic circuit shown below? Here, “·” , “+”, and “ ⊕ ”\nrepresent the logical product, logical sum, and exclusive logical sum operations\nrespectively, and “ X ” is the logical negation of “ X ”.\n","answer_label":"b","answer_id":13872},{"id":3233,"question":"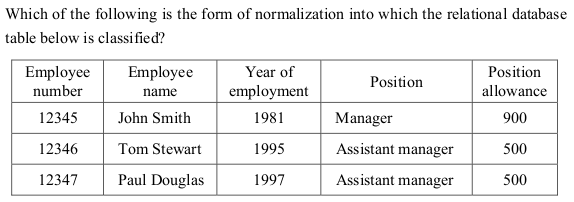","answer_label":"Second normal form","answer_id":13898},{"id":3238,"question":"The sales record for salespersons in a certain financial year at a company is shown in the\ntable below. Which of the following is an appropriate SQL statement that retrieves the\nname of the salesperson with average sales of $400,000 or higher for the year from the\n1st quarter (1Q) through the 4th quarter (4Q) and $300,000 or higher in sales for each\nindividual quarter? Here, the unit for the amounts in this table is 1,000 dollars.\n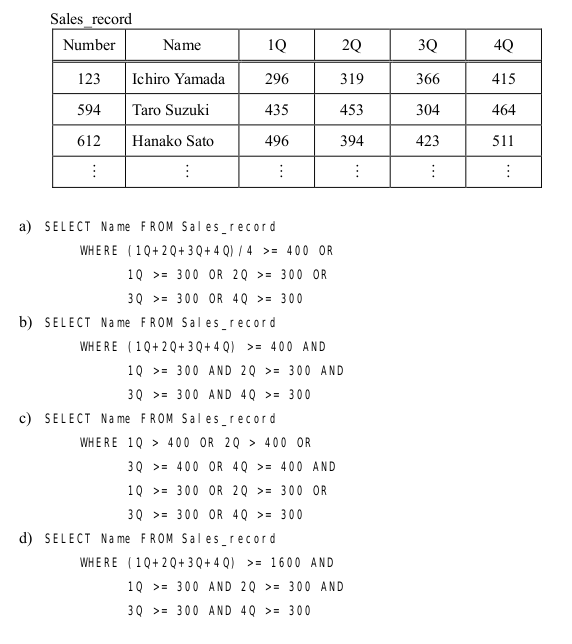","answer_label":"d","answer_id":13920},{"id":3254,"question":"","answer_label":"C","answer_id":13975},{"id":3264,"question":"As shown in the arrow diagram below, there exists a project consisting of nine activities\nA through I . When the number of days required for activity E is shortened from 9 days\nto 6 days, by how many days can the minimum number of days required for this project\nbe shortened?\n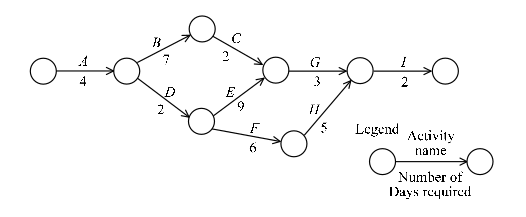","answer_label":"1","answer_id":14014},{"id":3292,"question":"As shown in the tables below, the 5-year investment effects of IT investment plans A\nthrough D are evaluated on the basis of ROI (Return on Investment). Which of the\nfollowing has the highest effect? Here, the internal rate of return (IRR) is 0, and ROI\nis calculated by dividing the total profit for the period by the amount of investment.\n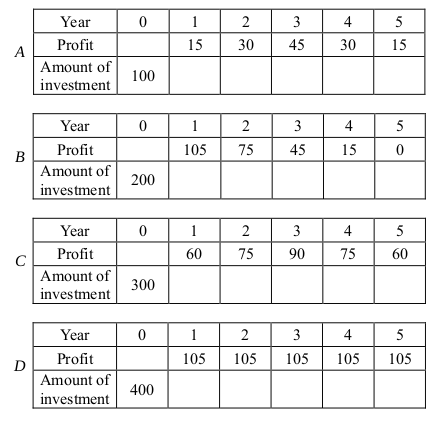","answer_label":"A","answer_id":14113},{"id":3296,"question":"Which of the following is applicable to “ A ” in the comparison table below that shows\nthe characteristics of each production system of continuous production, individual\nproduction, lot production, and process production?\n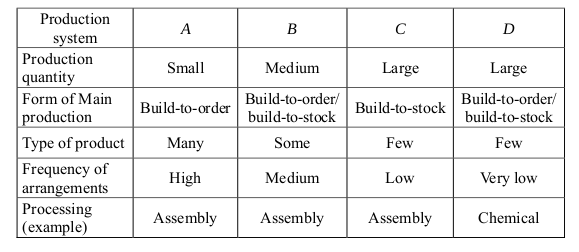","answer_label":"Individual production","answer_id":14129},{"id":3303,"question":"As shown in the table below, there are four tours provided by a tour company. The\ntable also shows the expected profit for each tour with accidents or without accidents.\nWhich of the following is the tour that is expected to make the highest profit according\nto the expected value principle?\n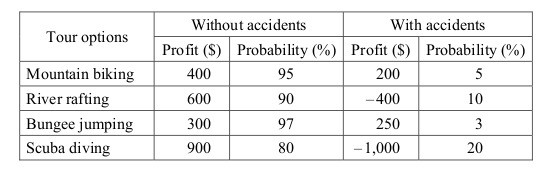","answer_label":"Scuba diving","answer_id":14157},{"id":3306,"question":"","answer_label":"When at least seven consecutive plots are above or below the center line","answer_id":14166},{"id":3308,"question":"Which of the following is the scatter diagram that shows a “negative correlation”?\n","answer_label":"b","answer_id":14171},{"id":3311,"question":"When the hexadecimal value 2A is stored in an 8-bit register and is logically shifted left\nthree bits, which of the following is the resulting value in decimal? Here, the bit\npositions vacated on the right are filled with zeros, and bits shifted out on the left are\ndiscarded.","answer_label":"80","answer_id":14180},{"id":3312,"question":"When two logical variables “p” and “q” are given, which of the following is a logical\nexpression that is equivalent to the XOR (exclusive OR) operation? Here, “∨”, “∧”,\nand “¬” represent the logical “OR”, “AND”, and “NOT” operations respectively.","answer_label":"(p ∨ q) ∧ ¬ (p ∧ q)","answer_id":14183},{"id":3313,"question":"A chemical manufacturer has a plan to deliver 500 liters of a 24% acid solution.\nHowever, the manufacturer has only two types of acid solutions available in its stock,\nwhich are 40% (Type A) and 20% (Type B). How many liters of each acid solution\nmust be mixed to make 500 liters of a 24% acid solution? UNIT: liter","answer_label":"Type A: 100, Type B: 400","answer_id":14186},{"id":3314,"question":"Each character in a text file is encoded as a double-byte character, and then the file is\ntransmitted with 4 KB header information through a serial communication interface at a\nspeed of 1,000 bps. When a text file consists of 100,000 characters, how long in\nseconds does it take to continuously transmit the file and its header? Here, 1 KB is\n1,000 bytes.","answer_label":"1632","answer_id":14193},{"id":3315,"question":"Which of the following is an appropriate set of sorting algorithms that are based on the\ndivide-and-conquer strategy?","answer_label":"Merge sort, quick sort","answer_id":14196},{"id":3316,"question":"When a series of data shown below is searched using the binary search algorithm, what\nis the minimum number of comparisons needed to find a value of 5?\n2, 5, 15, 16, 27, 27, 28, 40, 41, 51, 52, 55, 55, 57, 67, 79","answer_label":"3","answer_id":14200},{"id":3317,"question":"Which of the following is the most appropriate characteristic of XML?","answer_label":"XML can define any tag in order to make it easy to exchange data between\ninformation systems over the network.","answer_id":14202},{"id":3318,"question":"Which of the following is the appropriate course of actions to be taken by a processor\nat the occurrence of an interrupt?\n(1) Saving of the program register (i.e., program counter)\n(2) Transition from the user mode to the privilege mode\n(3) Determination of the start address of the interrupt processing routine\n(4) Execution of the interrupt processing routine","answer_label":"2->1->3->4","answer_id":14208},{"id":3319,"question":"Which of the following is an appropriate description concerning cache memory?","answer_label":"In machines with the large time gap between access to main memory and instruction\nexecution, the effective access time can be shortened by multi-level cache.","answer_id":14212},{"id":3320,"question":"Which of the following is an explanation of USB?","answer_label":"A serial interface to connect devices in a tree topology via hubs","answer_id":14214},{"id":3321,"question":"Which of the following is an appropriate explanation of a plasma display?","answer_label":"It consists of many tiny cells between two glass panels containing a mixture of noble\ngases with a phosphor coating, and displays images by using a gas discharge.","answer_id":14218},{"id":3322,"question":"Which of the following is a technique of dividing the data of each file into blocks of a\nfixed size, distributing and deploying those data blocks on multiple hard disks that can\nbe accessed in parallel, and thereby improving the file access speed?","answer_label":"Disk striping","answer_id":14224},{"id":3323,"question":"Which of the following is an appropriate characteristic of a Web system that is\nimplemented using the configuration of a three-tier client/server system?","answer_label":"A business process is executed on the server side, and the client software displays the\nresult on a screen according to the HTML coding.","answer_id":14226},{"id":3324,"question":"There are cases where the unused storage space is divided into lots of small and\nisolated areas because of repeated allocation and release of storage area by an OS.\nWhich of the following is the terminology applicable to such cases?","answer_label":"Fragmentation","answer_id":14230},{"id":3325,"question":"Which of the following is the virtual storage technique that can resolve external\nfragmentation rather than internal fragmentation by dividing virtual address space into\nfixed-length areas?","answer_label":"Paging","answer_id":14236},{"id":3326,"question":"Which of the following is an appropriate explanation of a benchmark test for computer\nsystems?","answer_label":"The relative processing power of each system is measured and evaluated by executing\na computer program, a set of programs, or other operations selected in accordance\nwith the purpose of usage.","answer_id":14239},{"id":3327,"question":"Which of the following is a technique that binds the modules constituting a program at\nthe time of executing the program?","answer_label":"Dynamic linking","answer_id":14242},{"id":3328,"question":"Which of the following is an OSS tool that is provided as the IDE (Integrated\nDevelopment Environment) of software?","answer_label":"Eclipse","answer_id":14247},{"id":3329,"question":"Which of the following is a sequential circuit that is capable of exhibiting either of two\nstable states and switching between them?","answer_label":"Flip-flop","answer_id":14252},{"id":3330,"question":"According to ISO 9241-210: 2010, which of the following is defined as the “extent to\nwhich a system, product, or service can be used by specified users to achieve specified\ngoals with effectiveness, efficiency, and satisfaction in a specified context of use”?","answer_label":"Usability","answer_id":14257},{"id":3331,"question":"Which of the following is an explanation of clipping in 3D graphics processing?","answer_label":"It is the process of defining a window within an image display area and removing\nobjects or parts of objects that lie outside the window.","answer_id":14258},{"id":3332,"question":"In a relational database, which of the following is an appropriate purpose of defining a\nforeign key?","answer_label":"To provide a constraint to maintain referential consistency between the records of\nrelated tables","answer_id":14263},{"id":3333,"question":"Which of the following is the unit of atomicity that a DBMS must guarantee for the\nupdate of a database?","answer_label":"From the start of a transaction to its commit or rollback operation","answer_id":14268},{"id":3334,"question":"Which of the following is an appropriate explanation of data warehouse?","answer_label":"A subject-oriented, integrated, time-variant, and non-volatile collection of data in\nsupport of management’s decision-making process","answer_id":14271},{"id":3335,"question":"Which of the following is the unit of transmission that is handled in the data link layer of\nthe OSI basic reference model and includes a header (and possibly a trailer) along with\nsome number of units of upper-layer data?","answer_label":"Frame","answer_id":14275},{"id":3336,"question":"In the traditional IPv4 addressing scheme, which of the following is the private IP\naddress range that is reserved for Class B?","answer_label":"172.16.0.0 through 172.31.255.255","answer_id":14280},{"id":3337,"question":"In a local area network using CSMA/CD as its access method, which of the following is\nan appropriate description concerning the transmission operation performed by a\nnetwork node?","answer_label":"Each node checks if the transmission medium is in use, and can transmit data if not\nin use. If a conflict is detected, retransmission is done after a random time interval.","answer_id":14283},{"id":3338,"question":"In the OSI basic reference model, which of the following is the appropriate layer that\nuses some common network programs and their corresponding protocols, such as\nHTTP, DHCP, and DNS?","answer_label":"Application layer","answer_id":14286},{"id":3339,"question":"In a TCP/IP network environment, which of the following is the most appropriate\ninformation used by a router in order to determine the routing path of a packet?","answer_label":"Destination IP address","answer_id":14290},{"id":3340,"question":"Which of the following is the attack where malicious input data is given to a Web\napplication to construct a database query or other data manipulation statements with the\naim of falsifying data or illegally acquiring information?","answer_label":"SQL injection","answer_id":14297},{"id":3341,"question":"Which of the following is an appropriate description of a directory traversal attack?","answer_label":"The attacker specifies files on the server by using a path that is unexpected by an\nadministrator, and gains unauthorized access to classified files.","answer_id":14301},{"id":3342,"question":"Which of the following is the most appropriate term that refers to the way in which a\ncompany collects any personal information about users via the company’s website and\nalso the way in which the company uses and protects such personal information?","answer_label":"Privacy policy","answer_id":14304},{"id":3343,"question":"Which of the following is the most appropriate method of determining whether to\nenable or disable communication that can be achieved by using the ARP mechanism\nfor a PC in which communication is requested?","answer_label":"The MAC address of the PC is checked, and communication is permitted only when\nthe MAC address has been registered beforehand.","answer_id":14306},{"id":3344,"question":"Which of the following is the most effective method for detecting the falsification of\ncontent on a Web server?","answer_label":"The hash value of each file containing the content of the Web server is stored and is\nperiodically compared with the hash value generated from each file.","answer_id":14311},{"id":3345,"question":"In a UML class diagram, which of the following is a direct relationship between one\nobject in a class and another object in another class and is graphically represented as a\nsolid line with or without an arrow?","answer_label":"Association","answer_id":14314},{"id":3346,"question":"Which of the following is an appropriate description concerning test data for a white box\ntest?","answer_label":"Test data is created on the basis of internal structures.","answer_id":14319},{"id":3347,"question":"When the quality of a software product is evaluated using the ISO/IEC 25000 series of\nstandards, which of the following is an appropriate quality characteristic that means the\ncapability of the software product to maintain a specified level of performance when it\nis used under specified conditions?","answer_label":"Reliability","answer_id":14325},{"id":3348,"question":"Which of the following is a type of integration test in which all the related program\nmodules are combined and tested at once regardless of the hierarchical structure after\nthe unit test for each module is completed?","answer_label":"Big bang test","answer_id":14326},{"id":3349,"question":"Among the maintenance activities of a system, which of the following is an appropriate\ndescription of adaptive maintenance?","answer_label":"The system is modified to cope with changes in the external environments.","answer_id":14333},{"id":3351,"question":"A chart or a diagram is created to resolve a quality problem. After the trends of\nfactors are analyzed, it is determined whether more than 80% of all the factors belong\nto a small group of factors. Which of the following is effective for this purpose?","answer_label":"Pareto chart","answer_id":14340},{"id":3352,"question":"Which of the following is an appropriate description of how to estimate person-months\nin software development?","answer_label":"In the function point method, the function points are defined and classified on the\nbasis of external input, external output, internal logical file, external interface file,\nand external inquiry.","answer_id":14344},{"id":3353,"question":"Which of the following is an appropriate inspection item that should be included in an\noperational test?","answer_label":"Ensuring that the system satisfies the requirements from the user’s viewpoint","answer_id":14349},{"id":3354,"question":"Which of the following is a characteristic of the one-time (or big bang) migration\nmethod that is one of the system migration methods?","answer_label":"A problem during migration has a very large impact on the new system.","answer_id":14350},{"id":3355,"question":"Which of the following is the primary purpose of the problem management process that\nis defined by ITIL v3?","answer_label":"To trace and eliminate the root cause of an incident, and to prevent the recurrence of\nthe incident","answer_id":14357},{"id":3356,"question":"An IT service is provided under the conditions described below. In order to meet the\nSLA, which of the following is the maximum allowable downtime (in hours) per\nmonth during service hours? Here, the number of business days in a month is 30.\n\n[Conditions of the SLA]\n• Service hours: 8 a.m. to 10 p.m. on business days\n• Availability: 99.5% or more","answer_label":"2","answer_id":14359},{"id":3357,"question":"When a version control system for source code is installed, which of the following is\nan appropriate item that should be added to system audit processes in order to check\nthe confidentiality of the source code?","answer_label":"The access control of the version control system must be set appropriately.","answer_id":14362},{"id":3358,"question":"Which of the following is an appropriate way of selecting systems that are subject to an\naudit based on risk assessment?","answer_label":"Systems that have a high possibility of occurrence of a problem and are significantly\naffected by the problem are subject to the audit.","answer_id":14369},{"id":3359,"question":"Which of the following is a management approach or technique that can be used for\nredesigning and restructuring the value-creating processes in an organization in order\nto gain significant benefits in productivity, profitability, service, and quality through\nmaximizing the potential of individuals and teams?","answer_label":"BPR","answer_id":14373},{"id":3360,"question":"Which of the following is an explanation of SaaS?","answer_label":"It is a service where the user can use the functions of application software via the\nInternet only when necessary.","answer_id":14374},{"id":3361,"question":"Among the costs related to computerization, which of the following is included in the\nrunning cost?","answer_label":"Maintenance cost of information equipment such as servers","answer_id":14381},{"id":3362,"question":"Which of the following is an explanation of the digital divide?","answer_label":"It refers to the social or economic gap that occurs depending on the level of\ninformation literacy and also on the differences in the usage environment of\ninformation technology.","answer_id":14384},{"id":3363,"question":"According to Michael Porter, who is the author of “Competitive Strategy”, which of\nthe following is the tool that is used to classify a company’s business activities into\nmain activities and supporting activities on a function-by-function basis in order to\nidentify key activities that generate the profit for the company and the possible benefit\nfor customers?","answer_label":"Value chain analysis","answer_id":14389},{"id":3364,"question":"Among the four stages, introduction, growth, maturity, and decline in the product life\ncycle, which of the following is a characteristic of the growth stage?","answer_label":"Customers are aware of product, and as a result, sales increase. However, profits\nmight sometimes decline for the company that first introduced the product, because\ncompetitors enter the market.","answer_id":14390},{"id":3365,"question":"Which of the following is an example of the strategic target and key performance\nindicator of a balanced score card from the viewpoint of customers?","answer_label":"Since the target is to establish a close and continuing relationship with the major\ncustomers, the number of complaints is the indicator.","answer_id":14395},{"id":3366,"question":"Which of the following is a pricing method that is based on the cost plus method?","answer_label":"Deciding the price by incorporating the desired margin in addition to the\nmanufacturing costs and business expenses","answer_id":14399},{"id":3367,"question":"Which of the following is a characteristic of an IC tag (i.e., RFID)?","answer_label":"An IC tag is resistant to dirt, and the recorded information is accessible from outside\nthe packaging","answer_id":14403},{"id":3368,"question":"Which of the following is the appropriate term applicable to the description below?\n\nIt is used to describe the economic concept or strategy of a certain Internet-based\nbusiness targeting less-competitive niche markets, which enables the business to gain\nsignificant profit in selling small volumes of hard-to-find items to many customers,\ninstead of selling large volumes of reduced number of popular items.","answer_label":"Long tail","answer_id":14408},{"id":3369,"question":"Which of the following is the methodology that performs both production scheduling\nand inventory control on the basis of steps (1) through (3) described below?\n\n(1) Based on the types and quantities as well as the component list of the product\nplanned to be manufactured during a fixed period of time in the future, the required\nquantity of components is calculated.\n(2) The net order quantity of each component is calculated from the amount of\ninventory that can be allocated.\n(3) The ordering point of each component is determined in consideration of the\nmanufacturing or procurement lead time.","answer_label":"MRP","answer_id":14413},{"id":3370,"question":"Which of the following is an appropriate reason for using a flash memory device as a\nbuilt-in memory feature of a one-chip microcomputer?","answer_label":"The program can be rewritten after the microcomputer is shipped.","answer_id":14416},{"id":3371,"question":"Which of the following is a specialization-oriented organization that is divided into\ngroups, such as research and development, manufacturing, sales, human resources,\ngeneral affairs, and accounting, according to the type of work performed?","answer_label":"Functional organization","answer_id":14419},{"id":3402,"question":"Which of the following is an appropriate explanation of an audit working paper?","answer_label":"It is an implementation record of the auditing procedure performed by an auditor, which forms the basis of the audit opinion.","answer_id":14534},{"id":3403,"question":"Which of the following is an appropriate description concerning the implementation structure of a system audit?","answer_label":"In order to enable the person requesting the audit to issue improvement instructions based on the audit report, the system auditor reports the audit results to the person requesting the audit.","answer_id":14535},{"id":3404,"question":"In the system design stage, which of the following is the point to be checked during the audit of control for reducing the risk of non-fulfillment of user requirements?","answer_label":"The user department should participate in the review of system design.","answer_id":14542},{"id":3405,"question":"Which of the following is an explanation of SOA?","answer_label":"SOA facilitates response to business changes by constructing software from components called services.","answer_id":14544},{"id":3406,"question":"Which of the following is an appropriate description of BPR (Business Process Reengineering)?","answer_label":"BPR is a management technique that is used to redesign and restructure the value-creating processes in an organization in order to gain significant benefits in productivity, profitability, service, and quality through maximizing the potential of individuals and teams.","answer_id":14550},{"id":3407,"question":"In computerization investment planning, which of the following is an explanation of the ROI that is an evaluation index for investment value?","answer_label":"ROI is a measure that is calculated by dividing the profit generated through factors, such as sales increase and cost reduction, by the amount of investment.","answer_id":14552},{"id":3408,"question":"Which of the following is the most appropriate action to be taken in order to eliminate the “digital divide”?","answer_label":"ncreasing learning opportunities for information literacy, and preparing an environment to further facilitate the use of information and telecommunications equipment along with information services","answer_id":14556},{"id":3409,"question":"According to “competitive strategy” proposed by Philip Kotler, which of the following is the company that has a small market share, but has the strategic aim of increasing income and acquiring a unique position by focusing management resources on particular products and services?","answer_label":"Market nicher","answer_id":14562},{"id":3410,"question":"When the effect of improvement is quantitatively evaluated, a weighted overall evaluation is used as a method of integrating and quantifying the results of the evaluation of multiple items. Which of the following is the improvement proposal that should be prioritized in the table below?\n\n","answer_label":"Proposal 2","answer_id":14564},{"id":3411,"question":"Which of the following is the business management technique that is used to develop specific targets and measures to implement a planned strategy, in consideration of the appropriate mutual relationships among four perspectives (i.e., financial, customer, internal business processes, and learning and growth)?","answer_label":"Balanced score card","answer_id":14567},{"id":3412,"question":"Which of the following is an explanation of the long tail?","answer_label":"The long tail refers to the situation where the sales percentage for a group of poor-selling products cannot be ignored in terms of the total sales of Internet shopping.","answer_id":14574},{"id":3413,"question":"Which of the following is the purpose of SCM?","answer_label":"To reduce costs and shorten delivery periods through integrated management of information across multiple companies or organizations from procurement to sales","answer_id":14578},{"id":3414,"question":"The figure below shows the transaction model of an escrow service that is used on an Internet auction site or such other transaction. Which of the following is the action that corresponds to (5) in this figure? Here, (1) through (6) indicate the sequence of transactions, and each of (3) through (6) corresponds to one of a) through d).\n\n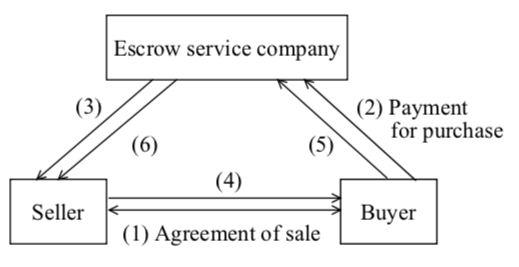","answer_label":"Notice of receipt of product","answer_id":14580},{"id":3415,"question":"Which of the following is an explanation of RFID?","answer_label":"RFID is a combination of an extremely small integrated circuit and an antenna, which is used for an electronic tag that enables an object to be identified and located by using the wireless automatic recognition technique.","answer_id":14583},{"id":3416,"question":"Which of the following is a chart or a diagram that is used to analyze possible relationships between two variables and is composed of a horizontal axis containing the measured values of one variable and a vertical axis representing the measurements of the other variable?","answer_label":"Scatter diagram","answer_id":14590},{"id":3417,"question":"When the relationship between the list price of a product and the demand for the product is defined as a linear expression, which of the following is an appropriate numerical value to be inserted into blank A below?\n(1) When the list price is set to 30 dollars, demand is 0 units.\n(2) When the list price is set to 10 dollars, demand is 60,000 units.\n(3) When the list price is set to 15 dollars, demand is A units.","answer_label":"45,000","answer_id":14594},{"id":3418,"question":"Which of the following is the forecasting technique that performs the procedure below in order to address problems that involve future prediction difficult to make by using other techniques?\n\n[Procedure]\n(1) Select some experts as respondents to questions.\n(2) Aggregate the responses to questions for use in feedback, and ask questions again.\n(3) Process the responses statistically, and present the responses together with their\ndistribution.","answer_label":"Delphi method","answer_id":14597},{"id":3419,"question":"As shown in the table below, a factory manufactures the three types of products: X, Y, and Z. How much is the maximum possible profit in dollars? Here, there is an upper limit of the monthly demand for each product. Also, the factory can be used up to 200 hours per month for product assembly, but multiple products cannot be assembled in parallel.\n\n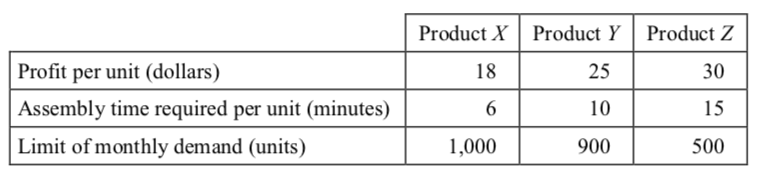","answer_label":"33,000","answer_id":14602},{"id":3420,"question":"Which of the following is the form of organization that has the characteristics (1) through (4) described below?\n(1) The organization is formed by assembling necessary experts from all departments to achieve strategic objectives.\n(2) The organization is a strategic organization that responds to changes in the environment, and is independent of functional departments.\n(3) The organization has the flexibility to dissolve if the expected objectives are achieved.\n(4) A task force team belongs to this form of organization.","answer_label":"Project organization","answer_id":14606},{"id":3421,"question":"The relationship between the value “x” of a certain factor in the manufacture of a product and the value “y” of a quality characteristic for the product is plotted as shown in the figure below,. Which of the following can be understood from this figure?\n\n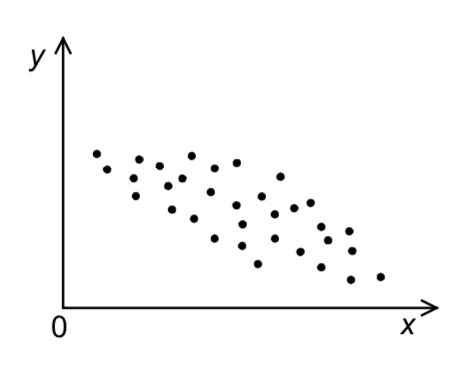","answer_label":"The correlation coefficient of x and y is negative.","answer_id":14608},{"id":3422,"question":"Which of the following is NOT protected by “copyright” that is based on the WTO’s\nAgreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"Programming language and its conventions","answer_id":14613},{"id":3431,"question":"Which of the following is equivalent to the result of the arithmetic expression “753₈ - A6₁₆”? Here, each number is written in radix notation; that is, the radix is represented by a subscript following the number.","answer_label":"325₁₀","answer_id":14648},{"id":3432,"question":"Which of the following is equivalent to the logical expression “not ( A ⩽ B or C < D )”? Here, A, B, C, and D are variables, and the resulting values of “ A ⩽ B ”\nand “ C < D ” can be either 1 for true or 0 for false.","answer_label":"A > B and C ⩾ D","answer_id":14651},{"id":3433,"question":"Which of the following is a logical equation that is equivalent to the logic circuit shown below? Here, the “ • ” is the logical product, “+” is the logical sum, and X is the negation of X.\n","answer_label":"c","answer_id":14656},{"id":3434,"question":"An empty tank can be filled with water in 20 minutes by using Pipe A or in 30 minutes by Pipe B, and the tank filled with water can be emptied of water in 40 minutes by using Pipe C. When the three pipes A, B, and C work together, approximately how long (in minutes) does it take to fill the empty tank with water?","answer_label":"17.1","answer_id":14660},{"id":3435,"question":"Among network topologies represented using graphs, which of the following can be regarded as a spanning tree?\n","answer_label":"c","answer_id":14664},{"id":3436,"question":"There is a two-dimensional array A with ten rows and ten columns. Each element in the array is two bytes long and is stored sequentially in memory in the customary “horizontal row first and vertical column second” order. When the first element A(1,1) is stored in memory address 500 that is represented in hexadecimal, what is the memory address of A(3,5) in hexadecimal?","answer_label":"530","answer_id":14667},{"id":3437,"question":"A leap year in the Gregorian calendar includes an extra day at the end of February. Any year that is divisible by 4 and does not end in 00 is a leap year. Years ending in 00 are leap years only if they are divisible by 400. How many leap years are there between 1895 and 2011 in the Gregorian calendar?","answer_label":"28","answer_id":14671},{"id":3438,"question":"There are two one-dimensional arrays A and B of size m and n respectively. Each array contains unique integer values sorted in ascending order. As shown in a sample figure below, these two arrays are merged into a single one-dimensional array C. Which of the following is the appropriate order of the computational complexity of this merge algorithm?\n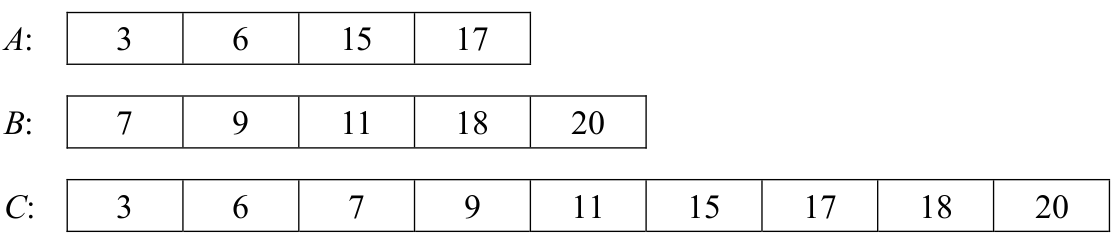","answer_label":"O ( m + n )","answer_id":14676},{"id":3439,"question":"Which of the following is the expression that represents the result “x” obtained by the series of three-address instructions below? Here, in a three-address instruction, an instruction using three operands “c = a op b” is represented as “op (a, b, c)”. “op” represents an operator. In the expression that represents the result “x”, priority decreases in order of *, /, +, and -.\n/ (c, d, w1)\n+ (b, w1, w2)\n/ (e, f, w3)\n- (w3, g, w4)\n* (w2, w4, x)","answer_label":"( b + c / d ) * ( e / f - g )","answer_id":14681},{"id":3440,"question":"Which of the following is the characteristic of pipeline control?","answer_label":"The processing of each instruction is divided into multiple stages in the processor, and thus multiple instructions are executed in parallel.","answer_id":14685},{"id":3441,"question":"Which of the following is a method of creating a program that can use the instruction cache effectively?","answer_label":"The frequently executed parts of the program are put together.","answer_id":14686},{"id":3442,"question":"In a virtual storage computer system with cache memory, main memory, and disk storage, it takes 2 nanoseconds, 10 nanoseconds, and 10 milliseconds, on average, to access data available in the cache, main memory, and disk storage, respectively. When the cache hit ratio and the main memory hit ratio (after a cache miss) are 0.95 and 0.99 respectively, which of the following is the approximate average time in microseconds to access the necessary data?","answer_label":"5.0","answer_id":14692},{"id":3443,"question":"When the size of a still image is 1 , 600 x 1 , 200 pixels and each pixel has a 256-level gray scale ranging from 0 to 255, approximately how many megabytes are needed at least to store five such still images?","answer_label":"10","answer_id":14696},{"id":3444,"question":"Which of the following is a self-luminous display that is classified as a kind of light-emitting diode technology?","answer_label":"OLED display","answer_id":14700},{"id":3445,"question":"Which of the following is an appropriate characteristic of a client/server system?","answer_label":"The server provides functions as services for the client and performs the intended application in cooperation with the client.","answer_id":14705},{"id":3446,"question":"In a client/server system, which of the following is the most appropriate advantage of using “stored procedures” that are available to all clients and do not need to be replicated in each client?","answer_label":"Data traffic between client and server can be reduced.","answer_id":14706},{"id":3447,"question":"Which of the following is the appropriate RAID configuration that provides disk striping at the block level rather than byte level and reserves one disk for parity information?","answer_label":"RAID4","answer_id":14713},{"id":3448,"question":"In an on-line real-time system, there occur transactions at a frequency of 20 times per second. Each of the transactions is completed after it performs the CPU processing once and the hard disk I/O processing four times. The I/O processing time of a hard disk drive is 40 milliseconds per each I/O, and the CPU processing time is negligibly small. When each hard disk drive is accessed evenly, at least how many hard disk drives are required for this transaction processing?","answer_label":"4","answer_id":14715},{"id":3449,"question":"In memory pool management for real-time systems that use memory resources of various sizes, which of the following is an appropriate characteristic of the fixed-length method in comparison with the variable-length method?","answer_label":"Memory efficiency is low, and processing speed to allocate or release memory is fast and constant.","answer_id":14720},{"id":3450,"question":"Which of the following is the method of improving the throughput of the entire system by transferring data from main memory to a low-speed output device via a high-speed auxiliary storage device?","answer_label":"Spooling","answer_id":14724},{"id":3451,"question":"Which of the following is an appropriate description concerning the use of an application on a computer with virtual memory?","answer_label":"Insufficient main memory causes excessive page faults during running the application and reduces the system throughput.","answer_id":14728},{"id":3452,"question":"A certain computer system runs in a multi-programming environment using a non-preemptive algorithm. In this system, two processes A and B are stored in the process queue, and A has a higher priority than B. The table below shows estimated execution time for each process; for example, process A uses CPU, I/O, and then CPU sequentially for 30, 60, and 30 milliseconds respectively. Which of the following is the estimated time in milliseconds to complete both A and B? Here, the multi-processing overhead of OS is negligibly small. In addition, both CPU and I/O operations can be executed concurrently, but I/O operations for A and B cannot be performed in parallel.\n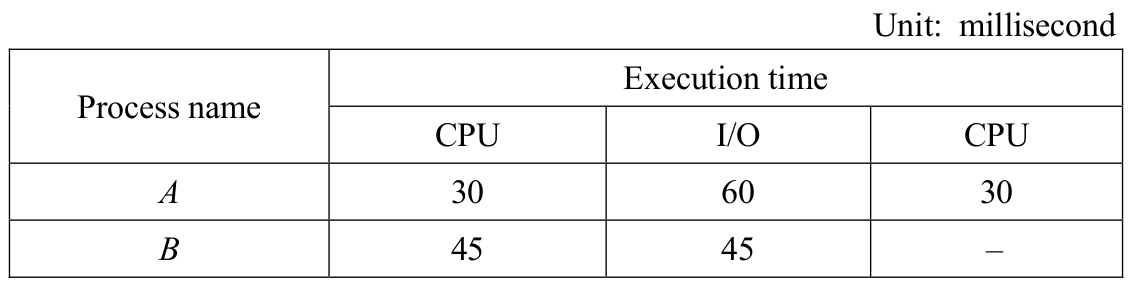","answer_label":"135","answer_id":14731},{"id":3453,"question":"Which of the following is the appropriate CASE tool that is prepared especially for the software development phases including program design, programming, and testing?","answer_label":"Lower CASE tool","answer_id":14736},{"id":3454,"question":"Which of the following is a language processor that can be used to create a program suited to the processing objectives, based on necessary conditions, such as input, process, and output, specified by parameters?","answer_label":"Generator","answer_id":14740},{"id":3455,"question":"Which of the following is the appropriate logic circuit with two inputs and one output where the output X is 0 only when the two inputs A and B are both 1s?\n","answer_label":"NAND circuit","answer_id":14743},{"id":3456,"question":"On a seven-segment LED lighting circuit as illustrated below, when 6D in hexadecimal is written out to the output port, which of the following is displayed? Here, P7 is the MSB (Most Significant Bit), and P0 is the LSB (Least Significant Bit). When 1 is written to a port, the corresponding LED segment is turned on.\n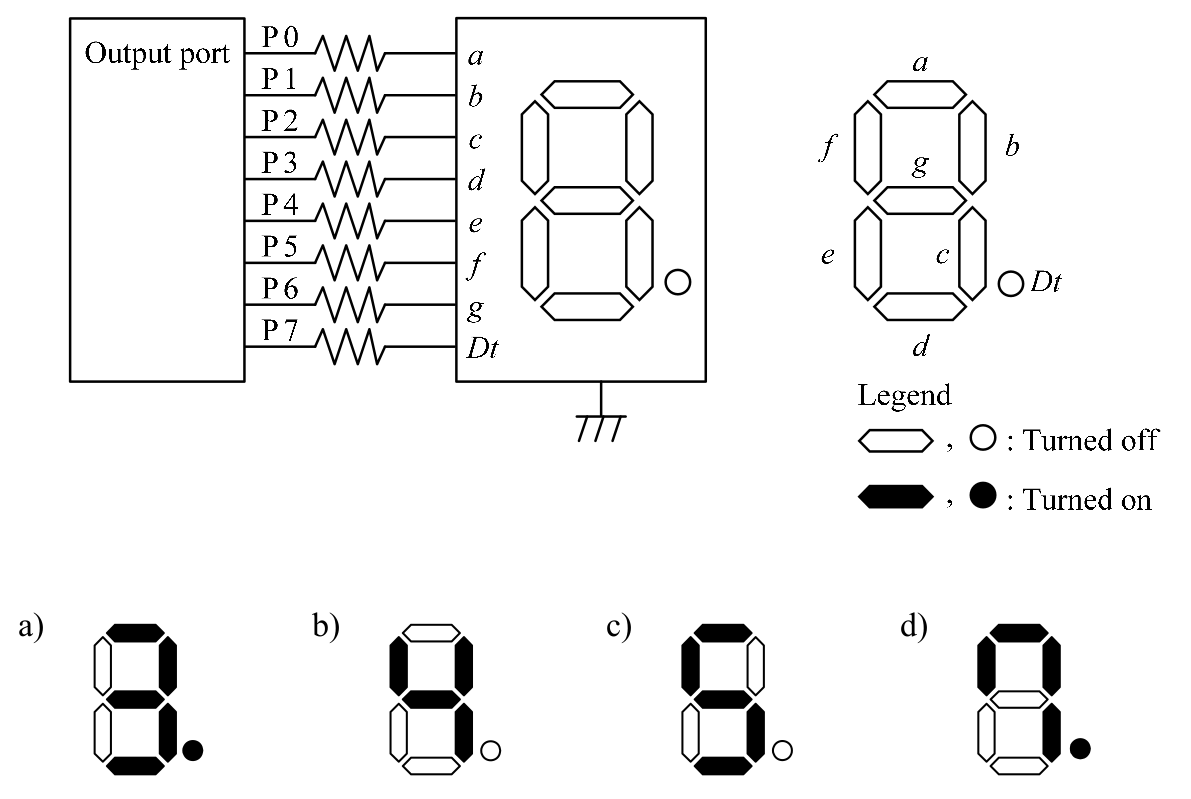","answer_label":"c","answer_id":14748},{"id":3457,"question":"Which of the following is an appropriate explanation of flash memory?","answer_label":"Data is written or erased electrically and erased either all at once or in blocks.","answer_id":14753},{"id":3458,"question":"When a GUI screen is designed for both users who are familiar with keyboard operation and users who are not, which of the following is an appropriate consideration to implement a user interface with good usability?","answer_label":"Both mouse and keyboard interfaces should be provided for as many operations as possible, in order to increase operational flexibility.","answer_id":14754},{"id":3459,"question":"Which of the following is the image processing technique that is used for pasting a two-dimensional image such as a pattern or design onto the surface of a modeled object?","answer_label":"Texture mapping","answer_id":14761},{"id":3460,"question":"Which of the following is a concept that is included in both E-R and Enhanced E-R diagrams?","answer_label":"Cardinality","answer_id":14762},{"id":3461,"question":"When the SELECT statement is executed to join two tables T1 and T2 as shown below, which of the following tables is created?\n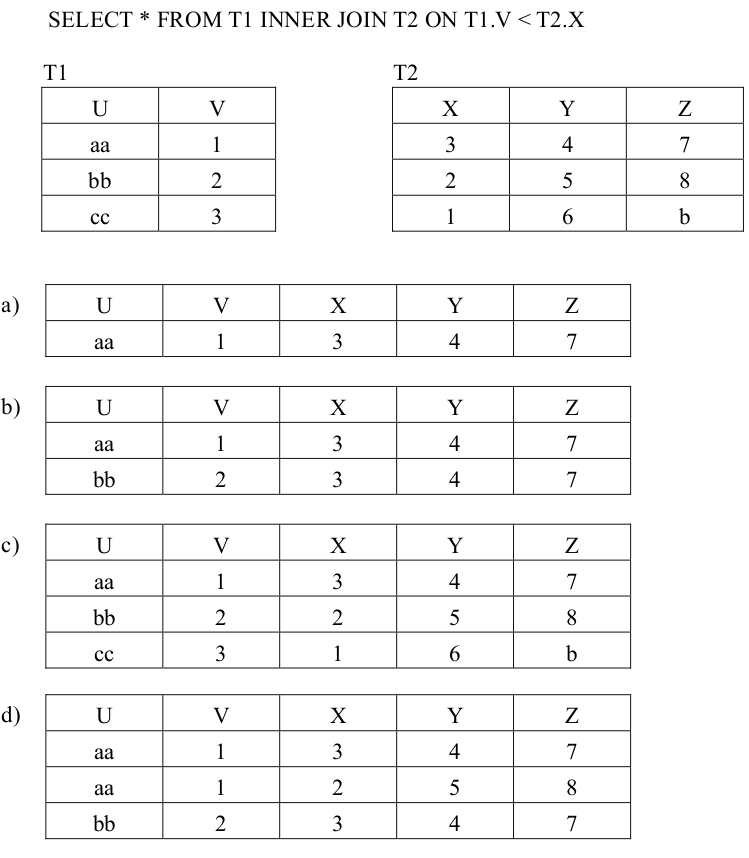","answer_label":"d","answer_id":14769},{"id":3462,"question":"Which of the following is the appropriate SQL command that can be used to undo any changes made to the database since the last commit?","answer_label":"Rollback","answer_id":14773},{"id":3463,"question":"Which of the following is the primary purpose of locking a resource in database management systems?","answer_label":"To maintain data integrity","answer_id":14775},{"id":3464,"question":"There is a database that manages user information (user database). From a viewpoint of security management, which of the following is the appropriate access privilege granted to an application program that searches the user database and displays the results? Here, the functions of privileges are described below.\n\n[Functions of privileges]\n- Read privilege: Records on the user database can be read.\n- Update privilege: Records on the user database can be registered, updated, and deleted.\n- Administrator privilege: Tables on the user database can be read, registered, updated, and deleted.","answer_label":"Read privilege","answer_id":14780},{"id":3465,"question":"Which of the following is an appropriate set of characteristics of a data warehouse in comparison with traditional databases?","answer_label":"Integrated, subject-oriented, non-volatile, and time-variant","answer_id":14783},{"id":3466,"question":"Which of the following is the broadcast MAC address that is used by multiple protocols, such as ARP (Address Resolution Protocol) and RIP (Routing Information Protocol), in order to transmit data to all of the hosts on the local subnet?","answer_label":"FF-FF-FF-FF-FF-FF","answer_id":14789},{"id":3467,"question":"In an IPv4 environment, when the subnet mask “255.255.255.224” is used for a class C network, how many IP addresses including reserved or ineffective addresses can be assigned to subnets and hosts per subnet respectively?\n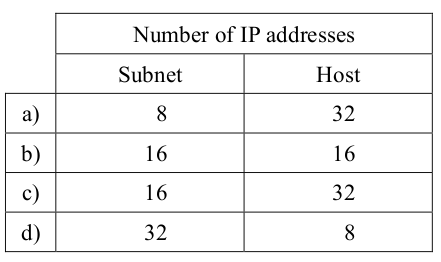","answer_label":"a","answer_id":14790},{"id":3468,"question":"Which of the following is the appropriate layer of the OSI basic reference model that provides RPC (Remote Procedure Call) support, maintains the integrity of the connection between nodes, and controls data exchange?","answer_label":"Session layer","answer_id":14797},{"id":3469,"question":"Which of the following is a connectionless protocol that offers speed and low overhead as its primary advantage in the transport layer of the OSI basic reference model?","answer_label":"UDP","answer_id":14801},{"id":3470,"question":"Which of the following is a protocol used by the ping command in order to verify that the communication link between source and destination is working in the TCP/IP network environment?","answer_label":"ICMP","answer_id":14803},{"id":3471,"question":"Which of the following is an appropriate combination of information that a DHCP server dynamically provides for a client host to participate in the TCP/IP network?","answer_label":"IP address, subnet mask, default gateway address, and DNS server address","answer_id":14808},{"id":3472,"question":"Which of the following is the appropriate combination that is defined as a socket address in TCP/IP network environments?","answer_label":"IP address and port number","answer_id":14810},{"id":3473,"question":"A message with a digital signature is received via e-mail. Which of the following can be checked by verifying the digital signature of the received message?","answer_label":"The message has not been falsified.","answer_id":14816},{"id":3474,"question":"When Mr. A sends his confidential message to Mr. B by using public key cryptography as shown in the figure below, which of the following is the appropriate key K used for encryption?\n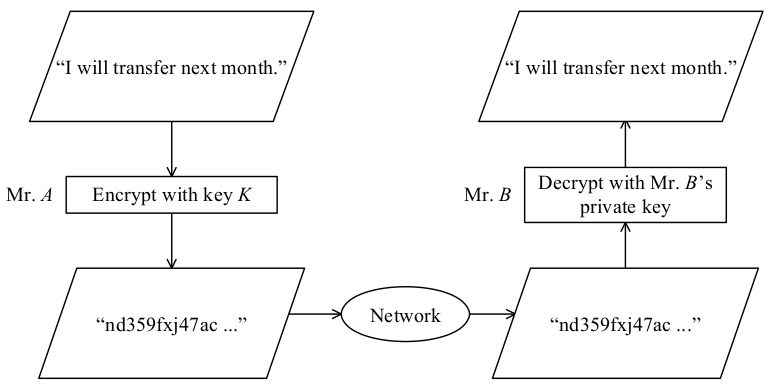","answer_label":"Mr. B’s public key","answer_id":14821},{"id":3475,"question":"Which of the following is a technique of social engineering that obtains sensitive or confidential data by searching for residual data left in a computer after job execution or by examining discarded or stolen media such as printed papers, tapes, and discs?","answer_label":"Scavenging","answer_id":14823},{"id":3476,"question":"Which of the following is a collection of infected computers that have been compromised without their owners realizing it and are being remotely controlled by attackers, in order to typically send spam or attack other computers?","answer_label":"Botnet","answer_id":14826},{"id":3477,"question":"A packet filtering-type firewall is installed at the connection point between an in-house network and the Internet. When the firewall makes possible access to the Web server (port number 80) on the Internet from a PC on the in-house network, which of the following is the appropriate combination that is permitted by the packet filtering rules?\n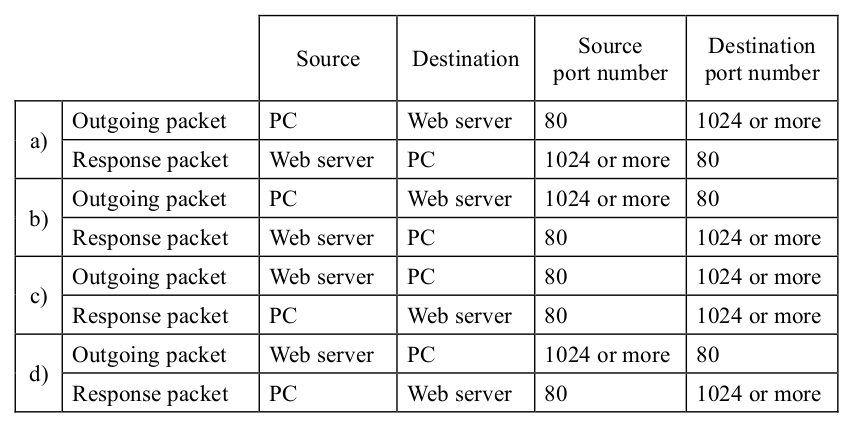","answer_label":"b","answer_id":14831},{"id":3478,"question":"Which of the following is a diagram used in UML2.0 for the purpose of depicting the interactions between the system, external systems, and users, or graphically describing who uses the system and in what ways the user expects to interact with the system?","answer_label":"Use case diagram","answer_id":14837},{"id":3479,"question":"Which of the following is the most appropriate statement concerning the use of frameworks in software development?","answer_label":"Frameworks can shorten the development period for software projects by taking advantage of the work and experience of others.","answer_id":14839},{"id":3480,"question":"In software development, which of the following is the most appropriate primary purpose of performing a system test?","answer_label":"To verify the functionality and operability of the deliverables principally on developer’s own responsibility in the production environment","answer_id":14842},{"id":3481,"question":"In object-oriented design, which of the following is a way to form new classes using classes that have already been defined and to take over data structures and procedures of the pre-existing classes referred to as base classes?","answer_label":"Inheritance","answer_id":14848},{"id":3482,"question":"Which of the following is an activity to be performed in software architecture design within the development process?","answer_label":"Determining how to implement software requirements already defined","answer_id":14851},{"id":3483,"question":"In a software test phase, when a bug control chart is used to evaluate test progress and software quality, which of the following is the most appropriate perspective to consider?","answer_label":"If the cumulative total number of completed test items, the cumulative total number of bugs, and the number of unresolved bugs all remain unchanged, it is necessary to check if the software has a bug that is hard to resolve.","answer_id":14854},{"id":3484,"question":"Which of the following is a technique that analyzes software or hardware and creates a design document, such as an E-R diagram based on the definition information of database system in the production environment?","answer_label":"Reverse engineering","answer_id":14860},{"id":3485,"question":"When a certain project includes activities A through H as shown in the arrow diagram below, which of the following is the earliest start date of avtivity H? Here, the number shown beside an arrow indicates the number of days required for each activity, and the project starts on day zero (0).\n","answer_label":"7","answer_id":14865},{"id":3486,"question":"Which of the following is the term that refers to a detailed breakdown of a project into a hierarchy of activities as shown in the figure below?\n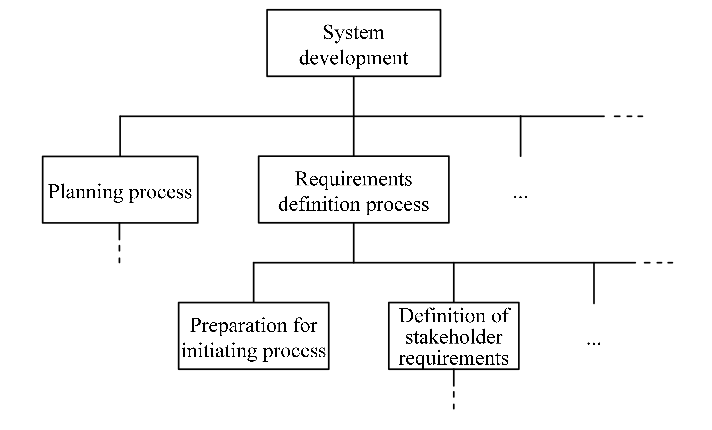","answer_label":"WBS","answer_id":14869},{"id":3487,"question":"It takes 36 days for Mr. A to complete a certain task, and 18 days for Mr. B to complete the same task. When Mr. A performs the task together with Mr. B, approximately how many days does it take to complete the task? Here, the task can be divided and performed in parallel, and both Mr. A and Mr. B can achieve an average working efficiency of 90 % every day during the cooperative task.","answer_label":"14","answer_id":14873},{"id":3488,"question":"When the number of programs composing the system and the number of person-days required for coding per program are as shown in the table below, what is the minimum number of staff members required to develop the system in 95 days? Here, in addition to coding, the activities of design and testing are also necessary to develop the system, and those activities require eight times as many person-days as coding.\n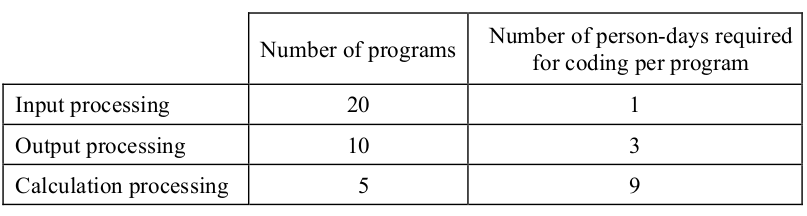","answer_label":"9","answer_id":14875},{"id":3489,"question":"According to ISO/IEC 20000-1:2011 (Information technology – Service management – Part 1: Service management system requirements), which of the following refers to an unplanned interruption to a service, a reduction in the quality of a service, or an event that has not yet impacted the service to the customer?","answer_label":"Incident","answer_id":14878},{"id":3490,"question":"An IT service is provided under the conditions described below. In order to meet the SLA, the maximum allowable downtime should be less than how many hours during the service hours per month? Here, the number of business days in a month is 30.\n\n[Conditions of the SLA]\n- Service hours: 7 a.m. to 9 p.m. (i.e. 14 hours per day) on each business day\n- Availability: 99.5% or more","answer_label":"2","answer_id":14883},{"id":3491,"question":"Company A issues an ID in the format shown below in the member registration processing. The table below shows the transition of the number of IDs issued by the end of each fiscal year. When this trend is assumed to continue in the future, in which fiscal year is Company A expected to run out of IDs in this format? Here, the IDs of resigned members are managed as vacant numbers and are not reused.\n\n[Format of the ID]\nXXNNN (e.g., AZ059)\n- For X, use an uppercase alphabetic character (A through Z).\n- For N, use a number (0 through 9).\n\n[Transition of the cumulative number of IDs issued by the end of each fiscal year]\n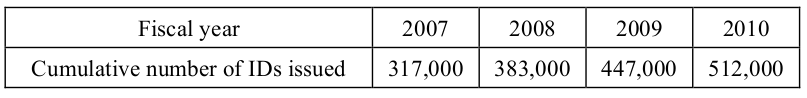","answer_label":"Fiscal year 2013","answer_id":14888},{"id":3492,"question":"When a hearing is conducted during a system audit, which of the following is the appropriate action to be taken by a system auditor?","answer_label":"When a problematic matter is found as a result of the hearing, backup data is collected and on-site investigations are conducted.","answer_id":14891},{"id":3493,"question":"Which of the following is pertinent to an audit finding in an audit of a user acceptance test?","answer_label":"The test is conducted by the information systems department without involving users, and the test results are approved by the person in charge of the department.","answer_id":14896},{"id":3494,"question":"From the viewpoint of internal controls, which of the following is a framework that can secure data integrity by means of a check and balance system in the organization?","answer_label":"The information systems department remains independent of the user departments that enter data, in order to ensure that the user departments can maintain the precision and accuracy of data.","answer_id":14899},{"id":3495,"question":"Which of the following is an appropriate explanation of SOA?","answer_label":"It is a design approach to architecture that builds software applications as reusable services and utilizes those services in a network such as the Internet in order to achieve a high level of productivity.","answer_id":14903},{"id":3496,"question":"Which of the following is an appropriate explanation of SCM (Supply Chain Management)?","answer_label":"It is a business process for managing the series of business operations linking purchase, production, sale, and distribution from the viewpoint of total optimization among companies in order to reduce delivery lead time and stock.","answer_id":14907},{"id":3497,"question":"Which of the following is the most appropriate explanation of system integration?","answer_label":"Necessary tasks related to an information system, such as planning, construction, and operations, are performed all together based on an underpinning contract.","answer_id":14912},{"id":3498,"question":"In verification of stakeholder requirements, which of the following means the ability to keep track of the process until the implementation of a change request related to a defined requirement is completed?","answer_label":"Traceability","answer_id":14916},{"id":3499,"question":"Which of the following is applicable to the definition of “ non-functional ” requirements?","answer_label":"Creating development criteria and standards suitable for the language used in system development","answer_id":14918},{"id":3500,"question":"The marketing strategies are categorized into four basic types: leader, challenger, follower, and nicher. The market follower is a firm that is not a market leader and that does not attempt to be a market leader. In addition, the follower can often find the reinvention of ideas easier than the originators. Which of the following is the basic strategy of the follower as a competitive position?","answer_label":"Imitation strategy for quickly responding to market opportunities","answer_id":14924},{"id":3501,"question":"The product life cycle is a concept based on the idea that all products pass through four stages: introduction, growth, maturity, and decline. Which of the following is the characteristic of the maturity stage in the product life cycle?","answer_label":"As demand increases, product differentiation and market segmentation become evident. Competition between competitors increases, and addition of new models and reduction of costs become important.","answer_id":14927},{"id":3502,"question":"Which of the following is a type of information system that helps companies change or otherwise alter their business strategy and structure and thus create a competitive advantage?","answer_label":"SIS","answer_id":14933},{"id":3503,"question":"Which of the following is an appropriate explanation of CRM?","answer_label":"It is a method for improving business performance by sharing information between all customer channels within a company and by increasing customer satisfaction.","answer_id":14934},{"id":3504,"question":"Which of the following is the characteristic of the cell production system where production is grouped into cells with each cell taking responsibility for the production of each product?","answer_label":"A single worker or a group of several workers completely assembles each product from start to finish.","answer_id":14939},{"id":3505,"question":"Which of the following is an appropriate explanation of XBRL?","answer_label":"It is a data description language developed for financial information exchange and reporting, based on XML (eXtensible Markup Language).","answer_id":14942},{"id":3506,"question":"Which of the following is the organizational structure that is given the authority and responsibility as an intrapreneur who performs a project as a semi-independent business unit and takes full responsibility for the outcome of the project?","answer_label":"In-house venture organization","answer_id":14948},{"id":3507,"question":"Which of the following is the appropriate rule for “brainstorming” that is a method of resolving problems?","answer_label":"Participants should listen to free-wheeling opinions, including unique ideas.","answer_id":14952},{"id":3508,"question":"Which of the following is an appropriate chart that can be used for planning the work schedule and for keeping track of the progress status in a project?","answer_label":"Gantt chart","answer_id":14956},{"id":3509,"question":"Which of the following is an appropriate explanation of the Delphi method that is a qualitative and exploratory forecasting approach?","answer_label":"It is a technique of obtaining the most reliable consensus of opinions from a group of experts through a series of questionnaires.","answer_id":14960},{"id":3510,"question":"Which of the following is an international standard that defines an encoding algorithm used to compress still image data?","answer_label":"JPEG","answer_id":14963},{"id":3602,"question":"When the equation 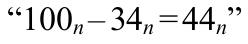 holds, which of the following represents  Here, each number is written in radix. In addition, when there is no subscript, the radix 10 is implied.radix notation; that is, each subscript “n” indicates the","answer_label":"22","answer_id":15325},{"id":3603,"question":"In the truth table shown below, which of the following is the correct combination of output values \n stands for the logical product, “+” for the logical sum,  for the exclusive OR, and  \nfor the logical negation of “ X ”.\n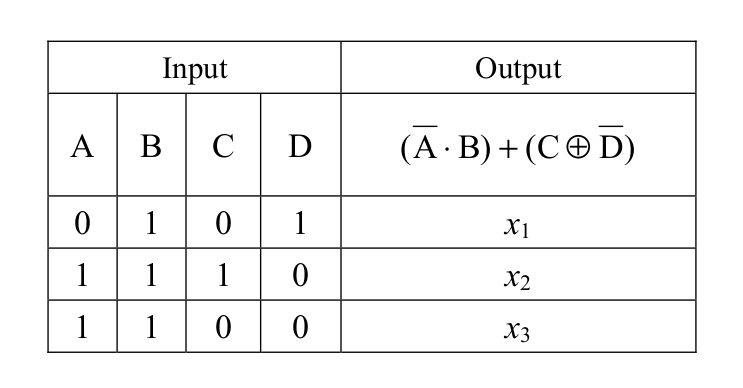\n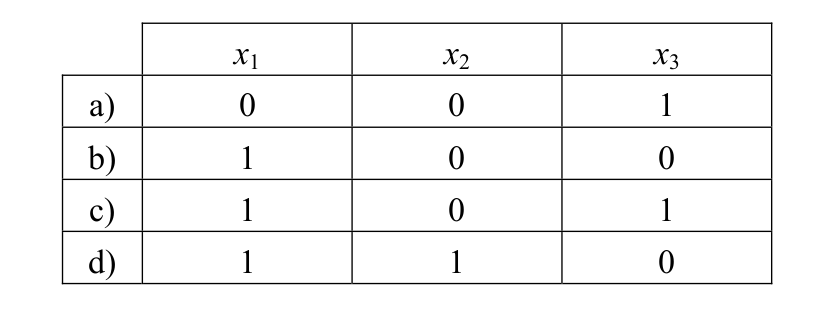","answer_label":"c","answer_id":15329},{"id":3604,"question":"Which of the following expressions can be used to calculate the quarter number (for example, “1” for January through March) for the n-th month of the year? Here, “n” ranges from “1” for January to “12” for December, and each fractional part of the resulting values is truncated.\n","answer_label":"b","answer_id":15332},{"id":3605,"question":"When the resulting value of the expression “13 × 16 + 11 × 16 + 9 × 16+ 3” is represented in binary, how many “1” bits are included in the binary value?","answer_label":"10","answer_id":15336},{"id":3606,"question":"When the simultaneous equations shown below hold for the Boolean variables w , x , y , and z , which of the following is the correct solution? Here, “+” stands for the logical sum operation, and “·” for the logical product operation.\n","answer_label":"c","answer_id":15341},{"id":3607,"question":"Tic-tac-toe, also known as noughts and crosses, is a popular game for two players, O and X, who take turns marking the spaces in a 3× 3 grid. The player who succeeds in placing three respective marks in a horizontal, vertical, or diagonal row wins the game. For example, the player O wins on the tic-tac-toe board shown below.\n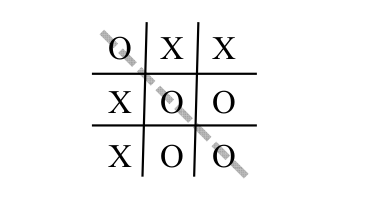\nHow many possible combinations of moves are there to fill all of the nine spaces, regardless of wins and losses?\n","answer_label":"c","answer_id":15345},{"id":3608,"question":"When three cards are randomly selected at a time from a standard deck of 52 playing cards, what is the probability that all of these three cards are in the same suit (heart, diamond, spade, or club)?\n","answer_label":"c","answer_id":15349},{"id":3609,"question":"When a linked list is used for queue implementation, which of the following structures provides the most efficient and effective way to perform both “insert” and “delete” operations? Here, the number of queue elements is variable, and the arrows shown in the figures represent link pointers.\n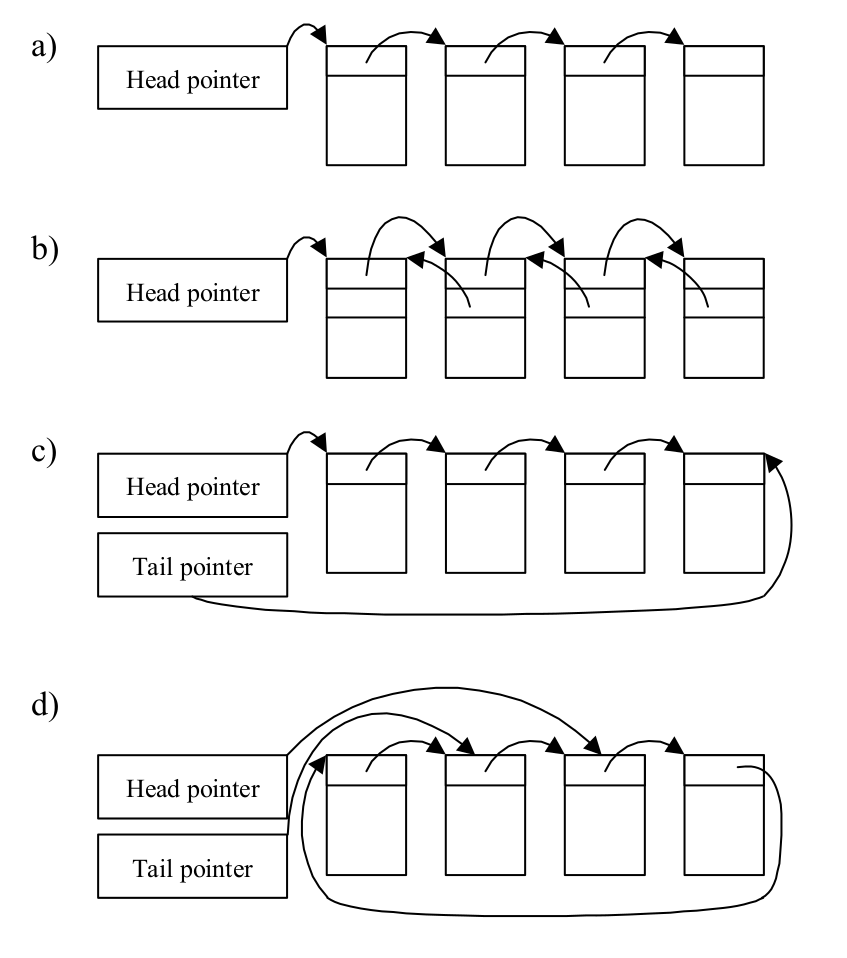","answer_label":"c","answer_id":15353},{"id":3610,"question":"Which of the following is an appropriate description concerning a binary search tree whose node values are 17, 6, 19, 3, 22, and 32?","answer_label":"No matter which value is placed at the root node, “3” cannot have a left child.","answer_id":15356},{"id":3611,"question":"In a binary tree,\n• any node that has two null children is called a leaf node, and\n• the other nodes except leaf nodes have one or two non-null children.\nWhen the number of nodes including leaf nodes is n , how many null children are included in the binary tree?","answer_label":"n + 1","answer_id":15362},{"id":3612,"question":"Which of the following data structures can be referred to as a “last-in first-out” operation?","answer_label":"Stack","answer_id":15366},{"id":3613,"question":"When the binary search algorithm is applied to the list of data sorted in ascending order as shown below, how many comparisons are needed to find the fact that “104” is not in the list?\n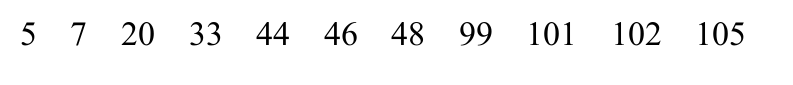","answer_label":"4","answer_id":15368},{"id":3614,"question":"When the expression 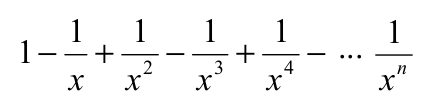 is calculated, which of the following should be inserted in the process box  in the flowchart shown below?\n\n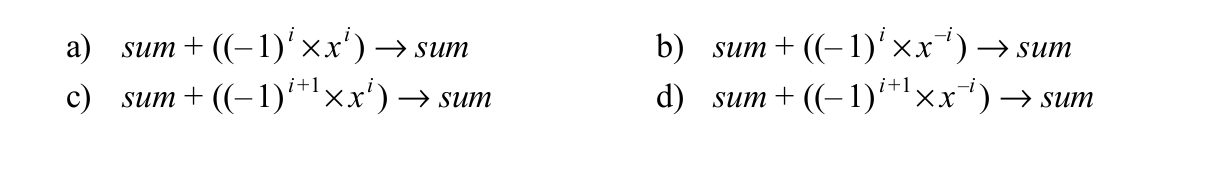","answer_label":"b","answer_id":15372},{"id":3615,"question":"Which of the following stands for the processor architecture in which a single stream of instructions can operate on multiple pieces of data in parallel?","answer_label":"SIMD","answer_id":15377},{"id":3616,"question":"Which of the following is classified as an internal interrupt?","answer_label":"Interrupt by divide-by-zero","answer_id":15379},{"id":3617,"question":"When a memory chip has 8 data lines and 9 address lines, what is the maximum number of bytes that can be stored in the chip? Here, chip select signals are implemented independent of those address lines, and no parity bit is considered.","answer_label":"512","answer_id":15385},{"id":3618,"question":"Which of the following is an optical disc that uses organic dye for the recording layer of the storage media and makes the traces of burning by laser light called pits to record the data?","answer_label":"CD-R","answer_id":15387},{"id":3619,"question":"Which of the following is an appropriate explanation of memory-mapped I/O?","answer_label":"is a technology for assigning the registers of I/O devices to the specifically dedicated I/O address space in main memory.","answer_id":15391},{"id":3620,"question":"Which of the following is the most appropriate explanation of grid computing?","answer_label":"By connecting multiple computers via a network, a high-performance system can be configured.","answer_id":15395},{"id":3621,"question":"As shown in the figure, this configuration consists of two systems. One performs on-line processing as an active system, and the other prepares for failure of the active system as a standby system. The standby system usually performs batch processing. What is this system configuration called?","answer_label":"Duplex system","answer_id":15400},{"id":3622,"question":"As shown in the figure, one server, three clients, and two printers are connected to the LAN. This system transfers the data on the server to a printer based on instructions from a client. When the availability of each device is as shown in the table, which of the following is the formula indicating the availability of this system? Here, the operation is considered normal if at least one of the three clients and one of the two printers are operating.\n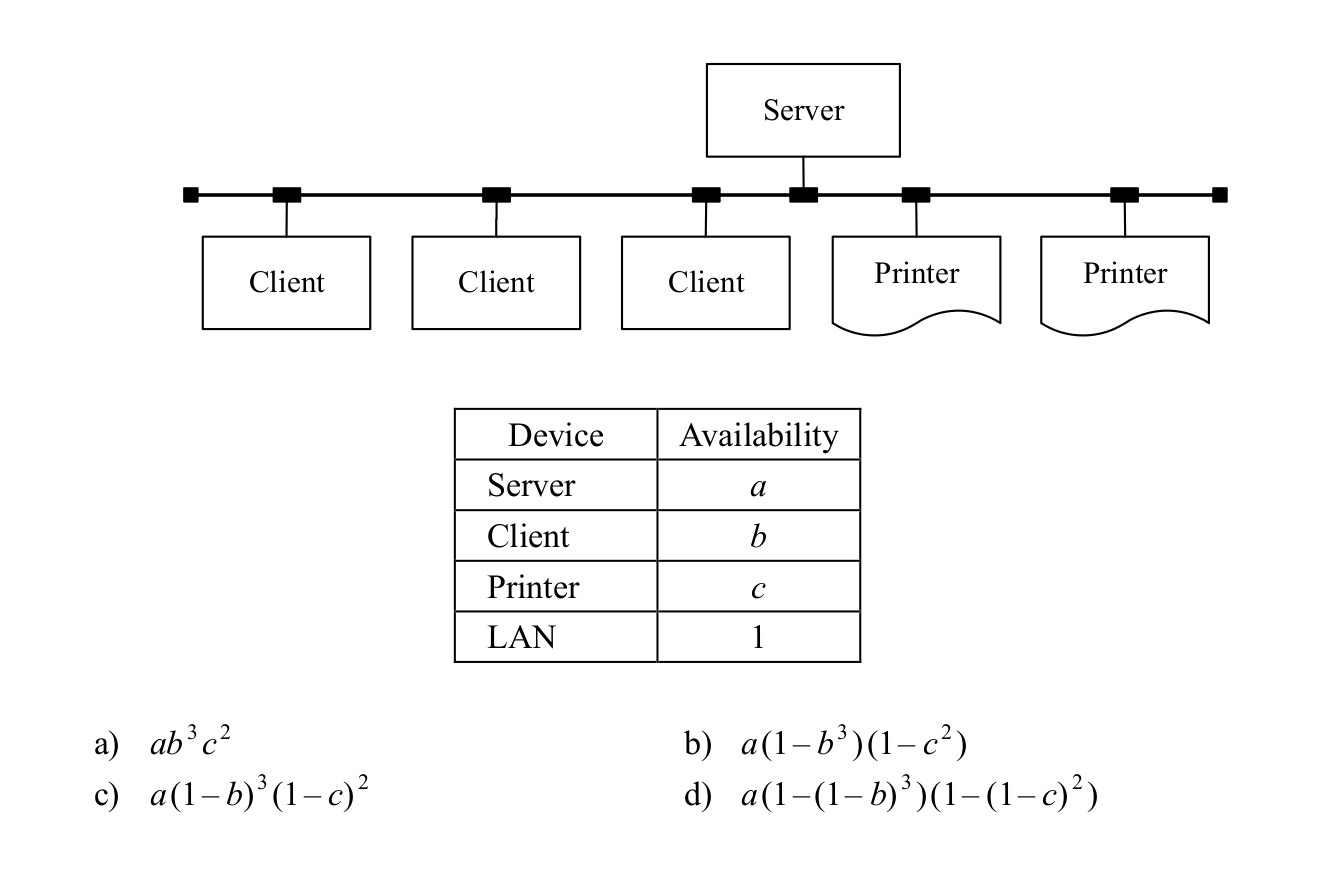","answer_label":"d","answer_id":15406},{"id":3623,"question":"The system operations model is shown in the figure. Which of the following is the appropriate combination of the expressions indicating MTBF and MTTR in this system? Here, 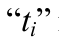\nrepresents the system operation time, and 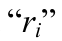 represents the system repair time (i = 1, 2, ..., n).\n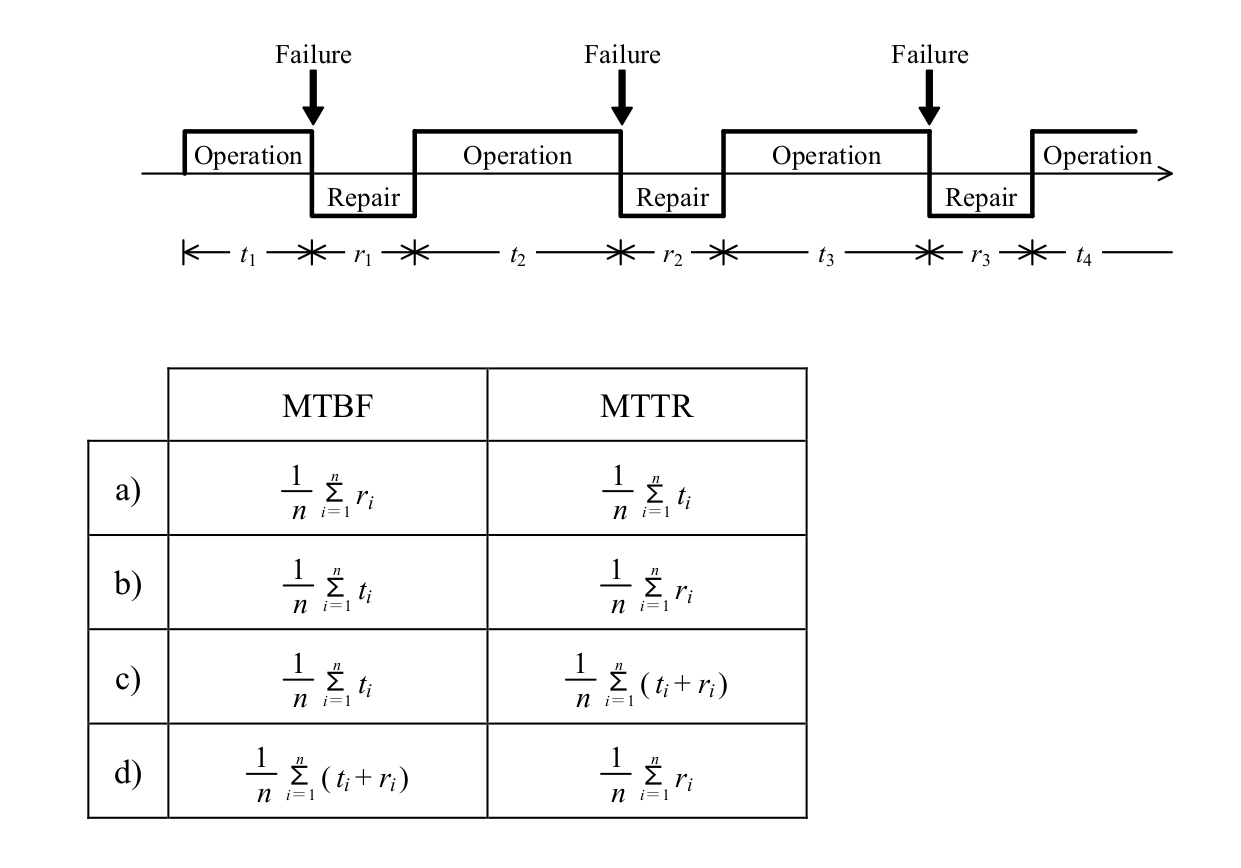","answer_label":"b","answer_id":15408},{"id":3624,"question":"A certain computer system runs in a multi-programming environment using a non-preemptive “shortest job first” algorithm. In this system, four processes A, B, C, and D arrive sequentially in the process queue every 1 millisecond. The table shown below includes estimated execution time for each process; for example, process A uses CPU, I/O, and then CPU sequentially for 4, 5, and 4 milliseconds respectively. Which of the following is the third completed process? Here, the multi-processing overhead of OS can be ignored, and both CPU and I/O operations can be executed concurrently.\n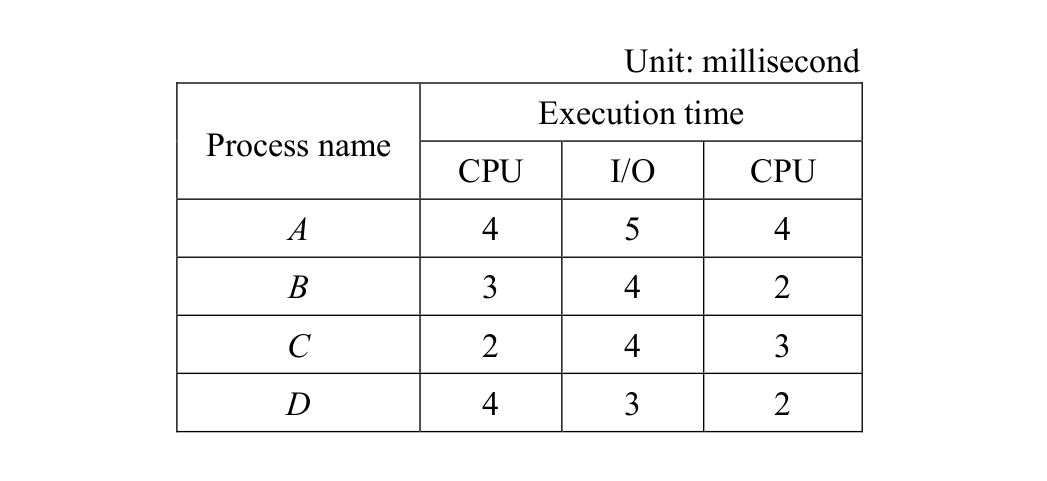","answer_label":"B","answer_id":15412},{"id":3625,"question":"In a certain file server system, it takes 15 ms to process one transaction if the target data is available in the disk cache. If the target data is stored in the hard disk in lieu of the disk cache, additional 75 ms for disk access is required to process it. When two-thirds of the number of transactions can be processed by using the disk cache data only, how many transactions per second on average can be consecutively handled in this system? Here, no parallel operation of disk access and data processing is performed. Overhead, such as communication and OS, can be ignored.","answer_label":"25","answer_id":15417},{"id":3626,"question":"There is a virtual memory system in which the FIFO or LRU page replacement algorithm can be used as a page replacement algorithm. There are 4 page frames available in real memory, and a process makes the list of page references as follows: 2 → 3 → 6 → 4 → 6 → 3 → 1 → 2 → 4 → 6. How many execution of this process using the FIFO and LRU page replacement algorithms page faults occur during separately? Here, all page frames are empty at the beginning of the process.\n","answer_label":"c","answer_id":15421},{"id":3627,"question":"Which of the following appropriately describes the role of task management?","answer_label":"It controls multiprogramming and uses the CPU effectively.","answer_id":15424},{"id":3628,"question":"Which of the following is the appropriate explanation of the hash method?","answer_label":"Access method that calculates the storing address of a record from its key value using a function","answer_id":15427},{"id":3629,"question":"Which of the following groups of CASE tools is used only in a particular stage of the software development life cycle and is designed to work cooperatively with other CASE tools in an integrated and consolidated environment?","answer_label":"Component CASE tools","answer_id":15431},{"id":3630,"question":"Which of the following is the appropriate explanation of DRAM?","answer_label":"It can represent one bit, depending on whether the capacitor is electrically charged or not. It is often used as main memory.","answer_id":15437},{"id":3631,"question":"As shown in the floor layout below, there are three sensors S1, S2, and S3 that control a light bulb in the middle of a hallway. The sensor S1 is a light sensor that generates the output signal “0” only when sunlight (or some other external light source) is detected. In case of no light, the output signal of S1 is “1”. The two sensors S2 and S3 are infrared sensors that generate the output signal “0” only when either S2 or S3 detects the movement of a thermal target in its effective range. If no movement is detected, the output signal is “1”. Which of the following logic circuits can be used to control a switch of signal “Bulb” of the given logic circuit is “1”. Sunlight streams in the hallwaythe light bulb? Here, the bulb is turned on only when the output through the windows, and the light bulb in the hallway does not affect the sensor S1.\n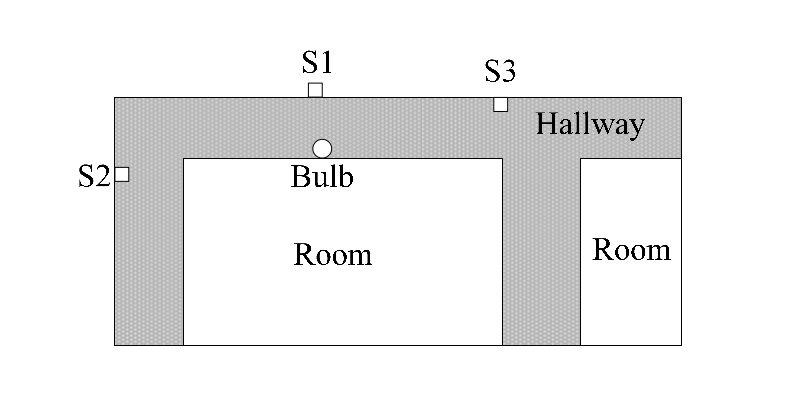\n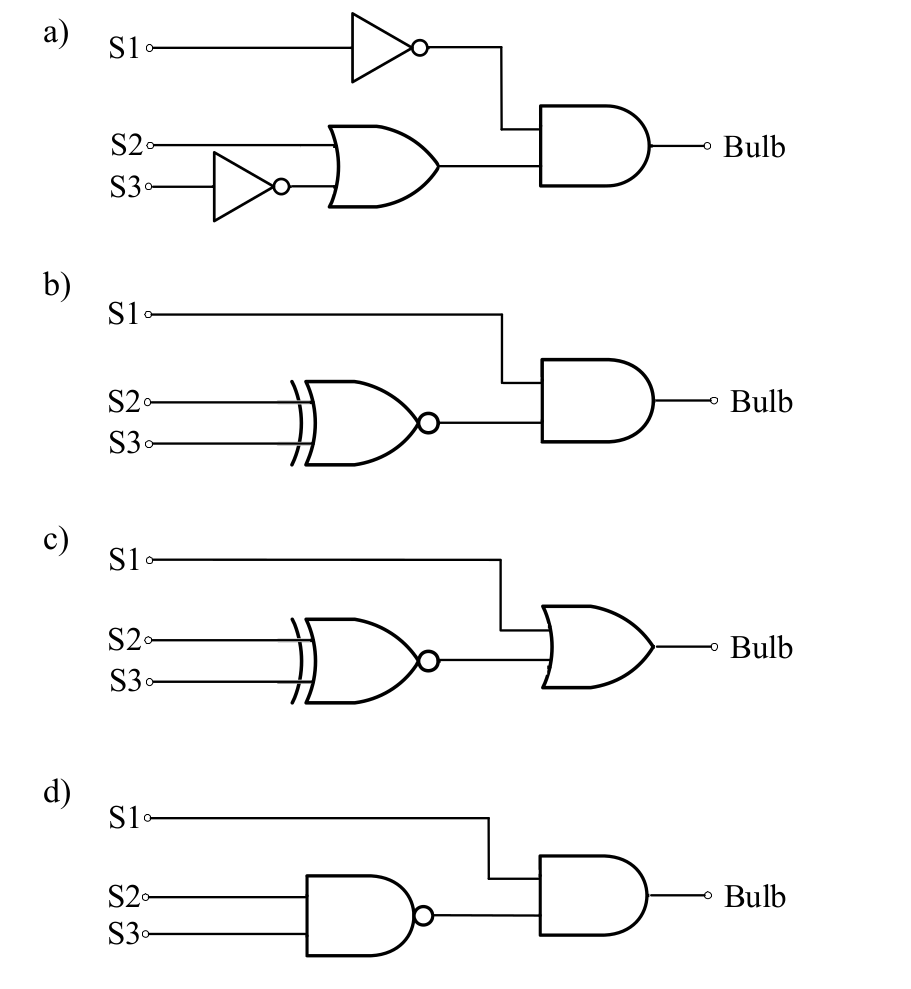","answer_label":"d","answer_id":15442},{"id":3632,"question":"The half adder in the diagram below adds one-digit binary numbers x and y, and produces z (the first digit of the sum) and c (carry) as output. Which of the following is the appropriate combination of elements A and B?\n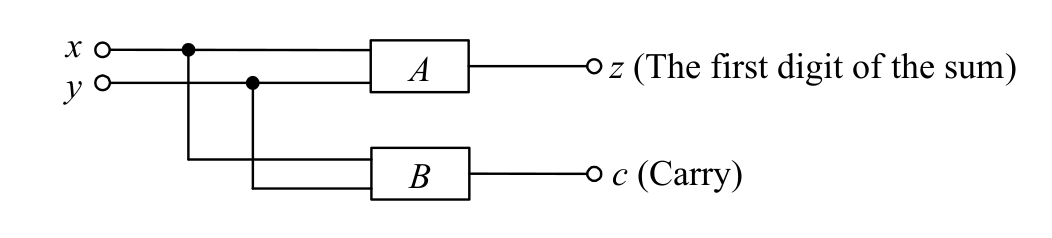\n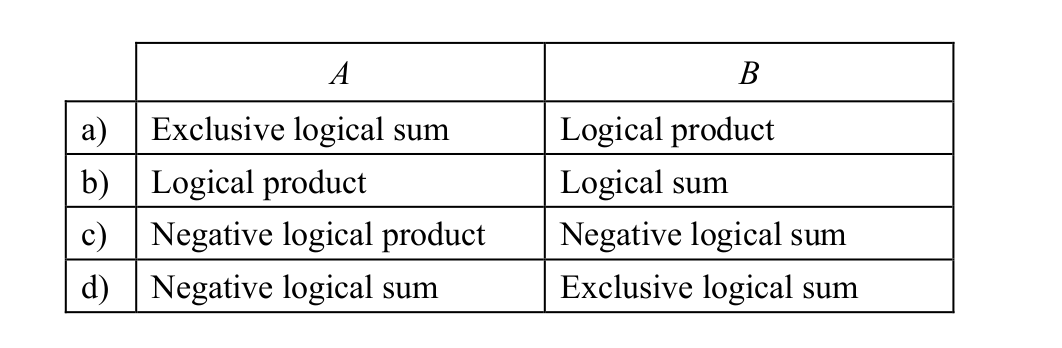","answer_label":"a","answer_id":15443},{"id":3633,"question":"Which of the following is an appropriate usage of a radio button that is a GUI component?","answer_label":"It is used to select one option from among a set of mutually exclusive options.","answer_id":15449},{"id":3634,"question":"Which of the following is a human interface design that is intended to improve the consistency of operations?","answer_label":"Designing operation buttons so that they have a common display location and shape on all screens","answer_id":15451},{"id":3635,"question":"Which of the following SQL statements corresponds to the “projection” operation of the relational algebra that can extract only the column “Continent” from the table “Country” and eliminate duplicates from the records returned?\n","answer_label":"d","answer_id":15458},{"id":3636,"question":"Among the ACID (Atomicity, Consistency, Isolation, Durability) properties of transactions, which of the following is the appropriate description concerning “atomicity”?","answer_label":"A transaction is a basic unit of processing; it must be performed in its entirety, or else it must be cancelled.","answer_id":15459},{"id":3637,"question":"When a database on a client/server system is accessed, which of the following is the function that can reduce the network load by preparing the instruction groups beforehand that are frequently used on the server?","answer_label":"Stored procedure function","answer_id":15465},{"id":3638,"question":"Which of the following is the appropriate description concerning exclusive control in a database?","answer_label":"When a shared lock is applied to a resource by a transaction, another shared lock can be applied to it by another transaction.","answer_id":15468},{"id":3639,"question":"Which of the following appropriately describes a characteristic of distributed database systems in comparison to centralized database systems?","answer_label":"Local queries and transactions accessing data at a single site have better performance because of the smaller local databases.","answer_id":15474},{"id":3640,"question":"Which of the following protocols can be used to temporarily assign an IP address leased from the pool to the host that asks for an address or to repeatedly assign the same IP address to the host according to the MAC address of the host?","answer_label":"DHCP","answer_id":15476},{"id":3641,"question":"Which of the following can be used to interconnect multiple LANs on the network layer (layer 3) of the OSI basic reference model and to relay packets of data?","answer_label":"Router","answer_id":15482},{"id":3642,"question":"When the subnet mask 255.255.255.240 is used for a server, which of the following is a valid IP address of the server?","answer_label":"195.206.108.25","answer_id":15485},{"id":3643,"question":"Which of the following is the signaling protocol that is widely used to initiate, manage, and terminate multimedia communication sessions, such as voice and video calls over the Internet?","answer_label":"SIP","answer_id":15488},{"id":3644,"question":"Which of the following is a security feature that can allow network administrators to specify exactly which stations should have access to the wireless network?","answer_label":"MAC address filtering","answer_id":15492},{"id":3645,"question":"Which of the following can be achieved by receiving mail text and its hash value from the sender and comparing the hash value with the one calculated from the mail text by the receiver? Here, the hash value from the sender is protected.","answer_label":"Detection of presence or absence of falsification","answer_id":15496},{"id":3646,"question":"When the judgment threshold is changed in a biometric authentication system, which of the following shows the relationship between FRR (False Rejection Rate) and FAR (False Acceptance Rate)?","answer_label":"As FRR decreases, FAR increases.","answer_id":15500},{"id":3647,"question":"As shown in the figure, an application on a client has access to the database on a server via a pair of database connection programs. Which of the following is the appropriate measure for preventing the data transmitted and received between the database connection programs from being wiretapped on a communication line?\n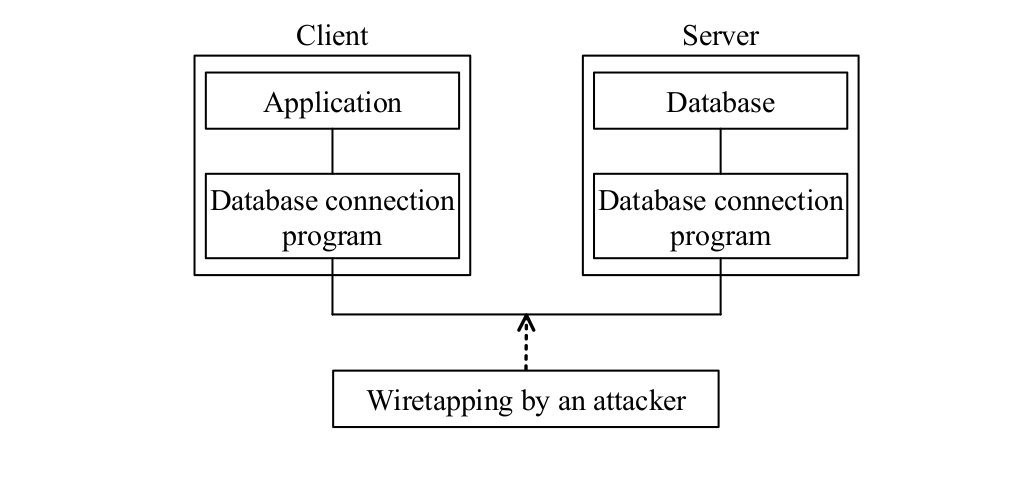","answer_label":"Encrypting the communication between the database connection programs on the client and server sides","answer_id":15504},{"id":3648,"question":"Which of the following sends a program incorporating fraudulent functions, such as destruction and falsification of data, for installation and execution?","answer_label":"Trojan horse","answer_id":15510},{"id":3649,"question":"A Web server was invaded from the outside, and its contents were falsified. Which of the following is the appropriate sequence of subsequent activities?\n","answer_label":"d","answer_id":15514},{"id":3650,"question":"Which of the following systems is the most suitable for a design using a state transition diagram?","answer_label":"A greenhouse control system, which keeps the optimum environment in a greenhouse based on the information of the installed sensors","answer_id":15515},{"id":3651,"question":"Which of the following appropriately describes “efficiency” that is one of six software quality characteristics defined in ISO/IEC 9126-1?","answer_label":"The capability of the software product to provide appropriate performance, relative to the amount of resources used, under stated conditions","answer_id":15522},{"id":3652,"question":"Which of the following is an example of the relationship between the base class and the subclass in object orientation?","answer_label":"“Figure” and “triangle”","answer_id":15525},{"id":3653,"question":"Which of the following is the appropriate purpose of regression test?","answer_label":"To verify the functionality of the upgraded system against a baseline system to ensure that any existing system capabilities have not been adversely impacted","answer_id":15530},{"id":3654,"question":"Which of the following is the appropriate description concerning standardization in programming?","answer_label":"Defining programming conventions is effective for preventing errors that programmers tend to make.","answer_id":15531},{"id":3655,"question":"The test data about the part of a program shown in the flowchart is specified by “decision condition coverage” (branch coverage). If this test data is specified by “multiple condition coverage,” which of the following is the appropriate data to add? Here, the part enclosed in parentheses indicates the pair of test data elements.\n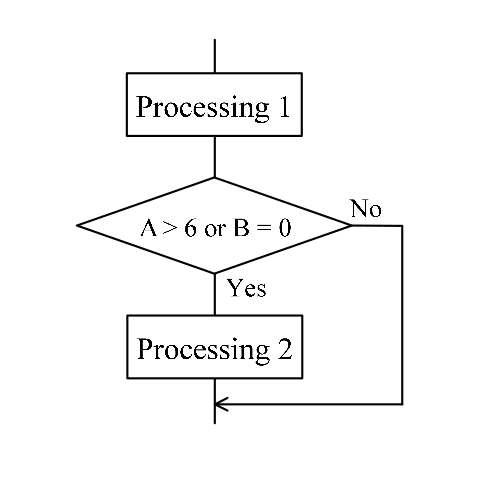\nThe test data used by “decision condition coverage” (branch coverage):\n(A = 4, B = 1), (A = 5, B = 0)\n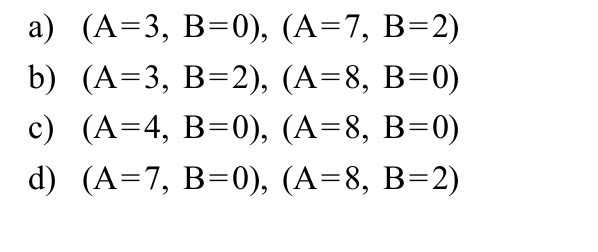","answer_label":"d","answer_id":15538},{"id":3656,"question":"The number of remaining bugs in software is estimated by bug-embedding method. The number of captured bugs by testing is 48. The number of bugs found by testing is 16 out of 22 embedded bugs. How many bugs are estimated to be still hidden? Here, the number of the embedded bugs found in the test is proportional to the number of the bugs found in the software.","answer_label":"18","answer_id":15541},{"id":3657,"question":"Which of the following is the model that can be used to guide process improvement and to assess the capability level and the maturity level of a project, a division, or an entire organization?","answer_label":"CMMI","answer_id":15543},{"id":3658,"question":"The table below shows the series of activities for a certain project. The numbers in the table indicate the cost of each activity and how long (in weeks) it takes to complete each activity. Prior to starting each activity, the previous activities shown in the table must be completed. When the weekly cost of the project is minimized without delay of the project, what is the highest weekly cost in dollars during this project? Here, the weekly cost remains stable and unchanged during each activity.\n","answer_label":"750","answer_id":15549},{"id":3659,"question":"The execution plan for the system development project is prepared, and the critical path is obtained. Which of the following is the activity that can be understood by means of the critical path?","answer_label":"The activity whose delay directly leads to the delay of the whole project","answer_id":15553},{"id":3660,"question":"Which of the following appropriately describes the purpose of using WBS (Work Breakdown Structure) in software development?","answer_label":"To divide development work into small tasks in a top-down manner, thereby facilitating work management","answer_id":15555},{"id":3661,"question":"Which of the following is an appropriate characteristic of a Gantt chart used in progress control?","answer_label":"It can compare the planned schedule and actual results.","answer_id":15562},{"id":3662,"question":"When the four roles, change control administrator, configuration administrator, maintenance administrator, and maintenance staff are defined in software maintenance organizations, which of the following persons should be primarily responsible for providing mechanisms for identifying, controlling, and tracking versions of software components?","answer_label":"Configuration administrator","answer_id":15564},{"id":3663,"question":"The membership registration process in company A issues IDs in the format defined below. The table shows the transition of the number of issued IDs at the end of each fiscal year. On the assumption that this tendency continues in years to come, when are the IDs in this format expected to be exhausted? Here, the IDs withdrawn from membership are treated as missing numbers and are not be reused.\n","answer_label":"Fiscal year 2012","answer_id":15569},{"id":3664,"question":"Which of the following is the primary objective of conducting a system migration test?","answer_label":"To confirm the procedures for switching from an existing system to a new system as well as problems accompanied with this switching, from the viewpoints of security and efficiency","answer_id":15574},{"id":3665,"question":"Among the functions provided by client management tools, which of the following is the most effective function for confirming that no software unrelated to the business operations is installed?","answer_label":"Inventory collection","answer_id":15575},{"id":3666,"question":"Which of the following is the purpose of periodically reorganizing a database in operation?","answer_label":"Additions, updates, and deletions performed repeatedly on a database generate storage areas that cannot be reused, and therefore the database volume increases and the processing speed decreases. For this reason, such areas are reorganized to prevent performance degradation.","answer_id":15579},{"id":3667,"question":"Which of the following is an appropriate description concerning the role of a system auditor?","answer_label":"It is to assure the full preparation and operations regarding the control of the information system or to give advice on them, from a professional standpoint independent from the audit target","answer_id":15583},{"id":3668,"question":"When IT controls are classified into the two categories of preventive control and detective control, which of the following falls into the category of detective control for discovering data entry errors or unauthorized actions?","answer_label":"Matching the output list of data entry results with the data entry sheets","answer_id":15589},{"id":3669,"question":"Which of the following is an explanation of EA (Enterprise Architecture)?","answer_label":"It is a technique to review respective business operations and information systems from the perspective of overall optimization through analysis of four key architectures — business, data, application, and technology.","answer_id":15594},{"id":3670,"question":"The diagram below shows the procedure for business improvement in six steps. When activities “a)” through “d)” are to be inserted into the blank boxes A through D, which of the following is the activity inserted in the blank box C ?\n","answer_label":"Develop improvement plan","answer_id":15595},{"id":3671,"question":"A scoring model is a method for quantifying qualitative evaluation items. Based on the four-level scoring model and evaluation items shown in the table below, which of the following indicates the goal achievement level of the entire system in percentage?\n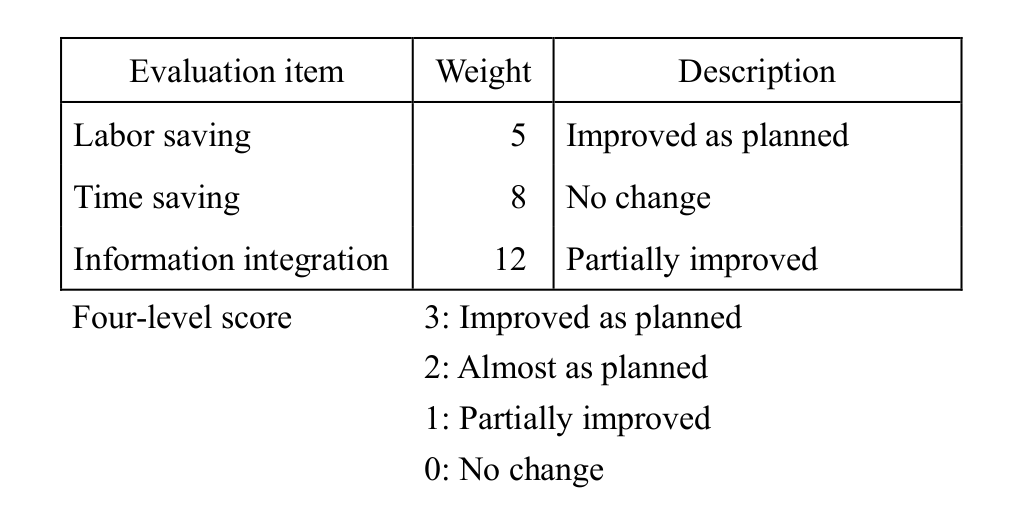","answer_label":"36","answer_id":15600},{"id":3672,"question":"Which of the following is a document that asks to provide the information necessary for the preparation of a document that asks for proposals?","answer_label":"RFI","answer_id":15604},{"id":3673,"question":"Which of the following is an advantage of M&A?","answer_label":"A company can establish a new business in a short period of time by acquiring skills and know-how that it does not have.","answer_id":15609},{"id":3674,"question":"Which of the following describes the characteristics of niche strategy in the context of competitive strategy?","answer_label":"Specializing in a market segment where other companies cannot enter easily to achieve higher profitability","answer_id":15614},{"id":3675,"question":"Which of the following is not an appropriate usage for embedded systems?","answer_label":"A host system for managing train ticket reservations","answer_id":15615},{"id":3676,"question":"Which of the following is “B to C ” in electronic commerce?","answer_label":"Virtual mall","answer_id":15621},{"id":3677,"question":"In an arrow diagram shown below, at least how many days are needed to complete all the activities A through J ? Here, in the diagram, each number shown beside the arrow indicates the number of days required for the activity.\n","answer_label":"11","answer_id":15626},{"id":3678,"question":"When the fixed order quantity model can be used for controlling inventory under the following conditions, what is the Economic Order Quantity (EOQ)? Here, EOQ is theoptimal order quantity that theoretically minimizes the total of the cost of ordering and holding inventory. The demand is constant, and does not vary over time.\n","answer_label":"1,000","answer_id":15629},{"id":3679,"question":"The sales staff at Company A wants to depart from Company A, visit customer companies B, C, and D once, respectively, and return to Company A. The table shows time required to move from one company to another. How long is the shortest time (in minutes) required for the visit?\n","answer_label":"110","answer_id":15632},{"id":3680,"question":"Which of the following appropriately explains “patent right” according to the WTO’s Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS)?","answer_label":"It is a right to exclusively utilize a new invention suitable for industrial use, which is granted upon application to and examination by the competent authority.","answer_id":15636},{"id":3681,"question":"Which of the following is the appropriate description concerning the CSV data format?","answer_label":"It separates character and numeric data by a comma and data records by line feeds. Character data may be enclosed in quotation marks.","answer_id":15642},{"id":3803,"question":"Which of the following is the addressing mode where the register specified is used to point to the memory address of the data to be operated upon?","answer_label":"Register indirect addressing mode","answer_id":16102},{"id":3804,"question":"As shown in the table below, when a computer executes three types of instructions A, B, and C, what is the performance in MIPS of the computer?\r\n","answer_label":"40","answer_id":16106},{"id":3805,"question":"Which of the following is a computer architecture where each instruction is divided into multiple stages (e.g., fetch, decode, and execute) in the processor, and multiple functional units execute two or more instructions in parallel by slightly shifting the instructions in stages?","answer_label":"Pipeline","answer_id":16108},{"id":3806,"question":"Which of the following is an appropriate explanation of memory interleaving?","answer_label":"Main memory is divided into multiple banks, and each bank is concurrently accessed in order to accelerate access from the CPU to main memory.","answer_id":16114},{"id":3807,"question":"Which of the following is the list that arranges A through D in order of effective access time of main memory from shortest to longest?\r\n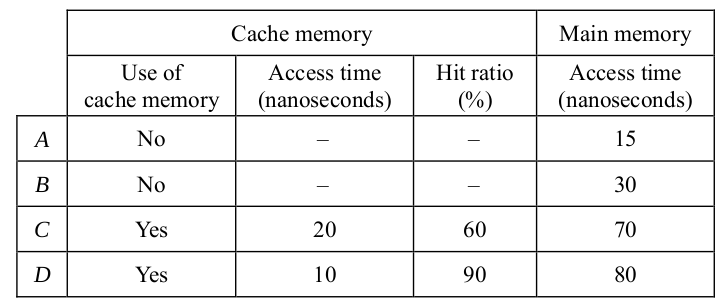","answer_label":"A, D, B, C","answer_id":16116},{"id":3808,"question":"Which of the following is widely used as storage media for image data in digital cameras or for music data in portable music players?","answer_label":"Flash memory","answer_id":16120},{"id":3809,"question":"When a 12-point character is displayed in bitmap on a 96-dpi display screen, how many dots are used for the height of a square font? Here, 1 point is 1/72 inch.","answer_label":"16","answer_id":16126},{"id":3810,"question":"In a client/server system using a database server, the generation of a large number of SQL statements causes a problem with a rapidly increasing network load between client and server. Which of the following is an appropriate solution to this problem?","answer_label":"Use of stored procedure","answer_id":16130},{"id":3811,"question":"The table below shows the number of failures per day and the average repair time (in minutes) per failure that are observed during the first 2 days in a newly installed system. What is the approximate availability of the system during that period? Here, the system is expected to operate for 24 hours every day.\r\n","answer_label":"0.83","answer_id":16134},{"id":3812,"question":"In the RAID0 and RAID1 systems using two disks, when one disk has a reliability rate of 99% and the other has a reliability rate of 97%, which of the following is the appropriate combination of each failure rate (in percentage) of RAID0 and RAID1? Here, the failure rate is calculated by using the formula below.\r\n failure rate (%) = 100% – reliability rate (%)\r\n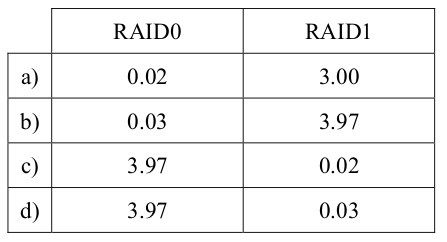","answer_label":"D","answer_id":16138},{"id":3813,"question":"Which of the following is a term that shows the amount of work that is processed per unit of time by a computer system?","answer_label":"Throughput","answer_id":16140},{"id":3814,"question":"Which of the following is the most appropriate explanation of a dual system?","answer_label":"It provides a duplicate system for performing the same processing, and performs a cross check of the processing results. In the event of a failure in either system, it continues the processing through degraded operation.","answer_id":16146},{"id":3815,"question":"Among the explanations of task scheduling methods, which of the following has the highest possibility that a specific task continues to wait for the allocation of CPU time?","answer_label":"The processing is executed from the task with the estimated shortest processing time. The subsequent task is started when the processing being executed is either completed or has been suspended for some reason.","answer_id":16150},{"id":3816,"question":"Which of the following is classified as an external interrupt?","answer_label":"An interrupt that is caused by an interval timer when the specified time elapses","answer_id":16153},{"id":3817,"question":"Which of the following is an appropriate explanation of the LRU method that is used as a page replacement algorithm?","answer_label":"The page that has not been used for the longest time is replaced.","answer_id":16156},{"id":3818,"question":"Which of the following is an appropriate reason for using a real-time OS in an embedded system?","answer_label":"There is a mechanism available to respond within the limited time.","answer_id":16162},{"id":3819,"question":"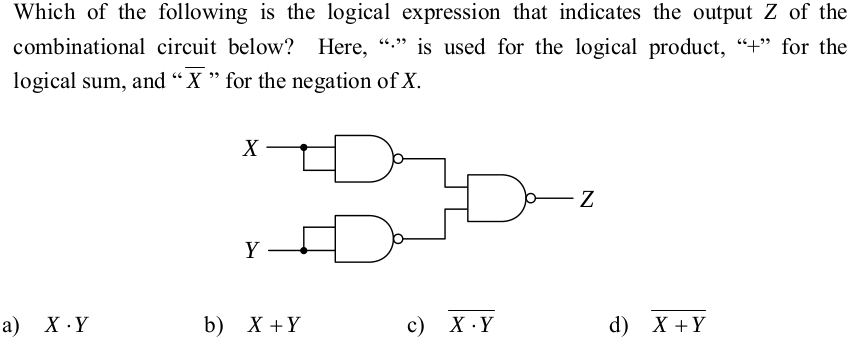","answer_label":"B","answer_id":16164},{"id":3820,"question":"Which of the following is a characteristic of DRAM, in comparison with SRAM?","answer_label":"DRAM is suitable for a higher level of integration.","answer_id":16168},{"id":3821,"question":"Which of the following is the case where outline fonts rather than bitmap fonts are effective and suitable for use on an output device such as a display or a printer?","answer_label":"Characters are enlarged using a given scale factor.","answer_id":16174},{"id":3822,"question":"Audio is sampled and recorded at a frequency of 11,000 times per second with a resolution of 8 bits per sample. How many minutes of audio at maximum can be recorded in flash memory with a capacity of 512x10^6 bytes?","answer_label":"775","answer_id":16177},{"id":3823,"question":"Which of the following is a mechanism that is used for defining the style of a Web page?","answer_label":"CSS","answer_id":16180},{"id":3824,"question":"Which of the following is the appropriate sequence of steps used for normalizing a relational database table?\r\nStep A: Attributes dependent on non-key attributes are separated as another table.\r\nStep B: Attributes dependent on only part of key are separated as another table.\r\nStep C: Repetitive data is separated as another table.","answer_label":"C → B → A","answer_id":16186},{"id":3825,"question":"In a relational database, which of the following is an appropriate definition of a composite key?","answer_label":"A primary or foreign key that consists of two or more attributes of a relation","answer_id":16188},{"id":3826,"question":"When the SQL statements shown below are executed for the “SMARK” table, which of the following is the appropriate table that can be obtained as a result?\r\nCREATE VIEW Result\r\nAS SELECT * FROM SMARKS AS S\r\nWHERE S.Marks > 52 AND S.ID <= 0100\r\nSELECT r.ID FROM Result AS r\r\nWHERE r.Status LIKE 'Pass' AND r.Mark <= 90\r\n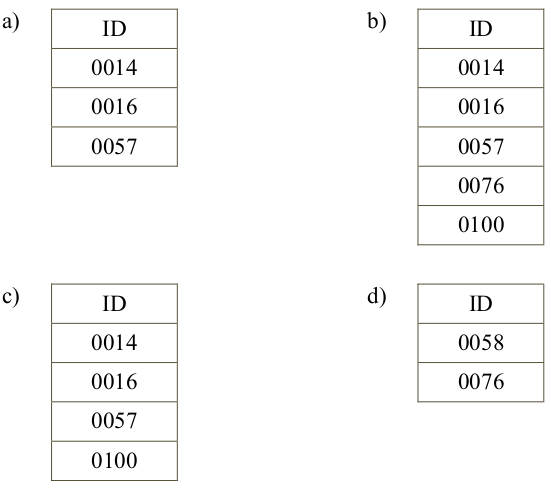","answer_label":"A","answer_id":16191},{"id":3827,"question":"In an SQL statement, which of the following is an appropriate explanation of the percent symbol (%) that is used with the LIKE operator in a WHERE clause?","answer_label":"It is a wildcard character that matches any string of zero or more characters.","answer_id":16198},{"id":3828,"question":"As shown below, there are three relational database tables Table_1, Table_2, and Table_3. Table_1 contains the students who have knowledge of Java language, and Table_2 contains the students who have knowledge of C++. Table_3 contains the students who know C++ but do not know Java. Which of the following is the appropriate operation in relational algebra that can be used to create Table_3?\r\n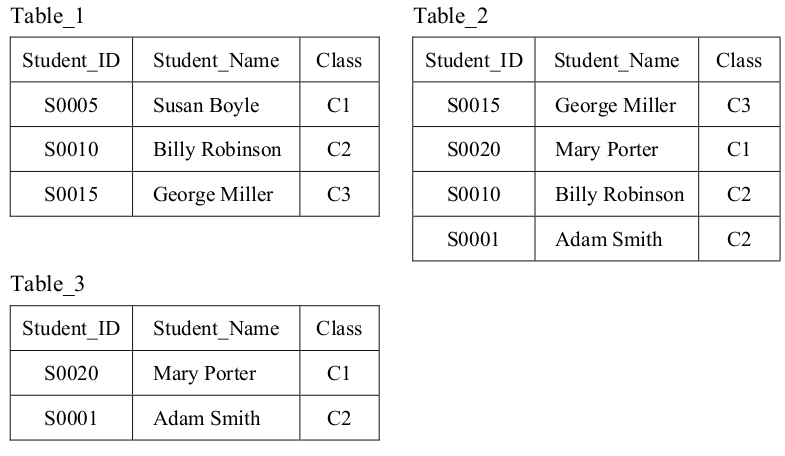","answer_label":"Difference","answer_id":16199},{"id":3829,"question":"Which of the following is an appropriate explanation concerning the NAT function of a router used for Internet connection?","answer_label":"Conversion between private IP addresses and global IP addresses can be performed.","answer_id":16204},{"id":3830,"question":"Which of the following is the appropriate protocol that is used on top of UDP for delivering real-time audio and video streams over the Internet?","answer_label":"RTP","answer_id":16210},{"id":3831,"question":"Which of the following is an appropriate function of a switching hub (layer 2 switch) that is used as a network device?","answer_label":"A received packet is forwarded only to a LAN port corresponding to a destination MAC address.","answer_id":16213},{"id":3832,"question":"In a TCP/IP network, which of the following is used to check if a computer or device is accessible across a network?","answer_label":"ping","answer_id":16218},{"id":3833,"question":"Which of the following is the most appropriate term that corresponds to the method of illegally intercepting audio and/or data being transmitted or received via a network?","answer_label":"Sniffing","answer_id":16221},{"id":3834,"question":"Which of the following is a computer network attack that can be classified as a DDoS attack?","answer_label":"All the computers infected by a virus send a large number of recursive queries simultaneously to a target computer when receiving a command from an attacker who is in a remote location.","answer_id":16226},{"id":3835,"question":"When information, such as an e-mail or a document file, is sent or received with a digital signature via the Internet, which of the following is the appropriate combination of security properties that ensure that such information has not been altered or tampered with during transmission?","answer_label":"Authenticity and integrity","answer_id":16228},{"id":3836,"question":"Which of the following is the most appropriate explanation of a digital certificate that is authorized by a trusted third party known as a CA (Certification Authority)?","answer_label":"A document that verifiably associates a public key with a particular person or party","answer_id":16231},{"id":3837,"question":"Which of the following is a biometric recognition technique that is used for identifying a person by using the person’s own behavioral features as well as physiological features?","answer_label":"Voice recognition","answer_id":16238},{"id":3838,"question":"Which of the following is an appropriate description concerning social engineering?","answer_label":"An attacker manipulates people into providing inappropriate access to sensitive or confidential data.","answer_id":16241},{"id":3839,"question":"Which of the following is a technique where a system is actually attacked and an intrusion attempt is made, with the aim of discovering security-related vulnerabilities of a computer or network?","answer_label":"Penetration test","answer_id":16243},{"id":3840,"question":"Which of the following is a network segment that is isolated from the external network (WAN) and the internal network (LAN) via firewalls in order to ensure that publicly accessible servers cannot contact other internal network segments in the event that such a server is compromised?","answer_label":"DMZ","answer_id":16247},{"id":3841,"question":"Among the diagrams used in UML 2.x, which of the following is the diagram that can represent the interactions based on messages sent or received between objects?","answer_label":"Sequence diagram","answer_id":16252},{"id":3842,"question":"When a system is developed by using object-oriented approach, which of the following is the effect of encapsulation?","answer_label":"When the internal data structure or the implementation of a method for an object is changed, other objects are not susceptible to the change.","answer_id":16258},{"id":4263,"question":"Which of the following is the correct decimal fraction equal to hexadecimal fraction 0.248?","answer_label":"31/125","answer_id":17920},{"id":4264,"question":"Which of the following is the correct value of the quadruple of hexadecimal fraction 0.FEDC?","answer_label":"3.FB70","answer_id":17925},{"id":4265,"question":"In a floating-point number format, which of the following is the correct operation for adjusting the radix point and the exponent so that the most significant digit of the mantissa can be a non-zero value? Here, an absolute value is used for the mantissa.","answer_label":"Normalize","answer_id":17928},{"id":4266,"question":"The decimal value “-72” is stored in an 8-bit register using 2’s complement. If the data in the register is logically shifted two bits to the right, which of the following is the correct result that is represented in decimal?","answer_label":"46","answer_id":17934},{"id":4267,"question":"By definition of the IEEE754 standard, 32-bit floating point numbers are represented as follows:\n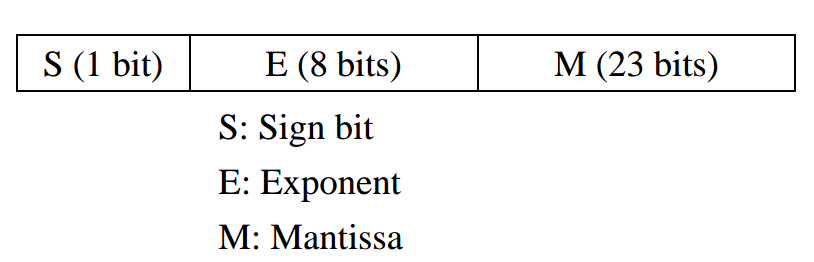\nWhich of the following is the correct “mask bits” in hexadecimal to be used for extracting only the exponent part of the above format? Here, “mask bits” means a bit pattern which is logically ANDed with the 32-bit floating point value.","answer_label":"7F800000","answer_id":17936},{"id":4268,"question":"In the Venn Diagrams labeled 1 to 3, which of the following is the result of Boolean “OR” operations for all three to be combined? Each set corresponding to x,y, or z is depicted by a circle.\n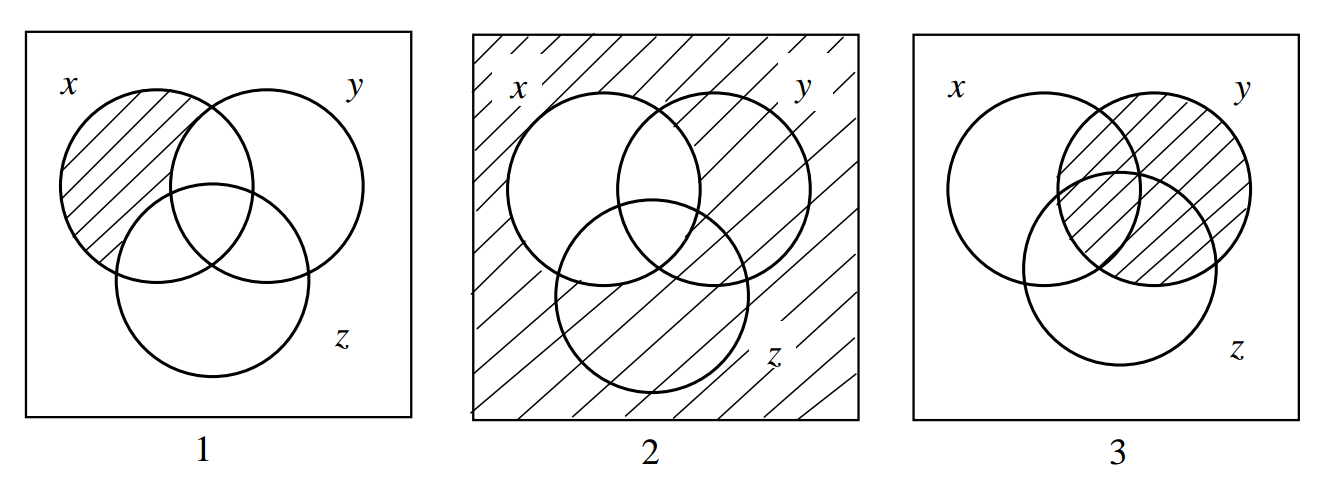","answer_label":"x AND (NOT y) AND (NOT z) OR (NOT x) OR y","answer_id":17941},{"id":4269,"question":"When you flip a coin four times, what is the probability that it will come up heads exactly twice?","answer_label":"0.375","answer_id":17944},{"id":4270,"question":"There are two important operations on a stack: PUSH and POP. PUSH adds the new data to the top of the stack leaving previous data below, and POP removes and returns the current top data of the stack. When the operations shown below are sequentially executed, which of the following is the correct combination of the values x and y? Here, the size of the stack is big enough to hold the entire data. “PUSH(a)” inserts the data a into the stack, and “POP(b)” removes the data b from the stack.\n[Operations]\nPUSH (5);\nPUSH (3);\nPUSH (6);\nPUSH (1);\nx = POP ( );\nPUSH (7);\ny = POP ( );","answer_label":"x = 1, y = 7","answer_id":17948},{"id":4271,"question":"Reverse Polish Notation (RPN) is used to represent arithmetic expressions without using brackets to define priorities for evaluation of operators. For example, $3\\times (a+b)$ becomes $3ab+\\times$ in RPN. Which of the following is the best data structure that should be used for implementation of RPN in a computer?","answer_label":"Stack","answer_id":17953},{"id":4272,"question":"Which of the following is an appropriate description concerning the list and/or array structures?","answer_label":"The list structure allows any data to be inserted or deleted simply by modifying pointers. But, after the data was deleted, the cells that contained the data remain as garbage in memory.","answer_id":17955},{"id":4273,"question":"The table below shows a state transition table that checks the input character string. This check starts from the initial state A, and it fails if the state changes to E during the input of the character string. Which of the character strings in the answer group fails this check? Here, the symbol Δ in the answer group represents a space.\n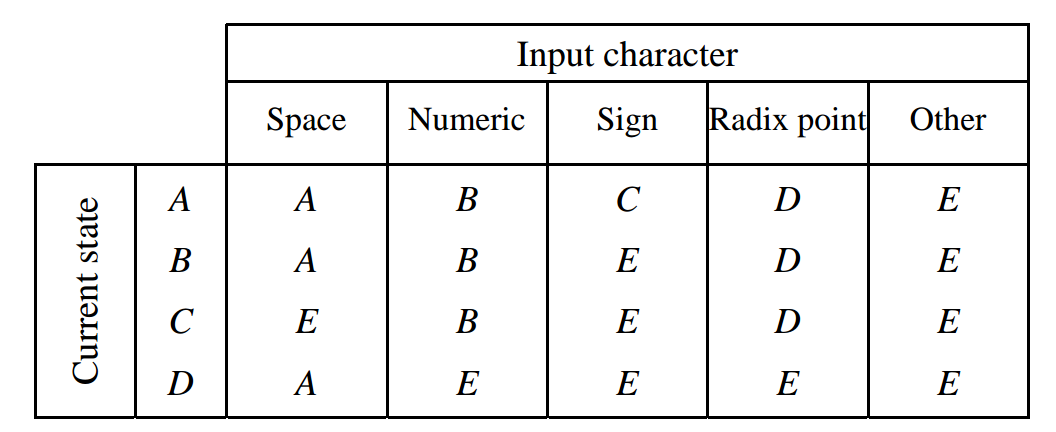","answer_label":"12.2","answer_id":17961},{"id":4274,"question":"There are two jugs; one is a 4-liter (4L) jug and the other is a 3-liter (3L) jug. Which of the following is the correct sequence to obtain exactly 2 liters of water in the 4L jug under the conditions shown below? Here, (x, y) indicates that the 4L jug contains x liters of water and the 3L jug has y liters of water.\n[Conditions]\nYou can use only the 3L and 4L jugs.\nYou are allowed to fill up or empty either jug.\nYou are allowed to pour water from one jug to the other.\nThe jugs have no scale marks.\nThere is an amply supply of water.","answer_label":"(0,0) → (0,3) → (3,0) → (3,3) → (4,2) → (0,2) → (2,0)","answer_id":17964},{"id":4275,"question":"Which of the following is the correct result produced by executing the program shown below? Here, the parameter “x” is called by value, and the parameter “y” is called by reference.\nMain Program\na = 2;\nb = 3;\nsub(b, a);\n\nSubprogram sub(x, y)\nx = x + y;\ny = x + y;\nreturn;","answer_label":"a = 7, b = 3","answer_id":17969},{"id":4276,"question":"The “prime number division remainder” method is a well-known hashing algorithm. In this method, a key value is divided by a number N, and the remainder which is also called a hash value is used directly as an index into the hash table. N is the largest prime number less than or equal to the size of the available addressable spaces. When the 20 addressable spaces are available, which of the following is the correct hash value calculated from the key value 136? Here, a prime number is one that cannot be divided evenly by any other number except one (1). 2, 3, 5, 7, 11, and 13 are the first few prime numbers.","answer_label":"3","answer_id":17972},{"id":4277,"question":"In a certain computer, a bubble sort of an array of 200 data elements takes the same time as a quick sort of the array. In case of an array of 40,000 data elements, how many times faster is a quick sort than a bubble sort? Here, a bubble sort and a quick sort take time proportional to $n^2$ and $n\\times log_2 n$ respectively, and “n” is the number of data elements.","answer_label":"100","answer_id":17976},{"id":4278,"question":"Integers are stored in the 1st to N-th elements of an array A (N > 1). The flowchart below shows the process to check which element of the array contains the same value as X. Which of the following correctly describes the execution result of this process?\n","answer_label":"If the same value as X exists in two places of the array, the 1st and N-th elements, k is set to 1.","answer_id":17978},{"id":4279,"question":"Which of the following statements concerning programming languages appropriately describes Java?","answer_label":"It enables the creation of applets and other programs that run in web browsers. The applets can be run on any environment where virtual machines are implemented.","answer_id":17982},{"id":4280,"question":"There are two methods to execute byte-code programs written in Java. In the first method, an interpreter is used to execute byte-code. In the second method, native code generated by a compiler is executed. In the second method, how many lines of byte-code are at least required, in order to achieve shorter processing time (including compiling time) than the first method, under the conditions below?\n\n[Conditions]\n\n(1) The execution time is proportional to the number of lines in the program.\n\n(2) If a program consisting of 100 lines of byte-code is executed using an interpreter, it takes 0.2 seconds. If the same program is executed after compiling, it takes 0.003 seconds.\n\n(3) It takes 0.1 seconds to compile 100 lines.\n\n(4) In case of the method using a compiler, an overhead of 0.15 seconds is always required for file input/output, compiler startup, and so on, regardless of the number of lines in the program.\n\n(5) Other miscellaneous time such as time for downloading the program file may be ignored.","answer_label":"155","answer_id":17989},{"id":4282,"question":"Which of the following is equal to the hexadecimal fraction 2A.4C?\n","answer_label":"a","answer_id":17993},{"id":4285,"question":"In fixed-point representation that expresses negative numbers by two’s complement, which range of integers can be expressed with n bits? Here, the position of the binary point is to the right of the least significant bit.\n","answer_label":"c","answer_id":18004},{"id":4286,"question":"Which of the following is a re-writable, erasable memory, using electrical signals, which is widely used for various devices such as digital cameras and digital music players and can maintain the data even after the power is turned off?","answer_label":"Flash memory","answer_id":18007},{"id":4287,"question":"The figure shows an RS flip-flop using two NOR gates. Which of the following is the correct truth table for the flip-flop? Here, “unchanged” show in the table means the outputs maintain a previous state, and “unstable” means the outputs are in an unstable state.\n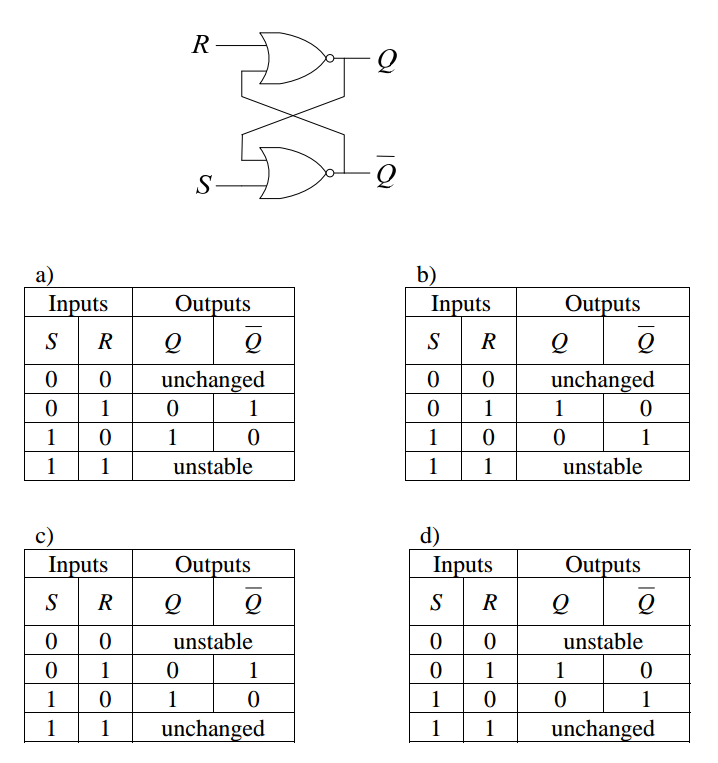","answer_label":"a","answer_id":18010},{"id":4288,"question":"Which of the following is the correct combination of various addressing modes? Here, $X_1$ is an address which is stored in a program counter. $X_2$ is an address part of an instruction which is addressed by $X_1$. $X_3$ is an address in which an operand needed to execute an instruction is stored. $X_4$ is a value in an index register. ($X_2$) means the contents of location $X_2$.\n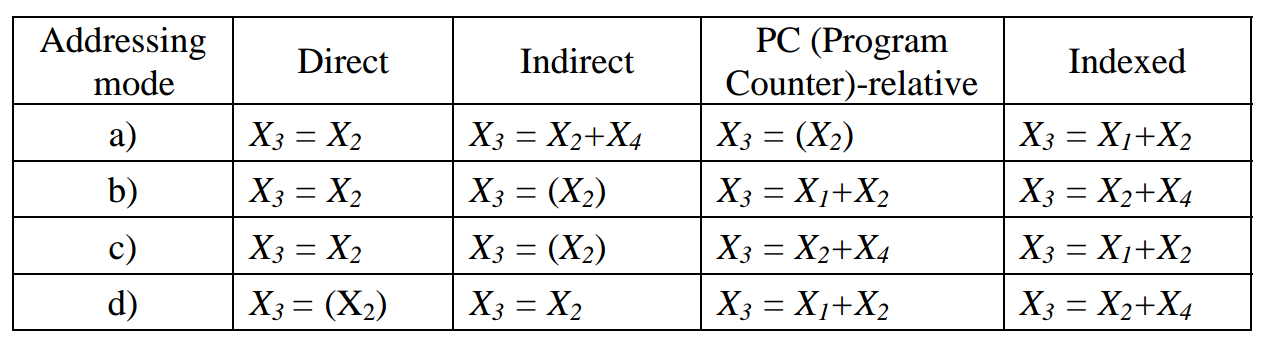","answer_label":"b","answer_id":18015},{"id":4289,"question":"A computer is designed to enable pipeline control so that each instruction can be completed in five cycles. How many cycles are needed to execute 20 instructions? Here, all instructions can be executed without being stopped halfway.","answer_label":"24","answer_id":18020},{"id":4290,"question":"Which of the following is an appropriate statement in regard to interrupts?","answer_label":"A priority is individually assigned to the cause of an interrupt in preparation for the occurrence of multiple interrupts.","answer_id":18023},{"id":4291,"question":"Which of the following is an appropriate description concerning cache memory?","answer_label":"In one method, when executing a write instruction, data is written to both cache memory and main memory. In the other method, data is written only to a block in cache, and the modified block is written back into main memory only when it is replaced.","answer_id":18028},{"id":4292,"question":"There are two systems A and B whose access times of cache and main memory are show in the table. When a certain program runs on these systems, the cache hit ratio and the effective access time are the same on both systems. What is the cache hit ratio in this case?\n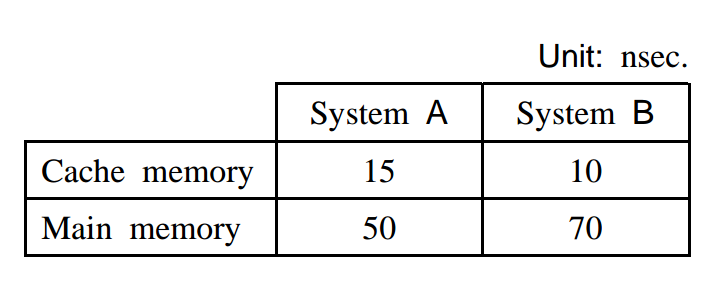","answer_label":"0.8","answer_id":18033},{"id":4293,"question":"Which of the following is an appropriate description of memory interleaving?","answer_label":"Dividing main memory into several banks and speeding up access to sequential addresses in memory.","answer_id":18035},{"id":4294,"question":"There is a hard disk drive with specifications shown below. When a record of 15 Kilobytes is processed, which of the following is the average access time in milliseconds? Here, the record is stored in one track.\n\n[Specifications]\n\nCapacity: 25 Kilobytes/track\n\nRotation speed: 2,400 revolutions/minute\n\nAverage seek time: 10 milliseconds","answer_label":"37.5","answer_id":18039},{"id":4295,"question":"The sequence of virtual page numbers shown below is encountered in the course of execution of programs on a computer with virtual memory.\n\n[Sequence of virtual page numbers]\n\n3 4 2 6 4 7 1 3 2 6 3 5 1 2 3\n\nIn the computer, the LRU page replacement policy is adopted. Main memory has a capacity of 5 pages for programs, and each page is initially empty. What is the page hit ratio (percentage of times that the referenced page is found in main memory) rounded to the nearest integer value?","answer_label":"33","answer_id":18043},{"id":4296,"question":"What is an advantage of DVD-RAM in comparison with DVD-RW and DVD+RW?","answer_label":"More durable rewritable disc","answer_id":18048},{"id":4297,"question":"Which of the following is the appropriate combination of 4 color inks or toners for a full-color printer?","answer_label":"Cyan, Magenta, Yellow, and Black","answer_id":18051},{"id":4298,"question":"Which of the following is the most appropriate index indicating the performance of a laser printer?","answer_label":"Number of dots per inch (2.54 cm) and number of pages that can be printed per minute","answer_id":18054},{"id":4299,"question":"The figure shows the basic configuration of a computer. Which of the following is the correct combination of A, B, and C to be inserted in the figure?\n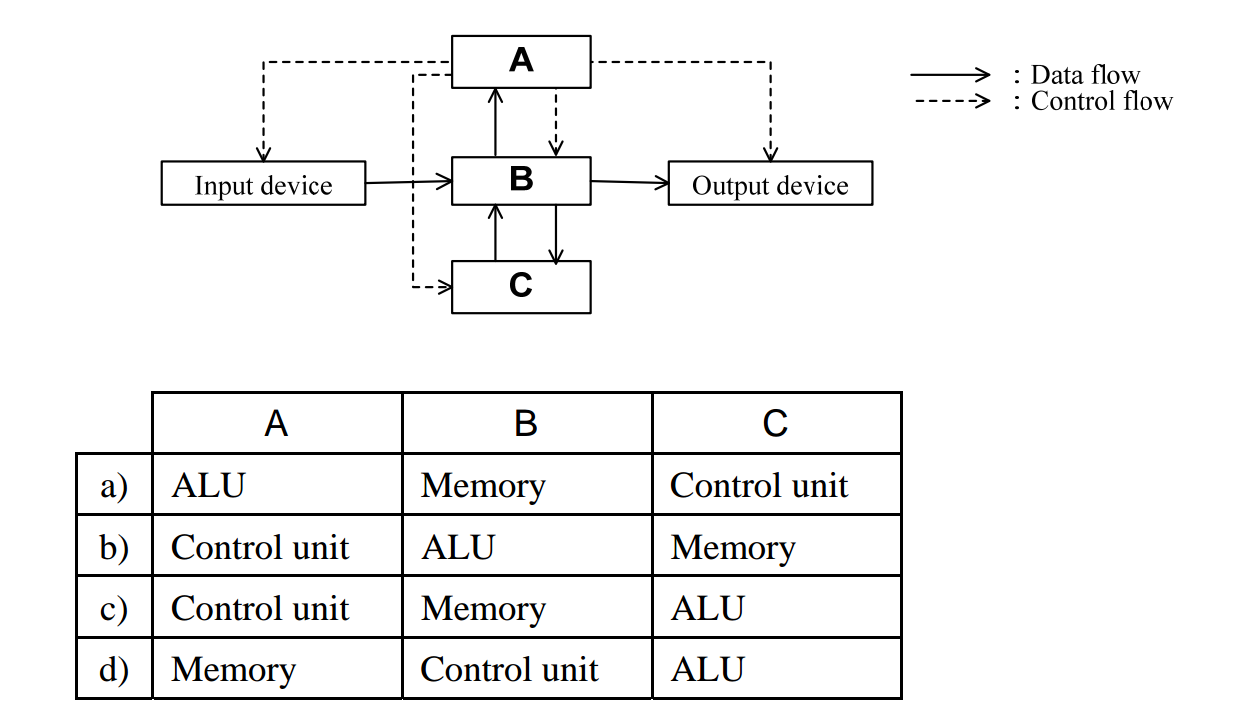","answer_label":"c","answer_id":18060},{"id":4300,"question":"Which of the following is an input device classified as a pointing device and can be used for graphical input in a CAD system?","answer_label":"Tablet","answer_id":18065},{"id":4301,"question":"Which of the following is a display, with low-voltage operation and low-power consumption, which does not need backlighting because it emits light when voltage is applied?","answer_label":"OLED","answer_id":18067},{"id":4302,"question":"Which of the following is an appropriate description concerning the role of a shell in an OS?","answer_label":"It interprets the commands entered by the user and instructs the OS to execute the corresponding functions.","answer_id":18072},{"id":4303,"question":"Which of the following terms refers to the function that adjusts all address dependent locations within a program to correspond to the load position when the program is loaded into main memory prior to its execution?","answer_label":"Relocation","answer_id":18077},{"id":4304,"question":"The table shows the priorities of five tasks A to E. When each task is independently executed, the processing sequences and times associated with CPU and I/O devices are also shown in the table. Which of the tasks B to E should be combined together with task A assigned a “high” priority so that there may be no idle time of CPU from starting of execution of the combined tasks to ending of both tasks? Here, I/O operations never conflict with each other, and any overhead involved in the OS can be ignored. The number in parentheses denotes each processing time.\n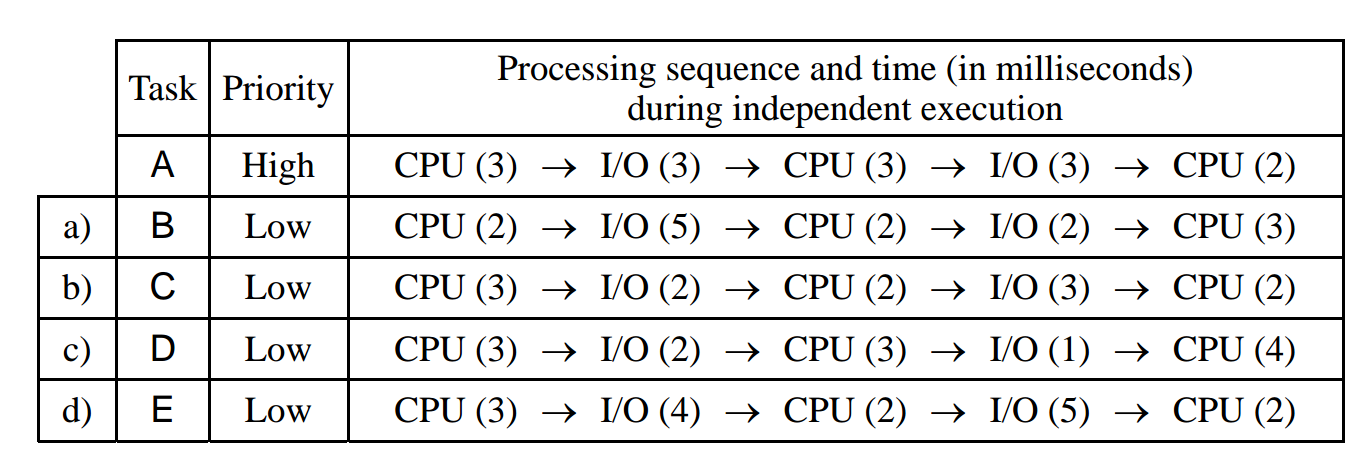","answer_label":"c","answer_id":18080},{"id":4305,"question":"Which of the following functions can reduce the network load by placing a frequently-used instruction set on the server in advance, when accessing a database in a client/server system?","answer_label":"Stored procedure function","answer_id":18084},{"id":4306,"question":"Which of the following is a system where one computer is in standby mode when the other computer is functioning normally?","answer_label":"Duplex system","answer_id":18087},{"id":4307,"question":"There is a CPU whose clock cycle time is 0.01 microsecond. The table below shows a program’s instruction mix executed on the CPU. What is the approximate MIPS value for the processor?\n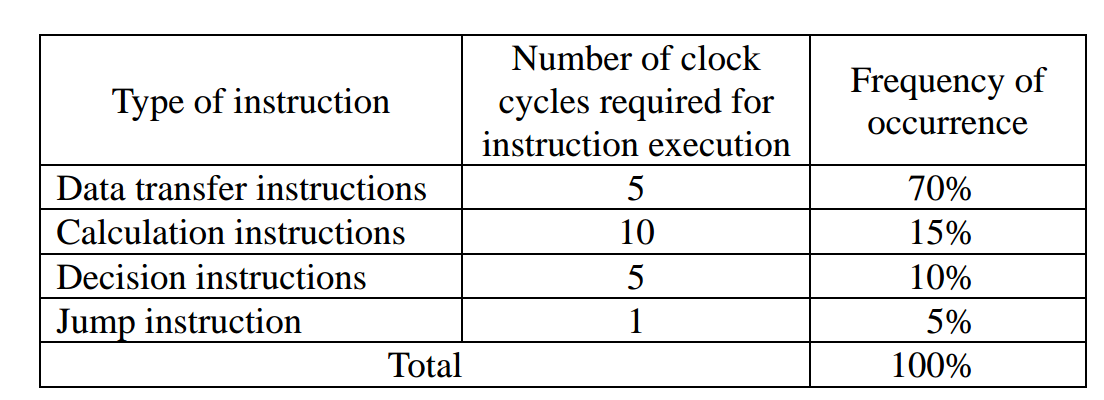","answer_label":"18.02","answer_id":18092},{"id":4308,"question":"Which of the following is an appropriate statement with regard to system performance evaluation, when selecting a new computer system?","answer_label":"The data required for evaluation can be acquired by running programs which are frequently used or time critical.","answer_id":18097},{"id":4309,"question":"A company uses 1,000 PCs. The mean failure in 20 days is to be restricted to 2 PCs. How many hours of MTBF are at least required for these PCs? Here, the mean usage time of the PCs is assumed to be 8 hours per day.","answer_label":"80,000","answer_id":18100},{"id":4310,"question":"Which of the following is an appropriate description concerning a tracer that is used as a debugging tool?","answer_label":"It outputs history information such as execution sequences and execution results of program instructions.","answer_id":18102},{"id":4312,"question":"When the results of the logical operation “x # y” are shown in the table below, which of the following expressions is equivalent to the operation “x # y”? Here, “AND” is used for the logical product, “OR” is for the logical sum, and “NOT” is for the logical negation.\n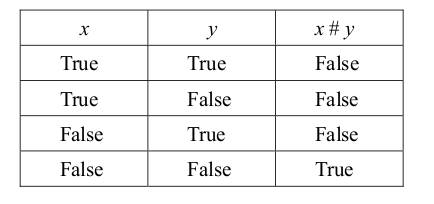","answer_label":"(NOT x) AND (NOT y)","answer_id":18111},{"id":4313,"question":"Which of the following is an appropriate description in regard to a waterfall model?","answer_label":"System development proceeds in the order of process flow, so going back upstream results in a significant loss of efficiency.","answer_id":18113},{"id":4314,"question":"Which of the following is an appropriate description concerning object-oriented design?","answer_label":"A class can inherit attributes and methods from its base class.","answer_id":18118},{"id":4315,"question":"Which of the following is a UML diagram that can be used to describe interactions among a number of objects in terms of an exchange of messages?","answer_label":"Sequence diagram","answer_id":18123},{"id":4316,"question":"A systems design is represented using several diagrams. When a system analyst wants to confirm the design information such as the relationships among functions and the interface among modules in a hierarchical manner, which of the following is the most appropriate diagram that should be inspected by the analyst?","answer_label":"Structured chart","answer_id":18128},{"id":4317,"question":"In the module design of software, which of the following is the appropriate technique for improving reliability and maintainability?","answer_label":"Module cohesion is increased, and module coupling is weakened.","answer_id":18130},{"id":4318,"question":"The entity-relationship diagrams A and B shows the relationships between three entities in a school: teacher, class, and classroom. Which of the following is an appropriate interpretation concerning the diagrams? Here, “1 1” shows a one-to-one relationship while “1 *” shows a one-to-many relationship.\n","answer_label":"In A, a teacher is responsible for one class only. In B, a teacher may be responsible for one or more classes.","answer_id":18133},{"id":4319,"question":"Which of the following is an appropriate statement in regard to a module unit test?","answer_label":"The module interface falls outside the scope of the unit test because the module interface cannot be tested using a single module.","answer_id":18139},{"id":4320,"question":"Which of the following is an appropriate statement in regard to program testing?","answer_label":"In the program testing, it is necessary to check not only whether the program works as intended but also whether there are any unintended operations.","answer_id":18141},{"id":4321,"question":"Which of the following software test methods is performed to verify whether changes made for software maintenance are not affecting other portions of the software?","answer_label":"Regression test","answer_id":18147},{"id":4322,"question":"A check digit for a 4-digit number $X_1X_2X_3X_4$ can be calculated as follows:\n$$\\bmod ((X_1\\times 4+X_2\\times 3+X_3\\times 2+X_4\\times 1), 10)$$\nWhen the check digit for the 4-digit number “$7X_242$″ is equal to 6, which of the following is the correct number to be put in $X_2$? Here, mod(a,b) returns the remainder after “a” is divided by “b.”","answer_label":"6","answer_id":18150},{"id":4323,"question":"An implementation plan for a system development project was drawn up, and the critical path was determined. Which of the following tasks can be identified by the critical path?","answer_label":"Tasks directly connected with the delay of the entire project","answer_id":18153},{"id":4324,"question":"From multiple types of slips, data in items specified for each type is inputted. Which of the following is the appropriate initial process to be executed in the program to confirm that all the required data is inputted?","answer_label":"A comparison is made between the number of items specified for each slip type and the number of items inputted.","answer_id":18157},{"id":4325,"question":"When the system development division and the operations divisions are separately organized, which of the following is an appropriate method for ensuring that the transition from development to operation proceeds smoothly and efficiently?","answer_label":"The operations division participates actively in system development to provide assistance from the viewpoint of operability.","answer_id":18164},{"id":4326,"question":"Which of the following is an appropriate description concerning CRM (Customer Relationship Management)?","answer_label":"It is an approach for increasing customer satisfaction and ultimately revenues by sharing information and raising the service levels, not only in the sales division but in all customer related channels within a company.","answer_id":18168},{"id":4327,"question":"The figures show the break-even point for two companies A and B. Which of the following is an appropriate statement with regard to the profit/loss analysis of Companies A and B?\n","answer_label":"Company A has low variable costs per unit of product, so when sales exceed the break-even point, Company A‘s profits are larger than Company B.","answer_id":18171},{"id":4328,"question":"Which of the following is an appropriate statement concerning a radar chart?","answer_label":"The degree of attainment of the benchmarking goal is plotted on the radial axis which corresponds to each item. All such plotted points are connected by a line, thereby making a comparison of overall balance.","answer_id":18175},{"id":4329,"question":"The figure below shows plots of the relationship between values of a certain factor x, in the product manufacturing process, and values of quality characteristics y. Which of the following is an appropriate description concerning this figure?\n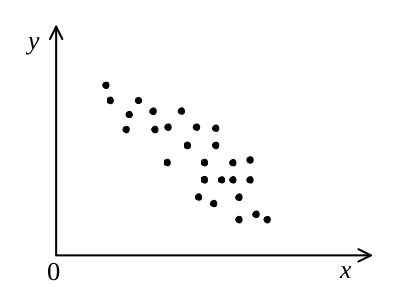","answer_label":"The coefficient of correlation between x and y is negative.","answer_id":18177},{"id":4330,"question":"In order to shorten the cumulative duration of activities on the critical path by one day, which of the following is the appropriate action to be taken?\n","answer_label":"To shorten the activity I by one day","answer_id":18184},{"id":4331,"question":"Three products A, B, and C are produced from raw materials at plant X. The production time per unit volume of each product, the required quantity of raw materials, and the profit amounts are shown in the table below. The maximum production hours per month at this plant total 240 hours, and the amount of raw materials that can be fed for production is 150 kg per month.\n\nUnder these conditions, management would like to know how many of A, B, and C should be manufactured so as to yield maximum profits. Which of the following is an appropriate method for solving this problem?\n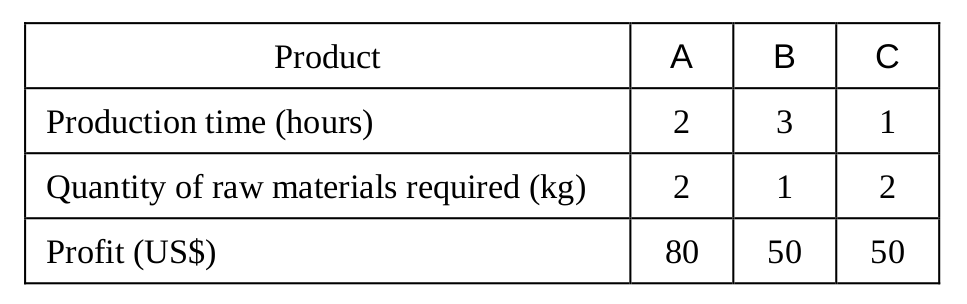","answer_label":"Linear programming method","answer_id":18187},{"id":4332,"question":"There are various types of e-commerce, depending on the transaction: B2B, B2C, C2C, m-commerce, etc. Which of the following refers to the activities associated with the selling and buying of goods and services via the Internet such as an online auction website and an online flea market?","answer_label":"C2C (Consumer to Consumer)","answer_id":18191},{"id":4333,"question":"","answer_label":"0071361286","answer_id":18196},{"id":4336,"question":"Computer font is an element in the user interface. Which of the following is the most appropriate explanation concerning the font?","answer_label":"A set of glyphs and associated information such as code points","answer_id":18206},{"id":4337,"question":"In a search system, when search was first performed under condition A, there were 5,000 search results. When further narrowed down with condition B, 30% of these search results remained. If search first performed under condition B produces 10,000 search results, what percentage will remain when these are further narrowed down with condition A?","answer_label":"15","answer_id":18209},{"id":4338,"question":"Which of the following is an appropriate statement in regard to operation of a distributed system?","answer_label":"A dedicated administrator is assigned in the same manner as in a centralized system to manage common resources such as databases.","answer_id":18213},{"id":4339,"question":"In the OSI 7-layer model, which of the following layers coverts data from the upper layer into many tiny pieces called segments for transmission across the network?","answer_label":"Transport Layer","answer_id":18220},{"id":4340,"question":"Which of the following is the appropriate protocol that can deliver data from sender to receiver, correctly and in order?","answer_label":"TCP","answer_id":18224},{"id":4341,"question":"Which of the following protocols is used in a TCP/IP network to provide a virtual terminal function that enables remote login to a host for remote operation?","answer_label":"TELNET","answer_id":18228},{"id":4342,"question":"When constructing a network with a TCP/IP environment, IP address management becomes cumbersome and complicated as the number of clients becomes larger. Which of the following protocols is able to increase the efficiency of IP address management by assigning IP addresses dynamically according to requests from clients?","answer_label":"DHCP","answer_id":18229},{"id":4343,"question":"Which of the following is an appropriate statement in regard to the transmission operation of nodes connected to a LAN in the CSMA/CD method?","answer_label":"Each node checks whether the carrier is busy and can transmit only if the carrier is not busy. When collision is detected, transmission is tried again after a random time has elapsed.","answer_id":18233},{"id":4344,"question":"A message consists of 200 characters. If we can transmit 200 messages on average before a 1-bit error occurs, what is the bit error rate of the transmission line? Here, 1 character equal 2 bytes while 1 byte equals to 8 bits.","answer_label":"1/640,000","answer_id":18237},{"id":4345,"question":"Which of the following appropriately describes a schema in a relational database management system?","answer_label":"It is a set of data definitions such as the data properties, format, relationship with other data, etc.","answer_id":18241},{"id":4346,"question":"Which of the following appropriately describes a domain (defined area), a term used for relational databases?","answer_label":"It is a set of values that attributes can hold.","answer_id":18246},{"id":4347,"question":"Which of the following operations extracts specific columns from tables in a relational database?","answer_label":"Projection","answer_id":18250},{"id":4348,"question":"When a transaction fails, which of the following should be performed in order to abort it and to rebuild the previous state of the database?","answer_label":"Rollback","answer_id":18256},{"id":4349,"question":"There is an OS that can set access privileges to read, update, and create subordinate files in a directory. These three types of access privileges can be set to “enabled” or “disabled” using 1 bit. If these three bits are set by an octal (base-8) number expressed by numerals 0 to 7, which of the following is an appropriate description, taking into account the trial results below?\n\n[Trial results]\n\n(1) When 0 was set, all accesses were disabled.\n\n(2) When 3 was set, read, and update were enabled, but create was disabled.\n\n(3) When 7 was set, all accesses were enabled.","answer_label":"When 4 is set, only create is enabled.","answer_id":18258},{"id":4350,"question":"Which of the following is an appropriate description of the virus pattern file that is used in virus protection measures for computers?","answer_label":"It is a file that records the signature code of known viruses and is used to detected viruses by the virus protection software.","answer_id":18263},{"id":4351,"question":"Against what kind of attacks does SSL (Secure Sockets Layer) protect users on the Internet?","answer_label":"Tapping and exploitation of data","answer_id":18268},{"id":4352,"question":"Which of the following is an appropriate statement regarding elements of information security defined in ISO/IEC 17799:2005?","answer_label":"Integrity is safe-guarding the accuracy and completeness of information and processing methods.","answer_id":18272},{"id":4376,"question":"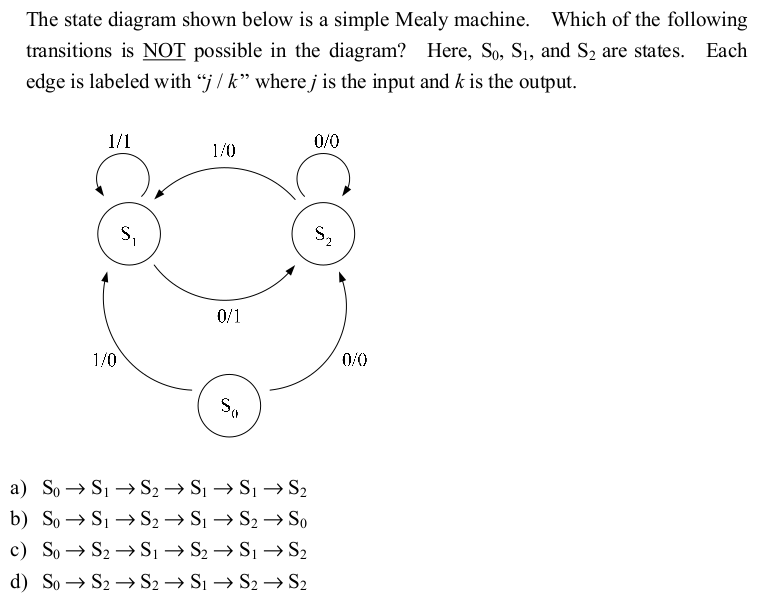","answer_label":"b","answer_id":18358},{"id":4379,"question":"","answer_label":"110","answer_id":18366},{"id":4382,"question":"In the binary tree shown below, which of the following trees is created after conversion into a (max) heap?\n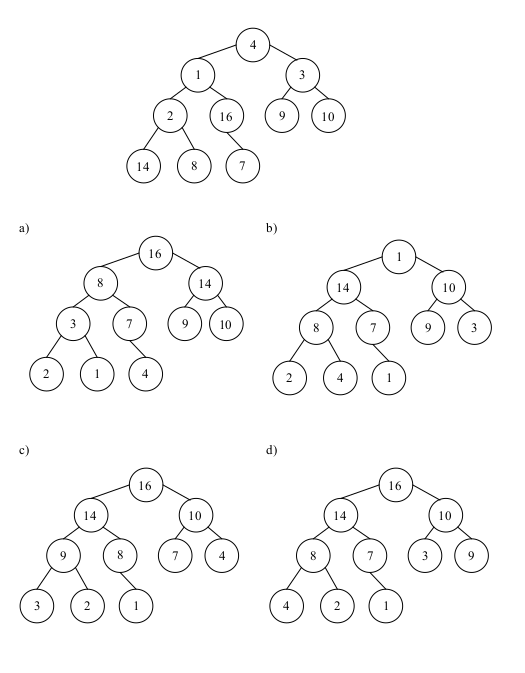","answer_label":"b","answer_id":18375},{"id":4383,"question":"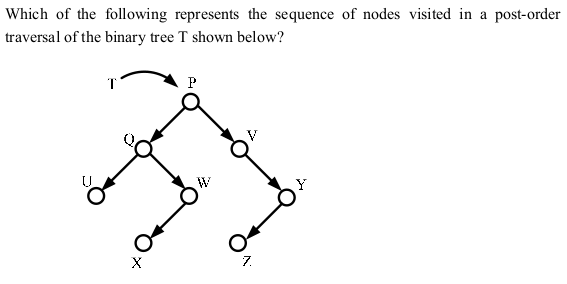","answer_label":"U X W Q Z Y V P","answer_id":18379},{"id":4385,"question":"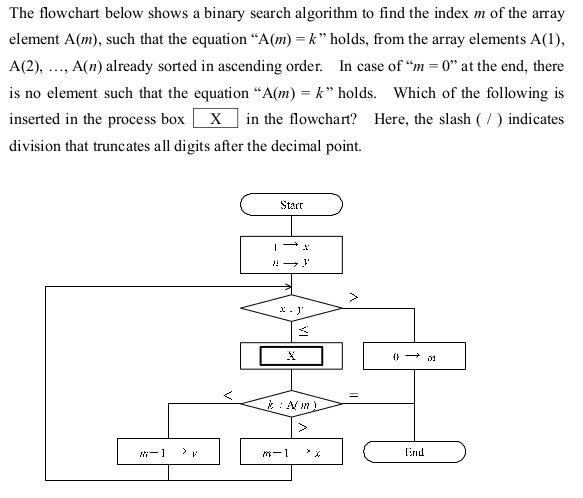","answer_label":"(x + y) / 2 → m","answer_id":18386},{"id":4386,"question":"How many memory cells (or latches for holding 1 bit each) are implemented in SRAM with 24 address lines and 16 data lines?\n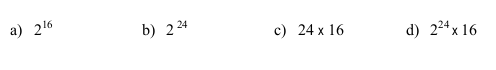","answer_label":"d","answer_id":18392},{"id":4390,"question":"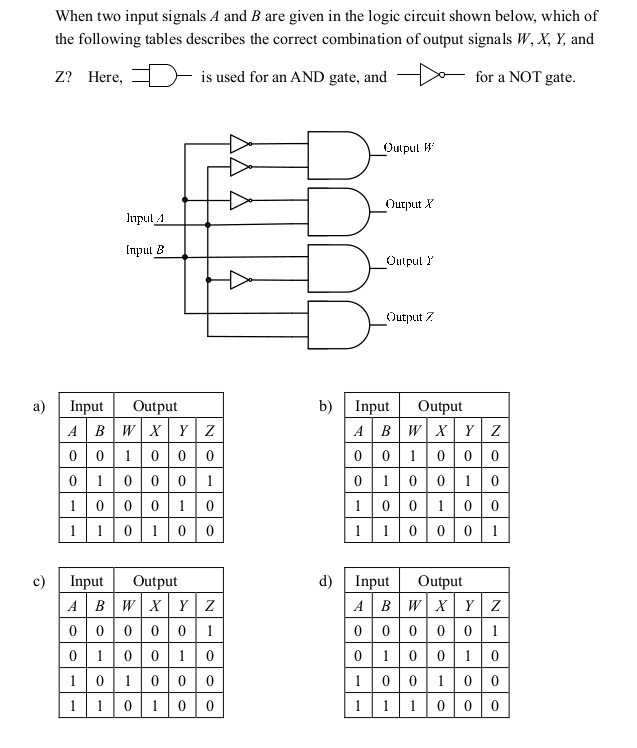","answer_label":"b","answer_id":18398},{"id":4393,"question":"","answer_label":"d","answer_id":18408},{"id":4399,"question":"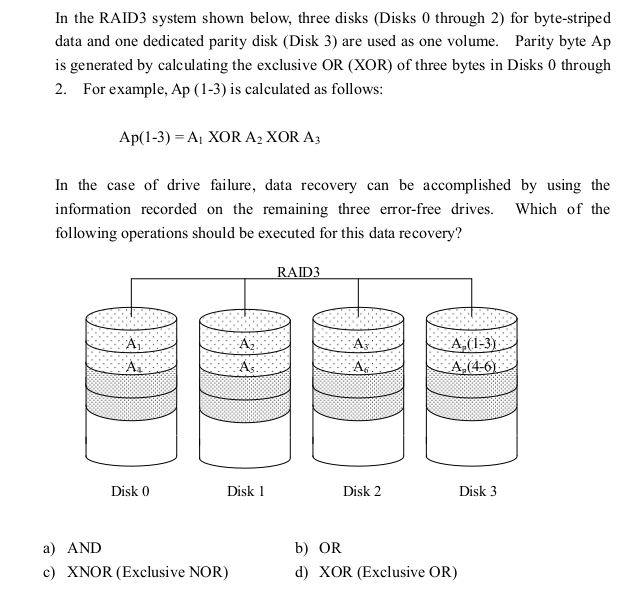","answer_label":"d","answer_id":18426},{"id":4406,"question":"","answer_label":"d","answer_id":18440},{"id":4408,"question":"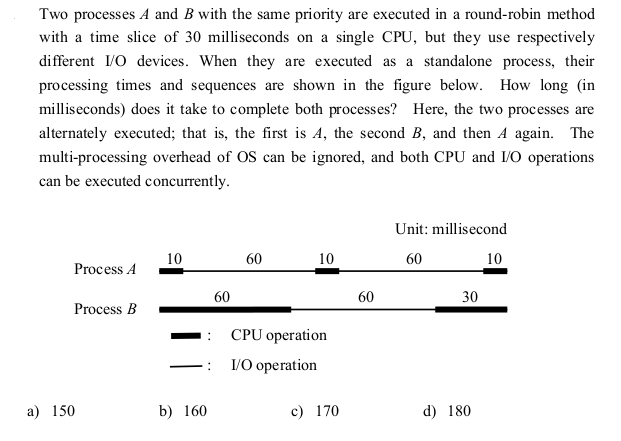","answer_label":"c","answer_id":18446},{"id":4410,"question":"","answer_label":"A","answer_id":18448},{"id":4412,"question":"","answer_label":"d","answer_id":18455},{"id":4413,"question":"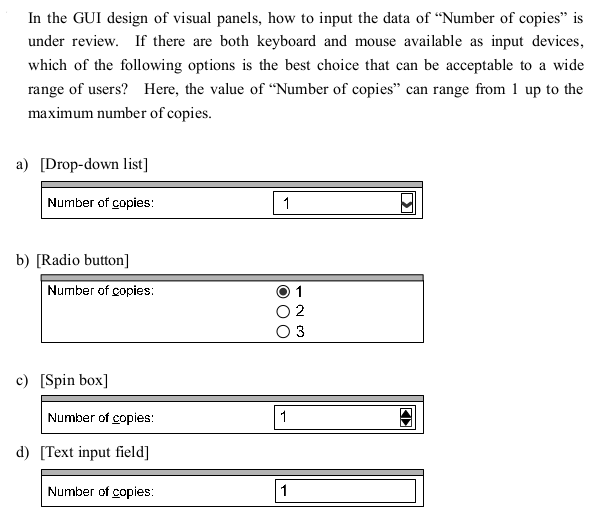","answer_label":"c","answer_id":18458},{"id":4415,"question":"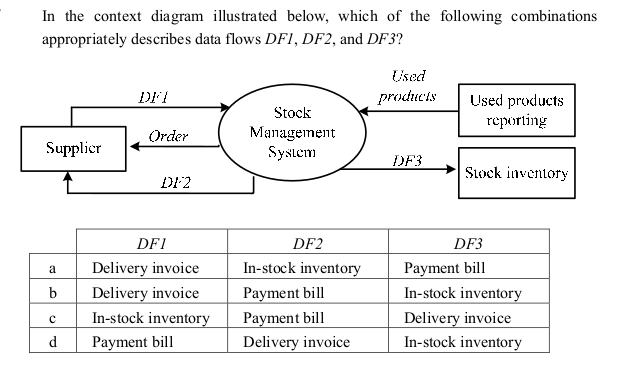","answer_label":"b","answer_id":18465},{"id":4417,"question":"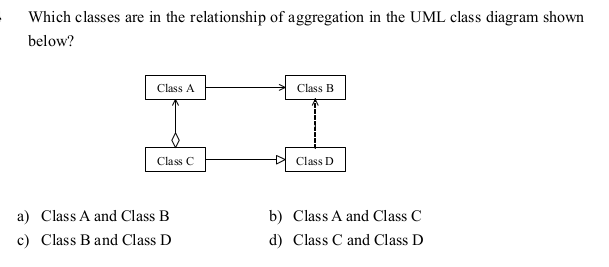","answer_label":"b","answer_id":18473},{"id":4420,"question":"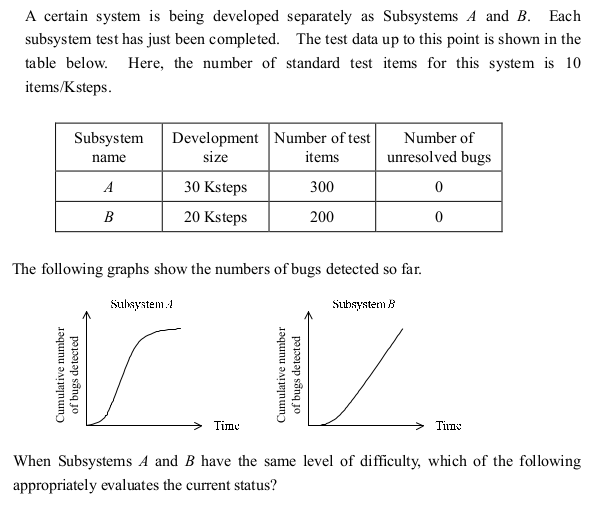","answer_label":"The number of bugs detected by the test is reaching the saturation level in\nSubsystem A compared to Subsystem B , so Subsystem A can be considered superior\nin quality.","answer_id":18486},{"id":4423,"question":"Which of the following is an appropriate description concerning the black box test?","answer_label":"Even if the program to be tested contains redundant code, such kind of code cannot be detected.","answer_id":18493},{"id":4424,"question":"Which of the following is the appropriate category of system maintenance that is performed for the purpose of adding new features to an existing system or enhancing existing features?","answer_label":"Perfective maintenance","answer_id":18499},{"id":4425,"question":"Which of the following is an appropriate explanation of Agile software development methodology?","answer_label":"A model that encompasses a group of adaptive, iterative, and incremental development methods, such as XP and Scrum, and focuses on collaboration and responding to changes in the shortest period of time in a sustainable manner","answer_id":18503},{"id":4426,"question":"Which of the following is the order that activities A through F are performed in a system development process using a waterfall model?\n[Description of activities]\nA : Investigating and analyzing current problems, and defining requirements for the target system\nB : Dividing functions required for the system into programs, and clarifying the flow of processing\nC : Designing detailed procedures, and writing code\nD : Performing tests\nE : Designing the internal structure of each program\nF : Defining functions needed as the system on the basis of the system requirements specifications","answer_label":"A , F , B , E , C , D","answer_id":18506},{"id":4427,"question":"In the development process, which of the following is an activity that should be performed in software architecture design?","answer_label":"Deciding how to implement the software requirements that are already defined","answer_id":18510},{"id":4428,"question":"Which of the following is an activity that is performed during the WBS creation process in project scope management?","answer_label":"Segmenting project activities hierarchically into smaller parts or pieces","answer_id":18516},{"id":4429,"question":"When the creation status of design documents is as described in the table below, how many person-hours are additionally needed to complete the creation of all three types of design documents?\n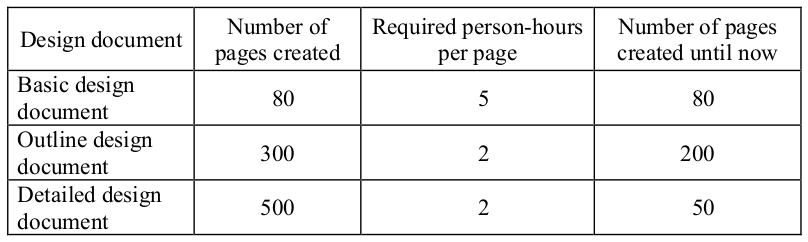","answer_label":"1100","answer_id":18519},{"id":4430,"question":"When the new procurement of a system is undertaken on the basis of the decision tree shown below, which of the following is the most appropriate course of action to be selected from a viewpoint of the lowest expected cost? Here, values enclosed in parentheses indicate the probability of each option, and the rightmost value is the estimated cost of each option. The expected cost of each choice (i.e., Build, Reuse, Buy, or Contract) is calculated as follows:\n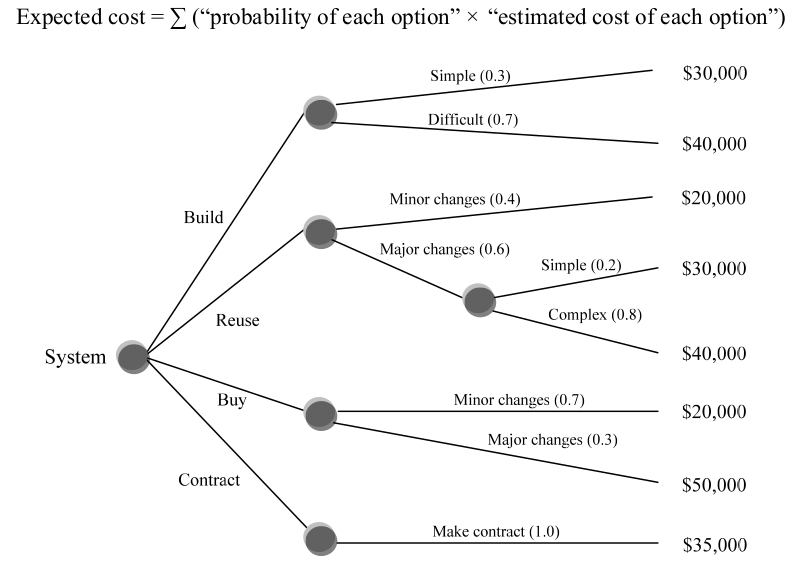","answer_label":"Buy","answer_id":18522},{"id":4431,"question":"The development scale of a new system is estimated as 500 Function Points (FPs). In the project for developing this system, in addition to the person-hours for development, 10 person-months are necessary for the installation of the system and the education of developers. Also, 10% of the person-hours for development, installation, and education are required for project management. How many person-months in total are necessary for this project? Here, the productivity in development is 10 FPs per one person-month.","answer_label":"66","answer_id":18528},{"id":4438,"question":"From a viewpoint of corporate management, which of the following is an explanation of BPM?","answer_label":"The management cycle of analysis, design, execution, and improvement is incorporated into business processes so that business processes can be continuously reviewed for improvement and integrated with optimum processes.","answer_id":18555},{"id":4439,"question":"Which of the following is an explanation of SOA (Service-Oriented Architecture)?","answer_label":"It is a concept that the functions of software are considered as components called services, and these services are combined together to construct a system.","answer_id":18560},{"id":4440,"question":"Which of the following is an explanation of SCM?","answer_label":"A series of business operations including purchase, production, sale, and distribution is reviewed from the viewpoint of total optimization among companies in order to reduce delivery lead time and inventory.","answer_id":18561},{"id":4441,"question":"Which of the following corresponds to an example of “ non-functional ” requirements?","answer_label":"Selecting development standards based on the language used in system development","answer_id":18567},{"id":4442,"question":"When a company’s own product is analyzed by using a SWOT analysis, which of the following is classified as an external factor?","answer_label":"Threats of new competitors","answer_id":18572},{"id":4443,"question":"Which of the following is the purpose of CRM?","answer_label":"To acquire customer loyalty and maximize customer lifetime value","answer_id":18573},{"id":4444,"question":"Which of the following is an explanation of social media?","answer_label":"It provides a mechanism that promotes the connection between users so that the information posted by a user over the Internet is widely transmitted to a large number of users.","answer_id":18578},{"id":4445,"question":"Which of the following is an explanation of core competence adopted in business administration?","answer_label":"It refers to a bundle of a company’s unique skills and technologies that are the source of competitive superiority and are superior to those of competitors.","answer_id":18581},{"id":4446,"question":"Which of the following is the procurement process that enables suppliers to bid against one another on the Internet in order to sell their products or services under the conditions specified by a general customer?","answer_label":"Reverse auction","answer_id":18587},{"id":4447,"question":"Which of the following is an explanation of knowledge management?","answer_label":"Business is conducted to enhance the problem-solving ability of the entire workforce by sharing information, skills, and understanding dispersed across a company.","answer_id":18590},{"id":4448,"question":"A restaurant is to be opened for business under the conditions shown below. In order to make the monthly profit of 50,000 dollars, how many customers are necessary for each seat per business day?\n","answer_label":"3","answer_id":18594},{"id":4449,"question":"Which of the following is an explanation of an affinity diagram?","answer_label":"It is a method by which the collected information is grouped according to the mutual relationship, and the problems to be resolved are clarified.","answer_id":18598},{"id":4453,"question":"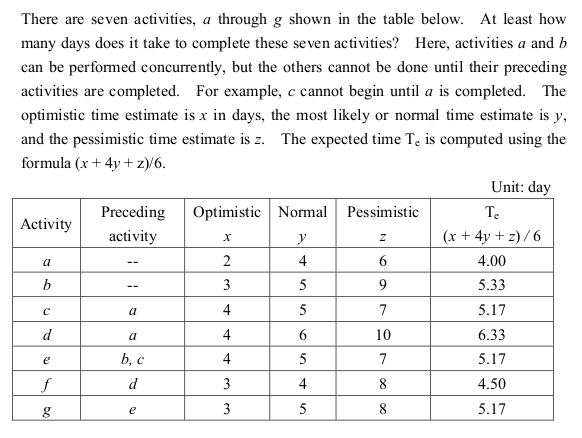","answer_label":"19.51","answer_id":18614},{"id":4490,"question":"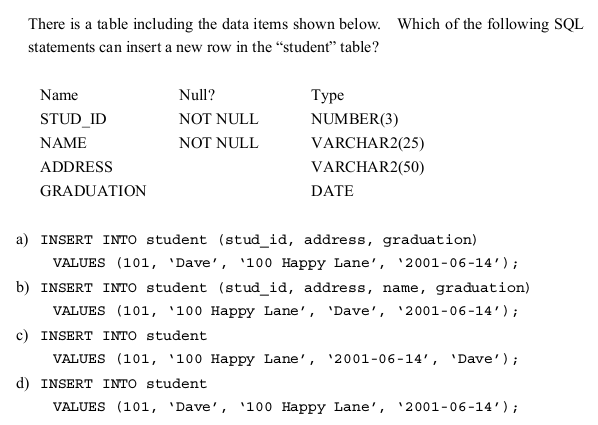","answer_label":"b","answer_id":18728},{"id":4491,"question":"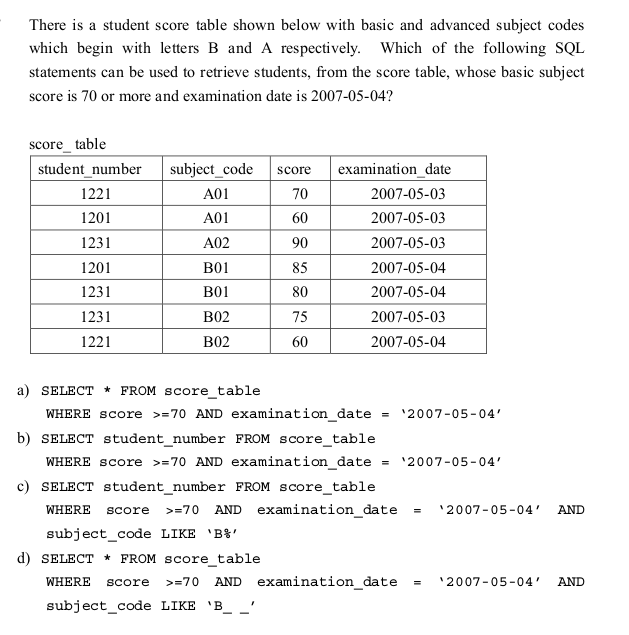","answer_label":"c","answer_id":18733},{"id":4518,"question":"","answer_label":"b","answer_id":18838},{"id":4573,"question":"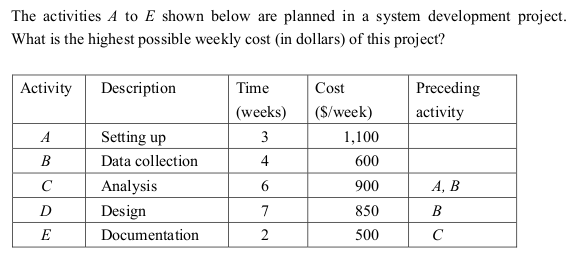","answer_label":"1,750","answer_id":19024},{"id":4575,"question":"","answer_label":"d","answer_id":19032},{"id":4580,"question":"In what radix does the following equation hold?\n131 − 45 = 53","answer_label":"7","answer_id":19036},{"id":4581,"question":"In a certain program, in order to stay in a loop, variable X must be in the range from 1\nthrough 10 (X >= 1 AND X <= 10). In this program, which of the following is the\ncondition of exiting the loop? Here, “AND” and “OR” are the logical product and\nlogical sum operations respectively. In addition, comparison operators <, <=, >, and\n>= are less than, less than or equal to, greater than, and greater than or equal to,\nrespectively.","answer_label":"X < 1 OR X > 10","answer_id":19042},{"id":4582,"question":"The formula shown below is represented in postfix (or reverse Polish) notation.\nWhich of following is the resulting value of this formula?\n5 1 – 3 * 3 1 – 2 * /","answer_label":"3","answer_id":19044},{"id":4583,"question":"There are five different sizes of white balls and five different sizes of green balls.\nWhen these ten balls are laid out in a line so that adjacent balls can have different\ncolors, how many arrangements of the balls can be made?","answer_label":"28,800","answer_id":19049},{"id":4584,"question":"A coin is tossed three times. What is the probability that it lands on heads exactly one time?","answer_label":"0.375","answer_id":19054},{"id":4585,"question":"A singly linked list is implemented using two arrays VALUE and LINK, in which\nLINK(I) points to the successor of VALUE(I). When a new element that does not\nexist initially in the list is assigned to VALUE(J), the program fragment shown below\nis executed.\nprogram?\nLINK(J) <- LINK(I);\nLINK(I) <- J;","answer_label":"VALUE(J) is inserted after VALUE(I) in the list.","answer_id":19056},{"id":4586,"question":"When a list of 7 elements shown below is rearranged in ascending order, which of the\nfollowing sorting algorithms is completed with the minimum number of element\nexchanges?\n\n3 | 5 | 12 | 9 | 10 | 7 | 15","answer_label":"Shell sort","answer_id":19062},{"id":4587,"question":"Which of the following interrupts can signal to OS that a program might have gone\ninto an infinite loop?","answer_label":"Timer Interrupt","answer_id":19066},{"id":4588,"question":"Which of the following appropriately explains the pipeline processing method of\nprocessors?","answer_label":"Method whereby one processor simultaneously executes multiple instructions with\nslight delays in time","answer_id":19070},{"id":4589,"question":"Which of the following appropriately describes cache memory?","answer_label":"Two methods exist: one is to rewrite both the cache and main memory when a write\ninstruction is executed; the other is to rewrite only the cache memory while the main\nmemory is not rewritten until the data is removed from the cache memory.","answer_id":19074},{"id":4590,"question":"A system manages files by allocating file storage on a block-by-block basis, where\neach block consists of eight 500-byte sectors. How many sectors in total are required\nto store two files: one with 2,000 bytes and the other with 9,000 bytes? Here, sectors\nfor management information such as directories can be ignored.","answer_label":"32","answer_id":19078},{"id":4591,"question":"Which of the following is an appropriate description concerning the characteristics of\nUSB?","answer_label":"It has three data transfer modes: high-speed mode for external hard disks, full-speed\nmode for printers and scanners, and low-speed mode for keyboards and mice.","answer_id":19079},{"id":4592,"question":"In a multiprogramming environment, there is a need to limit access to shared\nresources; that is, the current process has exclusive use of the assigned resources for\nsome period of time. Which of the following appropriately describes the function to\nsuccessfully implement this type of exclusive control?","answer_label":"A semaphore variable is used to indicate the status of common resource.","answer_id":19084},{"id":4593,"question":"In virtual memory systems, serious degradation of system performance may occur due\nto a large number of page faults. Which of the following terms most appropriately\ndescribes this situation?","answer_label":"Thrashing","answer_id":19090},{"id":4594,"question":"The FIFO method is used as the page-replacing algorithm in virtual memory. There\nare 3 page frames available for a program in main memory, and the page numbers\nreferred to by a program are 4 → 3 → 2 →1 → 3 → 5 → 2 in this order. How many\ntimes does page-in occur during execution of the program? Here, nothing is loaded\ninto main memory in the initial state.","answer_label":"5","answer_id":19093},{"id":4595,"question":"Which of the following is an appropriate description concerning throughput?","answer_label":"Spooling in which the output to the printer is temporarily stored on a hard disk drive\nis helpful for increasing the throughput.","answer_id":19095},{"id":4596,"question":"Last year, a company providing web application services needed an Internet line to\nservice clients’ demand at that time. However, in order to increase availability, the\ncompany actually made use of two Internet lines from different vendors. This year,\nthe demand is doubled and both lines are fully busy, so the company will install one\nmore Internet line. Each of the Internet lines has availability of 80%. What\npercentage of availability will be cut down after the installation?","answer_label":"7.8","answer_id":19101},{"id":4597,"question":"Which of the following is an appropriate language that can be used to develop\napplications running mainly on Web browsers?","answer_label":"JavaScript","answer_id":19105},{"id":4598,"question":"Which of the following appropriately describes a typical feature of ADSL?","answer_label":"By separating the frequency bands used by analog telephones and data\ncommunications, it allows both of these connections to be used simultaneously.","answer_id":19107},{"id":4599,"question":"Which of the following is an appropriate description concerning the spiral model?","answer_label":"The design and implementation of an application is performed for a unit of\ncomponent, and then this process is repeated successively for every component.","answer_id":19114},{"id":4600,"question":"Which of the following characteristics can be found in well-designed modules with a\nhigh degree of independence?","answer_label":"Low coupling and high cohesion","answer_id":19117},{"id":4601,"question":"In object orientation, the term “open (white box) reuse” refers to the reusing of\nbase-class data and functions by creating subclasses for the base class. Which of the\nfollowing is the appropriate description concerning the reuse technology in object\norientation of this method?","answer_label":"Only differences between the data and functions defined by the base class and those\nof subclasses can be stated in subclasses, so development is highly efficient.","answer_id":19120},{"id":4602,"question":"Which of the following is the method in which the designer and a group of involved\npersonnel review the design documents at the completion of each design for the\npurpose of early detection of design errors?","answer_label":"Walk-through","answer_id":19126},{"id":4603,"question":"Which of the following appropriately explains a tracer as one of the dynamic\ndebugging tools?","answer_label":"It outputs the contents of the memory and registers in order to monitor the results of\nthe program execution in chronological order.","answer_id":19130},{"id":4604,"question":"Full backup and differential backup are two methods of backing up a database.\nWhich of the following appropriately describes the differential backup method?","answer_label":"To recover a database, the full backup data is restored and then the differential\nbackup data is added.","answer_id":19134},{"id":4605,"question":"Which of the following most appropriately describes the handling of control\ninformation in system operation management?","answer_label":"The system should be managed by a small group of managers. Each manager\nshould be given an exclusive and separate account. Control information should be\ndisclosed to the general user after its security level and other factors are considered.","answer_id":19138},{"id":4606,"question":"Which of the following is an appropriate description concerning countermeasures to\nonline system failures?","answer_label":"The master file should be backed up not only at the completion of online service but\nat times corresponding to the characteristics of the system.","answer_id":19142},{"id":4607,"question":"Which of the following can make MTBF longer in system maintenance?","answer_label":"To do preventive maintenance","answer_id":19144},{"id":4608,"question":"When a network device is connected to the LAN with the network address of\n201.12.1.64 and the subnet mask of 255.255.255.192, which of the following IP\naddresses should NOT be assigned to the device on the network?","answer_label":"201.12.1.127","answer_id":19150},{"id":4609,"question":"Which of the following is the appropriate protocol that is widely used with TCP/IP\nnetworks to collect and manage information from network devices such as servers,\nrouters, switches, and hubs?","answer_label":"SNMP","answer_id":19154},{"id":4610,"question":"Which of the following is the appropriate protocol that is used to send e-mail\nmessages from one server to another over the Internet?","answer_label":"SMTP","answer_id":19158},{"id":4611,"question":"Which of the following operations is performed on the packet header while the data\npacket moves from the lower to upper layers according to the OSI basic reference\nmodel?","answer_label":"Header deletion","answer_id":19160},{"id":4612,"question":"Which of the following occurs when computer A broadcasts an ARP request to find\nthe MAC address of computer B on the same network?","answer_label":"All computers in network receive the request from A , and only B replies to A with its\nMAC address.","answer_id":19164},{"id":4613,"question":"Which of the following is the general-purpose markup language that allows its users\nto define their own tags and to facilitate the sharing of data across different\ninformation systems, particularly via the Internet?","answer_label":"XML","answer_id":19170},{"id":4614,"question":"Which of the following is the key technology that enables to connect a computer using\na private IP address to the Internet?","answer_label":"NAT","answer_id":19173},{"id":4615,"question":"Which of the following provides the function of mapping between domain names and\nIP addresses in a TCP/IP network?","answer_label":"DNS","answer_id":19176},{"id":4616,"question":"Which of the following is an appropriate purpose of installing a firewall in a computer\nnetwork?","answer_label":"To block and permit data traffic","answer_id":19180},{"id":4617,"question":"Which of the following is described graphically using an E-R diagram?","answer_label":"Entities and relationships between entities","answer_id":19185},{"id":4618,"question":"You are building a new database for a company with 10 departments. Each\ndepartment contains multiple employees. In addition, each employee might work for\nseveral departments. How should you logically model the relationship between the\ndepartment entity and the employee entity?","answer_label":"Create a new entry, create a one-to-many relationship from the employee to the new\nentry, and create a one-to-many relationship from the department entry to the new\nentry.","answer_id":19188},{"id":4619,"question":"Which of the following is an appropriate explanation concerning functions of\nkeywords in SQL?","answer_label":"“HAVING” specifies a search condition for an aggregate or a group.","answer_id":19191},{"id":4620,"question":"User A issues the command as follows:\n\nUPDATE cust_orders\nSET id = 200\nWHERE id = 1\n\nThen user B issues this command as follows:\n\nUPDATE cust_orders\nSET id = 300\nWHERE id = 1\n\nUser B informs you that his/her UPDATE statement seems to be hung.\nfollowing is a possible solution that you can find?","answer_label":"Ask user A to commit the transaction.","answer_id":19195},{"id":4621,"question":"In database recovery management, which of the following appropriately explains\nincremental logging with deferred update?","answer_label":"The new value of the updated item is stored in the log.","answer_id":19201},{"id":4622,"question":"What is the purpose of attaching a digital signature to software disclosed on the\nInternet?","answer_label":"To guarantee that the software contents have not been tampered with","answer_id":19203},{"id":4623,"question":"Which of the following can be realized by using the packet filtering function of a\nfirewall?","answer_label":"To allow only the packets with specific TCP port numbers to pass from the Internet\nthrough to the internal network","answer_id":19207},{"id":4624,"question":"Which of the following is the salami technique used in computer crime?","answer_label":"Stealing from multiple assets little by little, to a degree that the illegal action does\nnot come to the surface and become noticeable","answer_id":19214},{"id":4625,"question":"Which of the following is a method of phishing?","answer_label":"Someone sends e-mails to entice the recipients and to have them access fake Web\nsites that appear to be sites of actually existing companies etc. and steals personal\ninformation.","answer_id":19217},{"id":4626,"question":"Which of the following is a characteristic of the QR code?","answer_label":"Using three symbols for detection, the code makes it possible to recognize the\nrotation angle and the direction of reading.","answer_id":19222},{"id":4627,"question":"A data warehouse was set up, but it is hardly used. The result of a hearing suggests\nthat the users’ skill level is lower than expected. Which of the following is an\nappropriate measure for improvement to promote usage?","answer_label":"To prepare, as standards, templates according to data extraction and analysis patterns","answer_id":19224},{"id":4628,"question":"Which of the following appropriately describes financial statements?","answer_label":"Profit and loss statement is also known as the income statement. This presents\nhow revenues are converted to net income by reporting both revenues and expenses\nof the company for a given period of time.","answer_id":19229},{"id":4629,"question":"Which of the following is the appropriate statement according to the Pareto analysis\n(also known as the 80-20 rule)?","answer_label":"This is the idea that 80% of tasks can be completed in 20% of the disposable time. The remaining 20% of tasks will take up 80% of the time.","answer_id":19233},{"id":4630,"question":"The seven traditional, fundamental quality control tools consist of Check sheet, Pareto\nchart, Stratification, Scatter Diagram, Histogram, and Control Chart. What is the last\n(or 7th) one?","answer_label":"Cause and effect diagram","answer_id":19236},{"id":4631,"question":"A server runs a regional web application. It services the requests coming in from all\nregional offices. Each request is completed in 80 milliseconds on average. A total\nof 10 requests per second arrive at the server on average. If the M/M/1 queuing\nmodel can be applied, how many requests are waiting for the service on average?","answer_label":"4","answer_id":19240},{"id":4632,"question":"There are goods whose unit purchase prices are gradually rising. There was an\ninventory of these goods at the end of the last accounting period, and the goods were\ncarried into and out of the warehouse several times during the current period. Which\nof the following valuation methods produces the lowest valuation of the inventory at\nthe end of the current period?","answer_label":"Last-in first-out method","answer_id":19245},{"id":4677,"question":"In software development that uses the waterfall model, which of the following is an appropriate description concerning the cost of fixing errors detected during an operational test?","answer_label":"External design errors affect not only the program but also manuals and other documents, so those errors cost more to fix than coding errors.","answer_id":19389},{"id":4678,"question":"Which of the following is a chart or a diagram that shows the quality of a product in order of time and is used for determining whether or not the production process is in a stable state within the control limits?","answer_label":"Control chart","answer_id":19393},{"id":4679,"question":"When a declining metered rate method is applied to the total charge for usage of a computer system, the charge per unit of usage decreases as the system usage increases. \nWhich of the following is a graph that shows this method?\n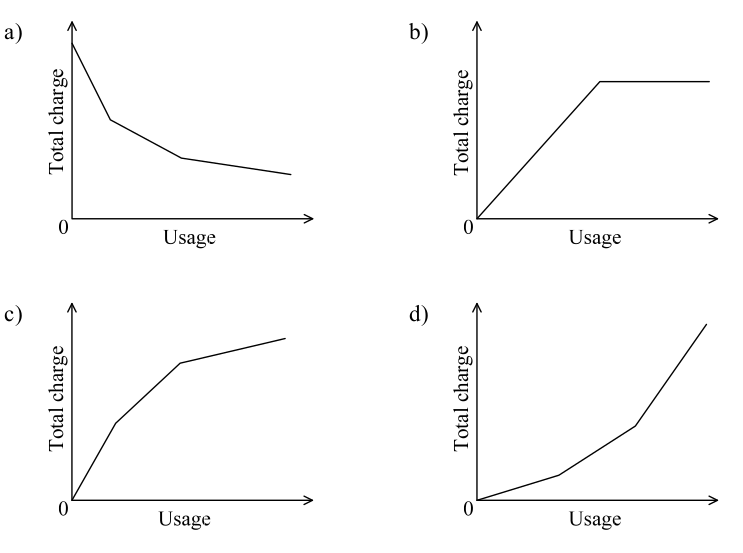","answer_label":"c","answer_id":19398},{"id":4680,"question":"Which of the following is an appropriate description concerning application maintenance?","answer_label":"The completion of maintenance is recorded in order to prevent maintenance activities from being left unfinished.","answer_id":19400},{"id":4681,"question":"Among the characteristics of the structure of a service desk organization, which of the following is a characteristic of the local service desk?","answer_label":"By placing the service desk close to users, intensive services are provided for users who have different languages and cultures or for VIPs by specialized service staff members.","answer_id":19406},{"id":4682,"question":"In the stage of system design, when an audit is performed on the control for reducing the risk that user requirements are not met, which of the following is a point to be checked?","answer_label":"Checking if the user department participates in the review of the system design documents","answer_id":19411},{"id":4683,"question":"When IT control is classified into preventive control and detective control, which of the following is applicable to detective control?","answer_label":"An output list resulting from data entry is cross-checked with the input form.","answer_id":19415},{"id":4684,"question":"Which of the following is a deliverable of data architecture that is one of the four architectures contained in Enterprise Architecture?","answer_label":"E-R diagram","answer_id":19416},{"id":4685,"question":"Which of the following enables users to connect to the system of a service provider via the Internet and make online use of the necessary functions of the applications that are offered by the service provider as needed?","answer_label":"SaaS (Software as a Service)","answer_id":19421},{"id":4686,"question":"When a computerization plan is made, which of the following is an item to be considered?","answer_label":"Clarifying the cost and investment effect of development, maintenance, and operations","answer_id":19424},{"id":4687,"question":"Which of the following is an item to be performed in the requirements definition process of system development?","answer_label":"Clarifying the procedures and rules of new business operations together with the constraints, and obtaining agreement between stakeholders","answer_id":19429},{"id":4688,"question":"Which of the following is an appropriate explanation of the benchmarking used for corporate management?","answer_label":"Understanding products, services, and operations of the company qualitatively and\nquantitatively in comparison with those of the strongest competitor or a leading company","answer_id":19435},{"id":4689,"question":"Which of the following is an explanation of marketing mix?","answer_label":"A company’s products are effectively sold by combining product strategy, price strategy, channel strategy, promotion strategy, and others appropriately.","answer_id":19436},{"id":4690,"question":"Which of the following is an appropriate explanation of demographic segment that is one of the market segments?","answer_label":"A group of a population segmented by factors such as age, gender, family size, income, occupation, education, religion, race, generation, and nationality","answer_id":19442},{"id":4691,"question":"Which of the following is an appropriate explanation of product innovation in the management of technology?","answer_label":"Developing new products or products differentiated from other companies","answer_id":19444},{"id":4692,"question":"Which of the following is the situation where an improvement can be expected by installing an MRP (Material Requirements Planning) system?","answer_label":"Information about materials and quantities necessary for production is complicated, so a miscalculation of order quantity or an interruption of production often occurs.","answer_id":19450},{"id":4693,"question":"When production is planned based on the calculation formula and table shown below, what is the value for production plan C ? Here, the carry-over inventory on April 1 is equal to 400 pieces of the actual inventory on March 31.\n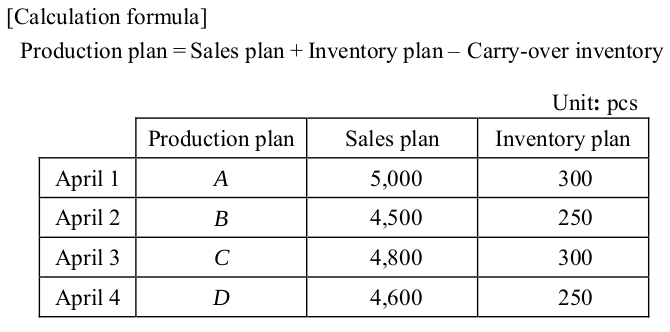","answer_label":"4,850","answer_id":19454},{"id":4694,"question":"Which of the following is an explanation of BCP (Business Continuity Plan)?","answer_label":"In order to avoid risks of business interruptions or recover promptly from damages, a policy or an activity procedure is prepared in advance.","answer_id":19458},{"id":4695,"question":"Which of the following is an organization that is formed for a certain limited period of time to solve a problem and is disbanded when the problem is solved?","answer_label":"Project organization","answer_id":19463},{"id":4696,"question":"Which of the following is a two-layered chart that is composed of a bar chart showing control items arranged in descending order of frequency and a line chart showing the cumulative percentage of each item?","answer_label":"Pareto chart","answer_id":19466},{"id":4697,"question":"Which of the following is a method which can be used to calculate a predicted value based on actual values of the previous time period and in which each of the actual values is equally weighted?","answer_label":"Moving average method","answer_id":19471},{"id":4698,"question":"Which of the following is a financial statement that represents the assets, liabilities, and net assets of a company at a certain point in time and indicates the financial condition of the company?","answer_label":"Balance sheet","answer_id":19472},{"id":4699,"question":"When a publisher’s lead editor omits a section of an author’s manuscript without obtaining the consent of the author, which of the following is infringed according to the international treaty called the Berne Convention for the Protection of Literary and Artistic Works?","answer_label":"Moral rights","answer_id":19477},{"id":4740,"question":"Which of the following arithmetic expressions is correct? Here, a number is written in radix notation; that is, a decimal subscript following the number \n is used to indicate the radix.\n","answer_label":"b","answer_id":19596},{"id":4741,"question":"When the binary fraction 11101.110 is subtracted from the binary fraction 101101.101, what is the correct result?","answer_label":"1111.111","answer_id":19602},{"id":4742,"question":"When a certain natural number x can be represented by a 2n-digit binary number consisting of 1 and 0 arranged alternately, i.e. 1010...10, which of the following equations holds for x?\n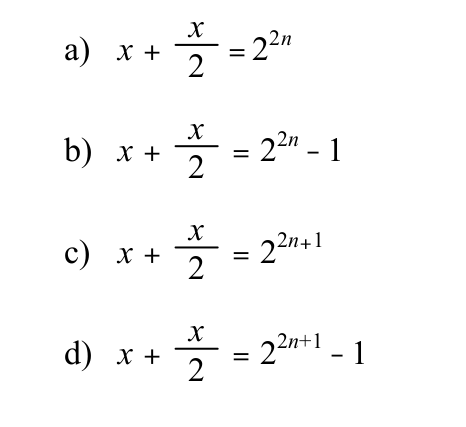","answer_label":"b","answer_id":19604},{"id":4743,"question":"There is an 8-bit numerical value, where a negative number is represented in two’s complement. When this value is represented in decimal, it becomes -100. When this value is regarded as an unsigned number, which of the following is the correct value in decimal?","answer_label":"156","answer_id":19609},{"id":4744,"question":"When multiple values are added arithmetically, it is recommended that the values be added sequentially, starting from the number whose absolute value is the smallest. Which of the following errors can be reduced by means of this method?","answer_label":"Loss of trailing digits","answer_id":19612},{"id":4745,"question":"The figure below shows daily changes in the weather for a given district, and each value represents the probability of changes in the following day’s weather. When the weather is rainy on a given day, what is the probability that the weather is clear two days later?\n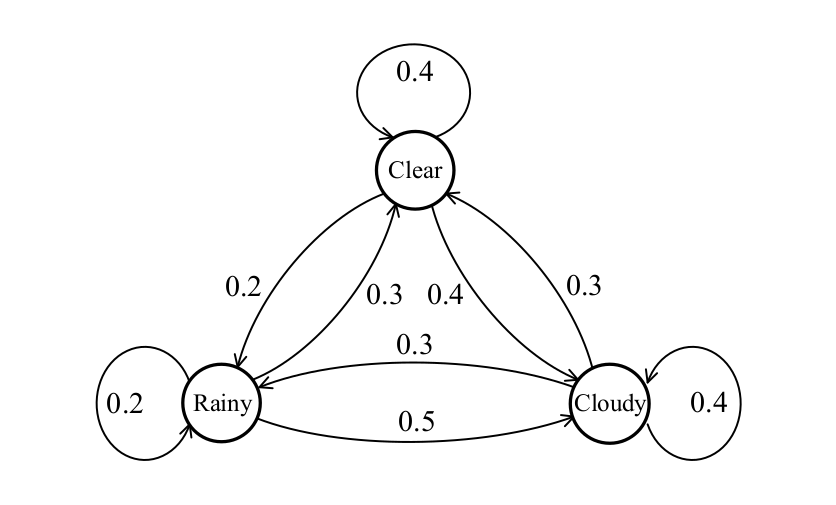","answer_label":"0.33","answer_id":19618},{"id":4746,"question":"Which of the following operations does not change the lower 4 bits of an 8-bit string?","answer_label":"A logical product (i.e. AND) with a bit string 0F in hexadecimal","answer_id":19619},{"id":4747,"question":"In a certain company, there are a total of 400 employees including 100 smokers. The number of male employees is 250, including 75 male smokers. What is the probability that an employee selected at random is a female nonsmoker?\n","answer_label":"d","answer_id":19626},{"id":4748,"question":"The decision table shown below is used to determine whether or not an order can be accepted in a sales order processing system. Which of the following logical expressions is equivalent to “Accept order”? Here, “NOT” is used for the logical negation, “AND” for the logical product, and “OR” for the logical sum.\n","answer_label":"b","answer_id":19628},{"id":4749,"question":"Which of the following sets is equivalent to the set 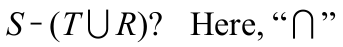\n Here,  stands for a product set operation, 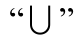\n for a union set operation, and “ - ” for a difference set operation.\n","answer_label":"a","answer_id":19631},{"id":4750,"question":"The figure below shows the state transition diagram of an automaton that accepts bit strings with even numbers of 1s. The double circle marked with “Even” represents the accepted state. Which of the following combinations should be inserted in the blank boxes labeled A and B ?\n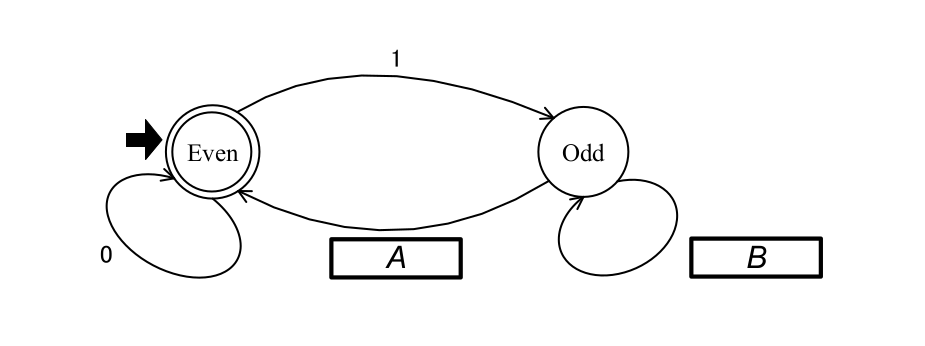\n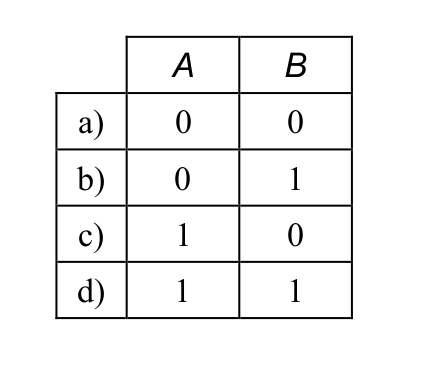","answer_label":"c","answer_id":19637},{"id":4751,"question":"Which of the following is the minimum possible depth of a binary tree with 14 nodes?","answer_label":"3","answer_id":19639},{"id":4752,"question":"Which of the following appropriately describes a characteristic of linked lists?","answer_label":"The elements cannot be accessed directly or randomly.","answer_id":19645},{"id":4753,"question":"There is a two-dimensional array A ( m , n ) with m rows and n columns, and the array in physically contiguous memory addresses is accessed such that rows are stored one after another, in row-major order. Which of the following is the correct memory address of any given element A ( i , j )? Here, both m and n are greater than 0, and the indices i and j range from 1 to m and n respectively. In addition, x is the memory address of the element A (1,1).","answer_label":"x + n × ( i – 1) + ( j – 1)","answer_id":19648},{"id":4754,"question":"When a list of seven elements shown below is rearranged in ascending order, which of the following sorting algorithms is completed with the minimum number of element exchanges?\n","answer_label":"Selection sort","answer_id":19652},{"id":4755,"question":"When a program (or a function) calls itself recursively, which of the following data structures is suitable for storing the data that is currently used in the program?","answer_label":"Stack","answer_id":19656},{"id":4756,"question":"Which of the following logic circuits (i), (ii), and (iii) is or are equivalent to the circuit shown in Figure 1?\nHere, A and B are input signals and F is an output signal. \n stands for an OR gate,  for an AND gate,  for a NAND gate, and  for a NOT gate.\n","answer_label":"(i), (ii), and (iii)","answer_id":19661},{"id":4757,"question":"When two D flip-flops are connected as shown below, which of the following timing charts represents this logic circuit? Here, in D flip-flop, an input signal is read in and held as an output signal only when a clock signal is changed from zero (or low) to one (or high). In other cases, no state transition occurs.\n\n","answer_label":"b","answer_id":19663},{"id":4758,"question":"Which of the following is a high-speed memory technology that uses flip-flop circuits?","answer_label":"SRAM","answer_id":19669},{"id":4759,"question":"In a certain intrusion detection system, a detector is driven by a 4 KHz crystal clock oscillator and checks intrusion every 1,000 clock pulses. How many times per minute does the detector check intrusion in this system?","answer_label":"240","answer_id":19672},{"id":4760,"question":"Which of the following addressing modes is shown in the figure below?\n","answer_label":"Indexed addressing mode","answer_id":19675},{"id":4761,"question":"A CPU that operates at 1 GHz is known to execute one machine-language instruction in an average time of 0.8 clocks. Approximately how many million instructions can be executed by this CPU in one second?","answer_label":"1250","answer_id":19681},{"id":4762,"question":"There is a hard disk drive that has the following specifications.\n\nHow many bytes can be stored in one track of this hard disk drive? Here, each track has the same capacity. 1 GByte is 10 9 bytes, and 1 Mbyte is 10 6 bytes.","answer_label":"50 Mbytes","answer_id":19684},{"id":4763,"question":"From a point of view of better performance, improved fault tolerance, and enhanced data integrity, which of the following RAID configurations is commonly suitable for enterprise systems?","answer_label":"RAID 5","answer_id":19689},{"id":4764,"question":"Which of the following is an explanation of USB?","answer_label":"A serial interface that connects devices in a tree topology via hubs","answer_id":19690},{"id":4765,"question":"When an image file is transferred from a PC at hand to another PC separated by a partition without any connection cables, which of the following interfaces can be used?","answer_label":"Bluetooth","answer_id":19694},{"id":4766,"question":"A color video clip is displayed in full-screen mode on a PC at 30 frames/second, with each screen comprising 300,000 pixels and 256 colors displayed at the same time. Under these conditions, which of the following is the approximate amount of data (in megabytes) that can be displayed in one minute? Here, the data is not compressed.","answer_label":"540","answer_id":19700},{"id":4767,"question":"With which of the following task scheduling methods is it highly possible for a specific task to continue to wait for the allocation of CPU resources?","answer_label":"The task with the shortest estimated processing time is executed first. The next task is initiated when the currently executed task is completed or suspended for some reason.","answer_id":19704},{"id":4768,"question":"When a printing operation is performed under the conditions shown below, what is the minimum number of megabytes necessary as the total capacity of the spool file?\n[Conditions]\n(1) The same job is executed continuously four times with multiplicity 1.\n(2) It takes 20 minutes to execute the job in a standalone mode.\n(3) The standalone job secures a 400-Mbyte print-spool file, where the printing data is stored.\n(4) After the job is executed, the contents of the spool file are processed by the printing function of the OS.\n(5) The OS deletes the spool file at the completion of the printing. Here, the time for this deletion can be ignored.\n(6) There is exactly one printer, and its printing speed is 10 Mbytes per minute.\n(7) Job execution and printing can be performed in parallel without one affecting the other.","answer_label":"1,200","answer_id":19708},{"id":4769,"question":"Which of the following is the appropriate purpose of using semaphores?","answer_label":"For managing shared resources","answer_id":19713},{"id":4770,"question":"The FIFO method is used as the page replacement algorithm in virtual memory. There are 3 page frames available in real memory, and a reference list of the virtual page numbers “1, 4, 2, 4, 1, 3” was allocated to real memory in this order as shown in the table below. The table, up through “assigning step 3”, shows the status of the real memory pages just after each of the first three page numbers “1, 4, 2” of the reference list was allocated to real memory. Which of the following should be inserted in the bold-lined box that indicates the last status of the real memory pages just after the remaining page numbers were referenced?\n\n","answer_label":"c","answer_id":19716},{"id":4771,"question":"When a certain job is executed in a computer system, 35 percent of the total processing time of the job is used for CPU and the rest is spent waiting for I/O to complete. If a newer CPU whose speed is three times faster than the current one is installed, approximately how many times faster is the new system than the current system? Here, the system environment except for the CPU remains unchanged.","answer_label":"1.3","answer_id":19719},{"id":4772,"question":"Which of the following is the system configuration with the highest availability? Here, multiple systems connected in parallel are considered operating if at least one system is operating.","answer_label":"Three identical systems with each availability of 80% in parallel connection","answer_id":19724},{"id":4773,"question":"When machine tools are controlled by microcomputers, which of the following focuses on fail safe?","answer_label":"The system automatically stops when an abnormal operation signal is detected.","answer_id":19729},{"id":4774,"question":"Which of the following is an appropriate explanation of availability concerning RASIS?","answer_label":"A computer system is maintained in such a state that it can be used whenever necessary.","answer_id":19730},{"id":4775,"question":"When a corporate intranet is connected to the Internet, which of the following mechanisms works as a bridge to access the Internet, enables high-speed access by caching Web content, and then is used to ensure security?","answer_label":"Proxy","answer_id":19737},{"id":4776,"question":"Which of the following is an appropriate explanation of data mining?","answer_label":"A technique that uses statistical and mathematical methods to analyze large volumes of data in order to discover rules and causal relationships","answer_id":19741},{"id":4777,"question":"Which of the following software development models is an appropriate description of the spiral model?","answer_label":"It is a model in which a large-scale system is developed by enlarging its scale of functions through the repetition of the development cycles of design, implementation, and testing on each independent subsystem.","answer_id":19743},{"id":4778,"question":"Which of the following tasks is performed in the external design phase of the waterfall model?","answer_label":"Code design","answer_id":19746},{"id":4779,"question":"Which of the following is the most appropriate description concerning software reuse?","answer_label":"More person-hours are required for development of reusable components than for regular software development of the same scale.","answer_id":19751},{"id":4780,"question":"A certain program module directly refers to the content of another module. It executes a single unique function, and some concept, data structure, or resource is hidden within the single module. From a standpoint of module independence, which of the following combinations appropriately shows the “module strength” and “module coupling” of this module?\n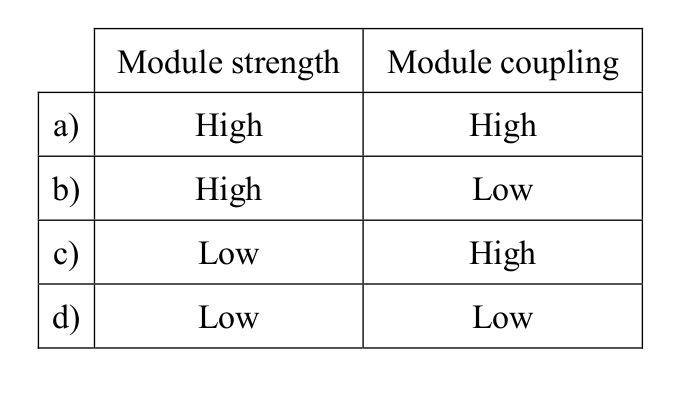","answer_label":"a","answer_id":19754},{"id":4781,"question":"The figure below shows an example of a DFD used in structured analysis. What does the symbol “◯” in the figure represent?\n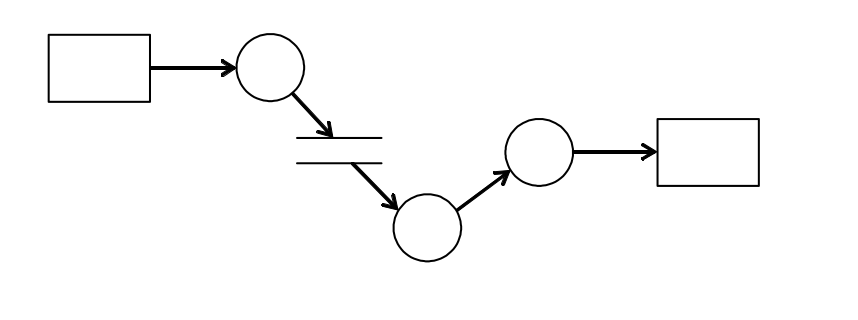","answer_label":"Process","answer_id":19761},{"id":4782,"question":"Which of the following is an explanation of encapsulation in the object-oriented paradigm?","answer_label":"Data and its related operational procedures are hidden inside objects.","answer_id":19764},{"id":4783,"question":"Which of the following combinations is described in a UML class diagram?","answer_label":"Attribute, operation, role name","answer_id":19767},{"id":4784,"question":"Which of the following is an appropriate execution sequence in the test phase of the waterfall model?","answer_label":"Unit test → Integration test → System test → Operational test","answer_id":19772},{"id":4785,"question":"In a narrow sense, which of the following is the most appropriate description concerning the function of a tracer that can be used for debugging purposes?","answer_label":"It can record program flow, such as the sequence and results of execution of the program instructions.","answer_id":19777},{"id":4786,"question":"An automated ticketing system for motorists is installed for a highway with a minimum speed limit of 60 kph (kilometers per hour) and a maximum speed limit of 100 kph. When the system is tested based on “equivalence partitioning” as a black box, which of the following is an appropriate set of speed values in kph?","answer_label":"40, 80, 120","answer_id":19779},{"id":4787,"question":"Which of the following is used for estimating the scale of system development with the function point method?","answer_label":"Number of screens","answer_id":19784},{"id":4788,"question":"In a system environment requiring continuous availability as well as a high level of reliability, which of the following is the most appropriate term that stands for the capability to automatically switch over to a standby or redundant database, a server, or a network when the previously active one fails to operate properly?","answer_label":"Fail-over","answer_id":19786},{"id":4789,"question":"A value is calculated from a given data according to specific rules, and then a check character is determined from this value and appended to the given data. This is used to check the input data. When the rules listed below are used, which of the following is the correct check character to be appended to the four-digit numeric data “2131”?\n[Rules]\n(1) Assign the coefficients 4, 3, 2, and 1 to each digit of the given data, in order from the first (leftmost).\n(2) Multiply each digit by its assigned coefficient, and calculate the sum of each product.\n(3) Divide the sum obtained in Step (2) by 11, and obtain the remainder.\n(4) The value of the remainder obtained in Step (3) is the check character. Here, when the remainder is 10, “X” is assigned to the check character.","answer_label":"7","answer_id":19793},{"id":4790,"question":"Which of the following devices is used for the purpose of protecting systems against momentary power loss and supplying just enough power for systems to shut down at the time of power outages?","answer_label":"UPS","answer_id":19797},{"id":4791,"question":"The person in charge of operating a sales management system has decided to rearrange the customer master file records in cooperation with the system users in the sales department. Which of the following is an appropriate policy for rearranging the master file?","answer_label":"Before deleting a customer record, it is necessary to first check that the customer code is not used anywhere within the sales management system and related systems.","answer_id":19798},{"id":4792,"question":"When the subnet mask “255.255.255.0” is used in a “class A” network, how many host addresses can be assigned to network devices?","answer_label":"254","answer_id":19802},{"id":4793,"question":"Which of the following protocols is used in mail servers on a TCP/IP network?","answer_label":"SMTP","answer_id":19807},{"id":4794,"question":"Which of the following protocols is supported by the transport layer of the OSI basic reference model?","answer_label":"TCP","answer_id":19813},{"id":4795,"question":"Which of the following is the network topology that is used to connect one central node or hub with point-to-point links to several other nodes?","answer_label":"Star","answer_id":19817},{"id":4796,"question":"In home and office networks of Fast or Gigabit Ethernet, which of the following cables can be used as a lower cost option for connecting a client PC to the network?","answer_label":"UTP","answer_id":19821},{"id":4797,"question":"Which of the following is a device that interconnects LANs at the physical layer of the OSI basic reference model?","answer_label":"Repeater","answer_id":19824},{"id":4798,"question":"Which of the following is the most appropriate information used by routers in order to determine the routing paths of packets?","answer_label":"Destination IP address","answer_id":19826},{"id":4799,"question":"As shown below, there are three tables Student, Instructor, and Result. Which of the following relational algebra operations can be used for deriving the table “Result” from the tables “Student” and “Instructor”?\n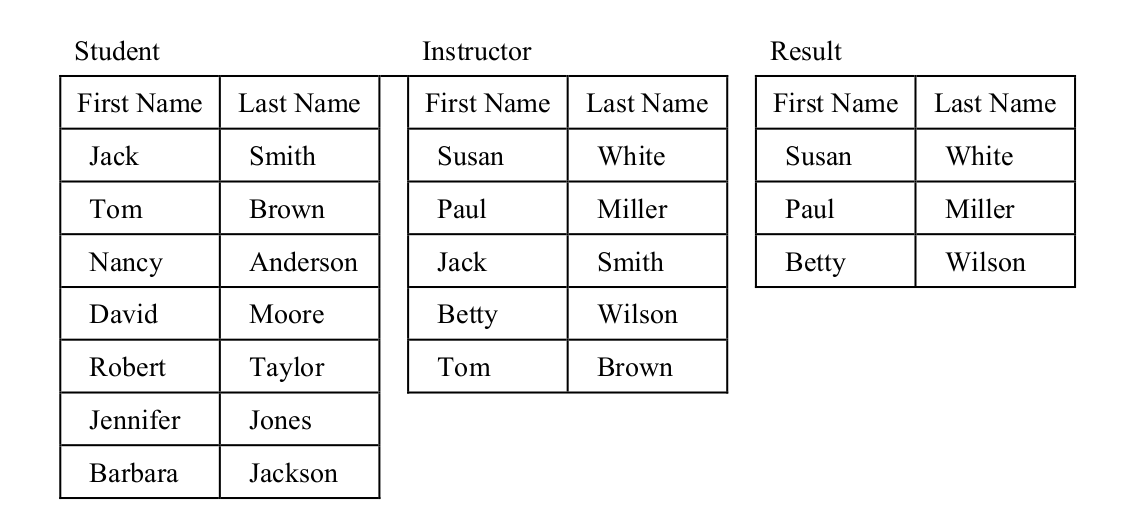\n","answer_label":"c","answer_id":19832},{"id":4800,"question":"There are three tables T1, T2, and T3 as shown below. Which of the following tables is created as the result of executing the SQL statement specified below?\n\n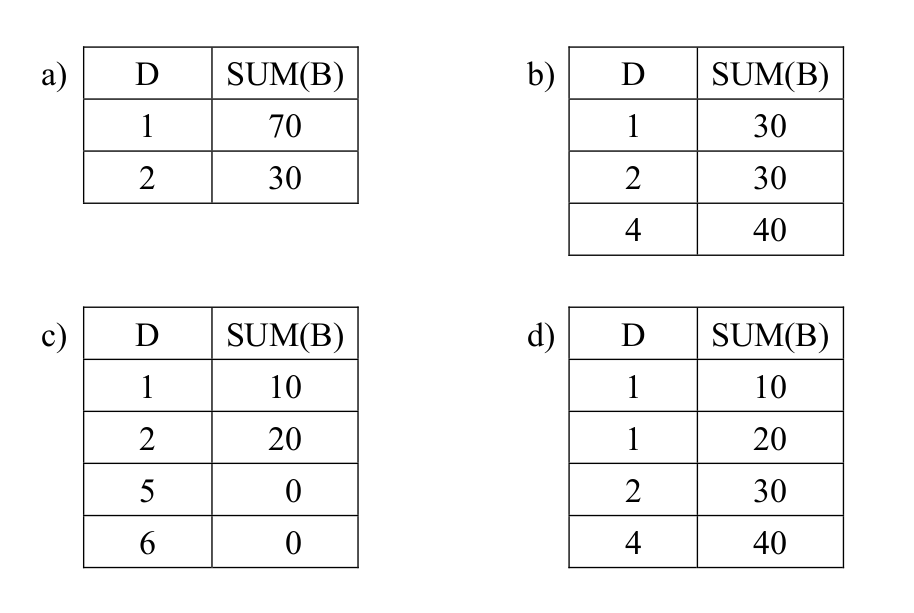","answer_label":"a","answer_id":19834},{"id":4801,"question":"When a program accesses relational database tables by means of embedded SQL statements, which of the following SQL statements is used to define the derived table?","answer_label":"DECLARE CURSOR","answer_id":19839},{"id":4802,"question":"Which of the following is an appropriate description concerning the recovery process of databases?","answer_label":"At the restart known as “warm start,” control goes back to the checkpoint, and the update information log is used for recovering the database.","answer_id":19843},{"id":4803,"question":"Which of the following is an appropriate description concerning the duties of database administrators?","answer_label":"To design and maintain databases, monitor their operations, and recover from failures","answer_id":19848},{"id":4804,"question":"For the purpose of finding out the number of times a Web page is accessed, an access counter is being designed. As shown in the figure, when two browsers gain access to the Web page simultaneously, Processes 1 through 4 are executed in this order on the server. When the access counter value is 100 before the two browsers access the Web page, what is the counter value at the completion of Process 4?\n","answer_label":"101","answer_id":19851},{"id":4805,"question":"In public key cryptography, which of the following key can be used for decrypting the data that is encrypted by using the server’s public key?","answer_label":"Server’s private key","answer_id":19856},{"id":4806,"question":"Which of the following is an appropriate description of phishing?","answer_label":"It is a technique for fooling users into visiting a hostile or untrusted website through spam messages and divulging personal data such as accounting numbers, passwords, and other confidential information.","answer_id":19858},{"id":4807,"question":"In an electronic transaction that employs public key cryptography, which of the following is created by the certification authority (CA), a third party independent of the parties involved in the transaction?","answer_label":"The electronic certificates for the public keys of the parties involved in the transaction","answer_id":19864},{"id":4808,"question":"Which of the following is an appropriate description concerning Internet VPN security?","answer_label":"There is no capability for identifying individual people who are qualified to participate in the network.","answer_id":19868},{"id":4809,"question":"Which of the following is an appropriate description concerning risk analysis?","answer_label":"It takes too much time and cost to handle all potential risks, so the damage costs and occurrence probabilities should be estimated in advance and priority should be given in accordance with the magnitude of risks.","answer_id":19870},{"id":4810,"question":"Which of the following is a meta-language that includes self-defining markup symbols called tags to describe the content of a Web page or file and supports bi-directional hyperlinks with high affinity to the Internet?","answer_label":"XML","answer_id":19877},{"id":4811,"question":"Which of the following is the purpose of emphasizing the importance of stakeholders in corporate management?","answer_label":"Improving satisfaction of interested parties such as customers, shareholders, and employees; aiming for sustainable growth","answer_id":19878},{"id":4812,"question":"When the average cost method is used for the inventory control in the transaction record table shown below, what is the inventory value (in dollars) at the end of March?\n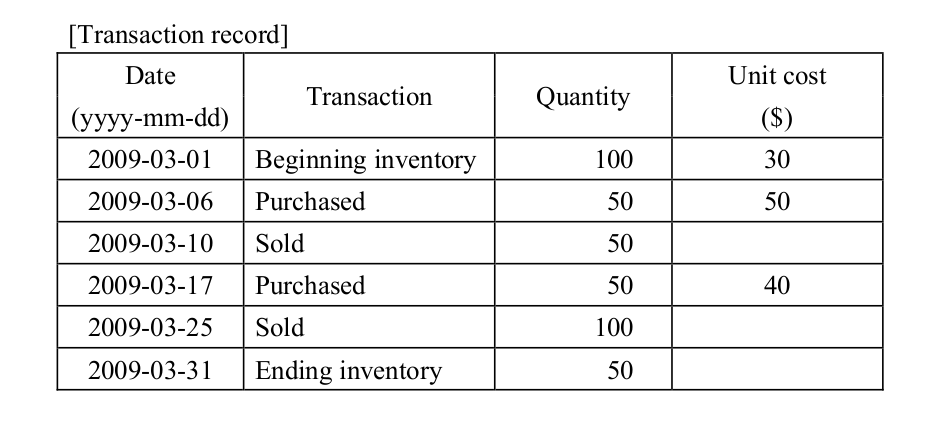","answer_label":"1,875","answer_id":19884},{"id":4813,"question":"As shown below, a shop purchases and sells a certain type of product.\n\nHow many units are sold at a “break even” point, where there is neither a profit nor a loss?","answer_label":"200","answer_id":19888},{"id":4814,"question":"Which of the following is the appropriate relationship between two variables x and y represented by the scatter diagram?\n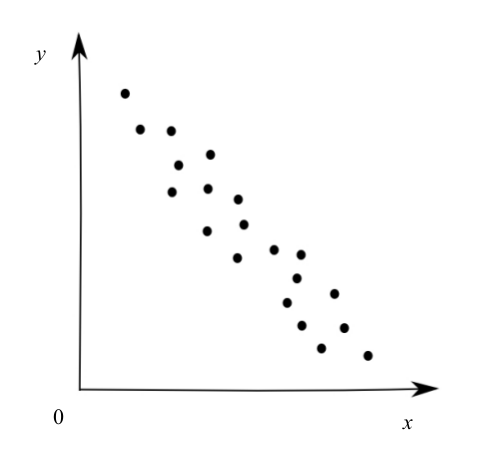","answer_label":"Negative correlation","answer_id":19890},{"id":4815,"question":"Which of the following is the diagram showing results of cluster analysis?\n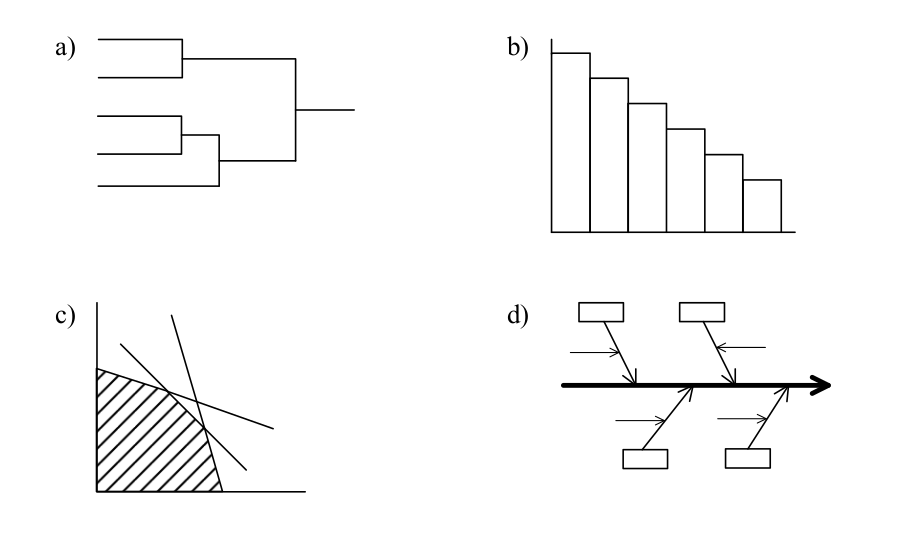","answer_label":"a","answer_id":19894},{"id":4816,"question":"When ABC analysis is done on the products shown in the table below, which of the following is a set of the product numbers that should be handled as management items of Group A?\n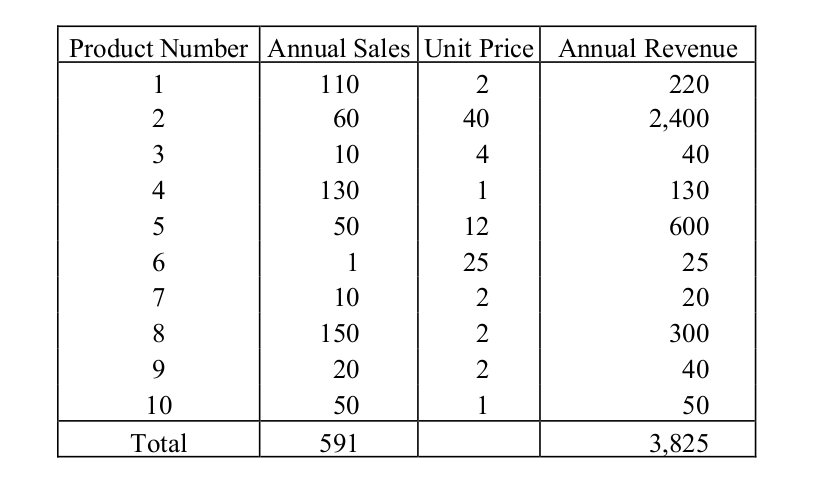","answer_label":"2 and 5","answer_id":19899},{"id":4817,"question":"The figure below is the OC curve (Operating Characteristic curve) that shows the result of a sampling inspection of a certain product lot. Which of the following appropriately describes what this figure indicates?\n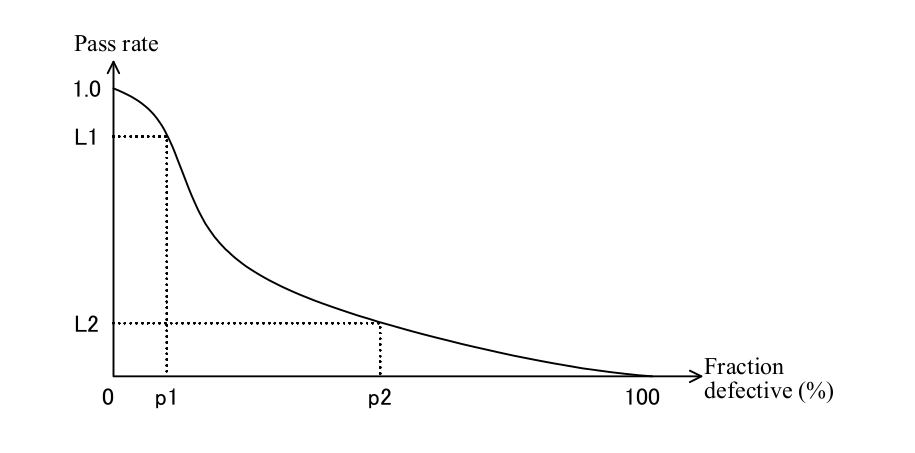","answer_label":"The probability that a lot with a fraction defective greater than p2% passes the inspection is at most L2.","answer_id":19903},{"id":4818,"question":"Which of the following is the explanation of a control chart?","answer_label":"Variation of data occurring in time sequence is expressed by a line graph; it is used to find an abnormal behavior, with an upper limit and a lower limit specified.","answer_id":19909},{"id":4819,"question":"Which of the following is a characteristic of IC tags (RFIDs)?","answer_label":"IC tags are dirt-resistant, and the information recorded on them can be read even from outside the package.","answer_id":19910},{"id":5071,"question":"Which of the following is the result of calculating the arithmetic expression “B6 – 7C”? Here, all numbers are represented in unsigned hexadecimal.","answer_label":"3A","answer_id":20758},{"id":5072,"question":"There are several formats for representing an integer in a computer. When a set of unsigned binary integers that are arranged in ascending order is interpreted in different formats and then sorted again in ascending order of their values, which of the following is the format that maintains the same order as the original unsigned binary integers?","answer_label":"Biased (i.e., offset binary) format","answer_id":20761},{"id":5073,"question":"The distribution of days that are required to complete a certain activity can be approximated by a standard normal distribution with a mean of 500 days and a standard deviation of 12 days. What is the approximate 95% confidence interval in days for the activity?","answer_label":"Between 476 and 524","answer_id":20766},{"id":5074,"question":"There is a series of project activities to be performed by two staff members, Mr. X and Mr. Y. When each of them works alone, it can be completed by Mr. X in 3 hours and by Mr. Y in 6 hours. When Mr. X starts to work at 9:00 a.m. and then Mr. Y starts to work with Mr. X at 10:00 a.m., which of the following is the time at which all the activities are completed? Here, the activities can be divided and performed in parallel by the two members without any loss of productivity.","answer_label":"11:20 a.m.","answer_id":20771},{"id":5075,"question":"The figure below shows the state transition diagram of an automaton. Which of the following is a bit string for which the automaton stops in the accepting (or final) state after the entire bit string has been read? Here, the double circle marked with “q 3 ” represents the accepting state.\n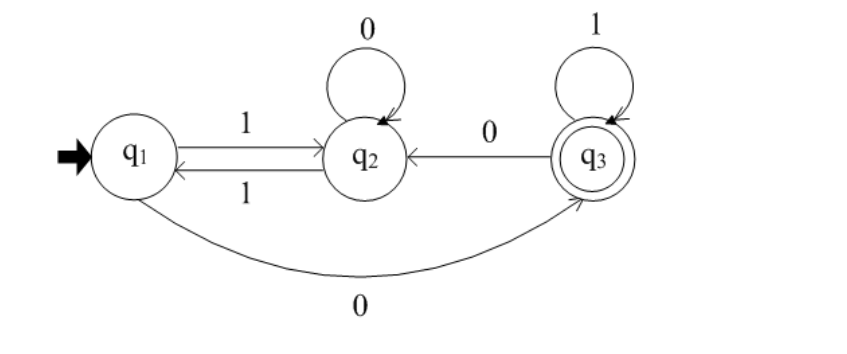","answer_label":"1101","answer_id":20775},{"id":5076,"question":"Which of the following is the logical expression whose resulting value is zero (0) only when the binary values of “x 1 , x 2 , ..., x n ” are all zeros (0s) or all ones (1s)? Here, “·” and “+” represent the logical product and logical sum operators respectively, and “ x ” is the logical negation of “x”.\n","answer_label":"d","answer_id":20780},{"id":5077,"question":"When “11” is inserted in the min-heap shown below, which of the following min-heaps is created? Here, a new node is first placed at the bottom (or last) of the tree, and then it is shifted up to its proper place to maintain the min-heap structure. \n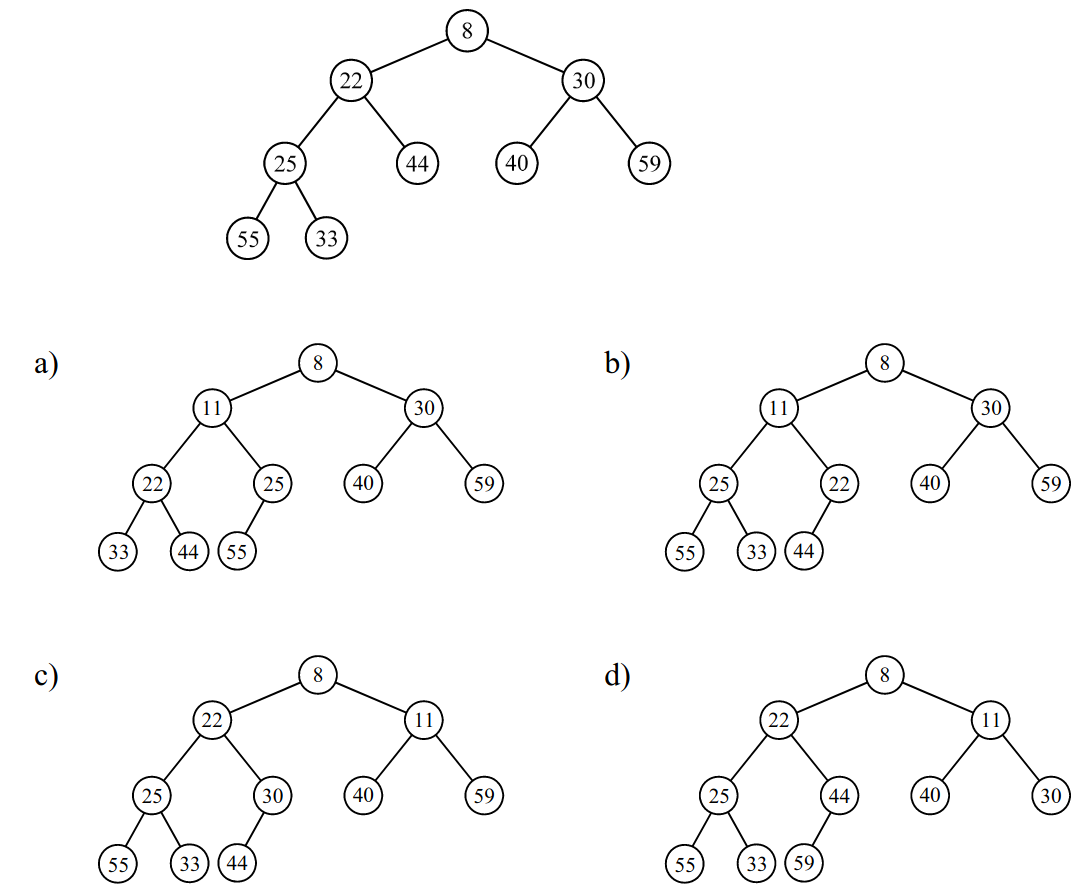","answer_label":"b","answer_id":20782},{"id":5078,"question":"The figure below shows the structure of a singly-linked list. In order to insert Philadelphia between New York and Washington DC, which of the following is an appropriate operation to be performed? Here, “null” indicates the end of the list.\n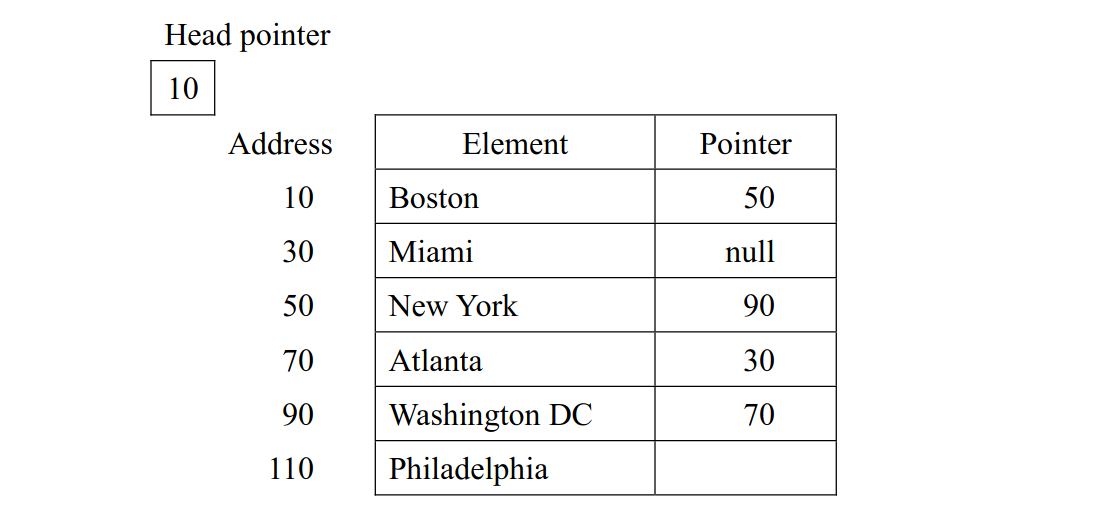","answer_label":"The pointers for New York and Philadelphia are set to 110 and 90 respectively.","answer_id":20788},{"id":5079,"question":"In the binary search tree shown below, which of the following is the appropriate sequence of nodes that are visited in an in-order traversal? \n","answer_label":"D => B => E => A => C => F","answer_id":20791},{"id":5080,"question":"Which of the following is the appropriate description of the “selection sort” algorithm?","answer_label":"The element with the largest value is determined and swapped for the last element, and then the largest value of the unsorted elements is determined and swapped for the second-to-the-last element. This operation is repeated in the same way.","answer_id":20795},{"id":5081,"question":"Which of the following is a role of the program register (i.e., program counter) of the CPU?","answer_label":"In order to read out an instruction, it contains the address where the next instruction is stored.","answer_id":20800},{"id":5082,"question":"When the average instruction execution time of a computer is 20 nanoseconds, what is the performance of this computer in MIPS?","answer_label":"50","answer_id":20804},{"id":5083,"question":"There is a digital video recording system installed with four security cameras. In this system, the video data from each camera is captured at 30 frames per second with a resolution of 640 × 480 pixels and a color depth of 16 bits per pixel, and then it is stored in the hard disk drive. Which of the following is the approximate storage capacity that is required for recording all video data for one minute? Here, 1 MB is 106 bytes, and 1 GB is 109 bytes.","answer_label":"4.5 GB","answer_id":20808},{"id":5084,"question":"Cache memory is usually organized at multiple levels, such as L1 for level 1 and L2 for level 2, with L1 having the smallest storage capacity but the fastest memory speed. The data in L1, L2, and main memory can be accessed using 1, 10, and 100 clock cycles, respectively. When the cache miss rates in L1 and L2 are 5% and 50% respectively, what is the average memory access time in clock cycles?","answer_label":"3.7","answer_id":20810},{"id":5085,"question":"The magnetic head of a hard disk drive is currently positioned at cylinder number 100, and the cylinder numbers 120, 90, 70, 80, 140, 110, and 60 are lined up in the I/O request queue. What is the total number of cylinders that the head moves to satisfy the conditions below? \n[Conditions] \n(1) The seek optimization method is applied to I/O requests, which are sorted in order of increasing cylinder number so that the head can move in the same direction to the extent possible. \n(2) The head is currently moving in the direction where cylinder number increases. \n(3) When there are no more I/O requests in the current direction, the direction of movement is reversed. \n(4) The results are not affected by the processing order of I/O requests. \n(5) New I/O requests do not occur during the process.","answer_label":"120","answer_id":20814},{"id":5086,"question":"Which of the following is the most appropriate explanation of cloud computing?","answer_label":"It provides the resources of a computer via a network so that the user can easily receive services with high scalability and availability.","answer_id":20820},{"id":5087,"question":"Which of the following is an essential activity for achieving a fault tolerant system?","answer_label":"Providing redundancy for a system configuration to minimize the effect of a component failure so that the processing can be continued without any effect on the overall system","answer_id":20823},{"id":5088,"question":"In reliability design, which of the following is an appropriate example of fail-soft?","answer_label":"In a system with a cluster configuration, even when a server does not work, another server takes over applications and provides functions.","answer_id":20825},{"id":5089,"question":"Which of the following is an appropriate description concerning MTBF and MTTR?","answer_label":"MTBF increases through the preventive maintenance of a system.","answer_id":20830},{"id":5090,"question":"The diagram below shows the state transition of the tasks in a multitasking computer system. When does a task in the running state move to the ready state?\n","answer_label":"When a task with a higher priority is set to the ready state","answer_id":20835},{"id":5091,"question":"In memory pool management of a real time system using various sizes of memory resources, which of the following is an appropriate characteristic of the fixed-length method in comparison with the variable-length method?","answer_label":"The memory efficiency is poor, and the processing speed for allocation and deallocation is fast and constant.","answer_id":20839},{"id":5092,"question":"When CPU processing and printing are performed for four jobs under the conditions below, how many minutes does it take to complete them from the start of the first CPU processing until the end of the last printing? \n[Conditions] \n(1) The multiplicity of jobs is 1 during execution. \n(2) The CPU processing time of each job is 20 minutes. \n(3) 400Mbytes of printing data are spooled for each job when the CPU processing ends. The printing function of the OS operates after spooling is completed, and printing is performed by the printer. \n(4) One printer is available, and the printing speed is 10 minutes per 100Mbytes. \n(5) The functions of CPU processing and printing can operate in parallel, and do not affect each other. \n(6) The time period that is not mentioned in the conditions, such as the time required for spooling, can be ignored.","answer_label":"180","answer_id":20843},{"id":5093,"question":"When the number of concurrently running programs is increased in a virtual storage system with the small and insufficient capacity of main memory, which of the following is the state in which the overhead of the system increases and the processor utilization of the applications decreases?","answer_label":"Thrashing","answer_id":20848},{"id":5094,"question":"Which of the following is the language processor that translates and executes a source program written in high-level language, on a line-by-line basis?","answer_label":"Interpreter","answer_id":20852},{"id":5095,"question":"For the purpose of monitoring the execution process of a program in order of time, which of the following is used as a dynamic debugging tool that records the contents of the memory and registers as well as the execution sequence of program instructions?","answer_label":"Tracer","answer_id":20856},{"id":5096,"question":"Which of the following is an appropriate explanation of DRAM?","answer_label":"It is often used as main memory, and one bit is represented depending on whether or not its capacitor is charged.","answer_id":20858},{"id":5097,"question":"The figure below shows a logic circuit representing a full adder. When 1, 0, and 1 are entered into x, y, and z respectively, which of the following is the appropriate combination of the output values of c (carry) and s (sum)? \n","answer_label":"c = 1; s = 0","answer_id":20863},{"id":5098,"question":"Which of the following is the logic gate that is equivalent to the logic circuit shown below?\n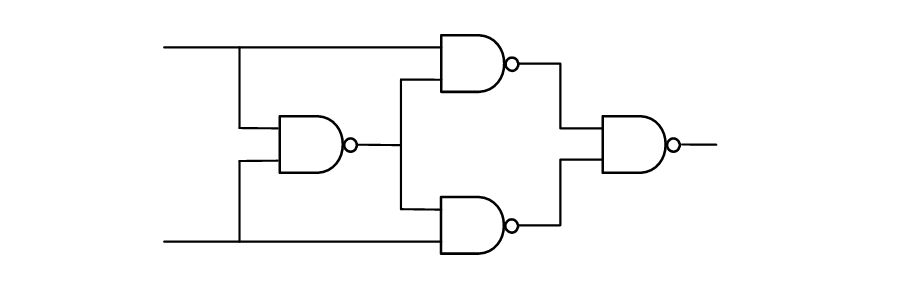","answer_label":"XOR","answer_id":20868},{"id":5099,"question":"When a 60-minute monaural audio signal is digitalized using a PCM format with a sampling frequency of 44.1 kHz and a quantization bit rate of 16 bits, what is the approximate data volume in Mbytes? Here, the data is not compressed.","answer_label":"320","answer_id":20871},{"id":5100,"question":"Among the descriptions concerning three-dimensional computer graphics, which of the following is an explanation of polygon?","answer_label":"It is a basic element that is used for constituting a polyhedron taking the form of a closed solid or for approximating a quadric surface or a free-form surface.","answer_id":20873},{"id":5101,"question":"As shown in the class diagram below, there is a many-to-many association between the two classes Product and Warehouse. When there is a need to know how many of each product are stored in each warehouse, the association class StockHolding can be added between the two classes Product and Warehouse so as not to hide the original many-to-many relationship.\n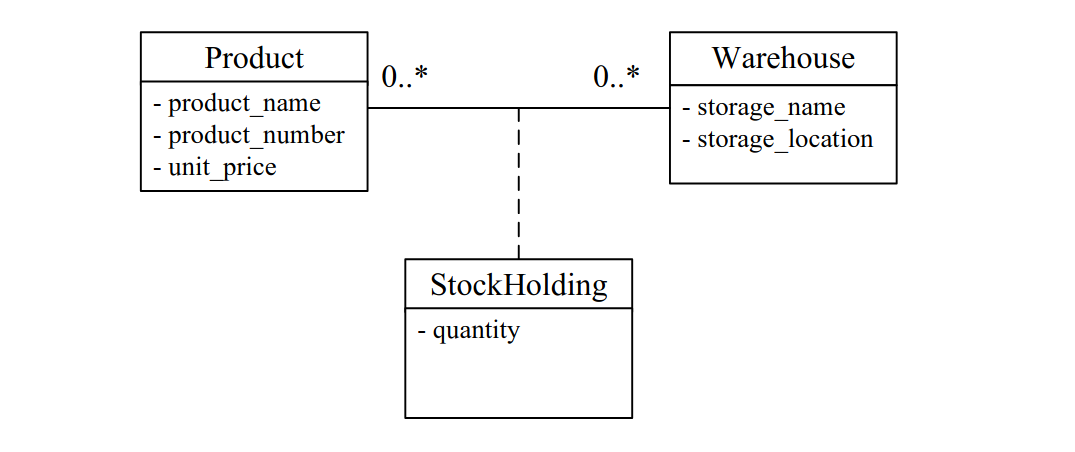\nIf the class diagram shown below is depicted using a full class instead of the association class, which of the following is the appropriate combination of cardinalities that are inserted into blanks A through D?\n","answer_label":"c","answer_id":20879},{"id":5102,"question":"As shown below, when the SQL statement is executed on the relational database table “Staff”, which of the following tables is created?\n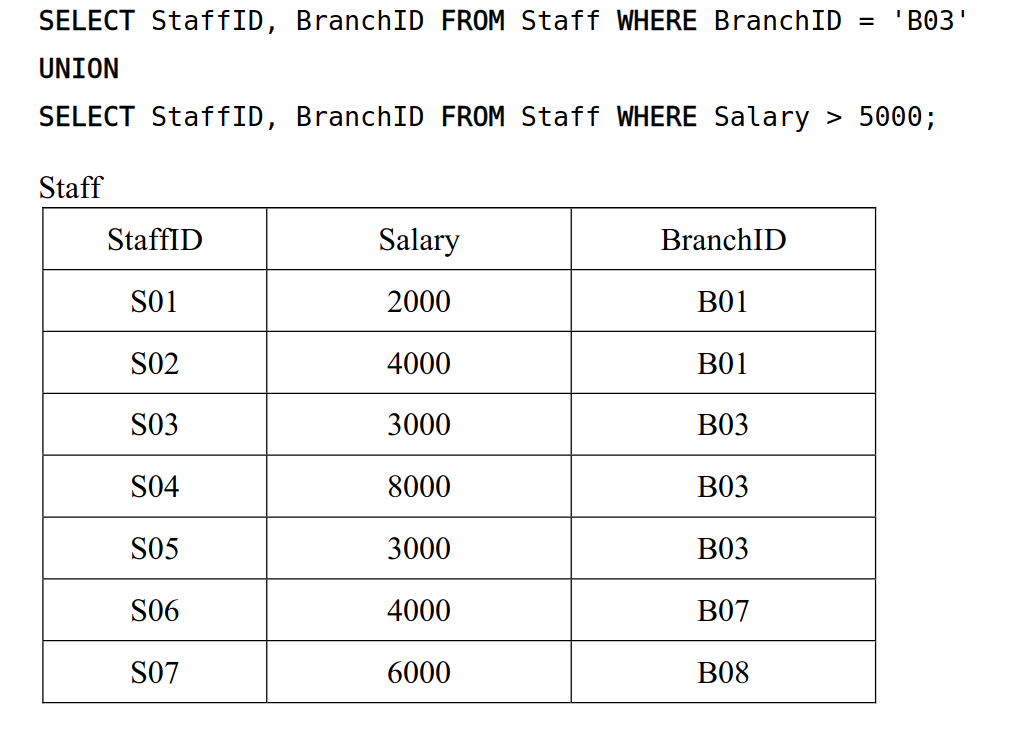\n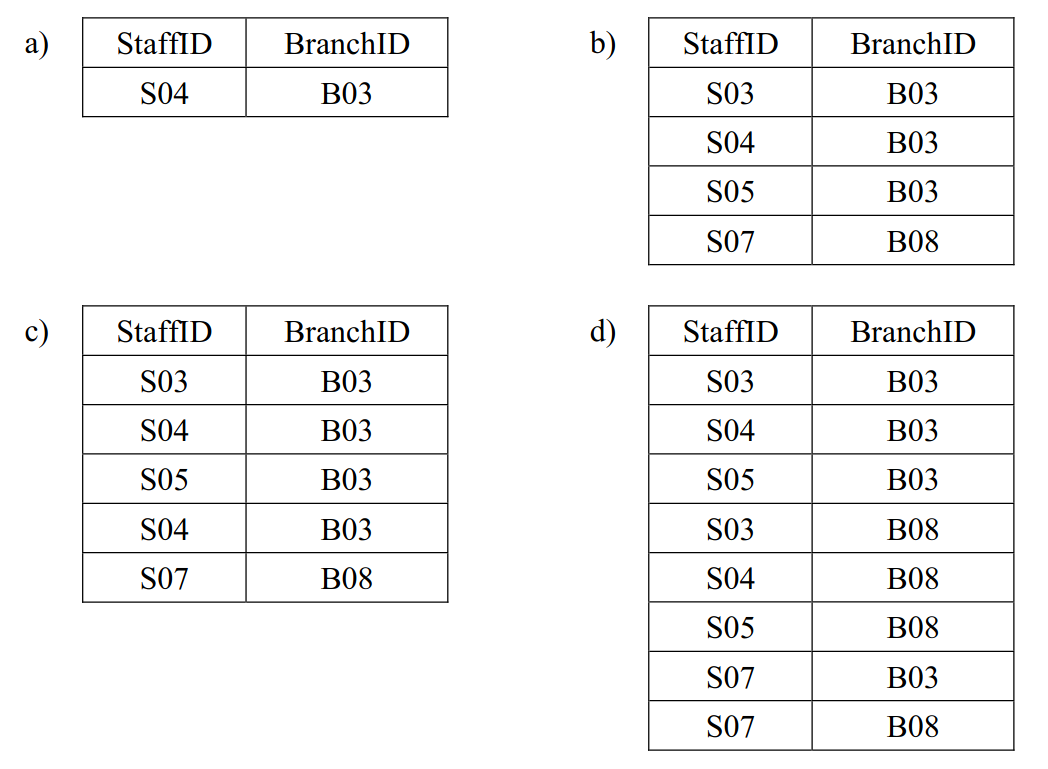","answer_label":"b","answer_id":20882},{"id":5103,"question":"Which of the following is the appropriate flow of execution of SQL statements?","answer_label":"Decomposition => Optimization => Code generation => Execution","answer_id":20887},{"id":5104,"question":"In a relational database system, which of the following is an appropriate purpose of recording changes in a database file as a journal file?","answer_label":"To enable recovery to be undertaken effectively in the event of a failure","answer_id":20890},{"id":5105,"question":"Which of the following is the most appropriate description concerning the exclusive control of a DBMS?","answer_label":"Exclusive control is necessary for data that might be updated simultaneously by several people.","answer_id":20893},{"id":5106,"question":"When an optical fiber cable is used for data communication, which of the following is the approximate bandwidth (in units of THz) of the light within the range of wavelength from 1000 to 1400 nanometers? Here, in consideration of data transmission efficiency and such other factors, the effective speed of the light on the optical fiber cable can be assumed to be 2 ×10^8 m/s.","answer_label":"57","answer_id":20898},{"id":5107,"question":"Which of the following is an appropriate description concerning interconnection devices between LANs?","answer_label":"The repeater extends the transmission distance by amplifying signals between the same types of segments.","answer_id":20903},{"id":5108,"question":"Among the layers of the OSI basic reference model, which of the following is the appropriate layer that is primarily responsible for the translation, encryption, and compression of data?","answer_label":"Presentation layer","answer_id":20907},{"id":5109,"question":"In a TCP/IP network using IPv4 addresses, which of the following is an effective IP address that can be allocated to a network device?","answer_label":"203.164.15.9/28","answer_id":20911},{"id":5110,"question":"Which of the following is an appropriate explanation of POP3 that is used in an e-mail system?","answer_label":"It is a protocol used to retrieve e-mails from the mailbox of a mail server.","answer_id":20916},{"id":5111,"question":"A PKI involves two types of key pairs: signature key pairs, in which the private key is used for signing and the public key for checking; and exchange key pairs, in which the public key is used by an application to encrypt data, and the private key is used to decrypt the encrypted data. Which of the following is the key pair(s) that may be escrowed or backed up to prevent the loss of important data even when the corresponding key or keys are forgotten?","answer_label":"Exchange key pair","answer_id":20919},{"id":5112,"question":"Which of the following can be achieved by receiving an e-mail text and its hash value from the sender, and then comparing this hash value with another hash value calculated by the recipient from the e-mail text? Here, the hash value that the recipient receives from the sender is correct.","answer_label":"Detecting the presence or absence of falsification in the e-mail text","answer_id":20922},{"id":5113,"question":"Which of the following is a security measure where it is effective to confirm the destination address with the sender when an e-mail is sent?","answer_label":"A preventive measure against wrong transmission of e-mail","answer_id":20926},{"id":5114,"question":"Which of the following is the purpose of using a WAF (Web Application Firewall)?","answer_label":"To block attacks to a vulnerability arising from a Web server and an application","answer_id":20929},{"id":5115,"question":"As a security measure on the Internet, a type of challenge-response test called a CAPTCHA can be used to determine whether the client is a human or a computer program. Which of the following is an appropriate purpose of using such a measure?","answer_label":"To protect against automated spamming","answer_id":20935},{"id":5116,"question":"Which of the following is an appropriate description concerning a use case diagram in UML?","answer_label":"It is used to show what system functions are performed for which actor, from the user’s perspective.","answer_id":20940},{"id":5117,"question":"During system development, a domain model is often created as part of the business modeling activities. Among the diagrams in UML, which of the following is the diagram that contains the implementation view of the entities in the domain model?","answer_label":"Class diagram","answer_id":20941},{"id":5118,"question":"In UML, the state machine diagram (previously called statechart diagram) is used for describing the state machine model of a target system. Which of the following is an appropriate description of the state machine diagram?","answer_label":"It shows how the system responds to internal and external events.","answer_id":20946},{"id":5119,"question":"In the course of object oriented design, which of the following can be regarded as a subclass of the base class “automobile”?","answer_label":"Truck","answer_id":20952},{"id":5120,"question":"The integration test for software that is composed of a set of modules arranged in a hierarchical structure is performed from a high-level module. In such a case, which of the following is a test module that is used as a substitute for the low-level module?","answer_label":"Stub","answer_id":20956},{"id":5121,"question":"When the data model conforms to the notation described below, which of the following is an appropriate description concerning the interpretation of the E-R diagram shown below?\n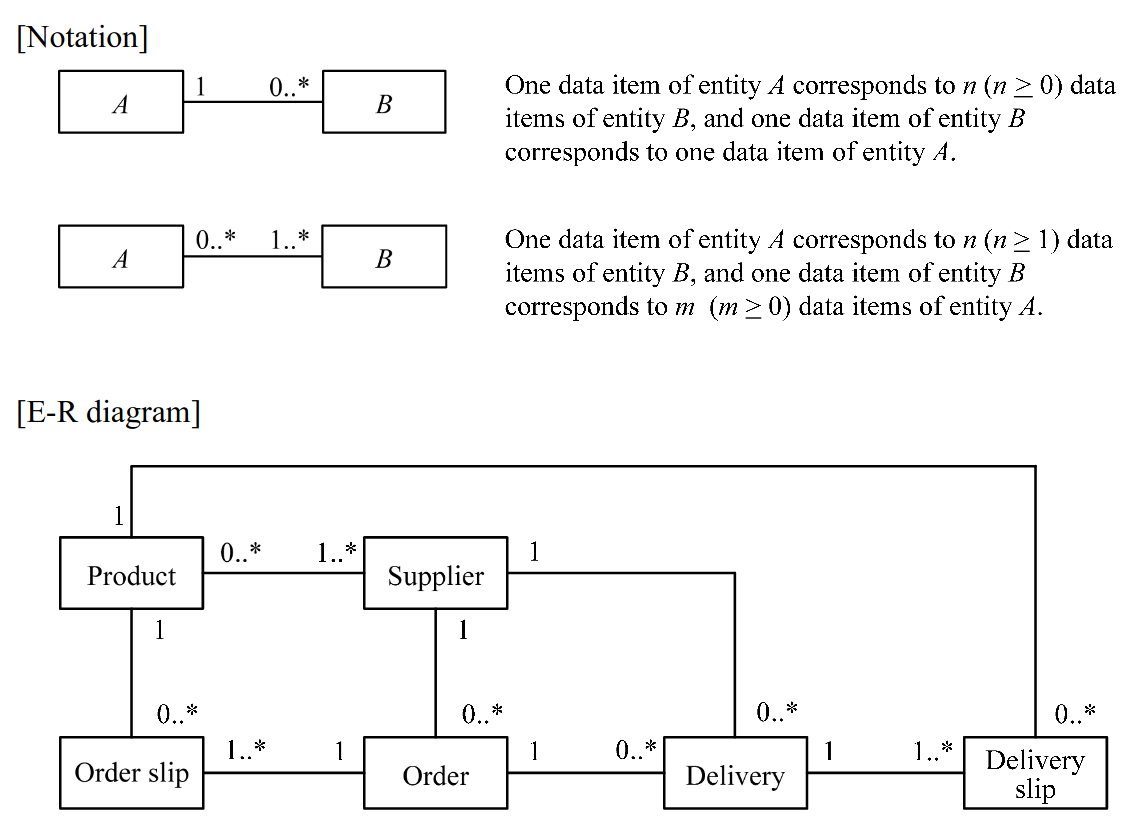","answer_label":"A single order is not made from multiple suppliers.","answer_id":20957},{"id":5122,"question":"Which of the following is the software development process model that aims to achieve a high degree of completion of a system by dividing the system into some subsystems and repeating the development cycle for each subsystem in consideration of minimizing the risk in each cycle?","answer_label":"Spiral model","answer_id":20963},{"id":5123,"question":"Which of the following is the most appropriate description concerning maintenance management that is to be planned for the development environment of an embedded system used during the development of a product?","answer_label":"It is necessary to maintain the development environment such as through periodic operational checks regardless of usage frequency.","answer_id":20967},{"id":5124,"question":"The arrow diagram shown below is created for time management of a project. Which of the following is the critical path?\n","answer_label":"B→E→F","answer_id":20971},{"id":5125,"question":"What is the function point value of a program that has the functions and characteristics shown in the table below? Here, the correction coefficient of complexity is 0.75.\n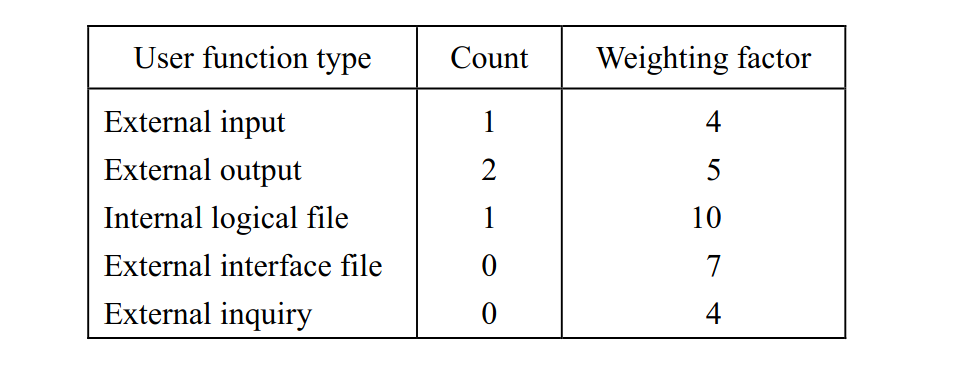","answer_label":"18","answer_id":20973},{"id":5126,"question":"Which of the following is a chart or a diagram that is often used in quality control to rank issues or problems in descending order of frequency?","answer_label":"Pareto chart","answer_id":20979},{"id":5127,"question":"Which of the following is the most appropriate indicator that is directly helpful in managing software quality in a system development project?","answer_label":"Period of time required to adequately review each deliverable","answer_id":20982},{"id":5128,"question":"According to the ISO/IEC 20000 series, which of the following has the objective that aims to minimize disruption to the business by proactive identification and analysis of the cause of incidents and by managing problems to closure?","answer_label":"Problem management","answer_id":20988},{"id":5129,"question":"Which of the following is a service delivery process that is defined, agreed, recorded, and managed in IT service management?","answer_label":"Service level management","answer_id":20992},{"id":5130,"question":"When there are several business systems available in a company, which of the following is the most appropriate method for access control?","answer_label":"Irrespective of the user’s job title, the appropriate access rights are set in each business system on the basis of the user’s job role.","answer_id":20995},{"id":5131,"question":"Whenan audit is performed on the reliability of programming, which of the following is the most appropriate item to be reported as a finding?","answer_label":"The programmer selects a subset of unit test items from all the program logic paths on a sampling basis.","answer_id":20999},{"id":5132,"question":"When a department that outsources system development must undergo a system audit concerning “progress management” of the outsourcing partner, which of the following is an appropriate set of materials that should be submitted?","answer_label":"Business reports received periodically from the outsourcing partner, and documents showing the verification result of the business reports","answer_id":21001},{"id":5133,"question":"In a system audit, which of the following acts as audit evidence?","answer_label":"System operation records obtained by the audit team from the audited department","answer_id":21008},{"id":5134,"question":"When an information strategy is developed, which of the following is an item that must always be made consistent with the strategy?","answer_label":"Medium and long-term management plans","answer_id":21009},{"id":5135,"question":"Which of the following is an improvement index in supply chain management?","answer_label":"Ratio of reduction in dead stock","answer_id":21015},{"id":5136,"question":"Which of the following is provided by an ASP (Application Service Provider)?","answer_label":"A service in which the functions of a general-purpose application system are provided to several customers via a network","answer_id":21020},{"id":5137,"question":"When an information system is procured according to the procedure shown in the figure below, which of the following is to be inserted into blank B?\n","answer_label":"RFP","answer_id":21023},{"id":5138,"question":"Which of the following is an explanation of core competence management?","answer_label":"Management is centered on proprietary know-how and technology that are not easy for other companies to imitate.","answer_id":21028},{"id":5139,"question":"In the product life cycle, which of the following is the stage where the market begins to understand the value of the product, and both product lines and sales channels need to be expanded?","answer_label":"Maturity stage","answer_id":21032},{"id":5140,"question":"A SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis is a technique that is used to identify and evaluate the internal and external factors that are helpful or harmful to achieving the objectives of business organizations or projects. Which of the following is the appropriate matrix that shows a combination of those factors?\n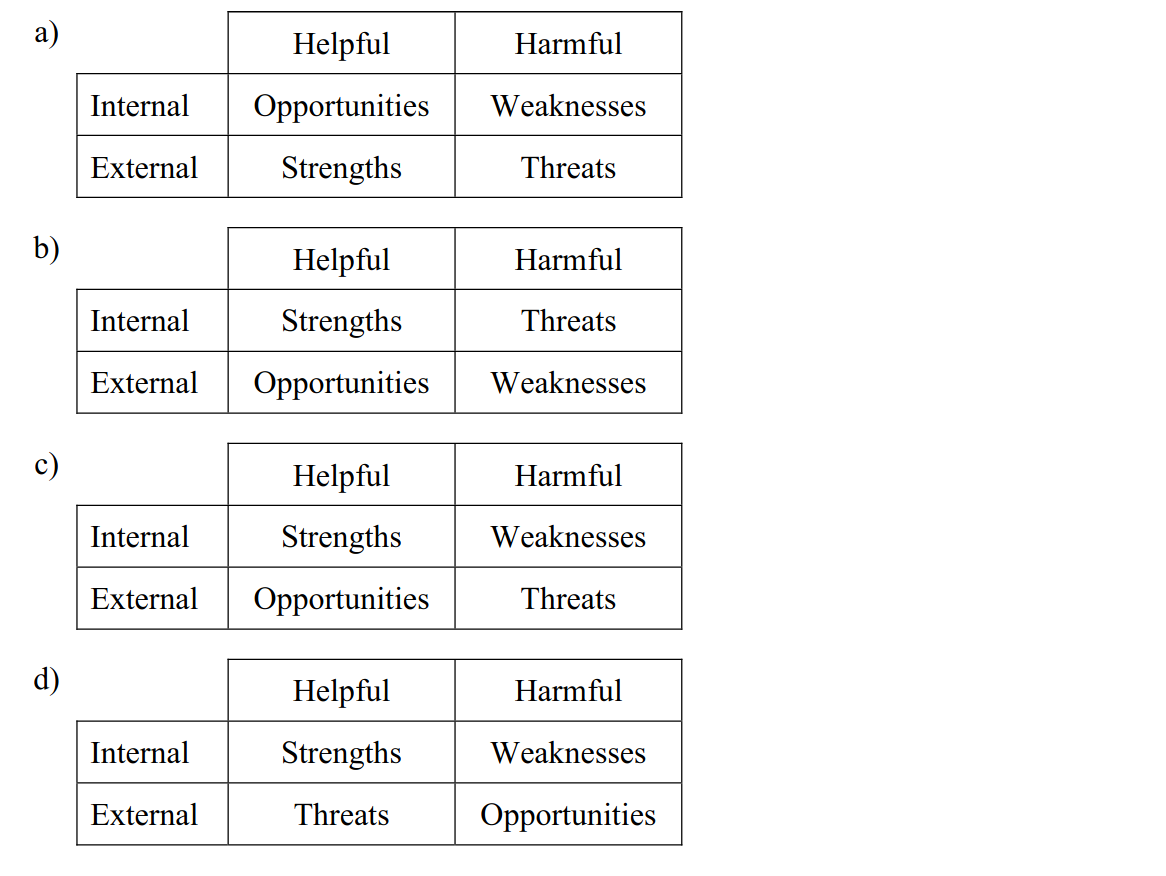","answer_label":"c","answer_id":21035},{"id":5141,"question":"Which of the following is an appropriate form of transaction where one company (i.e., the bidder) gains a decisive share of the basic equity of another target business?","answer_label":"Acquisition","answer_id":21037},{"id":5142,"question":"Product Portfolio Management (PPM) is a method for analyzing the positioning of a product within the market and reviewing the resource allocation. As shown below, PPM uses a matrix chart divided into four quadrants, with the market growth rate on the vertical axis, and the market share on the horizontal axis. Which of the following is the appropriate quadrant in which a product referred to as “cash cow” is categorized? \n","answer_label":"C","answer_id":21043},{"id":5143,"question":"Which of the following is an appropriate explanation of direct telemarketing?","answer_label":"A type of direct marketing that involves not only selling products on the phone but also asking for donations or opinions","answer_id":21045},{"id":5144,"question":"Which of the following is an appropriate example of the effective utilization of RFID?","answer_label":"Identification and control of humans or objects by using a small wireless chip","answer_id":21049},{"id":5145,"question":"Which of the following is an appropriate explanation of IR (Investor Relations)?","answer_label":"It is a business process of providing investors and analysts with accurate management information necessary for making investment decisions, on a timely and continuous basis.","answer_id":21056},{"id":5146,"question":"Which of the following is an explanation of a CIO?","answer_label":"An executive who is positioned to plan and execute strategies including information management and information system control","answer_id":21058},{"id":5147,"question":"Which of the following is a technique by which useful information and relationships are discovered and extracted from large amounts of customer and market data retained by a company?","answer_label":"Data mining","answer_id":21063},{"id":5148,"question":"Which of the following is a qualitative and exploratory forecasting approach that is used for obtaining the most reliable consensus of opinions from a group of experts through a series of questionnaires?","answer_label":"Delphi method","answer_id":21066},{"id":5149,"question":"The table below shows the transaction records for a certain fiscal period. When the average cost is calculated based on the periodic average method, how much is the “cost of sales” in dollars at the end of the period?\n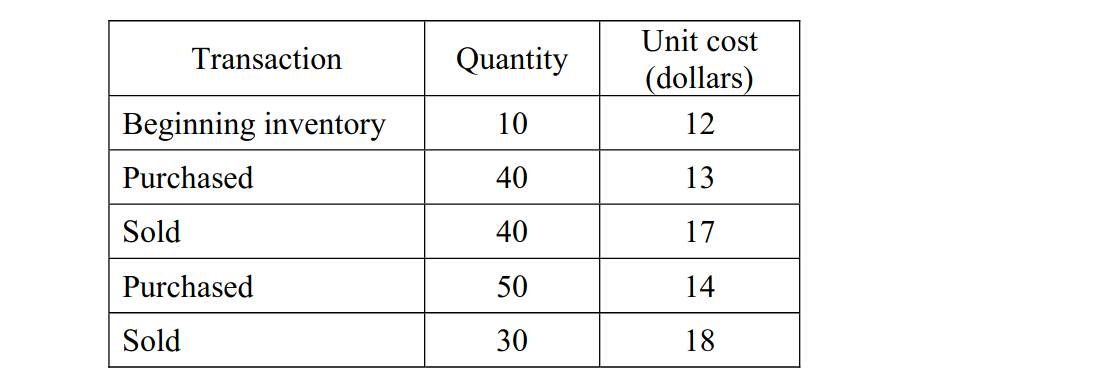","answer_label":"938","answer_id":21070},{"id":5150,"question":"The figure below shows each break-even point of Company A and Company B. Which of the following is an appropriate description concerning the benefit-risk analysis of the two companies?\n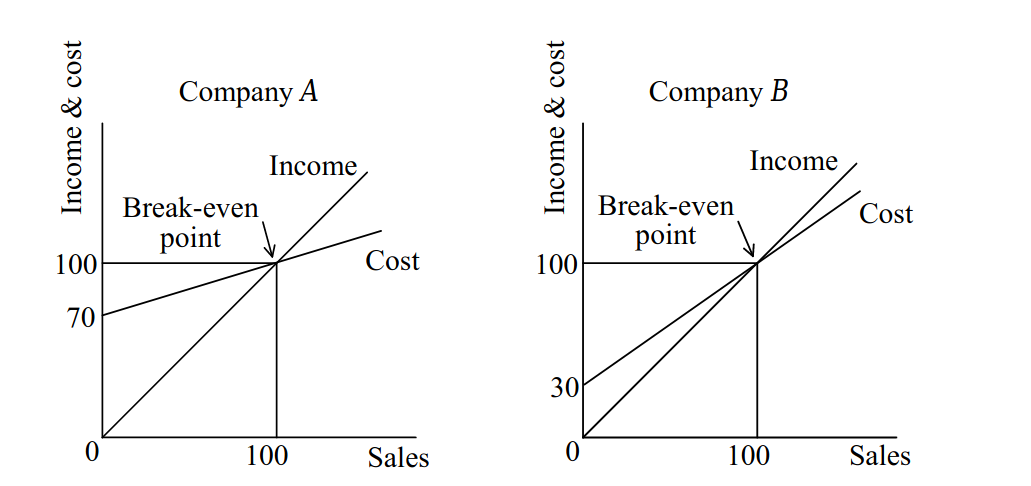","answer_label":"The variable cost ratio of Company A is lower than Company B, and therefore, when the sales above the break-even point are equal, the profit of Company A is higher than Company B.","answer_id":21075},{"id":5151,"question":"Which of the following is the binary fraction that is equivalent to the decimal fraction 115.625?","answer_label":"1110011.101","answer_id":21080},{"id":5152,"question":"Which of the following is equivalent to the logical expression below? Here, “AND” has higher precedence than “OR”, and “NOT” has the highest precedence. \n","answer_label":"a","answer_id":21081},{"id":5153,"question":"How many multiplications at a minimum must be performed in order to calculate the polynomial expression “x^4–2x^3+5x^2+x–6”?","answer_label":"3","answer_id":21086},{"id":5154,"question":"How many binary numbers can be represented using a 6-bit number that does not have two contiguous 1s? For example, “101010” does not have two contiguous 1s.","answer_label":"21","answer_id":21091},{"id":5155,"question":"When the expression 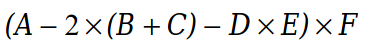 in conventional infix notation is converted to the prefix expression, which of the following represents the resulting expression? \n","answer_label":"d","answer_id":21096},{"id":5156,"question":"When the figure below shows the process flow of a compiler that is used for procedural languages, which of the following is the appropriate combination that should be inserted into blanks A though C?\n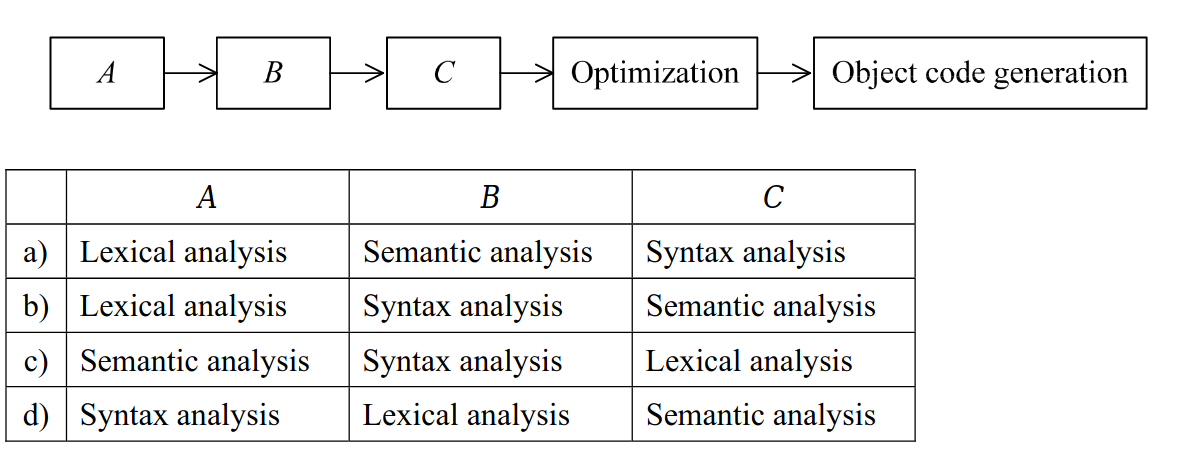","answer_label":"b","answer_id":21098},{"id":5157,"question":"Which of the following is an appropriate description concerning a max heap whose node values are 3, 6, 11, 17, 19, 22, and 32?","answer_label":"The root node value is always “32”.","answer_id":21103},{"id":5158,"question":"Which of the following is an appropriate technique that is used for implementing a queue as a data structure?","answer_label":"FIFO","answer_id":21105},{"id":5159,"question":"Bubble sort is implemented using a technique that repeatedly compares adjacent pairs of elements from left to right and swaps them if they are in the wrong order. Which of the following is the total number of comparisons for sorting a list of “n” elements?\n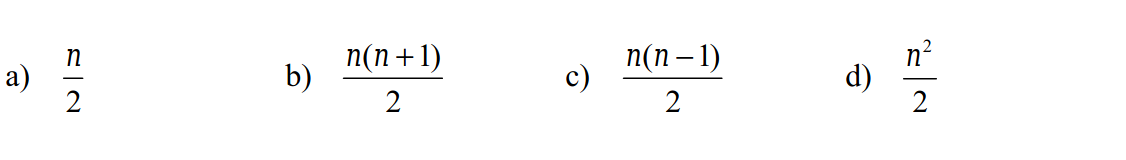","answer_label":"c","answer_id":21111},{"id":5160,"question":"The flowchart below shows an algorithm that can be used to sort all elements of one-dimensional array X in reverse order and store them in array Y. In order to complete the algorithm, which of the following should be inserted into blanks A and B? Here, the indices of the first and last elements of each array are 1 and n respectively.\n","answer_label":"b","answer_id":21114},{"id":5165,"question":"Which of the following is an example of a daisy chain connection?","answer_label":"Industrial cameras with each having two IEEE 1394 ports are serially connected, and then one end is connected to a PC.","answer_id":21135},{"id":5166,"question":"When analog audio signals are converted into digital audio signals using the PCM method at a sampling rate of 44.1 kHz, which of the following determines the amount of the encoded digital data.","answer_label":"The quantization bit width of the audio data","answer_id":21140},{"id":5167,"question":"Which of the following is the appropriate RAID configuration that provides byte-level striping in combination with parity information and stores the parity for each stripe in a dedicated disk?","answer_label":"RAID3","answer_id":21143},{"id":5168,"question":"Which of the following is the configuration of distributed system where hierarchical or dependency relations exist between processors as with relationships between clients and servers?","answer_label":"Vertical function distribution","answer_id":21147},{"id":5169,"question":"Which of the following is a framework or methodology of dividing the resources of a computer into multiple execution environments, by applying one or more concepts or technologies such as hardware and software partitioning, time-sharing, partial or complete machine simulation, emulation, quality of service, and many others?","answer_label":"Virtualization","answer_id":21152},{"id":5170,"question":"A system fails and recovers repeatedly over time, as shown in the figure below. Which of the following is the appropriate combination of the indicators or indexes that represent reliability and availability in RASIS?\n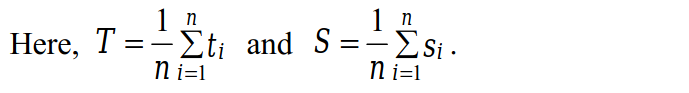\n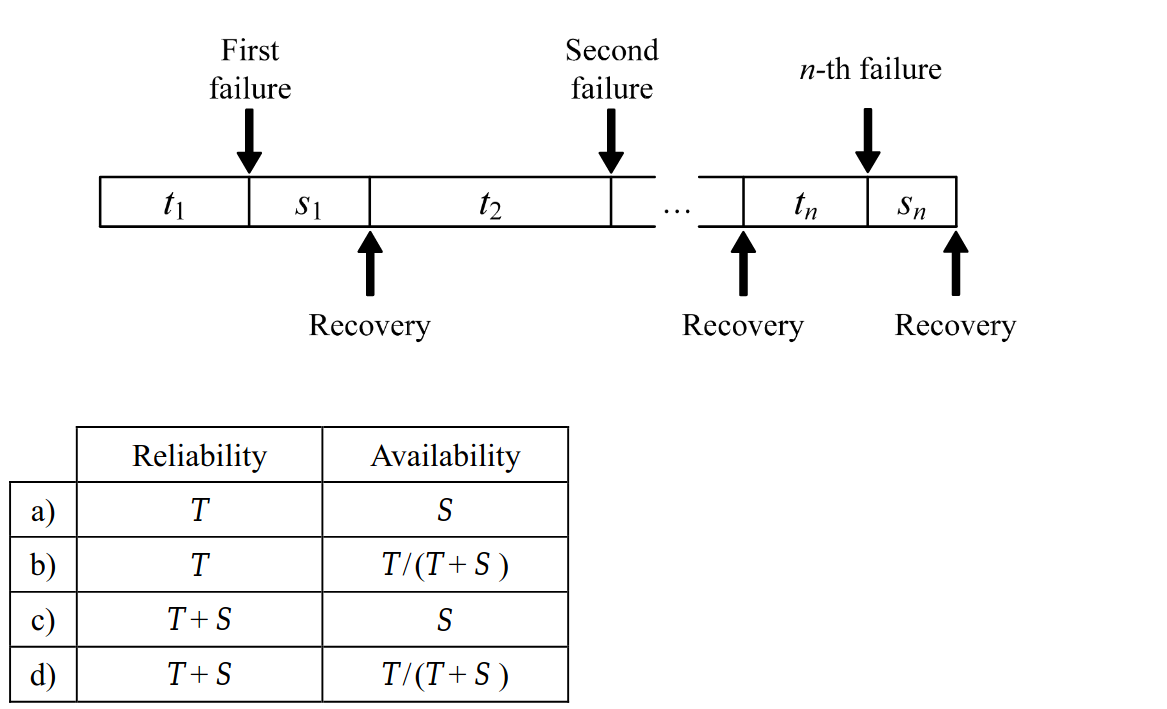","answer_label":"b","answer_id":21154},{"id":5171,"question":"Which of the following provides a job management function in OS that selects a program with the highest execution priority in the job queue and allocates resources required for the program?","answer_label":"Initiator","answer_id":21157},{"id":5172,"question":"In a certain processor, a timer interrupt is generated at a clock frequency of 60 Hz on a “per clock tick” basis. It takes 2 milliseconds (including process switching overhead) to handle the interrupt. What is the percentage of the interrupt handling time in the processor?","answer_label":"12","answer_id":21162},{"id":5173,"question":"In a preemptive multitasking OS environment, when a process is preempted by another process with a higher priority, which of the following is the appropriate state where the former process is to be placed?","answer_label":"Ready","answer_id":21165},{"id":5174,"question":"When four jobs A through D shown in the table below are executed on a first-come first-served basis, which of the following is the average waiting time (in minutes) in the job queue? Here, the job queue is empty before job A arrives.\n","answer_label":"2.5","answer_id":21169},{"id":5175,"question":"CPU utilization of a computer system can be improved by using multiprogramming. If there is one process in memory, the CPU utilization is (1 –p). Here, “p” is the fraction of time (e.g., I/O time) that a process spends away from the CPU. If there are “n” processes in memory, the probability of “n” processes waiting for an I/O is p*p...*p (n times). The CPU utilization is equal to (1 – p^n). When the system has enough main memory space to hold four processes and each process waits for I/O completion during 50% of the execution time, which of the following is the percentage of the CPU time wasted by waiting for I/O completion?","answer_label":"6.25","answer_id":21173},{"id":5176,"question":"In a logic circuit shown below, which of the following is an appropriate combination of input signals A through C that can generate the output signal “0”?\n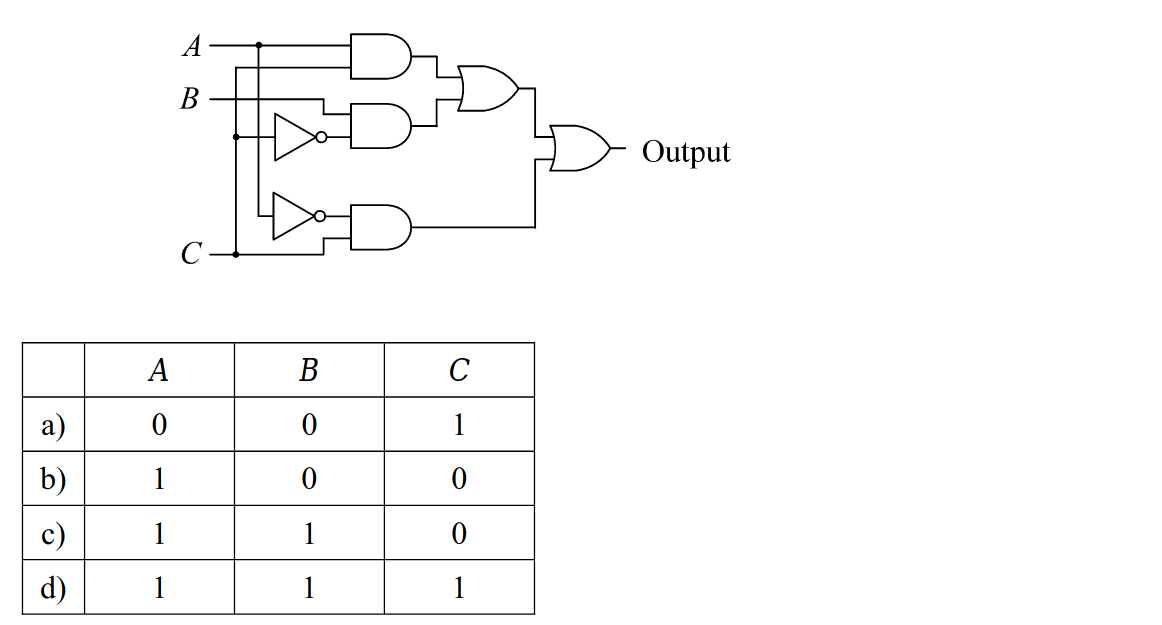","answer_label":"b","answer_id":21178},{"id":5177,"question":"The figure shown below represents a logic gate and its timing chart. Which of the following is an appropriate logical function of this gate? Here, both A and B are the input signals, and F is the output signal.\n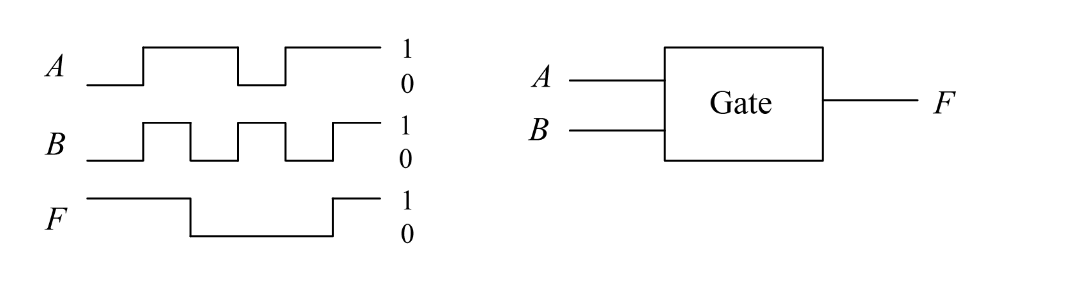","answer_label":"Exclusive-NOR","answer_id":21182},{"id":5178,"question":"Which of the following is the name of a phenomenon where multiple ON/OFF signals are generated during a few milliseconds after a push-button switch with a mechanical contact is pressed once?","answer_label":"Chattering","answer_id":21186},{"id":5179,"question":"Which of the following is the specification for dividing frequently-used functions of a Java program into reusable components that can be deployed in a network on any major operating system platform?","answer_label":"JavaBeans","answer_id":21191},{"id":5180,"question":"According to ISO 9241-11, usability is defined as the “extent to which a product can be used by specified users to achieve specified goals with effectiveness, efficiency, and satisfaction in a specified context of use.” Which of the following is an appropriate method for evaluating the “level of user satisfaction” mentioned in this definition?","answer_label":"Interview method","answer_id":21195},{"id":5181,"question":"Which of the following is an appropriate example of VR (Virtual Reality)?","answer_label":"Computer games and simulations make use of multimodal devices, such as a wired glove, a headgear, and an omni-directional treadmill, in order to provide very enriching and life-like experience for the user.","answer_id":21198},{"id":5182,"question":"A publishing company produces textbooks for high school. Each book is written by an author who specializes in a subject. An editor is assigned to work with an author for a book. An editor can review several books while an author can write several books on the same subject. There are several authors on the same subject and several editors to choose from. The E-R diagram below shows the relationships between subject, author, book, and editor, but the relations between author and book and between author and editor are incomplete. Which of the following is the appropriate combination of relations that are applied to complete the E-R diagram? Here, 1______* indicates a one-to-many relation, *______* is a many-to-many relation.\n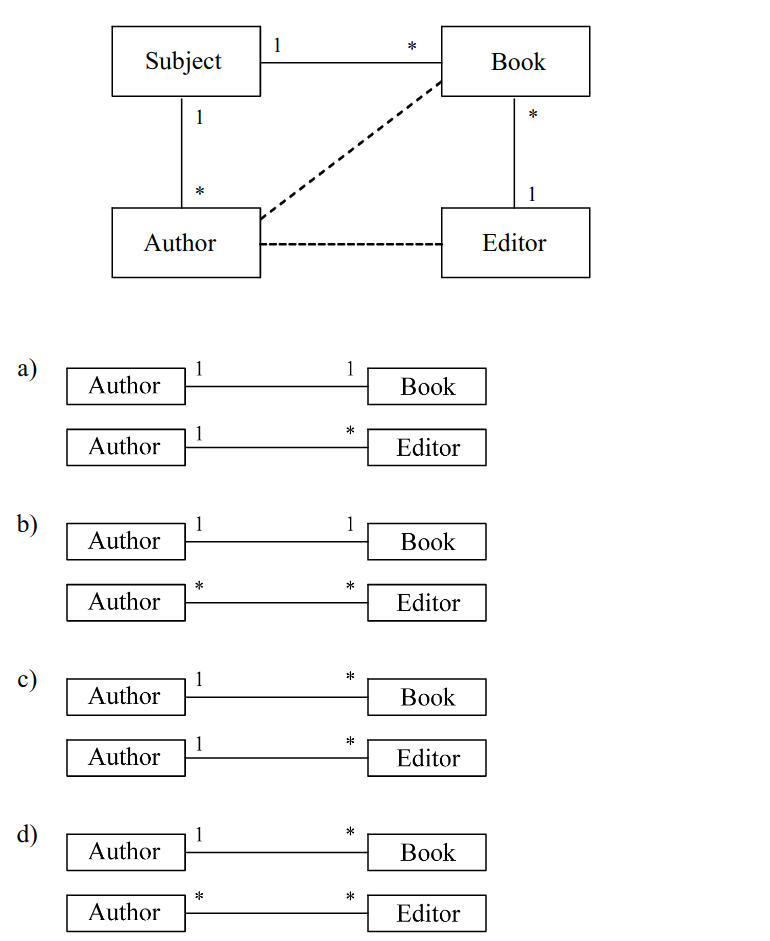","answer_label":"d","answer_id":21204},{"id":5183,"question":"When the database design is divided into three phases (i.e., conceptual design, logical design, and physical design), which of the following is a part of the physical design?","answer_label":"Describing base relations, file organizations, and indexes used to improve query performance","answer_id":21208},{"id":5184,"question":"When the table below is used to design a relational database for managing a video-rental shop, which of the following can be a potential candidate key? Here, (X, Y) represents a tuple of attributes X and Y.\n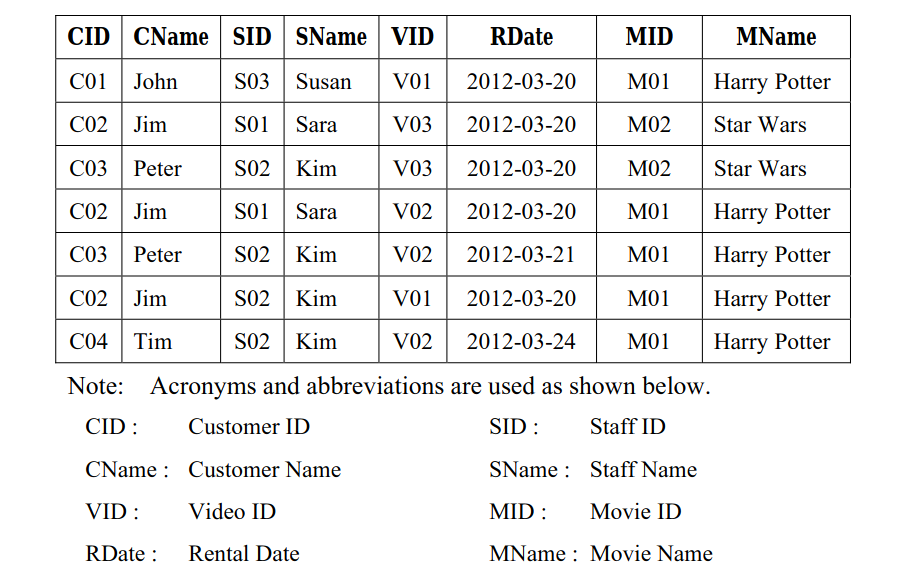","answer_label":"(CID, VID, RDate)","answer_id":21210},{"id":5185,"question":"In the term “ACID”, which is the basic foundation that database transactions are built upon, what does the third character “ I ” stand for?","answer_label":"Isolation","answer_id":21216},{"id":5186,"question":"Which of the following is the UPDATE statement that can correctly update the data of the “Product” table? Here, the “Product” table is defined by the CREATE statement shown below.\n","answer_label":"d","answer_id":21220},{"id":5187,"question":"Which of the following is the server that can be used to intercept all messages entering and leaving the network and to effectively hide the true network addresses?","answer_label":"Proxy server","answer_id":21224},{"id":5188,"question":"Which of the following is the data transmission technique that has features or characteristics shown below? \n- It is designed for cost-efficient data transmission for intermittent traffic between LANs and between end-points in a WAN. \n- Data is transmitted in a variable-size unit. \n- Error correction (i.e., retransmission of data is left up to the end-points. \n- It is based on the X.25 protocol, but it is faster because of a simplified X.25 protocol with minimal services. \n- It provides a mid-range service between ISDN and ATM.","answer_label":"Frame relay","answer_id":21226},{"id":5189,"question":"In the network shown below, the STP (Spanning Tree Protocol) is used on both S1 and S2 switches. When the link between two PCs A and C is established via L1, which of the following is the appropriate link that is used to transfer data between two PCs Band D?\n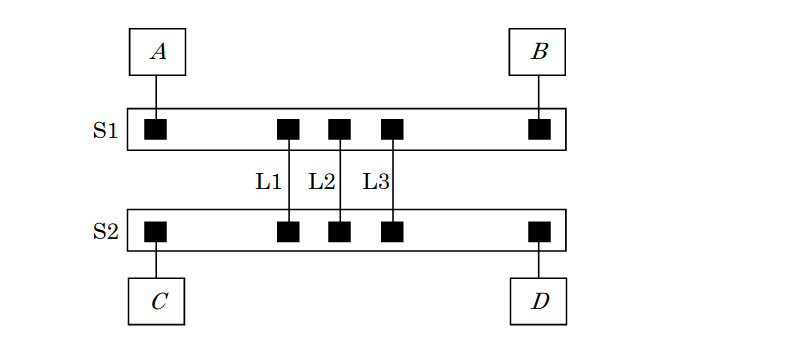","answer_label":"Always L1","answer_id":21229},{"id":5190,"question":"In a URL (Uniform Resource Locator) specified to access a Web page through the Internet, which of the following is the appropriate sequence of four basic parts: the name of the Web page, directory and/or subdirectory which holds the Web page, access protocol, and host name?","answer_label":"protocol, host name, directory, page","answer_id":21235},{"id":5191,"question":"Which of the following is used for encoding and interpreting binary files, images, video, and non-ASCII character sets within an e-mail message on the Internet?","answer_label":"MIME","answer_id":21238},{"id":5192,"question":"Which of the following is the protocol that is expanded and standardized based on SSL (Secure Sockets Layer) v3 but cannot interoperate with SSL?","answer_label":"TLS (Transport layer security protocol)","answer_id":21244},{"id":5193,"question":"Which of the following provides a baseline of security requirements for the operations of CA (Certification Authority) and RA (Registration Authority)?","answer_label":"Certificate policy","answer_id":21245},{"id":5194,"question":"Which of the following is an appropriate description concerning a digital envelope?","answer_label":"The sender encrypts the message by using symmetric key cryptography and then encrypts the symmetric key by using public key cryptography.","answer_id":21251},{"id":5195,"question":"There are two methods of biometric authentication: one extracts physical characteristics and the other extracts behavioral characteristics. Which of the following uses behavioral characteristics?","answer_label":"Authentication is performed by extracting characteristics from the writing speed and pen pressure used when a signature is produced.","answer_id":21255},{"id":5196,"question":"Which of the following is a method that is used to check if an image or other digital content has been illegally copied and resold?","answer_label":"Digital watermark","answer_id":21260},{"id":5197,"question":"The class diagram below shows part of an ordering system used for mail order and teleshopping. Which of the following is the most appropriate combination of relations that should be inserted into blanks A through D in order to complete the diagram?\n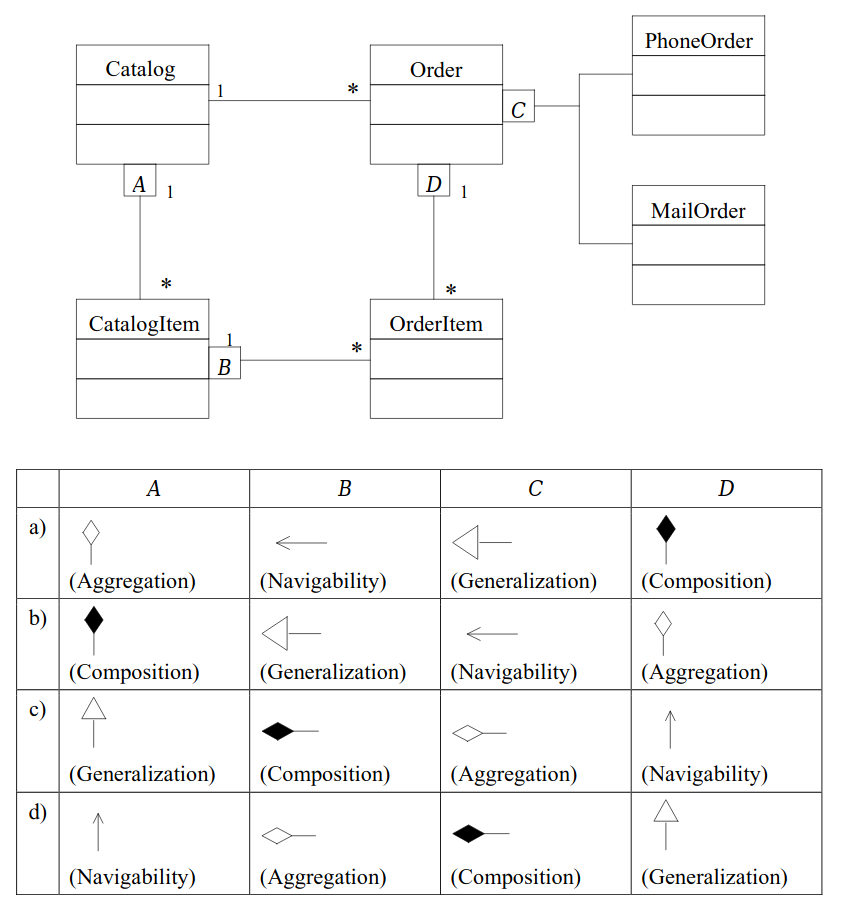","answer_label":"a","answer_id":21261},{"id":5198,"question":"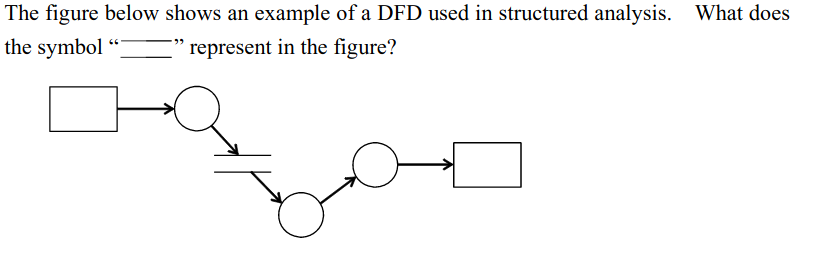","answer_label":"Data store","answer_id":21266},{"id":5199,"question":"Which of the following is a diagram that is used for modeling the event-driven or discrete behavior of an object in UML 2.x (i.e., UML 2.0 or later)?","answer_label":"State machine diagram","answer_id":21272},{"id":5200,"question":"From internal and external viewpoints concerning software product development and maintenance, which of the following is an appropriate quality characteristic that includes several sub-characteristics such as maturity, fault tolerance, recoverability, and availability?","answer_label":"Reliability","answer_id":21276},{"id":5201,"question":"Which of the following is a type of integration test that has the characteristics listed below? \n[Characteristics]\n- All of the related program modules are combined and tested at once. \n- Neither drivers nor stubs are required. \n- It is useful for small programs, but not for commercial development projects.","answer_label":"Big bang test","answer_id":21277},{"id":5202,"question":"Which of the following is a typical method that is contained in agile software development?","answer_label":"Extreme programming","answer_id":21282},{"id":5203,"question":"When 50% of the undefined specifications are defined each time a prototype is created, how many prototypes should be created to define over 90% of the specifications that are undefined at the start of prototyping?","answer_label":"4","answer_id":21288},{"id":5204,"question":"Which of the following is an appropriate explanation concerning a milestone in project management?","answer_label":"A milestone is a major event in a project schedule that is easily identifiable by such things as the completion of a significant deliverable and the occurrence of an event.","answer_id":21289},{"id":5205,"question":"The workload required to develop a system is estimated at 80 person-months if it is carried out by one person. When four staff members with the same productivity work together to develop the system, each member’s productivity is expected to decrease by 20%. How many working days does it take for the four members to develop this system? Here, this development work can be equally divided into four parts, and the four members can perform each individual part in parallel. In addition, each member can work 22 working days per month.","answer_label":"528","answer_id":21295},{"id":5206,"question":"When an application program has functions and characteristics shown in the table below, which of the following is the function point value of the program? Here the correction coefficient of complexity is 0.5.\n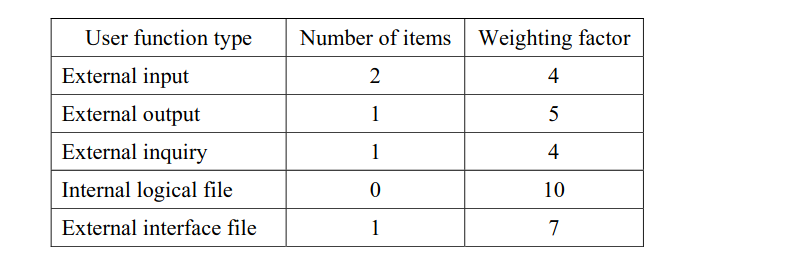","answer_label":"12","answer_id":21298},{"id":5207,"question":"Which of the following is the project management knowledge area that includes the processes of creating a staffing management plan, acquiring project team, developing project team, and managing project team?","answer_label":"Human resource management","answer_id":21302},{"id":5208,"question":"According to ISO/IEC 20000 (Information technology – Service management), which of the following is a process that has the objective to define and control the components of the service and infrastructure and to maintain accurate information on such components?","answer_label":"Configuration management","answer_id":21306},{"id":5209,"question":"Which of the following is an appropriate description concerning data backup?","answer_label":"Backup processing should not overlap with ordinary business processing in order to guarantee the integrity of backed-up data.","answer_id":21312},{"id":5210,"question":"In IT service management, which of the following is an activity that is performed as incident management?","answer_label":"Checking to see if a failure report from a user matches a known error","answer_id":21313},{"id":5211,"question":"Which of the following is an appropriate description concerning the implementation structure of a system audit?","answer_label":"The auditor reports the results of the audit to the requester so that the requester can give instructions for improvement based on the audit report.","answer_id":21319},{"id":5212,"question":"Which of the following is an appropriate description concerning an interview or a hearing that is conducted during a system audit?","answer_label":"The auditor should make an effort to get documents and records that confirm the information obtained from the department under audit during the interview.","answer_id":21322},{"id":5213,"question":"Which of the following is an appropriate measure that management takes to guarantee the apparent independence of internal system auditors?","answer_label":"Placing the department of auditors under the direct control of management","answer_id":21327},{"id":5214,"question":"The “four domains” of enterprise architecture include business architecture, technology architecture, application architecture, and one other. Which of the following is the one remaining architecture?","answer_label":"Data architecture","answer_id":21330},{"id":5215,"question":"Which of the following is the purpose of BPM that is a management approach in a company or an organization?","answer_label":"Continuous improvement of a company’s operational processes","answer_id":21334},{"id":5216,"question":"Which of the following is an explanation of “contact management” that is a basic function of SFA (Sales Force Automation)?","answer_label":"Performing effective sales activities for existing and prospective customers by managing a set of records including customer visiting days and sales results","answer_id":21340},{"id":5217,"question":"Which of the following is an appropriate explanation of the RFI that is created when a new information system is procured?","answer_label":"A request is made to the vendor for helpful information by showing the details of business operations and the purpose of the computerization.","answer_id":21343},{"id":5218,"question":"When a company’s business is divided into four categories A through D as shown in the figure below, which of the following is the characteristic of the business that is classified as category B?\n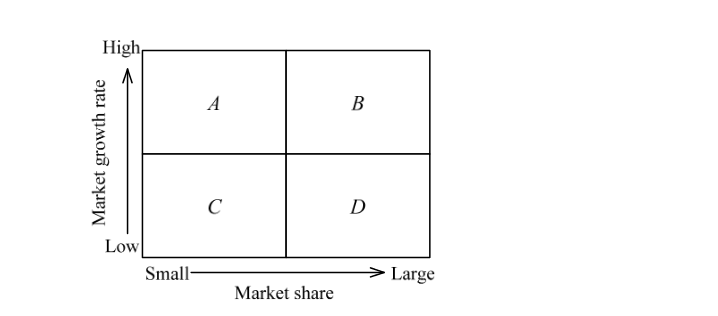","answer_label":"It is currently generating a large inflow of cash, but it also needs continuous investment into the future.","answer_id":21347},{"id":5219,"question":"Which of the following is the technique and concept for improving management efficiency by planning and controlling the company-wide management resources in an effective and integrated way?","answer_label":"ERP","answer_id":21350},{"id":5220,"question":"The four perspectives of the BSC (Balanced Score Card) includes “financial,” “learning and growth,” “internal business process,” and one other. Which of the following is the one remaining perspective that is sometimes extended to or replaced by “stakeholder” for modified or extended BSC models?","answer_label":"Customer","answer_id":21355},{"id":5221,"question":"Which of the following is an appropriate explanation of a franchise chain in the retail industry?","answer_label":"A form of organization in which a head office provides to its members usage rights of its trademarks and signs, and also provides managerial training and assistance in exchange for a fixed rate of compensation","answer_id":21359},{"id":5222,"question":"Which of the following is an appropriate characteristic of an RFID tag that is a type of IC tag and is used for locating and tracking merchandise, inventory, or other assets?","answer_label":"It reads information without physical contact by using electromagnetic waves.","answer_id":21363},{"id":5223,"question":"Which of the following is an appropriate explanation of EDI?","answer_label":"A method for electronically exchange of business data between computers over a network, based on standard formats and protocols","answer_id":21366},{"id":5224,"question":"Which of the following is a business organization that is divided according to the type of work performed as shown in the chart below?\n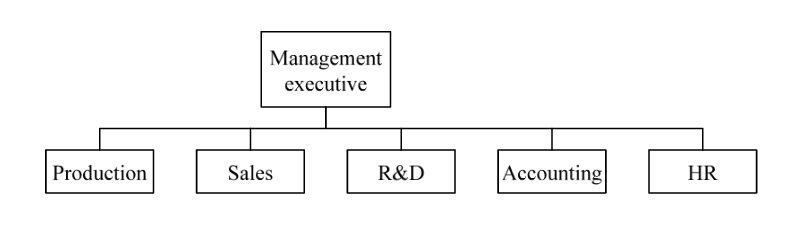","answer_label":"Functional organization","answer_id":21370},{"id":5225,"question":"Which of the following is an appropriate explanation of accessibility in the context of information technology?","answer_label":"Environment where even those who are handicapped or elderly have an easy access to information equipment and receive information services","answer_id":21374},{"id":5226,"question":"A trucking company has two types of trucks, A-type and B-type, as shown in the table below, and the company has a contract to deliver 900 boxes at a time by using the company’s own trucks. However, because of the limited availability of truck drivers, only a total of 10 trucks can be dispatched at a time. Which of the following is the set of expressions that can determine the number of trucks so as to minimize the delivery cost? Here, x and y are the number of A-type trucks and the number of B-type trucks, respectively.\n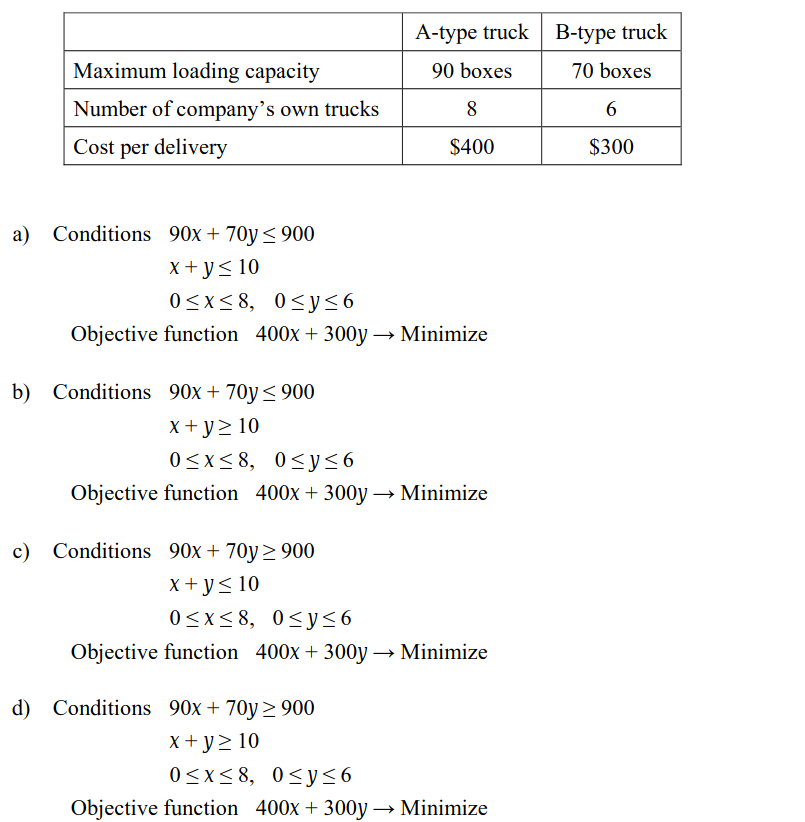","answer_label":"c","answer_id":21379},{"id":5227,"question":"An acceptance inspection is to be conducted on a purchased component that has a non-defective ratio of 0.9 and a defective ratio of 0.1. Four plans A though D are proposed for this acceptance inspection. The costs per non-defective and per defective for each plan are shown in the table below. Which of the following is the plan that has the lowest expected cost?\n","answer_label":"C","answer_id":21383},{"id":5228,"question":"The table below shows the income statement for a certain company. Which of the following is the amount of sales (in million dollars) at the break-even point?\n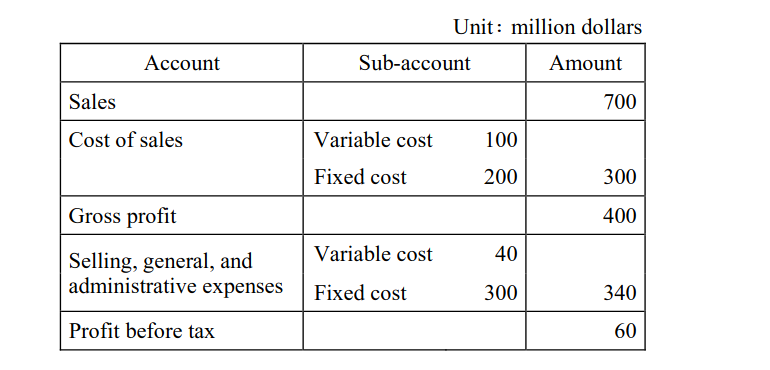","answer_label":"625","answer_id":21388},{"id":5229,"question":"Among various types of license agreements for a software package, which of the following is the most appropriate explanation of a site license?","answer_label":"A software package can be installed on any and all computers, such as PCs, workstations, and servers, at a given location in a company or an organization.","answer_id":21391},{"id":5230,"question":"Which of the following is the globally recognized model that is used for measuring the maturity level of software and systems development processes and providing guidance for quality processes across a project, a division, or an entire organization?","answer_label":"CMMI","answer_id":21393},{"id":5940,"question":"Which of the following represents the hexadecimal fraction 3A.5C as a decimal fraction?\na) ${\\frac {939} {16}}$\nb) ${\\frac {3735} {64}}$\nc) ${\\frac {14939} {256}}$\nd) ${\\frac {14941} {256}}$","answer_label":"b","answer_id":23972},{"id":5941,"question":"Which of the following hexadecimal numbers, representing signed 16-bit binary numbers, results in overflow when multiplied by 4? Here, a negative number is represented in 2’s complement.","answer_label":"DFFF","answer_id":23976},{"id":5942,"question":"Which of the following is the appropriate reason why the mantissa is normalized in the floating point representation?","answer_label":"The maximum number of significant digits can be maintained.","answer_id":23980},{"id":5943,"question":"The function f(x) has a real-type argument and a real-type return value. The procedure using this function is shown in the steps 1 through 5. When this procedure is executed repeatedly a sufficient number of times and the value of y stops changing in the step 3, which of the following expressions holds? \n[Steps] \n1. x←a \n2. y←f(x) \n3. Display the value of y \n4. x←y \n5. Return to the step 2","answer_label":"f(y) = y","answer_id":23986},{"id":5944,"question":"The student scores in a certain examination are shown in the table below. What is the standard deviation of these student scores? Here, the standard deviation δ can be defined as follows: \n$\\delta^2 = \\frac 1 n \\overset{n}{\\sum_{{i=0}}}{(x_i - \\overline{x})}^2$\n“δ” is a positive number, and “$n$” is the number of sample values. “$x_i$” is each sample value, and “$\\overline{x}$”is an arithmetic average of the sample values.\n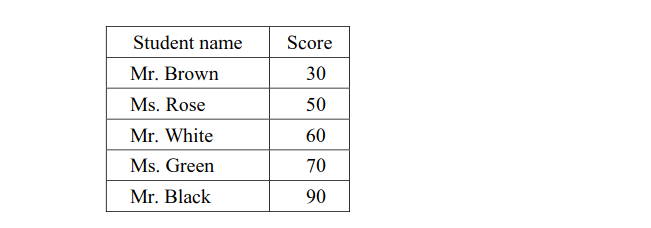","answer_label":"20","answer_id":23988},{"id":5945,"question":"There are three different sizes of white balls and three different sizes of green balls. When these six balls are laid out in a line so that the three white balls can be placed in adjacent positions, how many arrangements of all the balls can be made?","answer_label":"144","answer_id":23992},{"id":5946,"question":"Which of the following expressions results in a loss of trailing digits when calculated by a computer whose floating-point representation has a 23-bit mantissa? Here, the numbers in “( $)_2$” are represented in binary.\n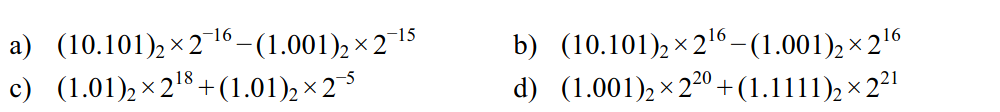","answer_label":"c","answer_id":23997},{"id":5947,"question":"There is a device consisting of Unit A, Unit B, and Unit C. Each unit can execute the “exclusive OR” operation in units of 4 bits. When an input bit string 1101 is given, an output bit string 0100 is obtained. In this device, if the internal key for Unit B is changed and the output bit string 1111 is generated, which of the following is the newly changed internal key for Unit B?\n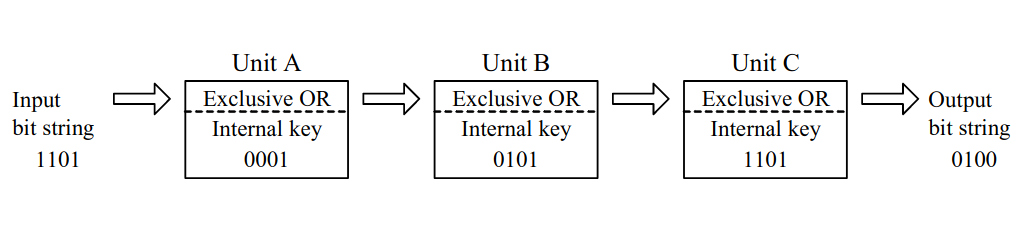","answer_label":"1110","answer_id":24002},{"id":5948,"question":"As shown in the truth table below, when an output signal is generated using three input signals A, B, and C, which of the following Boolean expressions can be applied to the output signal? Here, “$\\bigcap$” stands for the logical product, “$\\bigcup$\" for the logical sum, and “$\\overline{X}$” for the logical negation of “$X$”.\n","answer_label":"b","answer_id":24004},{"id":5949,"question":"A “negative AND” operation “X NAND Y” of X and Y is defined as “NOT (X AND Y)”. Which of the following is the logical expression that represents “X OR Y” by using NAND only?\n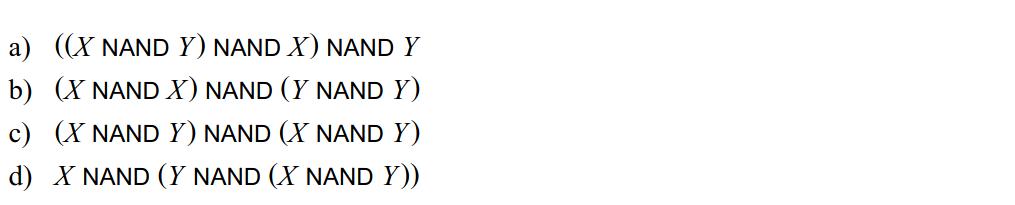","answer_label":"b","answer_id":24008},{"id":5950,"question":"Which of the following is included as an element of a set of character strings represented by a regular expression “[A – Z] + [0 – 9]*”? Here, the regular expression follows the rules described below. \n[A – Z] denotes a single alphabetical letter. \n[0 – 9] denotes a single numeral. \nThe symbol “*” denotes zero or more repetitions of the immediately preceding regular expression. \nThe symbol “+” denotes one or more repetitions of the immediately preceding regular expression.","answer_label":"ABCDEF","answer_id":24014},{"id":5951,"question":"Which of the following terms is applicable to the binary tree shown below?\n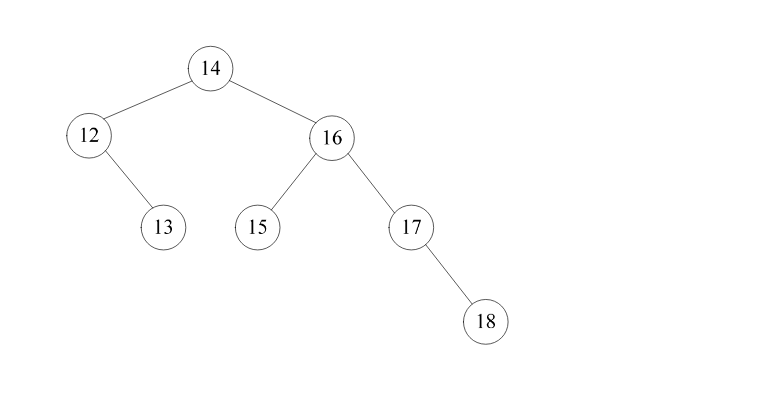","answer_label":"AVL tree","answer_id":24015},{"id":5952,"question":"In a unidirectional list shown below, $Blue$ is the top of the list, and its pointer indicates the next data address 110. In addition, $Yellow$ is the end of the list, and its pointer is 0. Which of the following operations can replace $Green$ with $Red$ in the list?\n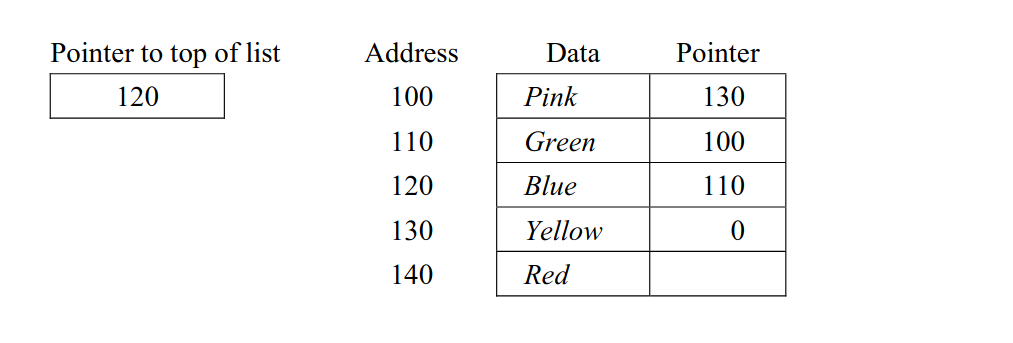","answer_label":"Set the pointers of *Red* and *Blue* to 100 and 140 respectively.","answer_id":24019},{"id":5953,"question":"In the graph shown below, which of the following is an appropriate description concerning the shortest path from the node “A” to another node? Here, the number shown beside the line indicates the distance between the two adjacent nodes.\n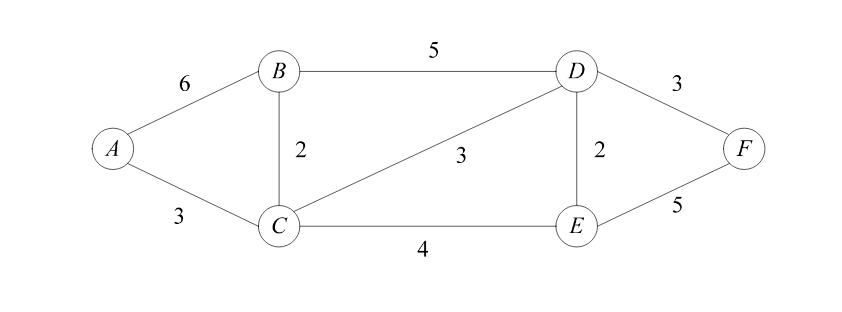","answer_label":"The shortest distance from A to F is 9.","answer_id":24026},{"id":5954,"question":"When the bubble sort algorithm is used for sorting the dataset (23, 43, 56, 12, 87, 14, 87, 15, 90, 23, 10) in descending order, how many data exchanges occur during the first pass?","answer_label":"8","answer_id":24028},{"id":5955,"question":"The flowchart below shows an algorithm in which two integers are temporarily entered into two variables x and y at the beginning, and then, after comparison of the two integers, the larger number is stored in the variable x and the smaller is in the variable y. In order to complete the algorithm, which of the following should be inserted in the process box $\\boxed {A}$ in the flowchart?\n","answer_label":"c","answer_id":24033},{"id":5956,"question":"Which of the following expressions shows the output $Z$ of the combinational circuit using NAND gates as shown below? Here, “・” stands for the logical product, “+” for the logical sum, and $\\overline {X}$ for the logical negation of $X$. \n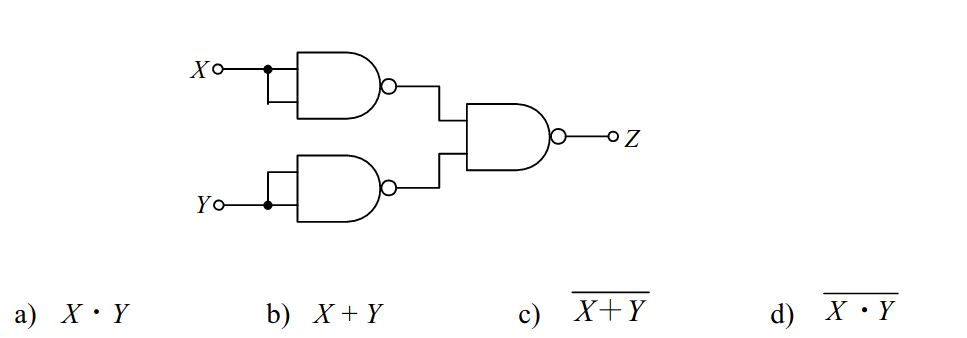","answer_label":"b","answer_id":24036},{"id":5957,"question":"When a certain RISC processor has a 5-stage instruction pipeline, how long (in nanoseconds) does it take to continuously execute 7 instructions excluding branch/jump instructions? Here, it takes 1.5 nanoseconds to complete each stage. In addition, any delay, such as pipeline stall and bubble, does not occur during the execution of those instructions.","answer_label":"16.5","answer_id":24041},{"id":5958,"question":"At least how many bits are required for the register identification field of a machine instruction code in order to specify one of 16 general purpose registers in the machine?","answer_label":"4","answer_id":24045},{"id":5959,"question":"Which of the following architectures in a uniprocessor requires multiple functional units that can execute two or more instructions in parallel during a clock cycle by simultaneously dispatching the instructions to the functional units?","answer_label":"Superscalar","answer_id":24049},{"id":5960,"question":"Which of the following is used to hold the address of the instruction being executed or the address of the next instruction to be executed, and is automatically incremented after fetching an instruction?","answer_label":"Program counter","answer_id":24054},{"id":5961,"question":"When a microprocessor works at a clock speed of 200 MHz and the average CPI (“cycles per instruction” or “clocks per instruction”) is 4, how long does it take to execute one instruction on average?","answer_label":"20 nanoseconds","answer_id":24056},{"id":5962,"question":"Which of the following is a method that serves to enhance the reliability of memory access and makes it possible to automatically correct some of data errors?","answer_label":"ECC","answer_id":24061},{"id":5963,"question":"Which of the following is an appropriate description concerning RAID?","answer_label":"RAID 0 increases performance by using disk striping. However, the reliability is rather low because damages on even one disk cause whole data to be lost.","answer_id":24063},{"id":5964,"question":"Which of the following USB transfer modes is mainly used for a mouse, joystick, etc.?","answer_label":"Interrupt transfer","answer_id":24069},{"id":5965,"question":"When an image is read with a scanner at a resolution of 600 dpi and printed with a printer at a resolution of 300 dpi, how many times as large as the area of the original image is the area of the printed image?","answer_label":"4","answer_id":24074},{"id":5966,"question":"Which of the following input devices is classified as a pointing device and used for graphics input in a CAD system?","answer_label":"Tablet","answer_id":24078},{"id":5967,"question":"Which of the following combinations of access time and hit ratio for cache memory and access time for main memory results in the shortest effective access time to main memory?\n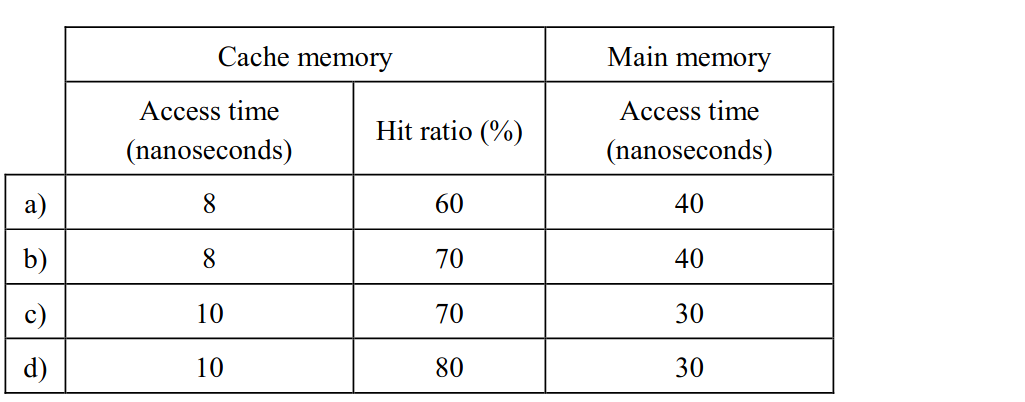","answer_label":"d","answer_id":24082},{"id":5968,"question":"The LRU method can be used as one of the methods for replacing blocks between the cache memory and the main memory. Which of the following blocks is subject to replacement by this method?","answer_label":"The block with the longest time since it was referenced last","answer_id":24086},{"id":5969,"question":"As one of the virtual storage methods, virtual address space is divided into fixed-length areas. What is such a fixed-length area called?","answer_label":"Page","answer_id":24088},{"id":5970,"question":"Which of the following descriptions about file storage is appropriate as the explanation of an archive?","answer_label":"It bundles multiple files into one file and stores it in a storage device.","answer_id":24091},{"id":5971,"question":"There is a fault-tolerant computer system with high reliability and availability in which two CPUs perform the same processing and compare the processing results to each other. If one CPU fails, the system cuts off the failed CPU and continues processing on the other CPU. What is this system configuration called?","answer_label":"Dual system","answer_id":24095},{"id":5972,"question":"Which of the following is an appropriate explanation of fault-tolerant systems?","answer_label":"Even in the event of a partial system failure, the system as a whole can provide necessary operational capabilities.","answer_id":24099},{"id":5973,"question":"There are four hard disk subsystems A, B, C, and D including two or three disks with designated MTBF values as shown in the table below. Which of the following hard disk subsystems can provide the highest reliability? Here, if one of the disks fails in each subsystem, it is regarded as a failure of the entire hard disk subsystem.\n","answer_label":"C","answer_id":24105},{"id":5974,"question":"Which of the following is the closest value as overall availability of the system composed of the four devices A to D? Here, availability of individual device is 0.9 for A and C, and 0.8 for B and D. In addition, when either of the parallel connections is operating, the corresponding parallel portion can be regarded as operating.\n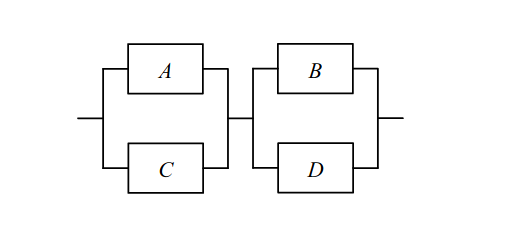","answer_label":"0.95","answer_id":24110},{"id":5975,"question":"Which of the following is the most appropriate description concerning the interconnection interfaces between computers and peripheral devices or between peripheral devices?","answer_label":"IEEE 802.11 refers to a family of specifications for wireless LAN, and includes several standards, such as IEEE 802.11a, 802.11b, and 802.11g, which define over-the-air interfaces between a wireless client and a base station or between two wireless clients.","answer_id":24113},{"id":5976,"question":"Which of the following performs reasoning using a knowledge base?","answer_label":"Expert system","answer_id":24115},{"id":5977,"question":"Which of the following is the main purpose of optimization performed by a compiler?","answer_label":"To reduce program execution time","answer_id":24121},{"id":5978,"question":"Which of the following is the international standard of the document description language that defines how to describe the logical structure and makes it easy to manage and exchange electronic documents?","answer_label":"SGML","answer_id":24125},{"id":5979,"question":"Which of the following software, as represented by Linux, requires the freedom to redistribute, inclusion of the source code at redistribution, and consent to modify derived software?","answer_label":"Open source software","answer_id":24129},{"id":5980,"question":"Which of the following is the activity performed during the external design phase in system development?","answer_label":"Logical data design","answer_id":24131},{"id":5981,"question":"In the DFD for a sales management system shown below, which of the following is appropriate for item A?\n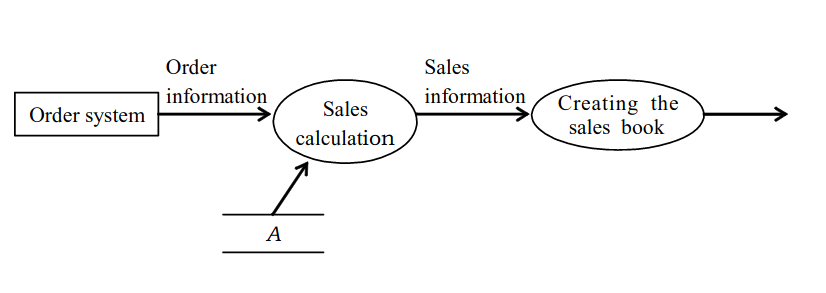","answer_label":"Unit price list","answer_id":24138},{"id":5982,"question":"Which of the following is the appropriate description of the relationship between a class and an instance in the object-oriented approach?","answer_label":"An instance is generated based on the definition of a class.","answer_id":24140},{"id":5983,"question":"Module coupling needs to be weakened in order to increase module independence. Which of the following has the weakest level of module coupling among methods of information transfers between modules?","answer_label":"Only data items are passed as arguments between modules.","answer_id":24145},{"id":5984,"question":"Which of the following is the appropriate point to notice at the time of creating the test data for a white box test?","answer_label":"The internal structures, such as the algorithm, for the program","answer_id":24149},{"id":5985,"question":"Which of the following is the appropriate purpose of design review?","answer_label":"To find specification defects and design errors at an early stage, and reduce the person hours for rework","answer_id":24151},{"id":5986,"question":"When the cost associated with information systems can be broken down into the initial costand the runningcost, which of the following is included in the initial cost?","answer_label":"Development cost of application software","answer_id":24156},{"id":5987,"question":"In an arrow diagram shown below, how many days are needed in minimum to complete all the activities A through G? Here, in the diagram, each number shown beside the arrow indicates the number of days required to complete the activity.\n","answer_label":"27","answer_id":24162},{"id":5988,"question":"When the development department and the operations department of a system are organized separately, which of the following is the appropriate method for smooth and effective transfer from development to operations?","answer_label":"The operations department proactively participates in the system development and provides advice from the viewpoint of operations.","answer_id":24166},{"id":5989,"question":"When there are multiple business application systems available, which of the following is the most appropriate method for access control?","answer_label":"Appropriate access permissions are granted for each business application system, irrespective of a user’s position and authority.","answer_id":24169},{"id":5990,"question":"Which of the following is the most appropriate description concerning the changes in network configuration after the beginning of operations?","answer_label":"It is necessary to update the equipment control log, network diagram, etc. on a timely basis so that the network configuration can be changed at any time as needed.","answer_id":24171},{"id":5991,"question":"Which of the following is an appropriate description concerning maintenance of applications?","answer_label":"Record the completion of maintenance in order to prevent maintenance activities from being left uncompleted.","answer_id":24176},{"id":5992,"question":"Which of the following appropriately explains the function of the transport layer in the OSI basic reference model?","answer_label":"It is responsible for maintaining reliable end-to-end communications and data transfer between systems across the network, and provides a variety of functions including flow control, virtual circuit, and error checking and recovery.","answer_id":24180},{"id":5993,"question":"Which of the following is the appropriate statement concerning the number of host addresses available to one sub-network in IPv4?","answer_label":"The number of host addresses available in a sub-network is determined by the number of “0” bits in the subnet mask.","answer_id":24185},{"id":5994,"question":"Which of the following is the local broadcast address to be used by a computer with IP address 202.130.17.63 and subnet mask 255.255.255.0 if classless addressing is used?","answer_label":"202.130.17.255","answer_id":24190},{"id":5995,"question":"When a 9-Kbyte data file is transmitted using the asynchronous (or start-stop) communication protocol at a speed of 2,400 bps, what is the “overhead” (time spent on sending start, stop, and parity bits except data bits) in seconds? Here, a start bit is first sent, followed by eight data bits, no parity bit, and one stop bit, for each byte of the data file.","answer_label":"7.5","answer_id":24191},{"id":5996,"question":"When MAC (Media Access Control) frames defined by IEEE 802.3 are transmitted over Ethernet, which of the following methods is used for error detection?","answer_label":"CRC","answer_id":24196},{"id":5997,"question":"Which of the following methods is used for avoiding unnecessary collisions in the IEEE 802.11 family of wireless LAN standards?","answer_label":"CSMA/CA","answer_id":24200},{"id":5998,"question":"VLAN (Virtual LAN) is used to logically segment a LAN into different broadcast domains. In which of the following network devices should the function of VLAN be supported?","answer_label":"Switch","answer_id":24206},{"id":5999,"question":"Which of the following is an appropriate explanation of the schema in a relational database management system?","answer_label":"It is a set of data definitions, such as the data attributes, data formats, and relationships with other data.","answer_id":24207},{"id":6000,"question":"$\\boxed{x} \\to \\boxed{y}$ indicates that the value of attribute $y$ is determined uniquely by the value of attribute $x$. Which of the following appropriately defines the relationships shown in the figure as a set of tables of the third normal form? Here, multiple attributes contained in a box $\\boxed{x}$ show that the value of attribute $y$ is determined uniquely by the values of all those multiple attributes.\n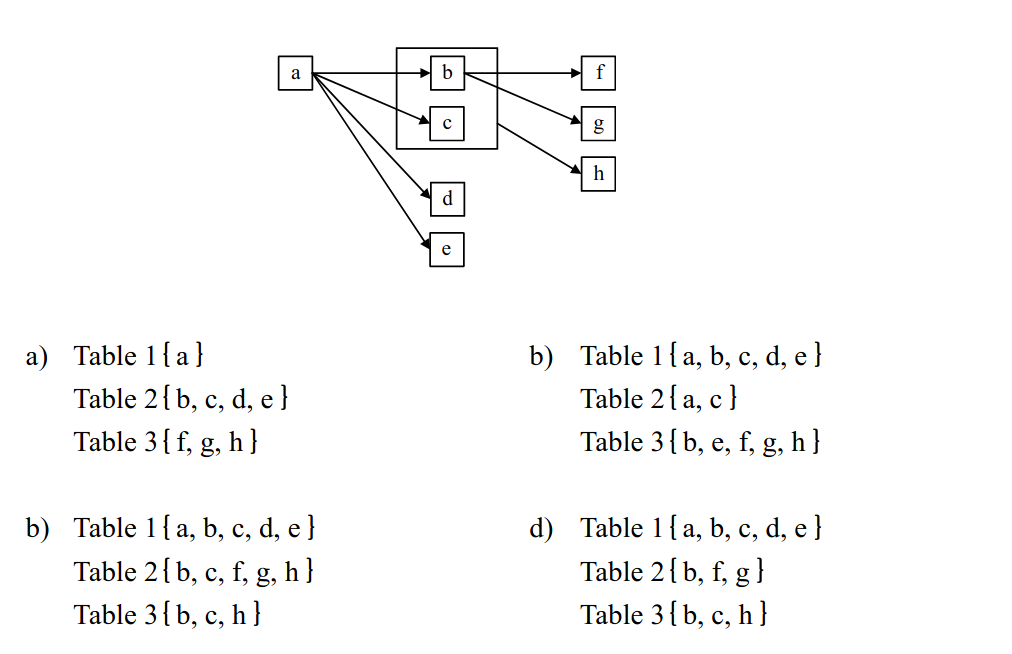","answer_label":"d","answer_id":24214},{"id":6001,"question":"Which of the following is a non-updatable view?","answer_label":"A view including a “GROUP BY” clause in the view definition","answer_id":24216},{"id":6002,"question":"There are two tables X and Y as shown below. Which of the following SELECT statements returns the maximum number of rows by using these two tables?\n","answer_label":"a","answer_id":24219},{"id":6003,"question":"When a new record is inserted in the relational database table “Payment” shown below, which of the following SQL statements causes a unique constraint violation? Here, “Contract_number” and “Contract_date” are primary keys.\n","answer_label":"d","answer_id":24226},{"id":6004,"question":"Which of the following files is used for writing the values before and after a database update, and storing them as a database update record?","answer_label":"Journal file","answer_id":24230},{"id":6005,"question":"When secret documents are sent and received using public key cryptography, which of the following is an appropriate description of the key management?","answer_label":"The decryption key must be kept private, but the encryption key is public.","answer_id":24231},{"id":6006,"question":"In the context of message authentication code, which of the following is the purpose of using message digests?","answer_label":"To confirm that no message has been tampered with","answer_id":24237},{"id":6007,"question":"Which of the following is an appropriate explanation of Web beacons?","answer_label":"Images embedded in Web pages to gather information such as user access trends","answer_id":24239},{"id":6008,"question":"Which of the following is an appropriate description concerning security measures for network systems?","answer_label":"By using a circuit-switched network with closed-area connection functions, limiting connections to particular user groups is an effective way to prevent unauthorized external access.","answer_id":24243},{"id":6009,"question":"There are two types of attacks which an information system might face: active attack and passive attack. Which of the following is categorized as an active attack?","answer_label":"Falsification of data","answer_id":24249},{"id":6010,"question":"Which of the following shows the appropriate sequence of items 1 through 3 that are required for establishing ISMS according to ISO/IEC27001:2005? \n[Items] \n1. Prepare a Statement of Applicability \n2. Select control objectives and controls for the treatment of risks \n3. Analyze and evaluate the risks","answer_label":"3 → 2 → 1","answer_id":24254},{"id":6011,"question":"The projected annual purchase amount and the actual annual transaction value of each client company are plotted on the graph. Which of the following is the appropriate description concerning the future sales policy?\n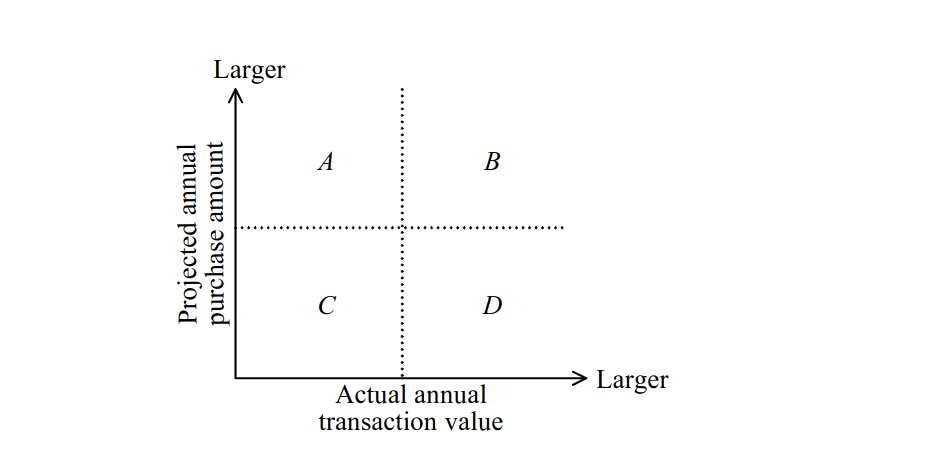","answer_label":"A client in area A has the potential of becoming a major customer, so it is better to strengthen sales activities.","answer_id":24255},{"id":6012,"question":"Which of the following financial statements indicates the assets, liabilities, and net assets of a company at a specific time and shows the financial condition of the company?","answer_label":"Balance sheet","answer_id":24259},{"id":6013,"question":"The table shows the sales, cost, and profit for a certain product in the current period. When the sales unit price of this product is 5 dollars, at least how many should be sold to earn twice or more in profit during the next period?\n","answer_label":"3000","answer_id":24265},{"id":6014,"question":"Which of the following is the work sampling method?","answer_label":"It specifies the number of observations and observation time, and estimates working hours from the ratio of the number of observation points by actual observation based on statistical theory.","answer_id":24270},{"id":6015,"question":"How many days in total are required in the critical path of the arrow diagram? Here, the number shown beside the arrow indicates the number of days for each activity.\n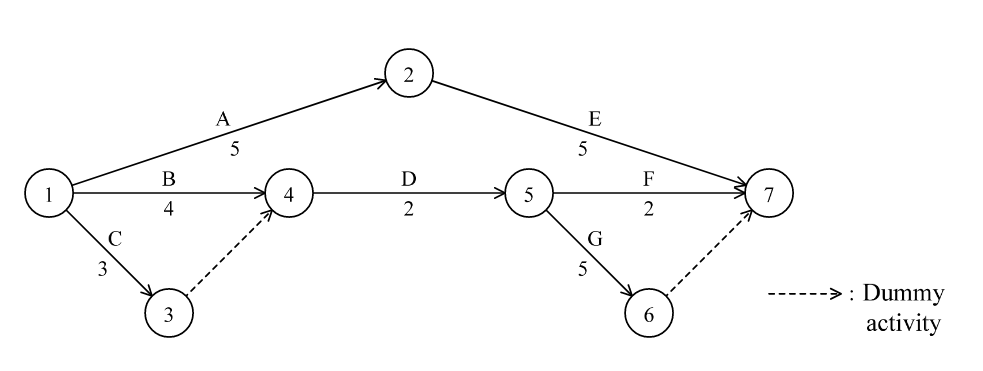","answer_label":"11","answer_id":24274},{"id":6016,"question":"A certain factory has recorded the number of defective products in the past on a root cause basis. Which of the following is the graph that indicates the factors that are ranked high for defective products and their rates, based on this record?\n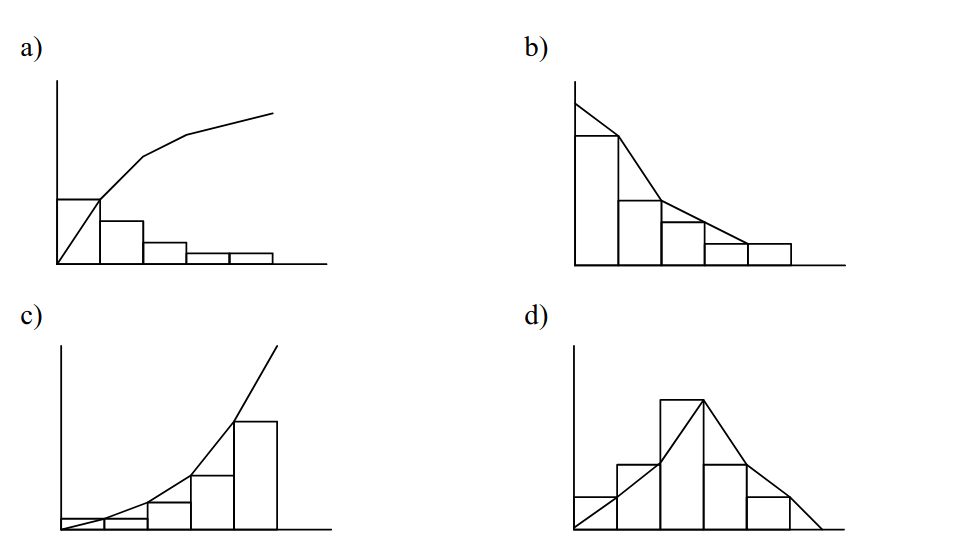","answer_label":"a","answer_id":24275},{"id":6017,"question":"You want to invest in one of the stocks A through D, all of which are 100 dollars at the current price. The table shows the predicted price increase of each stock when the growth of the economy is high, medium, or low. When the “maximin” principle is applied, which of the following stocks should be invested in?\n","answer_label":"A","answer_id":24279},{"id":6018,"question":"Three products A, B, and C are processed by two machines M1 and M2. Processing must be performed in order of M1→M2 (M1 first and then M2). The table shows the time required to process each product on each machine.In this case, which of the following shows the order of processing these three products so that the time required from the start of the process to the completion of the process for all the products may be the shortest? Here, when processing of a product at M1 is completed, another product can be processed consecutively at M1. Preparation time, such as setup time, is ignored.\n","answer_label":"B→A→C","answer_id":24284},{"id":6019,"question":"Which of the following explains a volume license agreement?","answer_label":"The agreement offers a master to a bulk buyer of the software, such as a company, and determines the maximum installable number of licenses beforehand.","answer_id":24288},{"id":6021,"question":"There is an 8-bit register where integers are represented in binary by using 2’s complement for negative numbers. When the decimal integer “– 24” is stored in the register and then arithmetically shifted 2 bits right, what is the resulting value in decimal? Here, the leftmost bit of the register is used as a sign bit.","answer_label":"-6","answer_id":24298},{"id":6022,"question":"When a single-bit “half adder” circuit is used for simply adding two input signals x1 and x2 , which of the following is the appropriate combination of logical expressions for two output signals s (sum) and c (carry)? Here, “ + ” stands for the logical OR operation and “ ・ ” for the logical AND operation.\n","answer_label":"c","answer_id":24302},{"id":6023,"question":"Which of the following prefix expressions is equivalent to the infix expression “(A + B)*C–(D–E)”?","answer_label":"–* + A B C – D E","answer_id":24304},{"id":6024,"question":"The syntax rules of the field identifier “field ID” are represented in BNF notation as shown below. When each ID is defined as an arbitrary sequence of letters and/or digits, which of the following should be inserted into the blank A?\n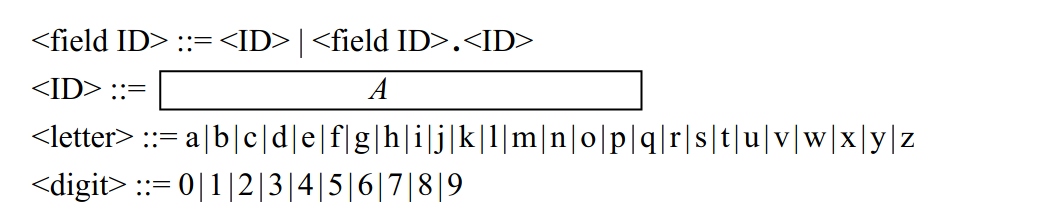","answer_label":"<letter> | <digit> | <ID> <letter> | <ID> <digit>","answer_id":24310},{"id":6025,"question":"As shown in the figure below, there is a binary tree which is created in accordance with a specific rule that the value of a parent node is greater than that of a child element. \n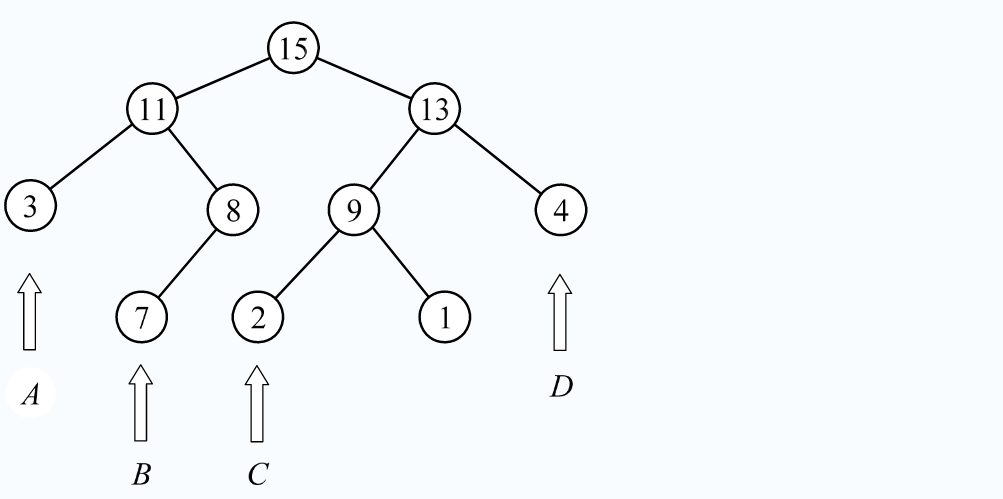\nWhen a new element with the value 12 is inserted in the places marked by A, B, C, or Din the tree according to the steps defined below, where should it be inserted in order to maintain the specific rule and minimize the number of exchanges? \n[Steps] \n1. Add the element to a leaf node of the tree. \n2. Compare the added element with its parent; if the result is in the correct order, stop. If not, go to Step 3. \n3. Exchange the element for its parent and return to Step 2.","answer_label":"D","answer_id":24315},{"id":6026,"question":"When a set of values “5, 4, 3, 2, 8, 6, 0, 1, 9, and 7” is inserted in this order to create a binary search tree, which of the following represents the sequence of node values visited in the post-order traversal of the binary search tree?","answer_label":"1 0 2 3 4 7 6 9 8 5","answer_id":24317},{"id":6027,"question":"There is a queue with eight cells and two pointers as shown below. \n\nAt this point, three values 6, 8, and 15 are stored in the queue. The start and end pointers indicate the location of the first and last data values respectively. After the series of operations described below is performed, which of the following is the appropriate combination of the two pointers? Here, upon reaching the end of the queue area, the pointers wrap around to the beginning of the queue again. \n[Operations] \n1.One value is enqueued. \n2.Two values are dequeued. \n3.Three values are enqueued. \n4.One value is dequeued. \n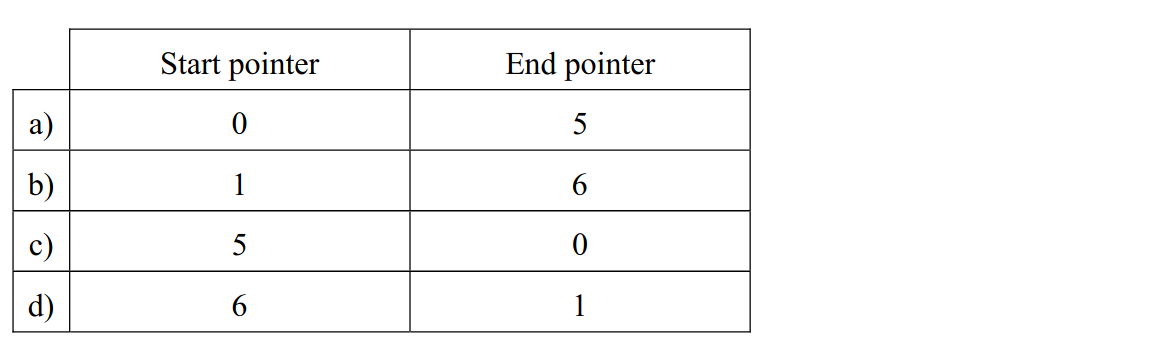","answer_label":"c","answer_id":24322},{"id":6028,"question":"When the series of operations below is performed on an empty stack, which of the following is the data remaining on the stack? Here, “push x” is the operation to save data x to the stack, and “pop” is used to retrieve data from the stack.\n push 1 → push 2 → pop → push 3 → push 4 → pop → push 5 → pop","answer_label":"1 and 3","answer_id":24324},{"id":6029,"question":"The steps below are used to sort a dataset in descending order by using a max heap.\n[Steps] \n1.Extract an element one by one from an unsorted dataset, and insert it into a max heap until all the elements are extracted and inserted. \n2.Delete the root element from the max heap, and store it in a sorted dataset. Stop if all the elements are deleted. Otherwise, go to Step 3. \n3.Move the rightmost element on the deepest level to the root. Go to Step 2 if the remaining elements are in the correct order as a max heap (that is, all the parent elements are greater than or equal to their corresponding child elements). Otherwise, go to Step 4. \n4.Compare the replaced element with its children, and then exchange the element for its larger child. Go to Step 2 if all the elements are in the correct order as a max heap. Otherwise, continue Step 4 toward deeper levels. \nIn the max heap shown below, how many element exchanges in Step 4 are executed to build the next max heap after deletion of the root “5” in Step 2?\n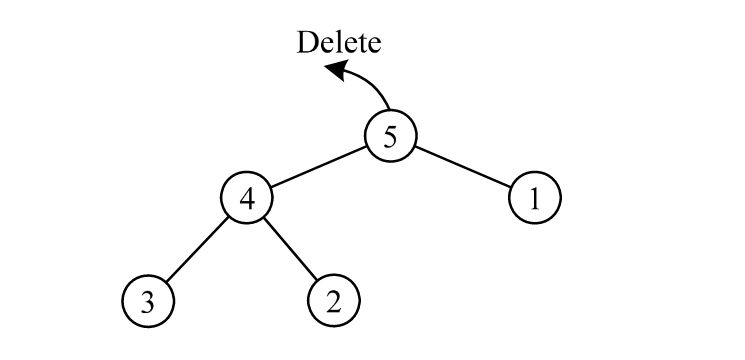","answer_label":"2","answer_id":24330},{"id":6030,"question":"The Fibonacci sequence (0, 1, 1, 2, 3, 5, 8, 13, 21, 34, ...) can be defined recursively as follows: \n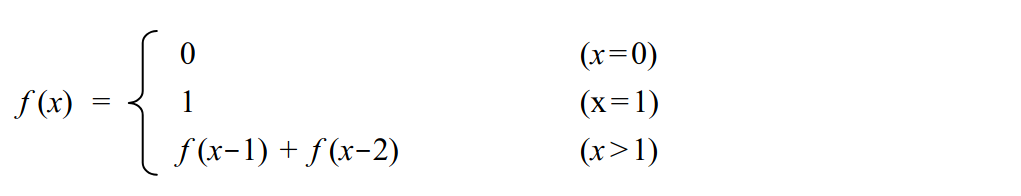\nHow many times is the function f(x) called to calculate the Fibonacci number f(5)?","answer_label":"15","answer_id":24335},{"id":6031,"question":"In a certain CPU, a floating point adder unit uses a total of 40 percent of the execution time. If the floating point adder unit is replaced with a new unit whose speed is ten times faster than the original unit, approximately how many times faster is the new CPU than the original one? Here, there is no modification in the instruction set of the new CPU.","answer_label":"1.56","answer_id":24338},{"id":6032,"question":"There is a CPU with a clock frequency of 1 GHz. When the instructions consist of two types as shown in the table below, what is the performance in MIPS of the CPU?\n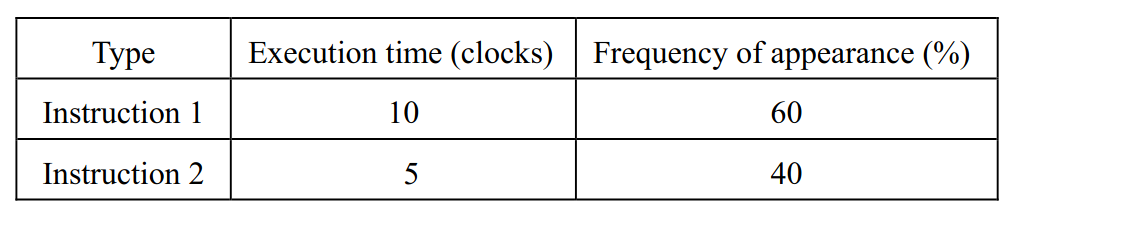","answer_label":"125","answer_id":24342},{"id":6033,"question":"When a color image is stored in video memory at a tonal resolution of 24 bits per pixel, approximately how many megabytes (MB) are required to display the image on the screen with a resolution of 1024x768 pixels? Here, 1 MB is 10^6 bytes.","answer_label":"2.4","answer_id":24345},{"id":6034,"question":"How many memory cells (or latches for holding 1 bit each) are implemented in SRAM with 24 address lines and 16 data lines?","answer_label":"2^24x16","answer_id":24351},{"id":6035,"question":"There is a hard disk drive that has the specifications shown in the table below. When a record of 10,000 bytes is read out from this disk, approximately how long (in milliseconds) does it take to access the disk and to complete the data transfer? Here, the data is stored contiguously from the beginning of one track, and the entire data on the track can be read and transferred per revolution. \n","answer_label":"42","answer_id":24355},{"id":6036,"question":"Which of the following is the appropriate purpose of defragmentation of hard disks?","answer_label":"To access disk files faster and more efficiently","answer_id":24356},{"id":6037,"question":"Which of the following is an appropriate explanation of TCO?","answer_label":"Total cost required throughout the life cycle of a system","answer_id":24363},{"id":6038,"question":"In the RAID3 system shown below, three disks (Disks 0 through 2) for byte-striped data and one dedicated parity disk (Disk 3) are used as one volume. Parity byte Ap is generated by calculating the “exclusive OR” ($\\bigoplus$) of three bytes in Disks 0 through 2. For example, $A_p$(1-3) is calculated as follows:\n\n$A_p(1-3) = A_1 \\bigoplus A_2 \\bigoplus A_3$\n\nIn the event of a disk failure, data recovery can be accomplished by using the information recorded on the remaining three error-free disks. Which of the following operations should be executed for this data recovery?\n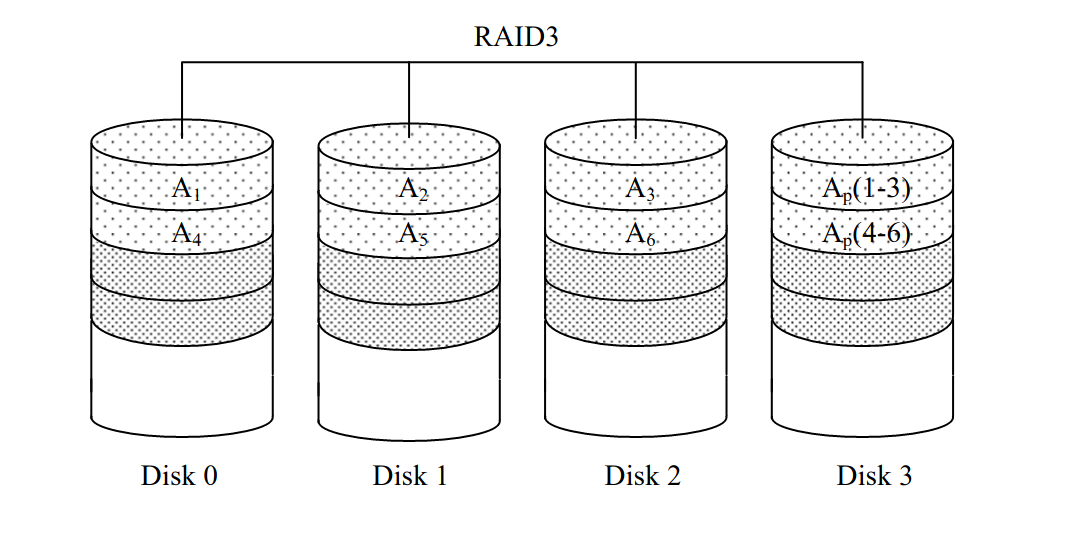","answer_label":"Exclusive OR","answer_id":24366},{"id":6039,"question":"Backup sites, which are used during system downtime, are classified into three types: warm, cold, and hot sites. In general, which of the following is the list arranged in order from shortest to longest recovery time?","answer_label":"Hot site, warm site, cold site","answer_id":24369},{"id":6040,"question":"Which of the following is the appropriate explanation of throughput?","answer_label":"It is the number of jobs processed per unit time. Spooling helps to improve throughput.","answer_id":24374},{"id":6041,"question":"What range of decimal numbers can be represented with an 11-bit two’s complement number?","answer_label":"-1024 to 1023","answer_id":24379},{"id":6042,"question":"Which of the following decimal fractions becomes a finite fraction in an octal representation?","answer_label":"0.5","answer_id":24383},{"id":6043,"question":"When a certain natural number x is expressed as a 2n-digit binary number “1010…10” consisting of 1 and 0 arranged alternately, which of the following equations can be formulated in terms of the number x?","answer_label":"x + x / 2 = 2^(2n) – 1","answer_id":24386},{"id":6044,"question":"An integer m is stored in a register as binary value. If this value is shifted to the left by three bits and m is added to the shifted value, how many as large as m is the resulting number? Here, no overflow occurs.","answer_label":"9","answer_id":24392},{"id":6045,"question":"Which of the following is the reason why a large number of computer use “complement representation” to simplify arithmetic circuits?","answer_label":"Subtraction can be processed by addition.","answer_id":24396},{"id":6046,"question":"Which of the following is the appropriate statement concerning Newton’s method that is known as an algorithm for obtaining the approximate value of the solution to the formula f(x) = 0?","answer_label":"An approximate value of the solution is obtained geometrically using the tangent lines of y = f(x).","answer_id":24398},{"id":6047,"question":"There is a four-digit number $N_1N_2N_3C$ that is used for Customer Account Number (CAN). The right most digit “C” can be calculated as follows:\n\n$$C = (N_1*3 + N_2*5 + N_3*7) \\bmod 10$$\n\nWhich of the following is a correct CAN? Here, x mod y returns the remainder when x is divided by y.","answer_label":"9690","answer_id":24403},{"id":6048,"question":"Two players, X and Y play a dice game. A pair of dice is tossed. If the sum of the dice is 2, 4, or 6, X wins the game. Otherwise, Y wins. What is the probability that Y wins the game?","answer_label":"3/4","answer_id":24408},{"id":6049,"question":"There are a total of 1,900 students in a school, 553 of whom are taking a course in computer science, 667 of whom are in mathematics, and 290 of whom are in both computer science and mathematics. How many students are not taking a course in either computer science or in mathematics?","answer_label":"970","answer_id":24411},{"id":6050,"question":"Which of the following is equivalent to the logical expression A • B + B • C • (B + C) ? Here, “•” is the logical product, and “+” is the logical sum.","answer_label":"B • (A + C)","answer_id":24415},{"id":6051,"question":"There are three 7-bit character codes: 30, 3F, and 7A. When an even parity bit is added to the front of each character code, which of the following shows the correct result? Here, the character codes are expressed in hexadecimal.","answer_label":"30, 3F, FA","answer_id":24418},{"id":6052,"question":"Which of the following data structures uses the LIFO (Last In First Out) method in order to manage data?","answer_label":"Stack","answer_id":24424},{"id":6053,"question":"In a microprocessor, there are two general registers: GRi and GRj (hereinafter referred to as GRx instead of GRi or GRj). PUSH GRx is used for adding the contents of GRx to the top of a stack. POP GRx is for removing the current top data of the stack and storing it to GRx. Which of the following operations can exchange the contents of GRi and GRj?","answer_label":"PUSH GRi, PUSH GRj, POP GRi, POP GRj","answer_id":24427},{"id":6054,"question":"Which of the following is the appropriate statement concerning data sorting methods?","answer_label":"The “heap sort” method builds an ordered tree from the unsorted portion of the elements, extracts the maximum or minimum value from this ordered tree, and moves it to the sorted portion. This operational sequence is then repeated to gradually shrink the unsorted portion.","answer_id":24430},{"id":6055,"question":"A binary tree is said to be perfect, if all its leaves are at the same depth and every internal node has two children. Which of the following is correct about the perfect binary tree? Here, n is the number of nodes, and h is the height of the perfect binary tree.","answer_label":"n = 2^(h+1) – 1","answer_id":24435},{"id":6056,"question":"A depth-first search (DFS) visits all the vertices in a graph. When an edge to be explored next is chosen, this algorithm always chooses to go “deeper” into the graph. That is, it will pick the next adjacent unvisited vertex until reaching a vertex that has no unvisited adjacent vertices. The algorithm will then backtrack to the previous vertex and continue along any as-yet unexplored edges from that vertex. After DFS has visited all the reachable vertices from a particular source vertex, it chooses one of the remaining undiscovered vertices and continues the search. Which of the following is not a valid order in which the vertices of the graph below can be marked as “visited” during a DFS?\n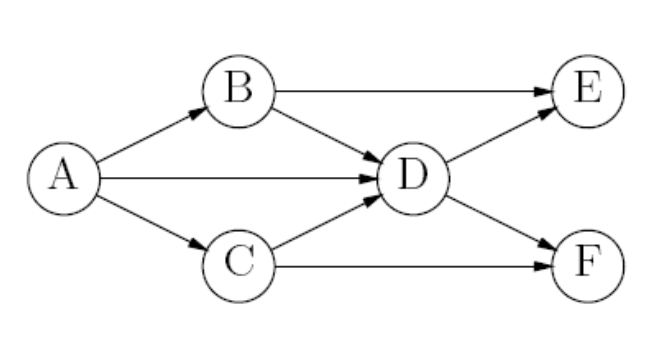","answer_label":"ABCDEF","answer_id":24437},{"id":6057,"question":"Which of the following equations holds well in the postfix notation (or Reverse Polish Notation)? Here, x, y, and z are variables.","answer_label":"x y – z + = x y z – –","answer_id":24443},{"id":6058,"question":"The following function f (n, k) exists:\n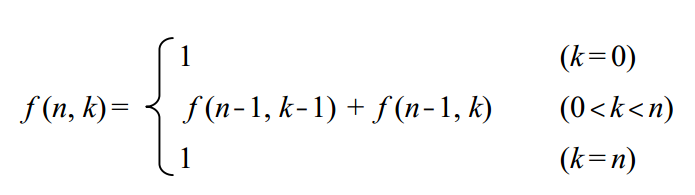\nWhat is the value of f (4, 2)?","answer_label":"6","answer_id":24448},{"id":6059,"question":"Which of the following logic circuits generates the same output as the logic circuit\nshown in the figure below? Here \nand represent the logical product, the logical sum, and the logical negation respectively.\n","answer_label":"b","answer_id":24450},{"id":6060,"question":"Which of the following leads to the von Neumann bottleneck?","answer_label":"Data transfer speed between CPU and main memory","answer_id":24456},{"id":6061,"question":"Which of the following is the highest priority process just after execution of each instruction on CPU?","answer_label":"Check if there are any interrupts waiting","answer_id":24458},{"id":6062,"question":"The instruction pipeline is a technique used in order to improve the CPU performance. Instructions are divided into stages and moved through the processor. An RISC processor has five-stage pipeline (Instruction fetch, Instruction decode, Execute, Memory access, Register write back) and can accept a new instruction at every clock cycle. How many clock cycles does this processor take for completion of the execution of 10 instructions? Here, there are no pipeline stalls, such as branch stall, load stall, and so on.","answer_label":"14","answer_id":24462},{"id":6063,"question":"There is a processor with a clock frequency of 1 GHz. When the instruction set of this processor is composed of two types of commands as shown in the table below, what is the approximate processing performance in MIPS?\n","answer_label":"125","answer_id":24467},{"id":6064,"question":"A CPU has four blocks of cache memory. Using the LRU (Least Recently Used) replacement algorithm, which memory blocks are stored in the cache memory after the execution of the following sequence of access to memory blocks: 1 2 3 4 5 2 5 4 1 5 2 3? Here, at the start of the memory access, the four cache blocks are empty and used in sequence until all the blocks are occupied. In other words, the cache blocks contain memory blocks “1 2 3 4” after access to the first four memory blocks.","answer_label":"1 5 2 3","answer_id":24470},{"id":6065,"question":"Which of the following appropriately describes the purpose of the cache memory used by processors?","answer_label":"To compensate for the difference between the main memory access speed and the processor speed","answer_id":24473},{"id":6066,"question":"Which of the following appropriately describes “memory interleaving” that is one of the high-speed computer technologies?","answer_label":"It is a method for dividing the memory into multiple independently-operating groups and accessing each group in parallel.","answer_id":24478},{"id":6067,"question":"How many tracks are required to store a sequentially organized data file including a total of 10,000 records on the hard disk drive under the following conditions? Here, each track can contain multiple blocks, but each block cannot be stored across multiple tracks.\n\n[Conditions]\n\nRecord length: 300 bytes/record\n\nTrack capacity: 30,000 bytes/track\n\nInter-block gap: 400 bytes\n\nBlocking factor: 20 records/block","answer_label":"125","answer_id":24484},{"id":6068,"question":"The head of a hard disk drive is currently positioned at cylinder number 100, and the cylinder numbers 120, 90, 70, 80, 140, 110, and 60 are lined up in the I/O request queue. What is the total number of cylinders that the head moves under the following conditions?\n\n[Conditions]\n\n(1) The seek optimization method reorders the I/O requests so that the head can move as much as possible in a single direction, and the requests are processed in order of cylinder number.\n\n(2) The requests so far are in the direction where the cylinder numbers increase.\n\n(3) When there are no more requests in the current direction, the direction of head movement is reversed.\n\n(4) The results are unaffected by the processing order of the requests.\n\n(5) New requests do not occur during the process.","answer_label":"120","answer_id":24486},{"id":6069,"question":"Which of the following technologies is used to divide each data file into blocks at constant length and to store them across multiple hard disks that can be accessed in parallel, thereby speeding up file access?","answer_label":"Disk striping","answer_id":24492},{"id":6070,"question":"Which of the following appropriately describes a method of recording data on CD-R?","answer_label":"Laser beams are radiated onto an organic dye layer in a disk. As a result, a series of burned spots called pits are created on that layer, thereby recording the data.","answer_id":24495},{"id":6071,"question":"Which of the following is a method whereby the relevant program is read into main memory and the CPU reads out and executes it sequentially?","answer_label":"Stored program method","answer_id":24500},{"id":6072,"question":"Which of the following functions is a part of OS task management?","answer_label":"CPU allocation","answer_id":24502},{"id":6073,"question":"When variables shared among tasks are updated, an unexpected result may occur if synchronous control among tasks is not performed. When the initial value of the variable x shared among tasks is 3, the final value of x is expected to be 12 if task A executes the assignment statement “x = x + x” and if task B executes the assignment statement “x = x × x.” Which of the following is the appropriate execution sequence that can return the expected result? Here, each assignment statement is executed by being divided into four portions as shown below.\n","answer_label":"a1 → b1 → b2 → b3 → b4 → a2 → a3 → a4","answer_id":24507},{"id":6074,"question":"Which of the following has the feature whereby only minimally limited OS functions, such as memory management and process management, are supported and other OS functions, such as the file system, are implemented as server processes?","answer_label":"Microkernel","answer_id":24510},{"id":6075,"question":"Which of the following is the appropriate statement concerning client/server architecture?","answer_label":"It divides a series of processes into two groups by means of an inter-process communication mechanism; one group includes processes that request services, and the other consists of processes that execute the requested services.","answer_id":24514},{"id":6076,"question":"Which of the following is the primary purpose to use RAID?","answer_label":"To ensure higher reliability and/or performance","answer_id":24519},{"id":6077,"question":"There is an RAID5 disk array system that is composed of 10 hard disk drives, and each disk capacity is 100Gbytes. What is the approximate maximum capacity (in Gbytes) that can be used to store user data and/or programs on this system?","answer_label":"900","answer_id":24524},{"id":6078,"question":"In some systems, the system manually or automatically determines memory blocks which are no longer referenced by a program and reorganizes the memory space so that it can be available for subsequent allocation. What is this process called?","answer_label":"Garbage collection","answer_id":24527},{"id":6079,"question":"Which of the following is the appropriate description concerning the performance evaluation of a computer system?","answer_label":"In the case of a system in operation, a software monitor can be used to collect and analyze statistical data, thereby permitting performance-related problems to be grasped.","answer_id":24532},{"id":6080,"question":"Which of the following appropriately describes a dual system?","answer_label":"Two systems perform the same processing, and the processed results are collated to confirm the correctness of the processing. If a fault occurs in either system, processing continues in degraded operation.","answer_id":24537},{"id":6081,"question":"When the operational model of a system is shown in the figure below, which of the following represents the correct combination of MTBF and MTTR of the system? Here, $t_i (i = 1, 2, …, n)$ denotes the operating time of the system, and $r_i (i = 1, 2, …, n)$ denotes the repair time of the system.\n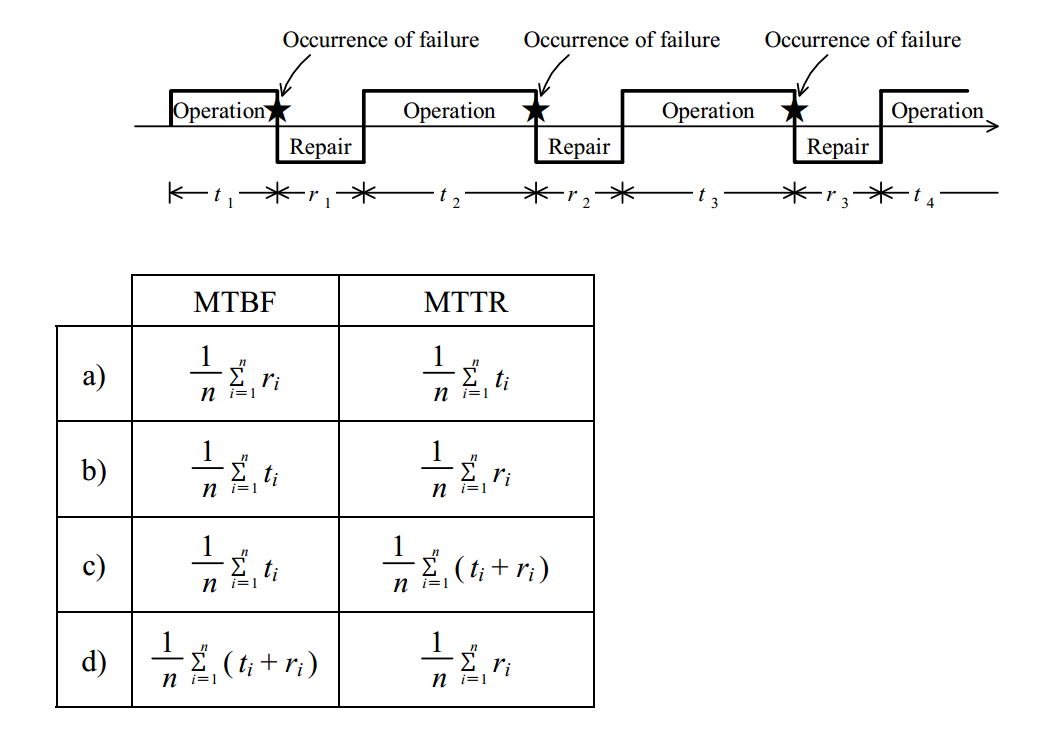","answer_label":"b","answer_id":24539},{"id":6082,"question":"Which of the following shows the system configuration that can operate with an overall system availability of $(1-(1-A)^2)^2$? Here, the element X is a processor with an availability of A. Also, the segment connected in parallel is considered operating if either of the two processors is operating. However, the segment connected in series is considered operating only when both processors are operating.\n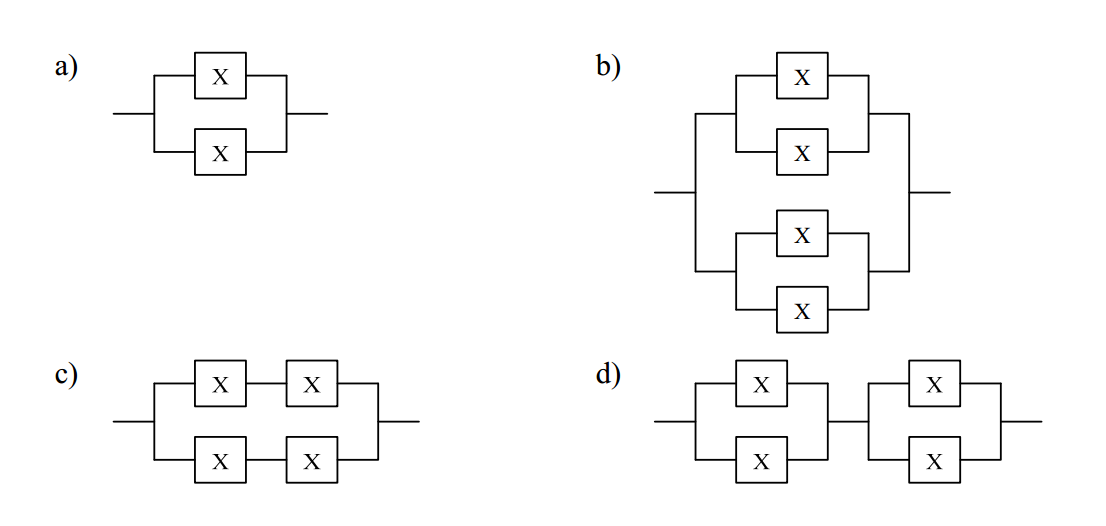","answer_label":"d","answer_id":24545},{"id":6083,"question":"In some circumstances, a program may be still running when it is called again by another program. Which of the following is the appropriate characteristic that should be implemented to execute this program correctly?","answer_label":"Reentrant","answer_id":24547},{"id":6084,"question":"Which of the following is the language processing program that generates, on a certain computer, object programs that can be executed on another computer that has a different instruction set?","answer_label":"Cross compiler","answer_id":24550},{"id":6085,"question":"Which of the following is the standardized document description language that prescribes methods, as an international standard, for describing the logical structures and attributes of documents using tags and facilitates the management and exchange of electronic documents?","answer_label":"SGML","answer_id":24556},{"id":6086,"question":"Which of the following is the appropriate combination of basic concepts of object-oriented approach?","answer_label":"Abstraction, encapsulation, inheritance, and class","answer_id":24558},{"id":6087,"question":"Which of the following is the appropriate characteristic of “data oriented design” as compared with “process oriented design?”","answer_label":"It is possible to consider data as shared resources and to manage it in a unified manner.","answer_id":24564},{"id":6088,"question":"Which of the following is the appropriate program that supports dynamic processing in a Web environment and runs only on a Web server?","answer_label":"Java servlet","answer_id":24568},{"id":6089,"question":"When the data model is represented to conform to the notational convention shown\nbelow, which of the following statements appropriately interprets the designated E-R\ndiagram?\n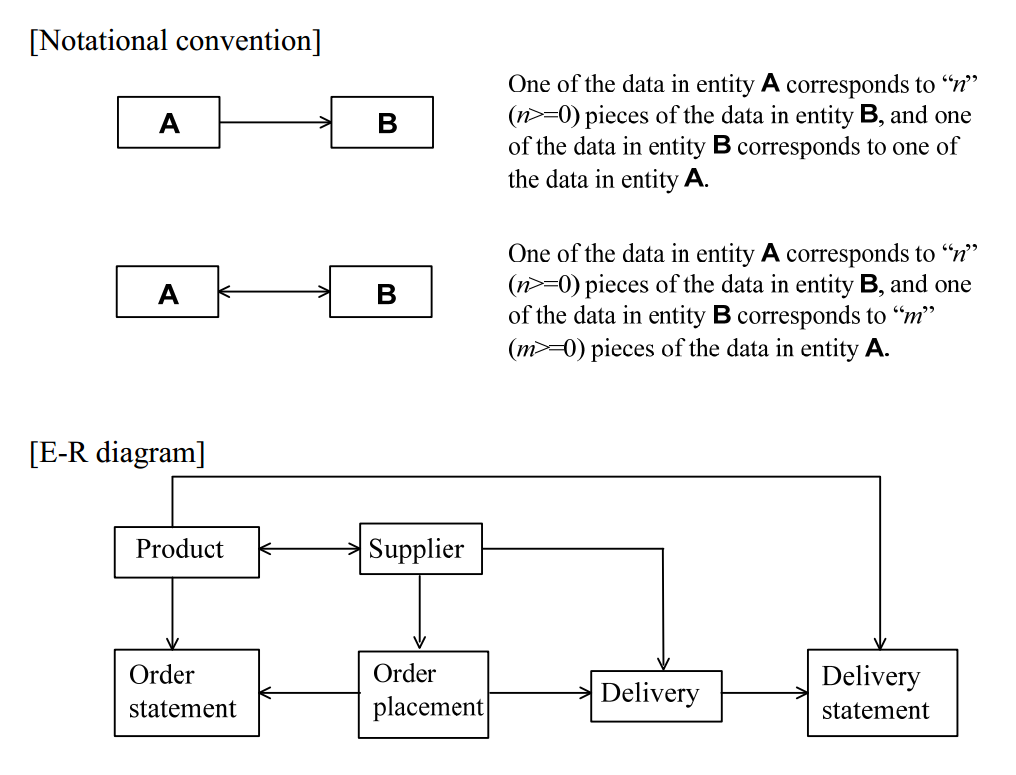","answer_label":"c) It does not occur that a single order placement is given to multiple suppliers.","answer_id":24572},{"id":6090,"question":"Which of the following design tasks is performed from the standpoint of the system developer, based on the deliverables of external design and in consideration of the implementation method and processing efficiency?","answer_label":"b) Functional decomposition and structured design","answer_id":24575},{"id":6091,"question":"Which of the following is the appropriate sequence of DB application development activities?","answer_label":"c) Database planning → Conceptual design → Physical design → Data conversion","answer_id":24580},{"id":6092,"question":"Which of the following is the appropriate statement concerning how to illustrate data flows (arrows) in DFD?","answer_label":"d) Each process must have at least one data flow in and one data flow out.","answer_id":24585},{"id":6093,"question":"Which of the following is the appropriate description concerning the functions of “driver” or “stub” used in the module test?","answer_label":"a) “Driver” calls the module to be tested while passing arguments to it.","answer_id":24586},{"id":6094,"question":"Which of the following is the appropriate description concerning black box testing?","answer_label":"b) Even if any redundant code exists in a tested program, it cannot be detected.","answer_id":24591},{"id":6095,"question":"Which of the following appropriately explains the function point method, which is one\nof the estimation methods used in system development?","answer_label":"It is a method for estimating the system size by evaluating system functions\r\nquantitatively on the basis of the amount of input/output data, the number of files,\r\netc. and by making proper adjustments based on the complexity and characteristics of\r\nthe application.","answer_id":24595},{"id":6096,"question":"Which of the following appropriately describes the purpose of using a check digit?","answer_label":"a) To detect an error of the inputted code value","answer_id":24598},{"id":6097,"question":"How many magnetic tapes are required to create and manage backup copies of server\nfiles under the following conditions?\n\n[Processing conditions]\n\n(1) A full backup copy is made at the beginning (on the first day) of each month. One\nmagnetic tape is required per full backup.\n\n(2) An incremental backup copy is made each day between the day following the day\nwhen a full backup copy is made and the day when the next full backup copy is made.\nAn incremental backup copy is added to a separate magnetic tape dedicated to\nincremental backups. All the incremental backup copies made during a one-month\nperiod can be recorded on a single magnetic tape.\n\n(3) It is guaranteed that any file can always be restored to the state of any specified day\nwith respect to any data for any day not earlier than this day six months ago. Here, if\nthis day of the month did not exist six months ago, it is guaranteed that any file can be\nrestored to the state of any specified day with respect to any data for any day not\nearlier than the last day six months ago. (For example, if the current day is October\n31, it is guaranteed that any file can be restored to the state of any specified day with\nrespect to any data for any day not earlier than April 30.)","answer_label":"14","answer_id":24604},{"id":6098,"question":"Which of the following subnet masks provides the minimum number of IP addresses available in the subnet to assign to devices that request a connection?","answer_label":"c) 255.255.255.252","answer_id":24608},{"id":6099,"question":"In the OSI basic reference model, which of the following layers provides a set of rules\r\nfor establishing and terminating the connection between applications on computer\r\nsystems?","answer_label":"Session layer","answer_id":24612},{"id":6100,"question":"Which of the following protocols is used on the transport layer of OSI basic reference\r\nmodel?","answer_label":"UDP","answer_id":24617},{"id":6101,"question":"Which of the following is the appropriate technology that is used to establish a private or\r\nsecure network connection within a public IP network, such as the Internet, and to give\r\nthe company the same capabilities at much lower cost by using the shared public\r\ninfrastructure rather than a private one?","answer_label":"VPN","answer_id":24621},{"id":6102,"question":"Which of the following IP addresses can be used to connect a computer directly to the\r\nInternet?","answer_label":"203.162.1.160","answer_id":24625},{"id":6103,"question":"Which of the following is the appropriate specifications concerning 100Base-T?\n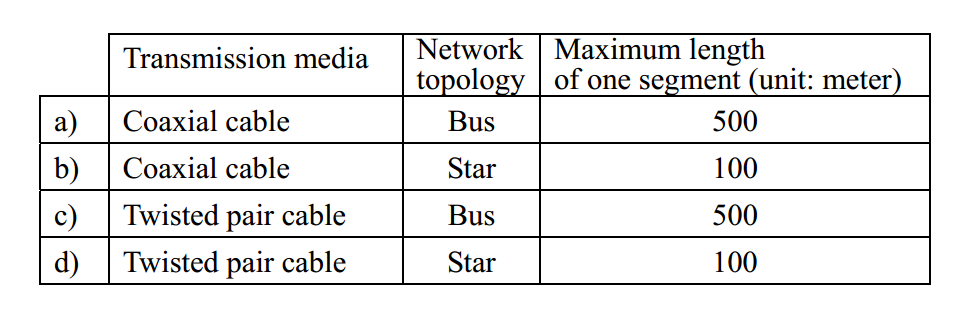","answer_label":"d","answer_id":24629},{"id":6104,"question":"Which of the following is the correct table that is created by the “natural join” operation\nof two tables $T_1$ and $T_2$?\n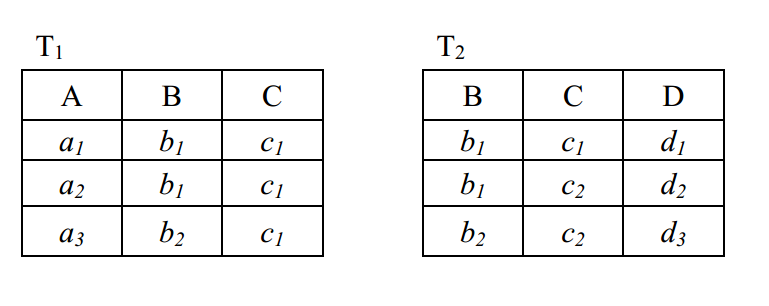\n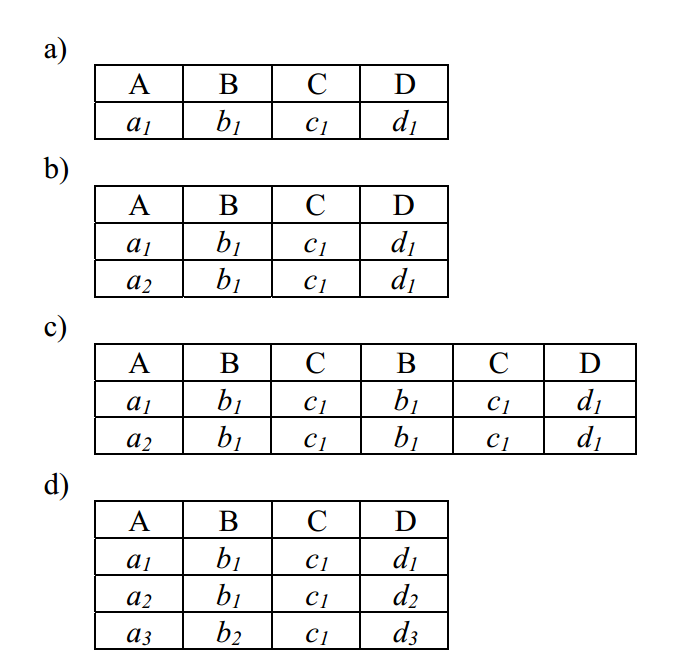","answer_label":"b","answer_id":24631},{"id":6105,"question":"Which of the following is the appropriate description of a lock that is the exclusive control of a database?","answer_label":"b) Locks come in two types: shared locks, used while reading, and exclusive locks, used during a change.","answer_id":24635},{"id":6106,"question":"In a database system employing incremental log with immediate updates, information in\nthe log is used in restoring the state of the system to a previous consistent state when a\ncrash occurs. A log record is generated upon execution of a write operation. Each\nlog record consists of the transaction name $T_i$, the data item name, the old value of the\ndata item, and the new value of the data item. The log record shown below is the normal\ntransaction sequence after the last checkpoint. Which of the following recovery\nactions should be performed after a restart of the system if a crash occurs just after <\n$T_2$ , C, 3000, 3500> and before < $T_2$ , commit>?\n\n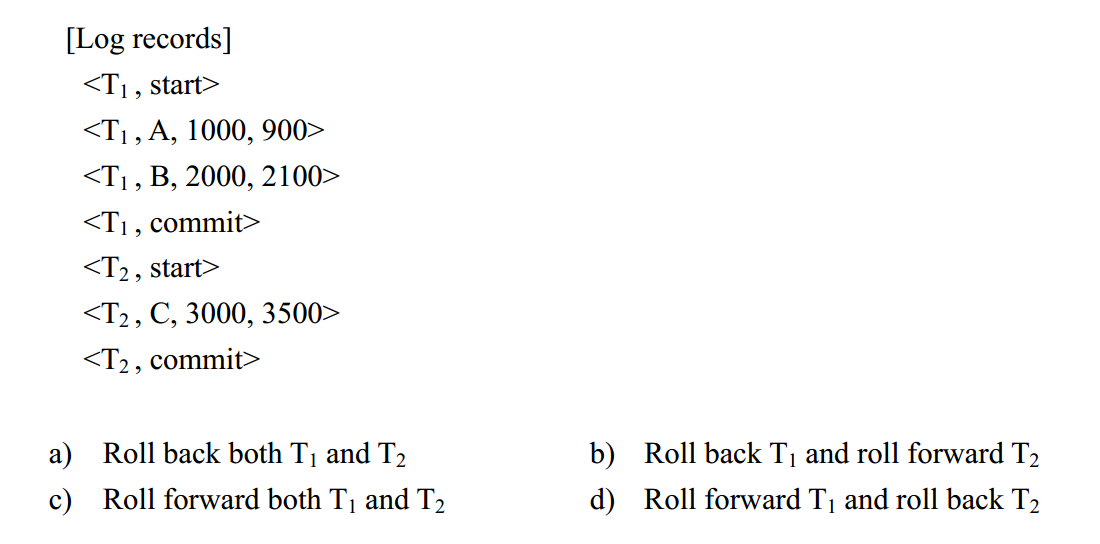","answer_label":"d","answer_id":24641},{"id":6107,"question":"Which of the following is the appropriate SQL statement that is used to create Table A\nfrom Persons Table?\n\n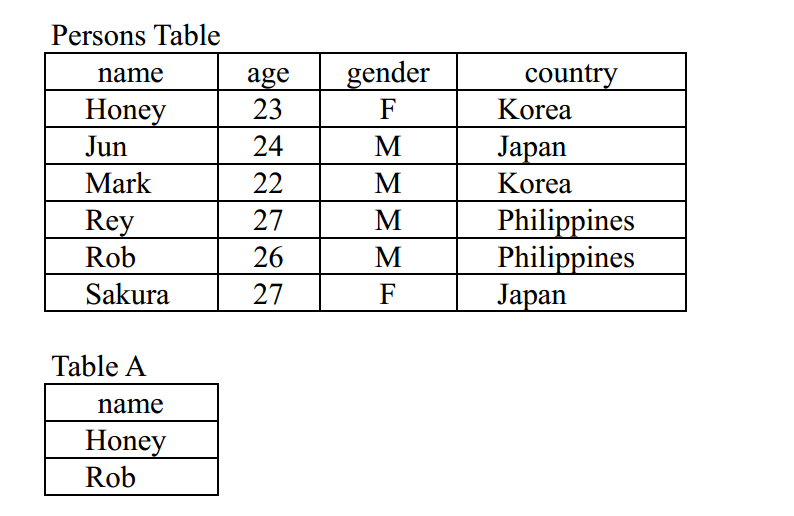","answer_label":"SELECT name FROM Persons WHERE country LIKE '%Korea%'\r\nAND gender = 'F' OR age = 26","answer_id":24643},{"id":6108,"question":"Which of the following is the major impact of a Denial of Service (DoS) attack?","answer_label":"Degradation of service due to network traffic congestion","answer_id":24647},{"id":6109,"question":"Which of the following is the appropriate method that supports both private key\r\ncryptography and public key cryptography, enables users to securely exchange e-mail\r\nmessages, and to secure files, disk volumes, and network connections with both privacy\r\nand strong authentication?","answer_label":"PGP (Pretty Good Privacy)","answer_id":24652},{"id":6110,"question":"Port scanning is the process of sending packets to check every port on each target system\r\nto see which ports are open and which ports are locked. Which of the following\r\ninformation can be identified by port scanning?","answer_label":"Network and application services currently available","answer_id":24656},{"id":6111,"question":"Which of the following appropriately explains benchmarking used in business\r\nmanagement?","answer_label":"It is to make comparisons with the strongest competitors or advanced companies in\r\norder to scope out best practices for setting business goals, and to gain an\r\nunderstanding of products, services, and practical methods qualitatively and\r\nquantitatively.","answer_id":24658},{"id":6112,"question":"Which of the following appropriately describes a cause-and-effect diagram?","answer_label":"It systematically arranges the relation between cause and effect in a fishbone format\r\nand clarifies which causes are related to particular effects.","answer_id":24665},{"id":6113,"question":"Which of the following is the appropriate statement concerning how to use management\r\nscience methodology?","answer_label":"The time-series analysis method is used to forecast product sales in the market.","answer_id":24669},{"id":6114,"question":"The selling price per unit of product Z is set to $250, and sales for the coming year are expected to be 500 units. If the company requires a return of 15% in the coming year on its investment of $250,000 in product Z, what is the target variable cost per unit for the coming year? Here, the fixed cost is $10,000 per annum.","answer_label":"$155","answer_id":24671},{"id":6115,"question":"When the moving average method is applied to the receipt/shipment ledger shown\nbelow, how much in dollars is the closing inventory value of August?\n\n","answer_label":"1300","answer_id":24676},{"id":6116,"question":"In a production process of 1,000 units of product X, “material cost” incurred is $10,000,\r\nand “direct labor cost” is $20,000. “Production overhead” is 100% of direct labor cost.\r\n“Selling and distribution cost” is $10,000. How much in dollars is the unit cost of\r\nproduct X?","answer_label":"50","answer_id":24680},{"id":6117,"question":"The following table shows the duration for the optimistic, most likely, and pessimistic\r\nscenarios in a program development. How many hours are required to complete all the\r\nactivities on a “three point estimate” basis?\n\n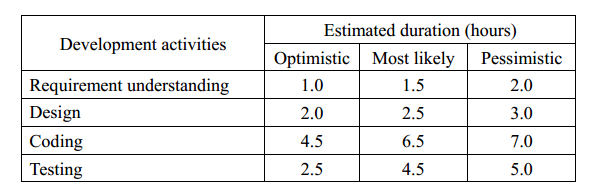","answer_label":"14.5","answer_id":24683},{"id":6118,"question":"Which of the following is the appropriate combination of processing modes in banking\nactivities?\n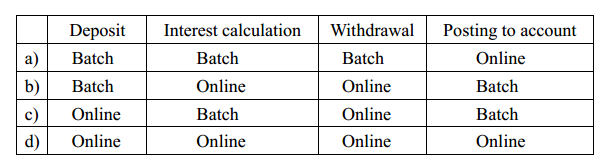","answer_label":"c","answer_id":24688},{"id":6119,"question":"In an online transaction system environment, which of the following represents the interval of time from the time the system completes receipt of an input to the time the system begins to return its resulting output?","answer_label":"Response time","answer_id":24692},{"id":6120,"question":"Which of the following is the most appropriate set of major functions supported by an OS?","answer_label":"Data management, job management, and task management","answer_id":24695},{"id":6121,"question":"Multiple directories having the names “A” and “B” are managed in the structure shown below.\n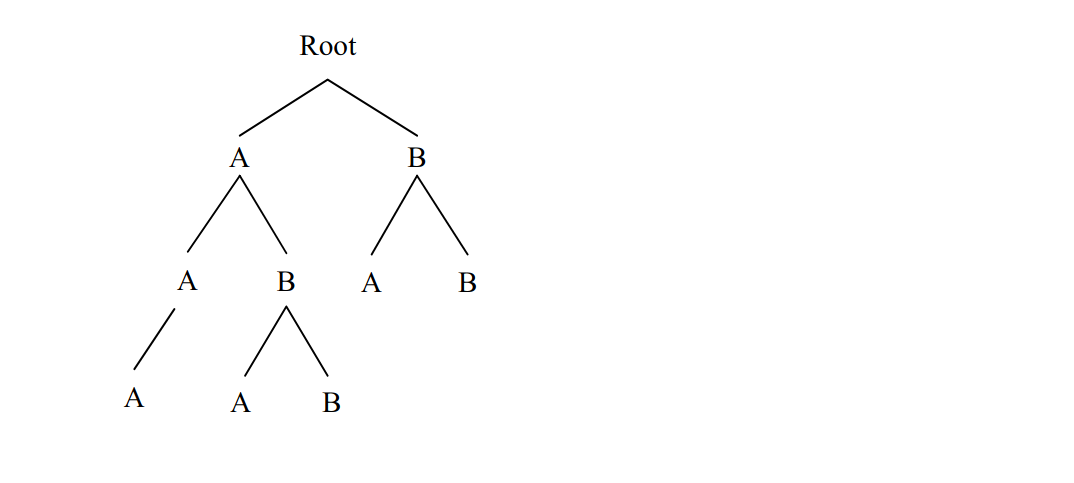\nWhen the current directory is changed in order of “\\A\\B → .. → ..\\B → .\\A”, which of the following is the resulting current directory? Here, directories are specified as follows: \n[Methods to specify directories] \n(1) A directory is referenced as “directory name\\···\\directory name”, where the directories on the path are listed and separated with “\\” (backslash) in sequence, followed by “\\”and the directory name.\n(2) The current directory is represented by “.” (one period). \n(3)The directory one level above is represented by “..” (two periods). \n(4) When a reference begins with “\\”, it is assumed that the root directory is omitted from the beginning of the reference.\n(5) When a reference does not start with “\\”, “.”, or “..”, it is assumed that “.\\”, which means that the reference is under the current directory, is omitted from the beginning of the reference.","answer_label":"\\B\\A","answer_id":24701},{"id":6122,"question":"There are some methods of getting backup files for the purpose of recovering files and managing generations. Which of the following is an appropriate description concerning those methods or procedures?","answer_label":"A differential backup contains all files changed after the last full backup, while an incremental backup saves all files changed after the last full, differential, or incremental backup.","answer_id":24702},{"id":6123,"question":"Which of the following circuits can write out “1” to the output line Z only when the input lines X and Y have the same value?\n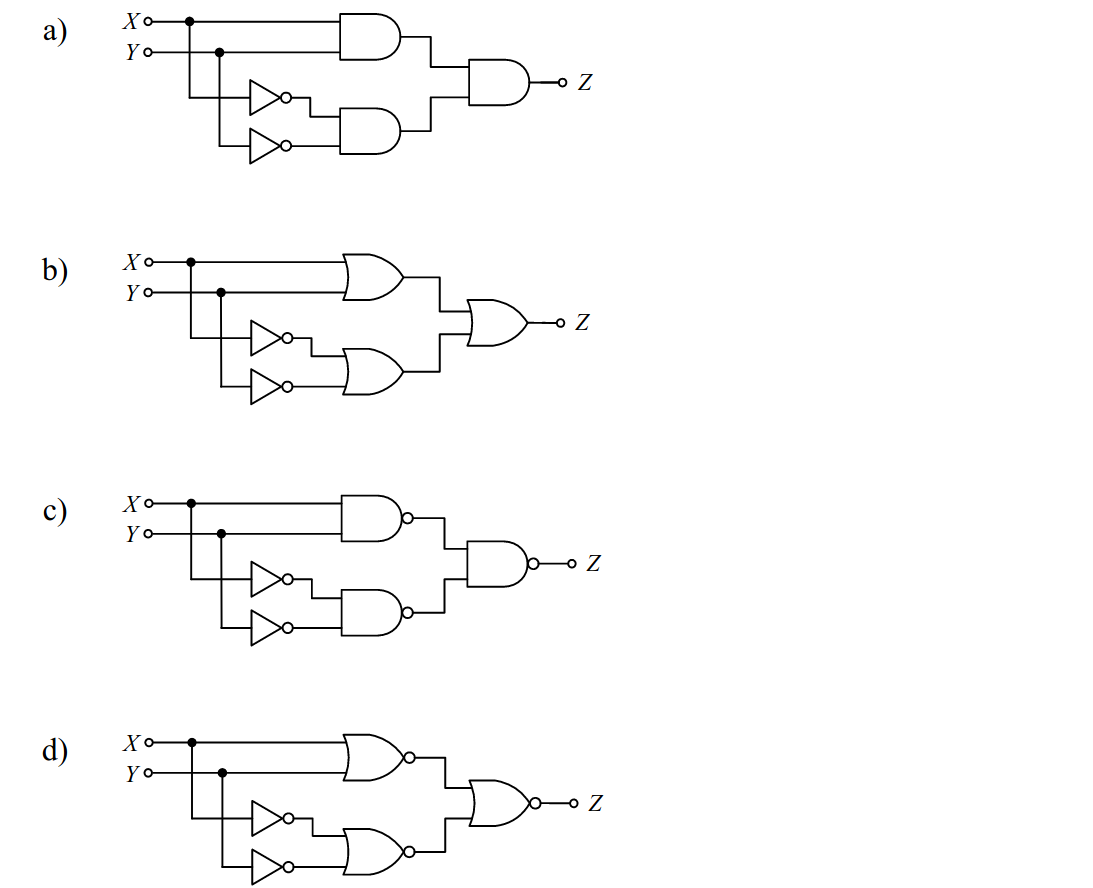","answer_label":"c","answer_id":24708},{"id":6124,"question":"The figure below shows a logic circuit representing a full adder. When 1, 0, and 1 are entered into x, y, and z respectively, which of the following is the appropriate combination of the output values of c (carry) and s (sum)?\n","answer_label":"c","answer_id":24712},{"id":6125,"question":"Which of the following is an appropriate explanation of SoC (System on a Chip)?","answer_label":"A semiconductor chip in which all required functions (systems) are integrated in the same manufacturing process","answer_id":24715},{"id":6126,"question":"Which of the following is a user interface that enables frequently-used operations to be performed efficiently?","answer_label":"Shortcut key","answer_id":24720},{"id":6127,"question":"Which of the following is the data model that was originally introduced for the purpose of conceptual modeling and is often used for logical modeling and physical modeling as well as conceptual modeling?","answer_label":"E-R model","answer_id":24722},{"id":6128,"question":"The figure below shows the relationships among data items used in a certain parts management system. When the system is implemented as a relational database, which of the following is the most appropriate and effective table structure of the relational database?\n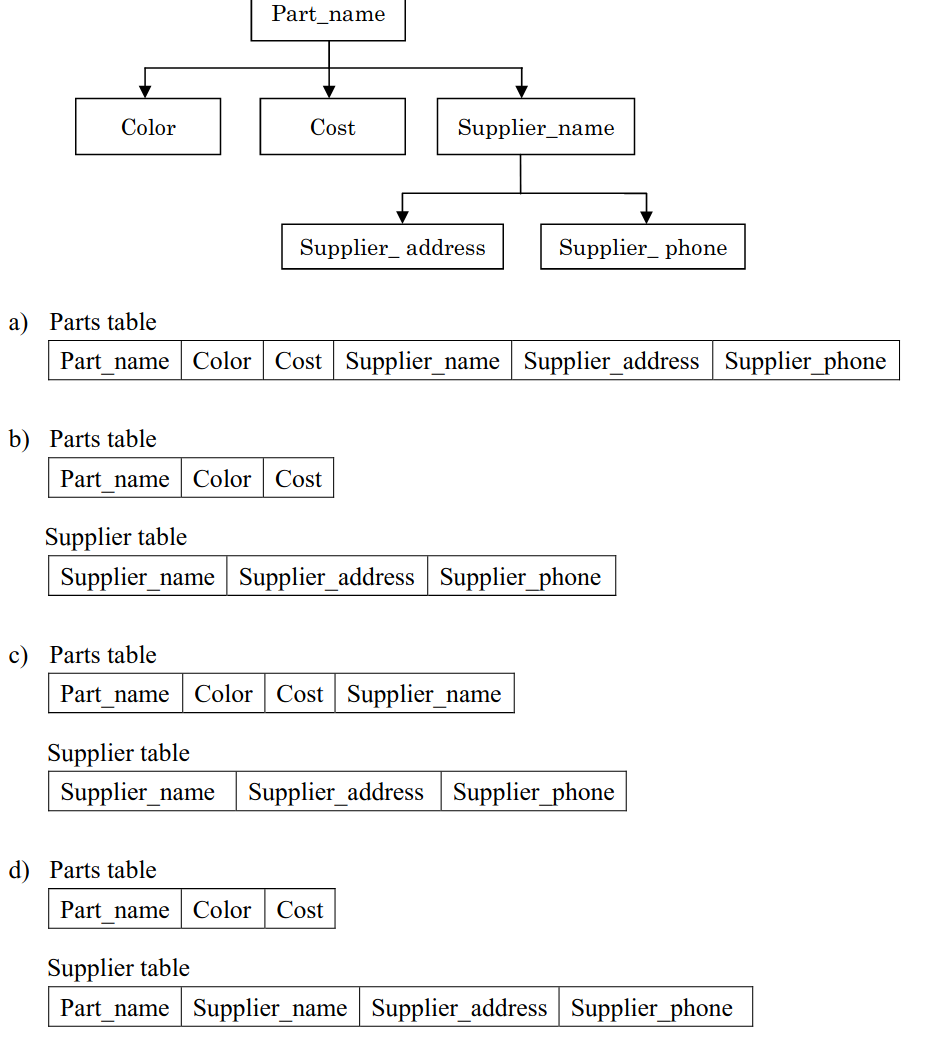","answer_label":"c","answer_id":24728},{"id":6129,"question":"As shown below, there are two relational database tables Movie and Actor. Which of the following SQL statements should be used for retrieving a list of movie titles, released years, and directors, from all the movies that include “Action” or “Comedy” as a genre and “Cooper” as an actor’s name? Here, there is no movie remade with different actors, so “Title” and “Movie_title” are both primary keys in each table. \n\nMovie (Released_year, Title, Director, Genre, Description) \nActor (Name, Movie_title, Role)\n\n","answer_label":"a","answer_id":24730},{"id":6130,"question":"As shown below, there are four relational database tables Product, Supplier, Sale, and Employee that are used for a database system in a retail store. Here, the solid and dotted lines indicate the primary and foreign keys, respectively. \n","answer_label":"10,000","answer_id":24735},{"id":6131,"question":"As shown in the table below, there are five transactions T1 through T5 that are performed simultaneously in parallel, in any order. Which of the following is the combination of transactions that has the possibility of a deadlock? Here, only one transaction can have an exclusive lock at a time. Shared locks can be used with multiple transactions.\n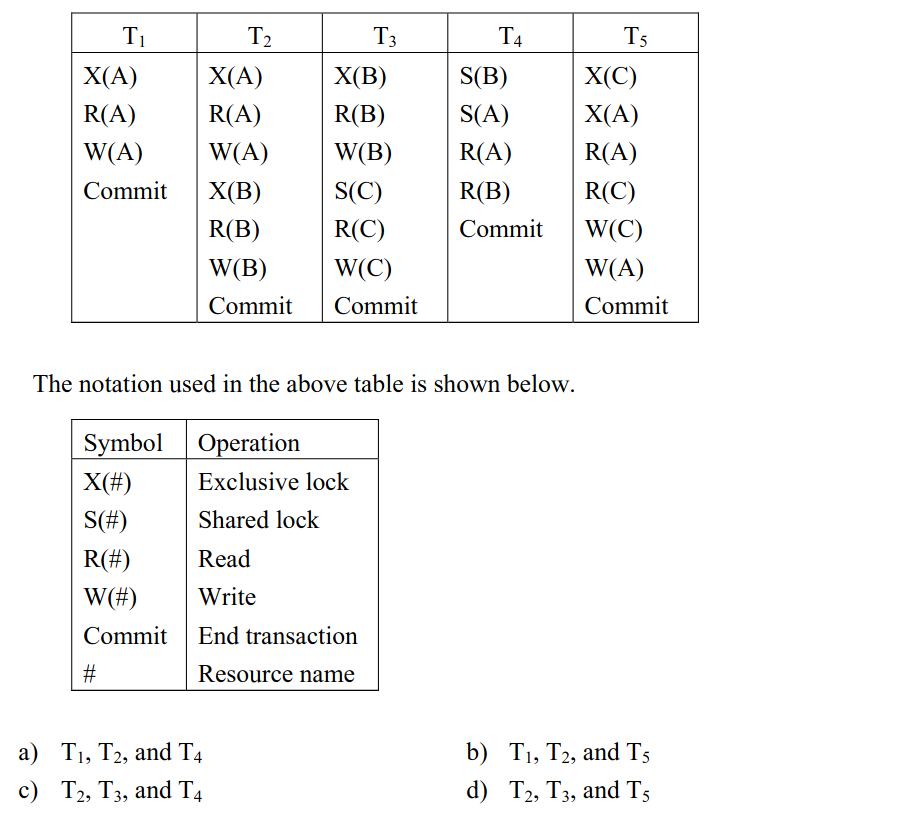","answer_label":"d","answer_id":24741},{"id":6132,"question":"Which of the following explains the database rollback process?","answer_label":"The “undo journal” is used to restore the data to the status immediately before the start of the transaction.","answer_id":24745},{"id":6133,"question":"Which of the following information in IP header is used for routing the IP packets across networks?","answer_label":"Destination address field","answer_id":24747},{"id":6134,"question":"Which of the following network topologies is commonly used, especially in Fast or Gigabit Ethernet, for connecting network devices via a centralized unit such as a hub or a switch?","answer_label":"Star","answer_id":24753},{"id":6135,"question":"What is the minimum number of communication cables that are needed to connect six network devices in a full mesh topology? Here, at least one communication cable is required to connect two network devices.","answer_label":"15","answer_id":24757},{"id":6136,"question":"Which of the following is the IP network addressing and routing scheme whereby data is routed to the “nearest” or “best” destination as viewed by the routing topology?","answer_label":"Anycast","answer_id":24758},{"id":6137,"question":"Which of the following protocols can be used to access e-mail messages that are stored on a remote, and possibly shared, mail server, and thereby are manipulated from a desktop computer at home, a workstation at the office, and a notebook computer while traveling, without the need to transfer messages back and forth between these computers?","answer_label":"IMAP","answer_id":24763},{"id":6138,"question":"When a message is sent to Person A from Person B using public key cryptography, which of the following keys should be used for encrypting the message?","answer_label":"A’s public key","answer_id":24767},{"id":6139,"question":"Which of the following is the function of S/MIME used for e-mails?","answer_label":"Encrypting e-mails and attaching a signature","answer_id":24771},{"id":6140,"question":"Which of the following can be achieved by using SSL/TLS?","answer_label":"Communication between clients and servers is encrypted.","answer_id":24774},{"id":6141,"question":"Which of the following refers to online scams where thieves attempt to entice e-mail recipients into clicking on a link that takes them to a bogus website, and the website may prompt the recipient to provide personal information such as social security number, bank account number, and credit card number, and/or it may download malicious software onto the recipient’s computer?","answer_label":"Phishing","answer_id":24780},{"id":6142,"question":"A government website accepts passport applications using HTTP forms to collect information. Users provide complete personal information in the forms to help expedite processing of face-to-face transactions, and payments are done offline. The information collected enters a secure server for processing and document releasing. In this system environment, which of the following is the most likely security attack?","answer_label":"Sniffing trafficfor identity theft","answer_id":24783},{"id":6143,"question":"Which of the following explains the pattern matching method that is used by antivirus software?","answer_label":"Viruses are detected by comparison with the signature codes of known viruses.","answer_id":24788},{"id":6144,"question":"The diagram shown below depicts who can use the system and in what ways the users (or external systems) expect to interact with the system. What is this type of diagram called?\n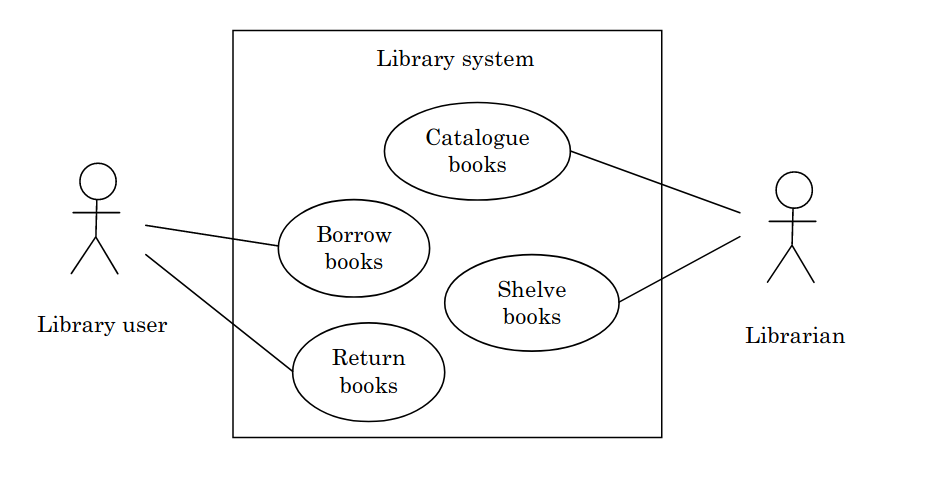","answer_label":"Use case diagram","answer_id":24793},{"id":6145,"question":"Which of the following is an appropriate combination of the fundamental object-oriented concepts?","answer_label":"Abstraction, encapsulation, inheritance, class","answer_id":24794},{"id":6146,"question":"In software development, it is a good practice to develop highly independent modules. When module independence depends primarily on two measures, module strength (or cohesion) and module coupling, which of the following is the appropriate combination of good programming practices?\n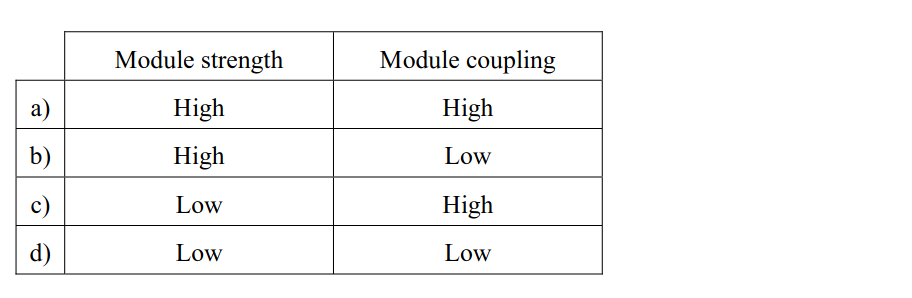","answer_label":"b","answer_id":24799},{"id":6147,"question":"As shown in the figure below, all the lines show signs of leveling off in the control chart of a program test. Which of the following can be inferred from this condition?\n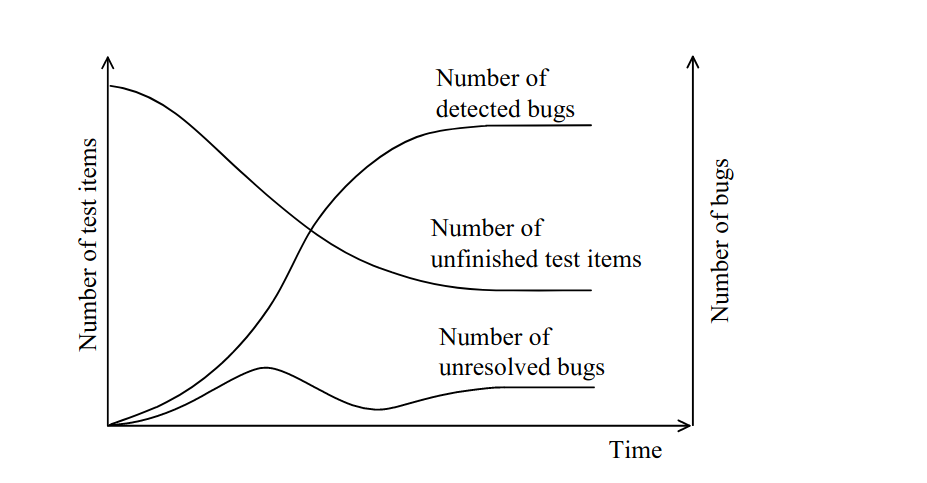","answer_label":"The process is facing some bugs that are difficult to resolve, and subsequent tests are not proceeding.","answer_id":24805},{"id":6148,"question":"Which of the following is the test that is performed to ensure that the components and modulesof a system can communicate with one another in accordance with the functional specifications and design?","answer_label":"Integration test","answer_id":24806},{"id":6149,"question":"Which of the following is the software development process model that incorporates the best features of both the classic lifecycle and the prototyping approaches, by beginning each repeated development cycle with extensive risk analysis throughout the entire software development life cycle for large-scale applications?","answer_label":"Spiral model","answer_id":24812},{"id":6150,"question":"Which of the following is an appropriate description concerning the maturity level in the staged representation of CMMI?","answer_label":"At the “managed” level, processes are documented and followed.","answer_id":24816},{"id":6151,"question":"Which of the following is the project management tool whereby the project activities and their relationships can be graphically represented, and the project manager can understand how the various activities flow towards completion in order of time?","answer_label":"Network diagram","answer_id":24819},{"id":6152,"question":"A painter has 20 houses and 4 shops to paint. In comparison with the shop, the house usually takes half the time to paint. The painter has finished painting 10 houses in 3 days. If the painter continues to work at the same pace, how many days does it take to complete the remaining work?","answer_label":"5.4","answer_id":24824},{"id":6153,"question":"Which of the following is the appropriate element that is used to calculate slack time in the PERT (Program Evaluation and Review Technique)?","answer_label":"The earliest of the latest start times of the successor activities","answer_id":24827},{"id":6154,"question":"Which of the following is the method used for estimating the scales or person-months in system development where the five basic components—external input, external output, internal logical file, external interface file, and external inquiry—are defined and classified with their complexity weights?","answer_label":"Function point method","answer_id":24831},{"id":6155,"question":"Which of the following is the risk response which accepts the cost of damages because risk impact is assumed to be small when the risk becomes exposed?","answer_label":"Risk retention","answer_id":24836},{"id":6156,"question":"Which of the following is an appropriate characteristic of the single-step (so-called “big bang”) migration method?","answer_label":"Problems during migration to the new system have serious impacts.","answer_id":24840},{"id":6157,"question":"From a viewpoint of reliability of systems, which of the following is the appropriate timing for measuring the availability of a system?","answer_label":"When the problems found immediately after the start of system operations have been resolved and the system is becoming stable","answer_id":24845},{"id":6158,"question":"When a company is notified of the necessity of upgrading the version for the server OS on which a database system and business application are running, which of the following is an appropriate decision on whether or not to upgrade the OS?","answer_label":"The company checks if the database system runs without problem in the new OS environment, and then checks the operation of the business application. If there is no problem, the company upgrades the OS.","answer_id":24847},{"id":6159,"question":"Which of the following is an effective measure to protect information systems from overvoltage caused by lightning?","answer_label":"Connecting communication cables to computers via SPD (Surge Protection Device)","answer_id":24850},{"id":6160,"question":"Which of the following is an appropriate responsibility of a system auditor for problems found during an audit?","answer_label":"Reporting the problems found to the audit requester","answer_id":24856},{"id":6161,"question":"Which of the following is an explanation of ERP?","answer_label":"It is the technique and concept for improvement in management efficiency by planning and controlling the company-wide management resources in an effective and integrated way.","answer_id":24858},{"id":6162,"question":"Which of the following is an explanation of BPR?","answer_label":"Redesigning the business processes from a customer perspective, by making full use of information technology to radically change the characteristics and structure of the company","answer_id":24864},{"id":6163,"question":"Which of the following is the service provided by ASPs?","answer_label":"Services to provide a variety of functions of a general-purpose application system to multiple customers over a network","answer_id":24868},{"id":6164,"question":"Which of the following is an activity concerning a model of business operations developed during the overall planning of information systems?","answer_label":"Associating business processes with data classes","answer_id":24870},{"id":6165,"question":"Which of the following is an explanation of digital divide?","answer_label":"It refers to economic or social disparities caused by differences in capabilities or opportunities to use PCs and telecommunications.","answer_id":24877},{"id":6166,"question":"Which of the following describes characteristics of the growth stage of the product life cycle?","answer_label":"The market begins to understand the value of the product. The company needs to expand its product lines and distribution channels. During this stage, sales increase but more investment is required.","answer_id":24881},{"id":6167,"question":"Which of the following is a mechanism used in electronic commerce to exchange data between companies?","answer_label":"EDI","answer_id":24883},{"id":6168,"question":"Which of the following is the most appropriate position that is primarily responsible for centralized oversight of enterprise IT strategic planning?","answer_label":"CIO (Chief Information Officer)","answer_id":24888},{"id":6169,"question":"When the relationship between the value “x” of a certain factor in manufacturing a product and the value “y” of a quality characteristic for the product is plotted in a chart, which of the following charts has the positive correlation coefficient between x and y?\n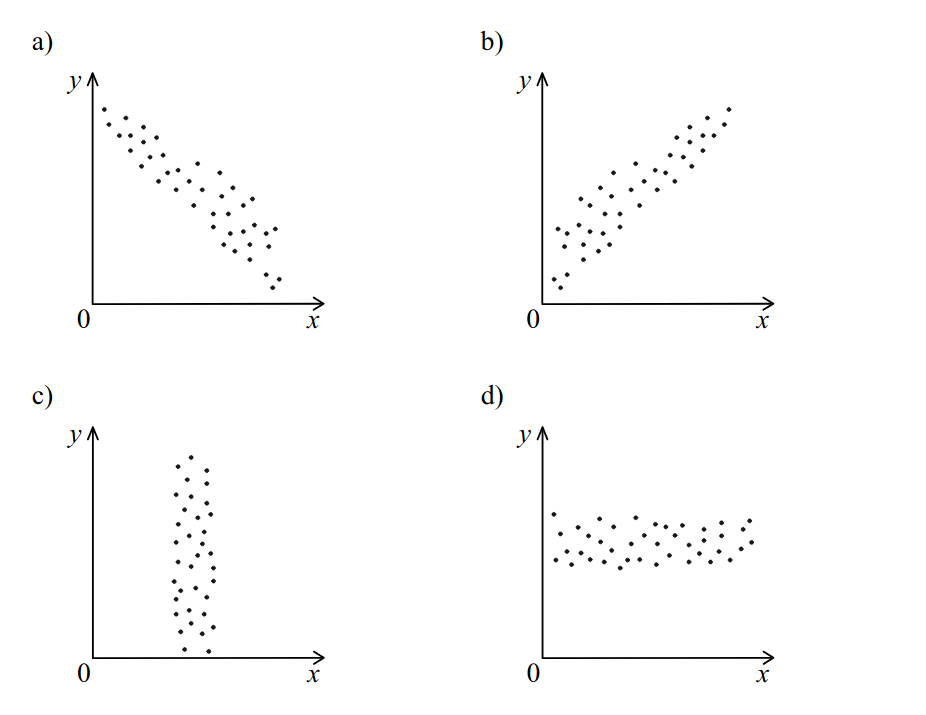","answer_label":"b","answer_id":24891},{"id":6170,"question":"When ABC analysis is used to categorize product items in the table below, which of the following is the combination of the product numbers for the items that are categorized into the group “A”?\n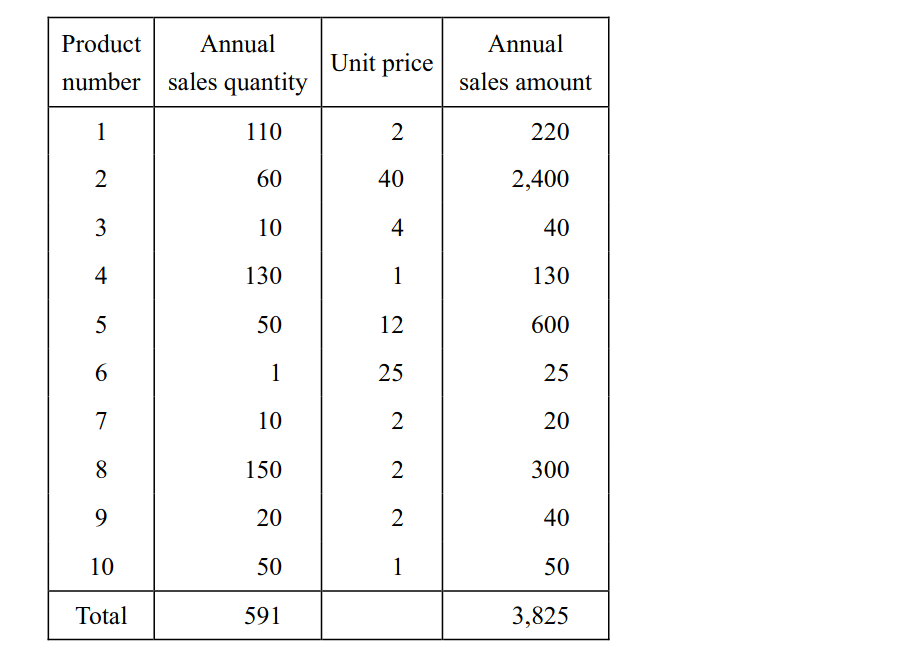","answer_label":"2 and 5","answer_id":24895},{"id":6171,"question":"When the relationship between the list price and expected demand of a product can be expressed by a linear expression, which of the following is the appropriate value to be inserted in the blank A?\n(1) When the list price is set to 30 dollars, the quantity demanded is 0.\n(2) When the list price is set to 10 dollars, the quantity demanded is 60,000.\n(3) When the list price is set to 15 dollars, the quantity demanded is $\\boxed{A}$.","answer_label":"45,000","answer_id":24901},{"id":6172,"question":"Which of the following is an appropriate description concerning financial indicators?","answer_label":"The total capital profit ratio is the ratio of profit to gross capital. As the value is larger, profitability is higher.","answer_id":24905},{"id":6173,"question":"The table below shows records of purchase and withdrawal for a component. When the first-in first-out method is applied, which of the following is the unit price of the withdrawal on April 10?\n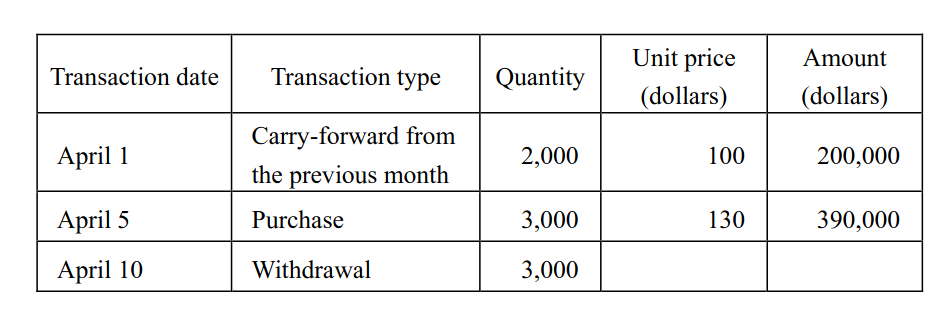","answer_label":"110","answer_id":24907},{"id":6174,"question":"Which of the following is a law that protects coded expressions of programs rather than ideas or algorithms in programs?","answer_label":"Copyright law","answer_id":24910},{"id":6175,"question":"Which of the following sets of standards should be applied for the purpose of developing the new products that are expected to be employed by government agencies of countries who are members of the WTO?","answer_label":"ISO standards","answer_id":24917},{"id":6291,"question":"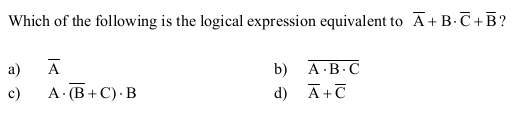","answer_label":"b","answer_id":25316},{"id":6294,"question":"","answer_label":"2","answer_id":25327},{"id":6296,"question":"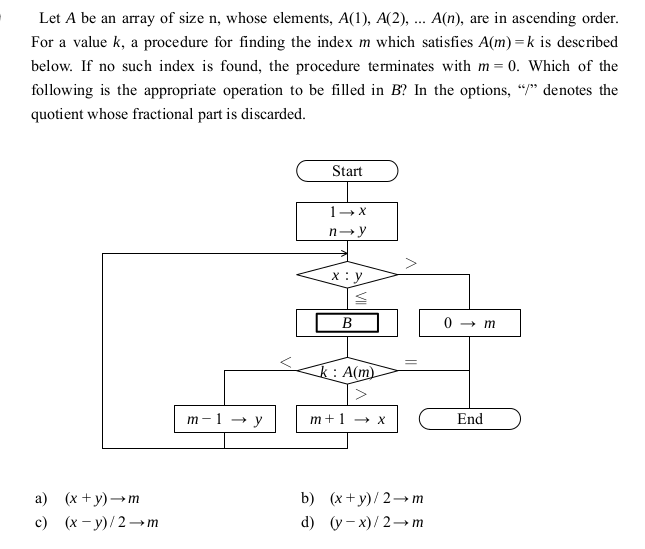","answer_label":"b","answer_id":25334},{"id":6297,"question":"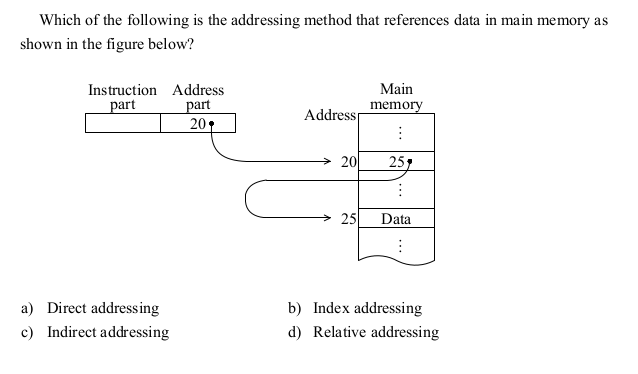","answer_label":"c","answer_id":25339},{"id":6298,"question":"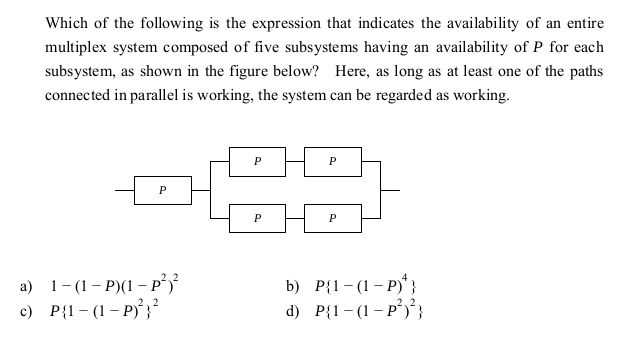","answer_label":"d","answer_id":25344},{"id":6299,"question":"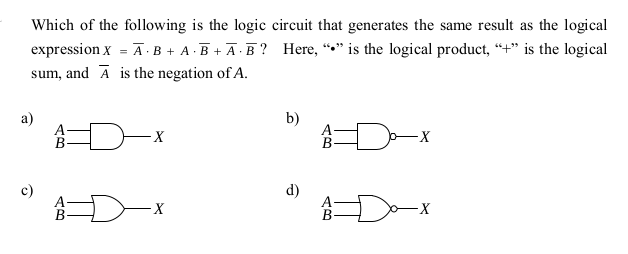","answer_label":"b","answer_id":25346},{"id":6300,"question":"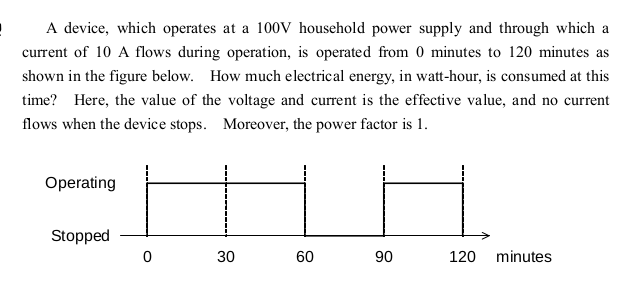","answer_label":"1,500","answer_id":25351},{"id":6302,"question":"","answer_label":"B","answer_id":25356},{"id":6303,"question":"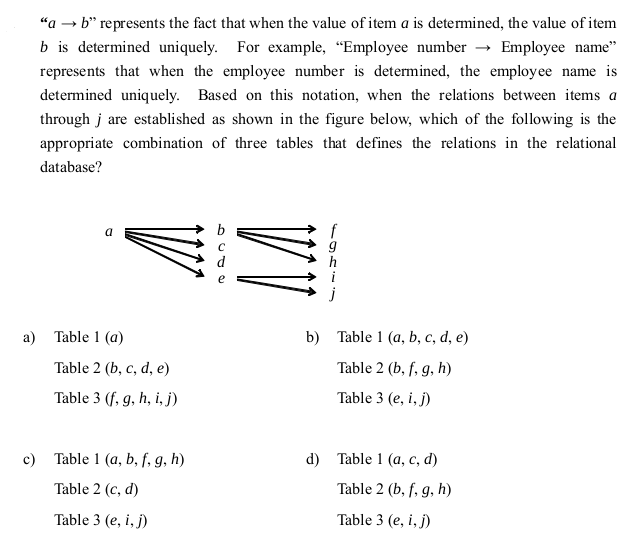","answer_label":"b","answer_id":25360},{"id":6305,"question":"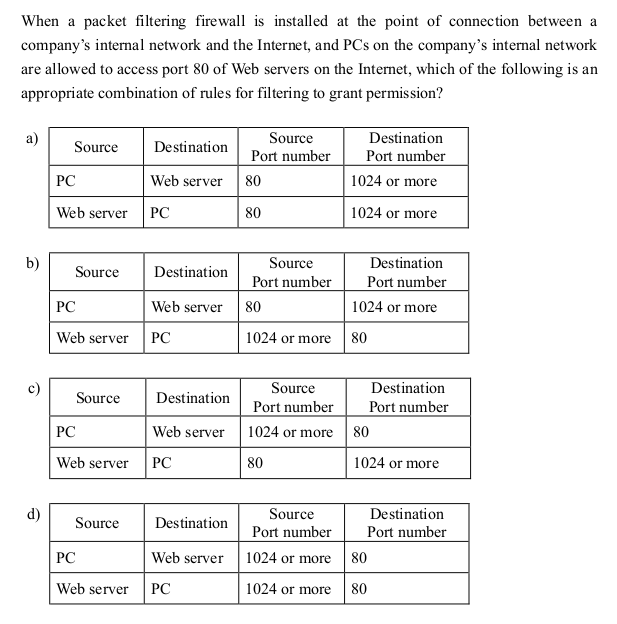","answer_label":"c","answer_id":25367},{"id":6306,"question":"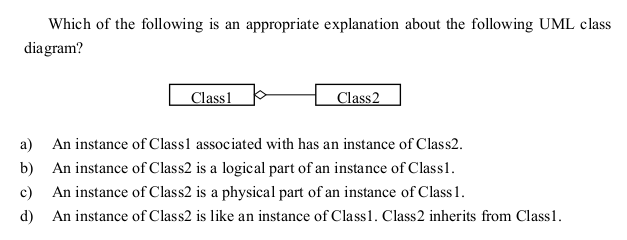","answer_label":"b","answer_id":25370},{"id":6308,"question":"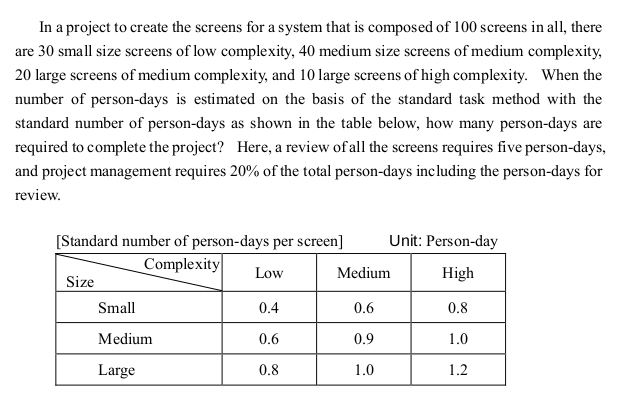","answer_label":"102","answer_id":25379},{"id":6310,"question":"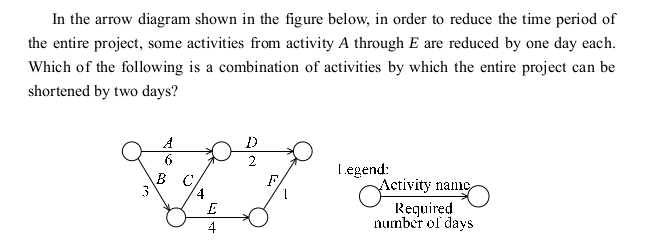","answer_label":"B, D","answer_id":25390},{"id":6313,"question":"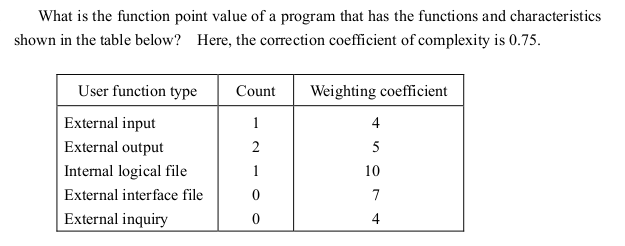","answer_label":"18","answer_id":25399},{"id":6315,"question":"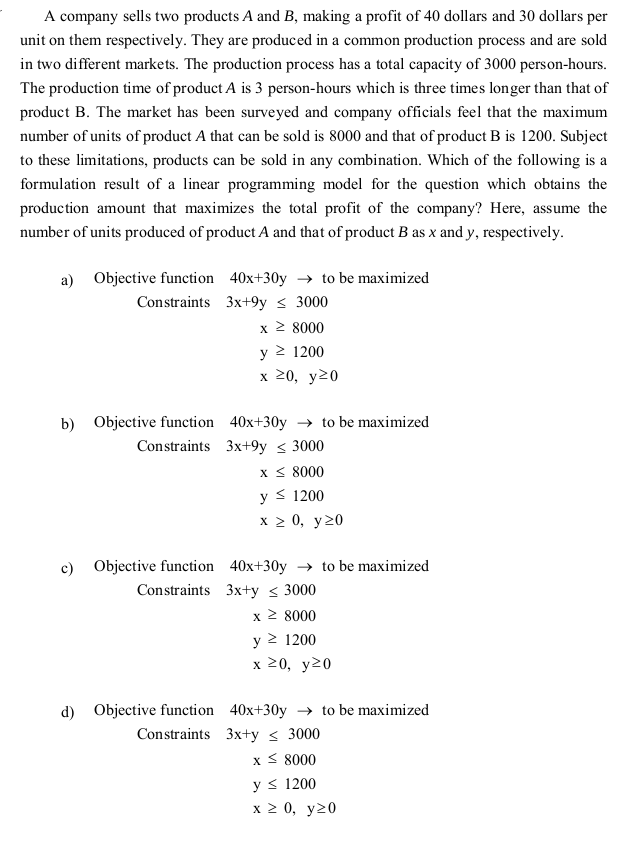","answer_label":"d","answer_id":25410},{"id":6317,"question":"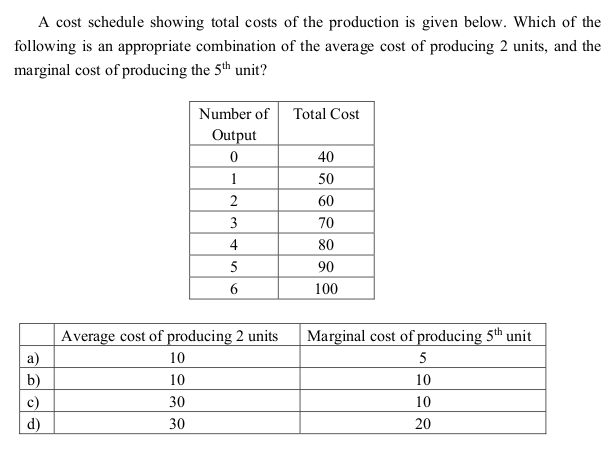","answer_label":"c","answer_id":25417},{"id":6319,"question":"","answer_label":"d","answer_id":25424},{"id":6351,"question":"Which of the following decimal fractions becomes a finite fraction when converted to an octal number?","answer_label":"0.5","answer_id":25532},{"id":6352,"question":"A register stores a numerical value representing a binary number. After a positive integer x is entered in the register, the following operation is performed: “shift the register value two bits to the left and add x.” How many times as large as x is the new value of the register? Here, the shift does not cause an overflow.","answer_label":"5","answer_id":25536},{"id":6353,"question":"Which of the following is the appropriate way to check whether or not an 8-bit unsigned binary number x is a multiple of 16?","answer_label":"The bit-by-bit logical product between x and the binary number 00001111 is 0.","answer_id":25538},{"id":6354,"question":"In the single precision of “IEEE Standard for Binary Floating-Point Arithmetic” (IEEE 754), the value “V ” is represented as follows: \n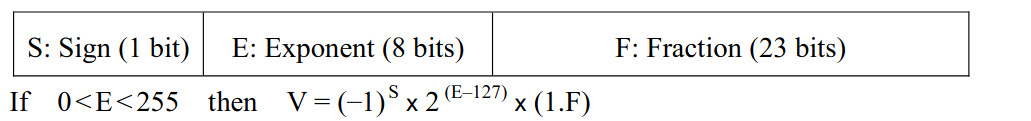\nwhere “1.F ” is intended to represent the binary number created by prefixing F with an implicit leading 1 and a binary point. \nWhen the hexadecimal value C1E00000 is represented in IEEE 754, what is the correct value converted to decimal?","answer_label":"–28","answer_id":25544},{"id":6355,"question":"There are a total of N values observed. The sum S (S> 0) of these values is obtained, and then the average value is calculated. Which of the following is the correct expression when the average value is rounded off to the nearest integer value? Here, “/ ” indicates division, and [X] is the maximum integer equal to X or less.","answer_label":"[S/N+ 0.5 ]","answer_id":25548},{"id":6356,"question":"A k-string is a character string with a length of k characters. An m-substring is an ordered sequence with a length of m characters, which consists of consecutive elements of the original k-string. An n-subsequence is also an ordered sequence with a length of n characters, which consists of elements of the original k-string, but it does not need to be consecutive. How many m-substrings and n-subsequences are respectively included in the k-string?\n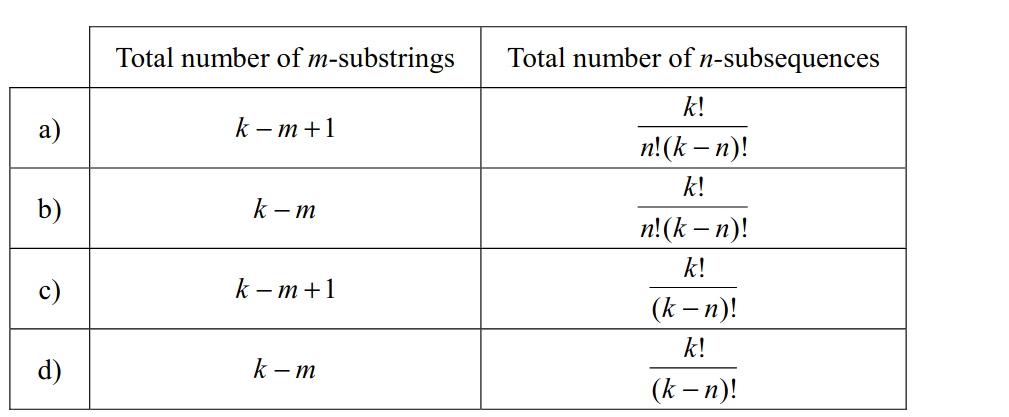","answer_label":"a","answer_id":25550},{"id":6357,"question":"There are 3 white balls and 3 red balls in a box. What is the probability that the two balls taken out at random from the box are one white ball and one red ball?","answer_label":"3/5","answer_id":25557},{"id":6358,"question":"There are n locks and n keys; the keys are mixed and need to specifywhich key belongs to which lock. Which of the following is the maximum number of trials to find the correct key for each lock? Here, one key can open only one lock.","answer_label":"(n^2–n) / 2","answer_id":25561},{"id":6359,"question":"Which of the following is equivalent to the logical expression shown below? Here, “•” is used for the logical product, and “+” is for the logical sum. \n((X + Y) • (X + Z)) + ((X •Y) + (X • Z))","answer_label":"(X + (Y • Z)) + (X • (Y + Z))","answer_id":25562},{"id":6360,"question":"Which of the following Boolean expressions is equivalent to the sentence below? \n“The output z is true if at least two of the three inputs x1, x2, and x3 are true.” \nHere, “$\\overline{x}_n$” is used for the logical negation of $x_n$, “+” for the logical sum, “.” for the logical product, and “⊕” for the exclusive disjunction (or exclusive OR).\n","answer_label":"d","answer_id":25569},{"id":6361,"question":"There are three stacks A, B, and C where stack A contains the values 1, 2, and 3; 3 is on the top of the stack, and stacks B and C are empty. The stack command format is as follows: \n<stack command> (<stack name>, <temporary variable>) \nWhat is the resulting content of stack A after executing the stack operations shown below? Each rightmost element in the option list represents the value on the top of the stack. \nPop (A, x) → Push (B, x) → Pop (A, x), → Push (C, x) → Pop (A, x) → Push (C, x) → Pop (B, x) → Push (A, x) → Pop (C, x) → Push (B, x) → Pop (C, x) → Push (A, x) → Pop (B, x) → Push (A, x)","answer_label":"3, 2, 1","answer_id":25573},{"id":6362,"question":"In a certain examination, the minimum and maximum scores are 31 and 95 respectively. A one-dimensional array shown below is used to display the distribution of scores for all examinees, and each array element indicates the number of examinees whose scores are in the specified ranges. Which of the following is the most appropriate expression to calculate an array index for each score? Here, any digits after the decimal point of the resulting value are truncated to generate an integer as an index.\n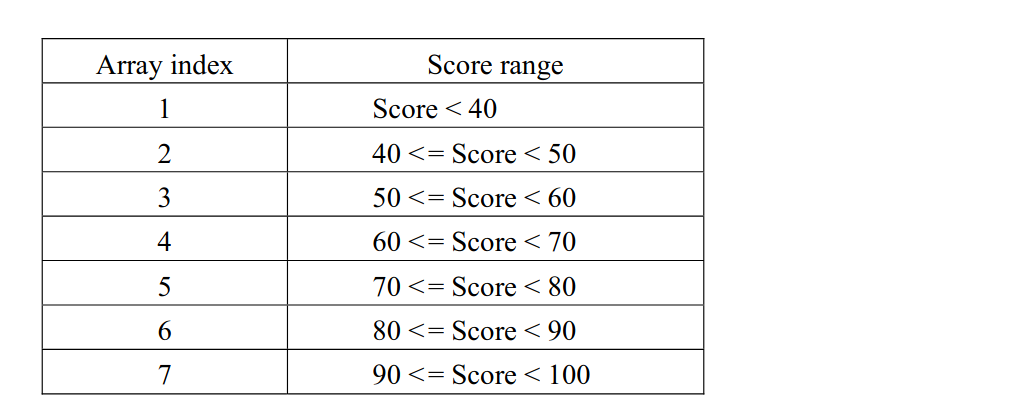","answer_label":"(Score–30) / 10 + 1","answer_id":25576},{"id":6363,"question":"A k-ary tree is a tree in which every node has no more than k children. A binary tree is the special case where k=2. In a k-ary tree with n nodes and height h, which of the following is an upper bound for the number of leaves?\n","answer_label":"b","answer_id":25579},{"id":6364,"question":"A recursive definition of a factorial function f(n) that calculates “ n ! ” can be represented as follows: \n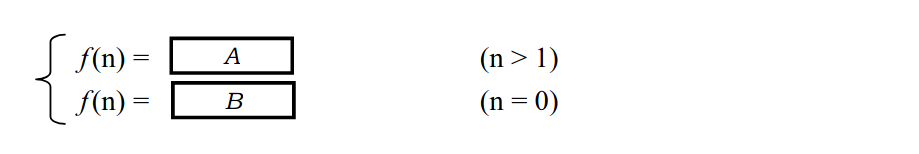\nWhich of the following combinations should be inserted in the boxes A and B? Here, “ n ” is a non-negative integer.\n","answer_label":"c","answer_id":25584},{"id":6365,"question":"A binary search tree is created by inserting the values shown below. \n7 9 11 2 8 10 5 3 \nAfter deletion of the root from the newly created tree, what does it look like?\n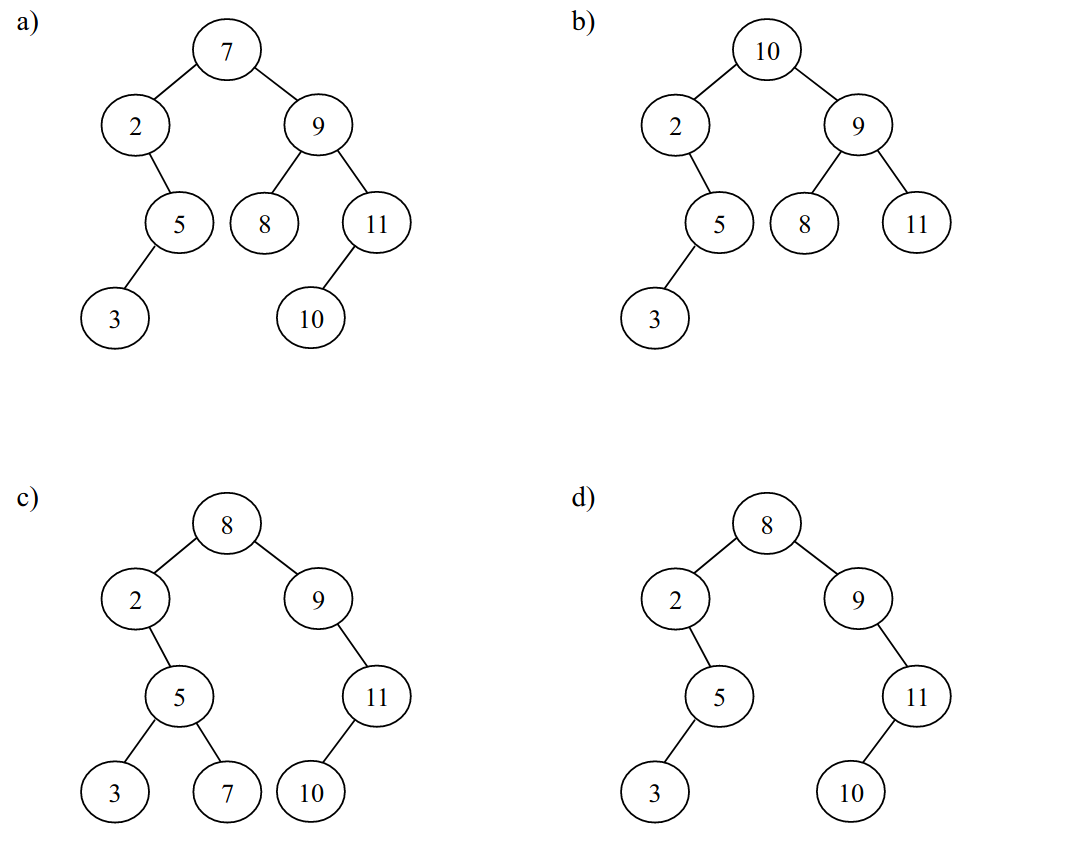","answer_label":"d","answer_id":25589},{"id":6366,"question":"Which of the following is the sorting algorithm that divides the data elements into two groups, in which all those elements less than a particular element (called a pivot value) and all those elements greater than or equal to it are separately included, and then repeats the same operation until all elements are sorted in ascending or descending order?","answer_label":"Quick sort","answer_id":25593},{"id":6367,"question":"The figure shown below represents a logic gate and its timing chart. Which of the following is an appropriate logical function of this gate? Here, both A and B are the input signals and F is the output signal.\n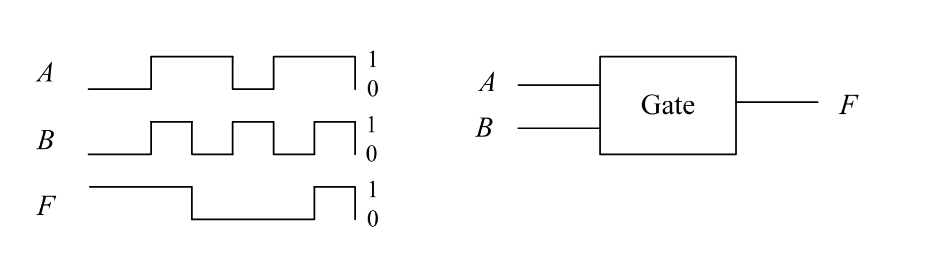","answer_label":"Exclusive-NOR","answer_id":25595},{"id":6368,"question":"Which of the following is an appropriate description concerning registers in processors?","answer_label":"A complement register generates integer complements in order to perform operations in the adder circuit.","answer_id":25599},{"id":6369,"question":"When a CPU can perform a multiplication in 12 nanoseconds (ns), an addition in 1 ns, and a subtraction in 1.5 ns, which of the following is the minimum CPU time, in nanoseconds, for the calculation of “a × a – b × b ” ?","answer_label":"14.5","answer_id":25604},{"id":6370,"question":"Which of the following is the appropriate diagram that explains pipeline control? \nHere, the meanings of the capital letters in the diagrams are as follows: \nF: Fetching instruction \nD: Decoding \nA: Address calculation \nR: Reading operand \nE: Executing\n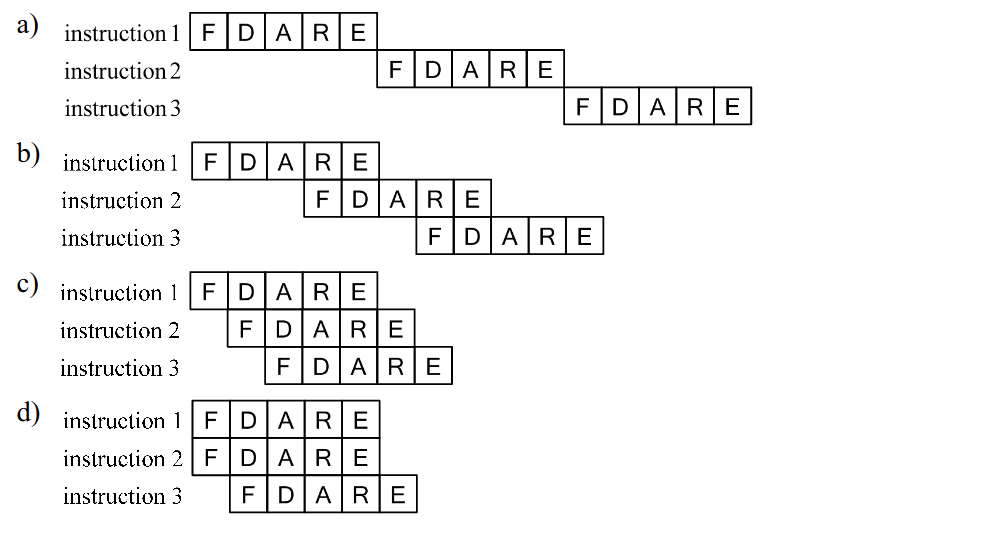","answer_label":"c","answer_id":25608},{"id":6371,"question":"Which of the following is the appropriate description of CPU clock frequencies for PCs?","answer_label":"The instruction execution timing in a CPU varies depending on the clock frequency. The higher the frequency, the faster the instruction execution speed gets.","answer_id":25611},{"id":6372,"question":"There is a CPU with an internal clock frequency of 700 MHz. The number of clock cycles for executing instructions and their appearance rates are shown in the table below. What is the approximate performance (measured in MIPS) of this CPU?\n","answer_label":"100","answer_id":25617},{"id":6373,"question":"A processor with a 256-Mbyte address space is using the address “35E3C03” to access a 16-Mbyte memory device. What are the highest and lowest addresses in the memory map of the 16-Mbyte memory device? Here, the memory addresses are expressed in hexadecimal. \n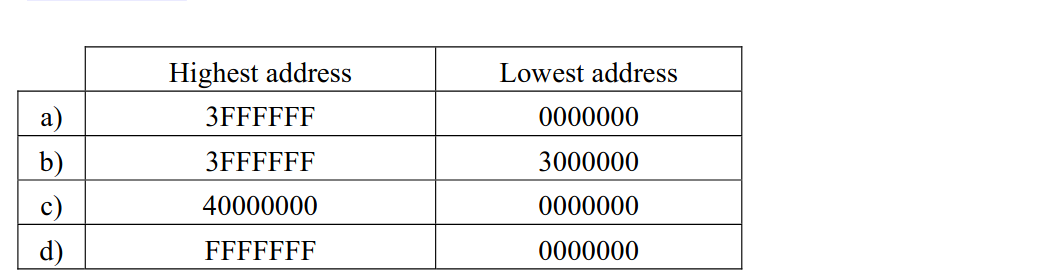","answer_label":"b","answer_id":25619},{"id":6374,"question":"Which of the following is used in ECC memory to detect 2-bit errors and correct 1-bit errors?","answer_label":"Hamming code","answer_id":25624},{"id":6375,"question":"A system has a main memory access time of 60 nanoseconds (ns) and a cache memory access time of 10 ns. When the effective access time for accessing the main memory via the cache memory is 15 ns, what is the hit ratio of the cache memory?","answer_label":"0.9","answer_id":25629},{"id":6376,"question":"Which of the following storage devices has the fastest access time?","answer_label":"CPU register","answer_id":25631},{"id":6377,"question":"Which of the following is widely used as a computer port for a modem connection?","answer_label":"Serial port","answer_id":25637},{"id":6378,"question":"A certain computer system runs in a multi-programming environment using a non-preemptive “shortest job first ” algorithm. In this system, four processes A, B, C, and D arrive sequentially in the process queue every 1 millisecond. The table shown below includes estimated execution time for each process; for example, process A uses CPU, I/O, and then CPU sequentially for 4, 5, and 5 milliseconds respectively. When 14 milliseconds elapse after the arrival of the first process A, which of the following processes is executed in CPU? Here, the multi-processing overhead of OS can be ignored, and both CPU and I/O operations can be executed concurrently. \n","answer_label":"C","answer_id":25640},{"id":6379,"question":"The figure below shows the state transition diagram of a certain process. Which of the following is the appropriate combination of States A, B, and C?\n","answer_label":"c","answer_id":25644},{"id":6380,"question":"Which of the following is the appropriate explanation of spooling?","answer_label":"Output data to a low speed device such as a printer is temporarily stored on a high speed hard disk and later sent as output to that target device.","answer_id":25648},{"id":6381,"question":"Which of the following is the appropriate set of major functions supported by an OS?","answer_label":"Data management, job management, and task management","answer_id":25651},{"id":6382,"question":"Which of the following is the appropriate explanation of RPC in a client/server system?","answer_label":"It is a method of communication between programs, where parts of the process are assigned to another computer.","answer_id":25654},{"id":6383,"question":"In order to make a multiplexing system with an availability of at least 0.999 by using devices with an availability of 0.9, how many of these devices need linking together in parallel?","answer_label":"3","answer_id":25659},{"id":6384,"question":"Which of the following helps improve availability?","answer_label":"Doubling MTBF and reducing MTTR to half","answer_id":25663},{"id":6385,"question":"Which of the following refers to the concept of fail-safe design?","answer_label":"If the system determines that the sensor which detects someone entering the work area has failed, the robot arm is stopped by force.","answer_id":25669},{"id":6386,"question":"Which of the following is the term that refers to collecting a large volume of data through a variety of corporate activities, organizing, integrating, and saving the data for specific purposes, and using it for decision-making support, for example?","answer_label":"Data warehouse","answer_id":25673},{"id":6387,"question":"When large-scale websites are built, application servers are often used in addition to Web servers. Which of the following is an appropriate reason for this?","answer_label":"System modification or expansion is made easier in comparison with Web servers alone.","answer_id":25674},{"id":6388,"question":"CASE tools can be classified on the basis of the applicable development processes and phases. Which of the following classifications includes support functions for requirements analysis?","answer_label":"Upstream","answer_id":25681},{"id":6389,"question":"Which of the following is the method which analyzes the source or object code to retrieve information concerning program specifications and design?","answer_label":"Reverse engineering","answer_id":25685},{"id":6390,"question":"Based on the concept of object orientation, which of the following can be commonly regarded as a subclass of the class “automobile”?","answer_label":"Truck","answer_id":25689},{"id":6391,"question":"Which of the following should be done in the internal design phase of software development processes?","answer_label":"Designing physical data structure","answer_id":25692},{"id":6392,"question":"In the flowchart below, which of the following indicates the relationship between the initial values a and b that are given in m and n in the process (1) in order to carry out these processes in the order shown below? \n(1) → (2) → (3) → (5) → (2) → (3) → (4) → (2) → (6) \nHere, a and b are both positive integers.\n","answer_label":"3a = 2b","answer_id":25697},{"id":6393,"question":"Which of the following is the appropriate sequence for drawing up a DFD model that is used to develop a new system based on the current system? \n1. Current logical model \n2. Current physical model \n3. New logical model \n4. New physical model","answer_label":"2 → 1 → 3 → 4","answer_id":25700},{"id":6394,"question":"In DFD illustrated below, DFi is used for data flow i, Pj for process j, Ek for source or destination of data k, and DSl for data storage l. There are three errors (rule violations) in this DFD. One is in P2; that is, P2 must have at least one output data flow. The other two are in data flows. Which of the following combinations includes two rule violations, one for each data flow?\n","answer_label":"DF1 and DF5","answer_id":25703},{"id":6395,"question":"Which of the following is the appropriate characteristic of object-oriented models?","answer_label":"Data is hidden from the outside and indirectly handled by procedures called methods.A program is a collection of data and methods.","answer_id":25708},{"id":6396,"question":"Which of the following is the test to verify interfaces both between modules and between subsystems?","answer_label":"Integration test","answer_id":25710},{"id":6397,"question":"A certain program contains the complex decision shown below: \n“Condition 1” OR (“Condition 2” AND “Condition 3”) \nWhen testing based on decision-condition coverage (branch coverage), which of the following is appropriate for an additional test item? \n[Test items completed] \n(1)“Condition 1” is true, “Condition 2” is false, and “Condition 3” is false. \n(2)“Condition 1” is false, “Condition 2” is true, and “Condition 3” is true.\n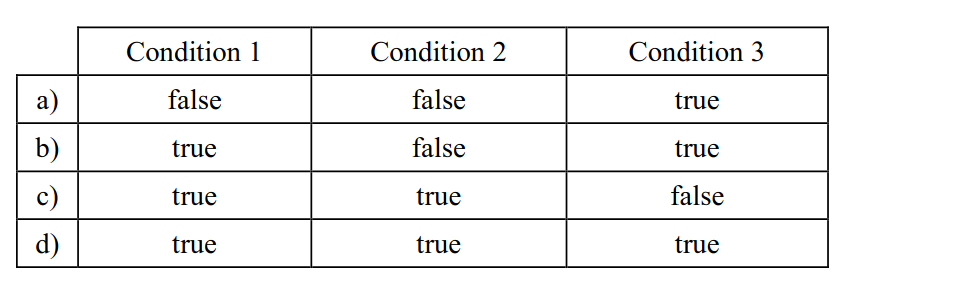","answer_label":"a","answer_id":25714},{"id":6398,"question":"Which of the following is the appropriate interpretation of the testing-process quality control graph shown below and follow-on actions to be taken?\n","answer_label":"The resulting quality is generally rather poor, so it is necessary to take strong measures against places in which errors occur frequently; the quality status of the preceding process should be reviewed and do it over again if necessary.","answer_id":25721},{"id":6399,"question":"How much is the approximate expected value in dollars, for the first-year correction cost of an application program under the following conditions? \n[Conditions] \n(1) Program size: 2,000 Ksteps \n(2) Potential program error rate: 0.04 errors / Ksteps \n(3) Annual discovery rate of potential errors: 20 % / year \n(4) Classification of errors \n Error with major impact: 20 % \n Error with minor impact: 80 % \n(5)Correction cost per error \n Error with major impact: 20,000 dollars \n Error with minor impact: 5,000 dollars \n(6) Only errors with major impact are corrected.","answer_label":"64000","answer_id":25722},{"id":6400,"question":"Which of the following is the most appropriate description concerning a “watch list” of system failures?","answer_label":"System operators also monitor processing delays, because such delays can cause system failures.","answer_id":25728},{"id":6401,"question":"Which of the following is an appropriate description concerning a characteristic of job scheduling in a computer system?","answer_label":"In a system on which interactive processing and batch processing are mixed, it is expected that the response performance of interactive processing is improved by giving a higher priority to interactive processing.","answer_id":25730},{"id":6402,"question":"In software maintenance, which of the following tests is performed to ensure that fixes or modifications do not affect other, unchanged parts of the software?","answer_label":"Regression test","answer_id":25737},{"id":6403,"question":"An IP address in IPv4 consists of two parts: the network address part and the host address part. Which of the following is the appropriate description concerning the network address and the host address? Here, n is the number of bits in the network address part, and h is the number of bits in the host address part. In addition, the special-purpose and ineffective addresses should not be counted as an effective address.","answer_label":"In classes A, B, and C, the maximum number of effective host addresses available to one network is defined as 2^h– 2.","answer_id":25738},{"id":6404,"question":"Which of the following terms can be applicable to an explanation below? “The sender sends a single datagram; the routers are responsible for making copies and sending them to a group of interested receivers.”","answer_label":"Multicast","answer_id":25744},{"id":6405,"question":"Which of the following is a protocol for e-mail on the Internet that supports not only text but other data such as audio and images through message header extension?","answer_label":"MIME","answer_id":25748},{"id":6407,"question":"Which of the following protocols is used for synchronizing the clocks in multiple nodes on the Internet?","answer_label":"NTP","answer_id":25755},{"id":6408,"question":"Which of the following is a mechanism that allows a Web server to store its own information about a user on the user’s own computer so that the Web server can identify users and possibly prepare customized Web pages for them?","answer_label":"Cookie","answer_id":25758},{"id":6409,"question":"Which of the following is the mechanism for interfacing a Web server with an external program in order to implement an interactive page where an application program on the server executes a request from a client and returns the resulting output to the browser?","answer_label":"CGI","answer_id":25762},{"id":6413,"question":"There are two tables “movie” and “movietype” as shown below. Which of the following tables is created as the result of executing the SQL statement specified below?\n\n","answer_label":"b","answer_id":25779},{"id":6414,"question":"Which of the following appropriately describes a group function of SQL?","answer_label":"A group function returns a single result row per group for a set of queried rows.","answer_id":25783},{"id":6415,"question":"Which of the following appropriately explains the SQL statements shown below?\n","answer_label":"“SELECT * FROM STAFF ” extracts all records in the table MANAGER.","answer_id":25786},{"id":6416,"question":"Which of the following authentications can be realized with the information exchange between two communication actors X and Y according to the procedure below? \n[Procedure] \n(1) Y transmits a character string (challenge) including optional information to X. \n(2) X generates a new character string (response) from the received character string based on predetermined rules between X and Y, and sends back this character string (response) to Y. \n(3) Y confirms that the returned character string (response) is correct.","answer_label":"Y authenticates X.","answer_id":25792},{"id":6417,"question":"Which of the following is an advantageous effect of encrypting e-mails?","answer_label":"It is possible to prevent the contents of e-mails from leaking out.","answer_id":25796},{"id":6418,"question":"Which of the following is an appropriate action to be taken when a computer virus is found?","answer_label":"First, the infected computer is disconnected from the relevant network, because other computers may be infected via the network.","answer_id":25799},{"id":6419,"question":"Which of the following is an appropriate operations management method for user IDs and passwords?","answer_label":"For the purpose of preventing passwords from being abused by other people, it is so arranged that users become free to change their passwords at any time.","answer_id":25803},{"id":6420,"question":"When LAN analyzers are used for finding out the causes of network failures, which of the following is a point to keep in mind?","answer_label":"Some analyzers are capable of displaying packets that pass through networks. Therefore, it is necessary to be careful not to use them in different ways such as wiretapping.","answer_id":25809},{"id":6426,"question":"Company A and Company B can expect profits as shown in the table below when each of them implements two different strategies. Which of the following is the profit of Company A when both companies carry out the maximum in strategy? In each cell of the table, the left value indicates the profit of A, and the right value indicates the profit of B.\n","answer_label":"5","answer_id":25832},{"id":6427,"question":"Which is the method of solving a problem of the following type: “How can we distribute a resource subject to constraints that can be expressed by first-degree equations so as to obtain a maximum effect?”","answer_label":"Linear programming","answer_id":25836},{"id":6428,"question":"A certain company has installed an online computer for the purpose of improving its inventory control system. When the company anticipates sales of 15,000 units per year, ordering cost of $60 per order, and annual holding cost of $20 per unit, what is the optimal order quantity (in units) per order? Here, the fixed order quantity model can be applied.","answer_label":"300","answer_id":25838},{"id":6429,"question":"There are seven activities A through G shown in the table below. Activities A and Bcan be performed concurrently, but the others cannot be done until theirpreceding activities are completed. For example, C cannot begin until A is completed. Which of the following is the critical path of these activities?\n","answer_label":"A→C→E→G","answer_id":25842},{"id":6430,"question":"Which of the following is the situation that is expected to be improved by the introduction of an MRP (Material Requirements Planning) system?","answer_label":"Information concerning materials necessary for manufacturing and their required quantities is complex, so errors can occur repeatedly in the estimated quantity of order and thereby bring about problems to production.","answer_id":25848},{"id":13772,"question":"For two 8-bit signed integers A and B in 2’s complement format, which of the following will cause an overflow when the addition of A and B is executed?\n\n","answer_label":"b","answer_id":53339},{"id":13773,"question":"What is the probability of getting at least two heads when a fair coin is flipped five times?","answer_label":"0.8125","answer_id":53343},{"id":13774,"question":"What is the value of the postfix expression below? Here, A, B, C, and D are operands whose values are 4, 3, 5, and 6, respectively. Symbols “+”, “−”, “×”, and “÷” are arithmetic operators for addition, subtraction, multiplication, and division, respectively. \n\nA B 2 × + D B ÷ C × −","answer_label":"0","answer_id":53347},{"id":13775,"question":"In machine learning, which of the following best describes the supervised learning?","answer_label":"It is used to get a correct answer for new input data after being trained on a dataset with answer keys.","answer_id":53352},{"id":13776,"question":"A list is implemented with two arrays \"box\" and \"next\". Each element in the list corresponds to a pair (box[i], next[i]), where box[i] is the value of the element, and next[i] is the index to the next element in the list. When the element of value \"H\" is inserted between the third and fourth elements in the list shown below, which of the following is the value contained in next[8]? Here, next[0] contains the index of the leading (first) element of the list, the index i whose next[i] is 0 indicates the last element of the list, and each index i whose next[i] is blank indicates that the element is out of the list.\n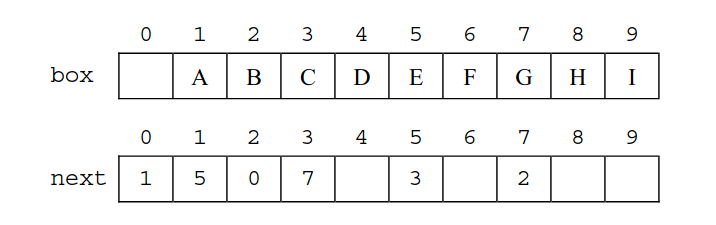","answer_label":"7","answer_id":53356},{"id":13777,"question":"Two operations against a queue are defined below. \nENQ n: adds a number n at the end of the queue. \nDEQ: removes the number at the head of the queue. \n\nFor an empty queue, a sequence of operations, \n“ENQ 1, ENQ 2, ENQ 3, DEQ, ENQ 4, ENQ 5, DEQ, ENQ 6, DEQ, DEQ”, \nis performed in this order. When another DEQ is performed in succession, what is the number to be removed by this operation?","answer_label":"5","answer_id":53360},{"id":13778,"question":"Every year that is exactly divisible by four is a leap year, except for years that are exactly divisible by 100, but these centurial years are leap years if they are exactly divisible by 400. For example, the years 1700, 1800, and 1900 are not leap years, but the years 1600 and 2000 are. How many leap years are there between 1895 and 2021?","answer_label":"31","answer_id":53363},{"id":13779,"question":"Which of the following is a characteristic of a RISC processor when it is compared with a CISC processor?","answer_label":"The RISC processor uses a uniform instruction length to process tasks in a pipeline.","answer_id":53367},{"id":13780,"question":"Which of the following is an appropriate characteristic of SRAM compared with DRAM?","answer_label":"SRAM does not need to be refreshed periodically as flips flops retain data, and DRAM needs to be refreshed at fixed intervals to retain data.","answer_id":53372},{"id":13781,"question":"Which one of the following serial transmission methods is used in asynchronous data communication","answer_label":"UART","answer_id":53377},{"id":13782,"question":"As a backup system configuration, which of the following is an appropriate description of a hot site","answer_label":"A site is operated as a standby site, the data and programs are updated at all times via a network, and the business operation is resumed immediately when a failure occurs.","answer_id":53379},{"id":13783,"question":"A RAID 6 server is configured with six hard disk drives, and each drive’s capacity is one TB. What is the maximum total data storage capacity in TB? Here, spare disks are not used.","answer_label":"4","answer_id":53383},{"id":13784,"question":"The life cycle of a computer system can be classified from the viewpoint of failure into the three periods of early failure period, random failure period, and wear-out failure period. Which of the following is the most appropriate description of the measures in the early failure period?","answer_label":"Strengthening the design review and failure analysis in order to reduce errors in the design and manufacturing","answer_id":53389},{"id":13785,"question":"When the number of concurrently running programs is increased in a virtual storage system with a small and insufficient main memory capacity, which of the following is the state in which the overhead of the system increases and the processor utilization of the applications decreases","answer_label":"Thrashing","answer_id":53393},{"id":13786,"question":"When the least recently used (LRU) method is used for swapping a block between cache memory and main memory, which of the following is a block in cache memory to be replaced","answer_label":"A block for which the longest period of time has elapsed since it was last referenced","answer_id":53395},{"id":13787,"question":"Assume that there are three pages in the real memory that can be allocated by the LRU method. Which of the following is the number of page faults for the page reference string shown below? Here, three pages are initially empty, and filling of an empty page is not considered as a page replacement operation. The numbers are the page IDs that come to the system from left to right. \n","answer_label":"7","answer_id":53401},{"id":13788,"question":"32-bit virtual address space is mapped to 4 k-byte pages. How many pages can be created? Here, 1k bytes represent 1,024 bytes.","answer_label":"2^20","answer_id":53404},{"id":13789,"question":"The four jobs A through D are executed based on the conditions below and printed. How many seconds is it until all printing is completed after a job is started?\n[Conditions] \n(1) All jobs are launched at once, and executed by the CPU with a multiplicity of one. \n(2) Job A has the highest priority, followed by B, C, and D. \n(3) After each job is executed, a spooling function prints each job in turn on a single printer. \n(4) The execution time and printing time when each job is executed separately are as shown in the table. \n(5) Other overheads are not considered.\n\n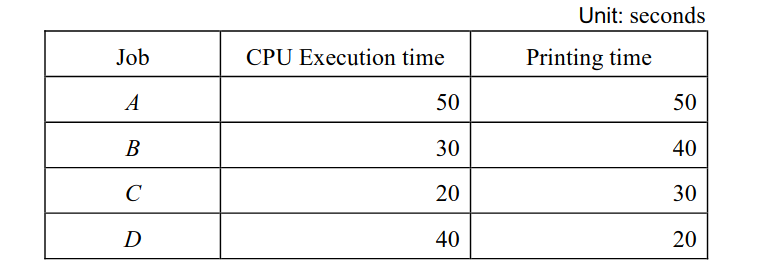","answer_label":"190","answer_id":53408},{"id":13790,"question":"Which of the following is an appropriate description of flash memory","answer_label":"The content can be erased electrically in units of blocks.","answer_id":53412},{"id":13791,"question":"Which of the following is equivalent to the circuit below?\n","answer_label":"d","answer_id":53417},{"id":13792,"question":"Which of the following is an appropriate equation of the XOR operator? Here, “・” represents the logical AND, “+” represents the logical OR, and P represents the inverse of P in the logical expression. \n\n","answer_label":"b","answer_id":53419},{"id":13793,"question":"Among GUI components,which of the following is an appropriate use of a radio button?","answer_label":"To select one item from a group of mutually exclusive items","answer_id":53424},{"id":13794,"question":"Audio signals are recorded using 8-bit samples at a sampling rate of 11,000 times per second. When a flash memory of 512 × 10^6 bytes is used, what is the maximum recording time of such data in minutes?","answer_label":"775","answer_id":53428},{"id":13795,"question":"From the figure below, which of the following isan appropriate set of attributes for the “CatalogProduct” class table?\n\n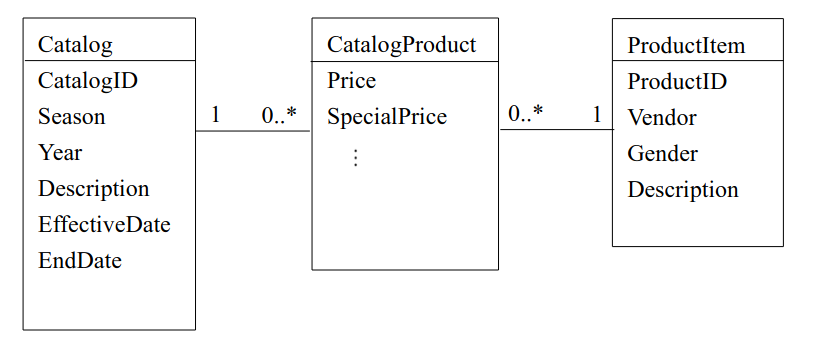","answer_label":"CatalogID, ProductID, Price, SpecialPrice","answer_id":53431},{"id":13796,"question":"Which of the following is the database function that is automatically executed when a specific action such as update, delete, or insert occurs within a database?","answer_label":"Trigger","answer_id":53436},{"id":13797,"question":"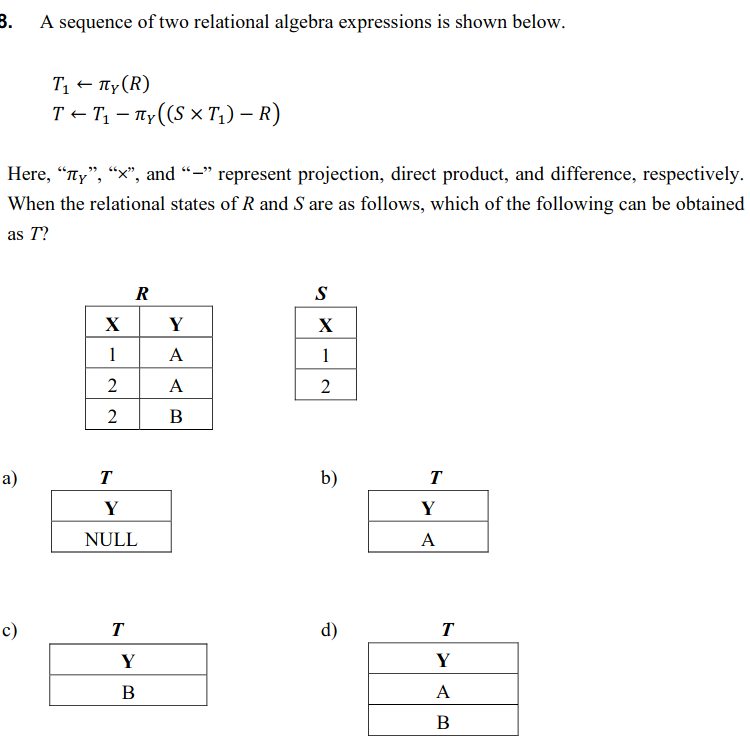","answer_label":"b","answer_id":53439},{"id":13798,"question":"There arethree tables, EMPLOYEE, PROJECT, and WORK_PROJ for recording employees, projects, and working information of employees on projects respectively. When the SQL statement shown below is executed for these tables, which of the following is generated as the output? \n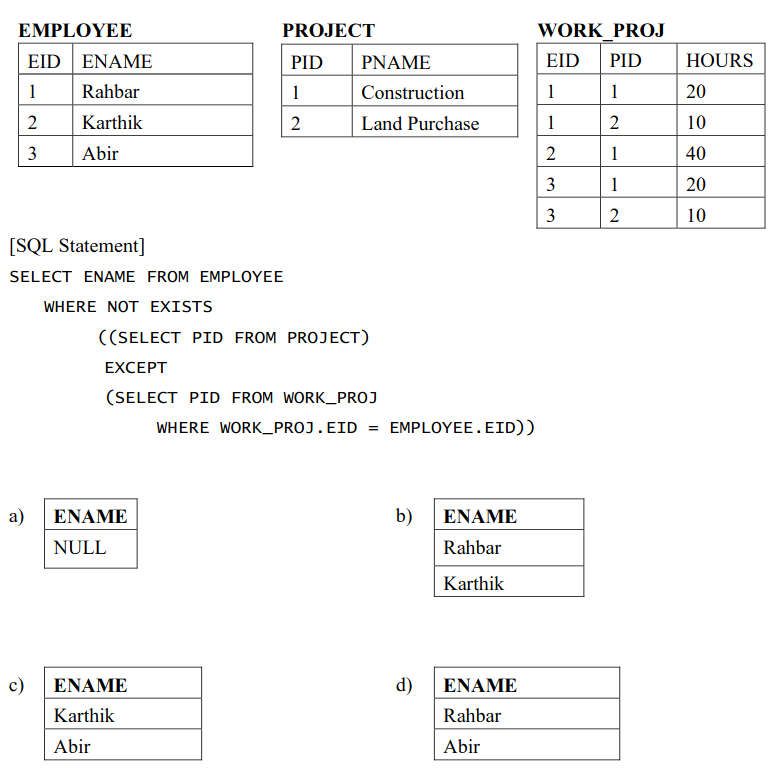","answer_label":"d","answer_id":53445},{"id":13799,"question":"In a database system, which of the following is the action to undo changes done by transactions executed after the last commit?","answer_label":"Roll back","answer_id":53447},{"id":13800,"question":"Which device performs protocol conversion between different types of networks, functioning at the layers of transport and above in the OSI basic reference model?","answer_label":"Gateway","answer_id":53451},{"id":13801,"question":"Locations A and B, both on the ground, communicate via a geostationary satellite at an altitude of about 36,000 km. When the distance between each location and the satellite is 37,500 km, and the delay caused by the relay at the satellite is 10 milliseconds, what is the total delay in seconds for the data sent from A to arrive at B? Here, the propagation speed of radio waves is 3×10^8 m per second","answer_label":"0.26","answer_id":53455},{"id":13802,"question":"Which of the following is an appropriate characteristic of IPv6 addresses?","answer_label":"There are several address representations, one of which uses a hexadecimal string with every four digits (i.e., 16 bits) separated by a colon “ : ” .","answer_id":53460},{"id":13803,"question":"There is a PC whose IP address and subnet mask are shown below. Which of the following is the network address of this PC? \n\nIP address: 10.170.70.19 \nSubnet mask: 255.255.255.240","answer_label":"10.170.70.16","answer_id":53463},{"id":13804,"question":"Which of the following is an Internet standard that extends the format of email messages to support non-ASCII text as well as audio, video, and images","answer_label":"MIME","answer_id":53468},{"id":13805,"question":"Which of the following is an attack using a trial-and-error method to obtain confidential information such as a user password or personal identification number (PIN)?","answer_label":"Brute force","answer_id":53470},{"id":13806,"question":"Which of the following is an appropriate description of clickjacking","answer_label":"An attacker misleads the user to interact with a user interface and to perform unintended operations.","answer_id":53475},{"id":13807,"question":"Which of the following activitiestargets the DHCP server and exhausts all its available IP address pool so that it cannot provide any IP addresses to its clients?","answer_label":"DHCP starvation","answer_id":53481},{"id":13808,"question":"Man-in-The-Middle (MITM) attack means the attacker intercepts and alters the communication between the end-user (victim) and the server, which is shown below. In an MITM attack, when the victim sends packets to the server, the attacker receives the packets and then forwards them to the server while the server sends the packets to the victim via the attacker. In this communication channel, which of the following is the appropriate description concerning the MITM attack?\n","answer_label":"The attacker always uses the victim’s IP during the communication with the server and always uses the server IP during the communication with the victim.","answer_id":53484},{"id":13809,"question":"Which of the following is the result when person A sends an e-mail that is encrypted by person B’s public key to person B and person C? Here, these three persons have the public keys of all three persons, and all of them have their own private keys.","answer_label":"Only B can decrypt the encrypted e-mail using B’s own private key.","answer_id":53489},{"id":13810,"question":"Which of the following is a package of unauthorized programs and tools that have functions such as creating a back door on a server and hiding the evidence of intrusion inside a server?","answer_label":"Rootkit","answer_id":53491},{"id":13811,"question":"Which of the following is the most appropriate countermeasure against cross-site scripting (XSS) attacks?","answer_label":"Filtering out the input that can be interpreted as a script","answer_id":53496},{"id":13812,"question":"Which of the following is a method to prevent damage caused by an SQL injection attack?","answer_label":"Preventing input characters from being interpreted as characters that have a special meaning in querying or manipulating data in a database","answer_id":53498},{"id":13813,"question":"Which of the following is the network security tool that isusually deployed by a network or system administrator and presents itself as a target machine trying to lure attackers to observe their behavior and attack methodology without harming other systems?","answer_label":"Honeypot","answer_id":53502},{"id":13814,"question":"SSL/TLS is the industry-standard security technology creating encrypted connections between a web server and a web browser. This is used to maintain data privacy and to protect the information in online transactions. The steps for establishing an SSL/TLS connection are randomly listedas follows:\n\n1. The web server sends a copy of its SSL/TLS certificate to the web browser. \n2. SSL/TLS encrypted communication takes place between the web browser and the web server. \n3. The web server sends the web browser an acknowledgment to start an SSL/TLS encrypted connection. \n4. The web browser checks if the SSL/TLS certificate is trustworthy or not. If it is trustworthy, then the web browser sends a message to the web server requesting to establish an encrypted connection. \n5. A web browser tries to connect to the web server secured with SSL/TLS. Which of the following is the correct step sequence?","answer_label":"5 → 1 → 4 → 3 → 2","answer_id":53509},{"id":13815,"question":"Which of the following is an appropriate description of a UML use case diagram?","answer_label":"It shows the scenarios for what the system will do, from the point of view of actors (i.e., external users or machines).","answer_id":53513},{"id":13816,"question":"Among the design techniques that are used in system development, which of the following is an explanation of a decision table?","answer_label":"It represents a combination of conditions and the corresponding operations.","answer_id":53514},{"id":13817,"question":"Test data about the part of a program shown in the flowchart below is specified by decision condition coverage (branch coverage). When this test data is changed to being specified by multiple-condition coverage, which of the following is the appropriate test data to be added? Here, the part enclosed by parentheses () represents the set of test data. \n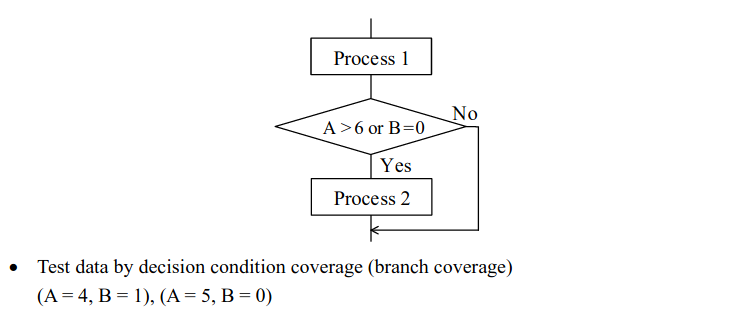","answer_label":"(A = 7, B = 0), (A = 8, B = 2)","answer_id":53521},{"id":13818,"question":"Among the different types of software tests, which of the following is a test that is performed with the purpose of checking whether or not a location that must not be affected by changes made for software maintenance is affected","answer_label":"Regression test","answer_id":53524},{"id":13819,"question":"Which of the following is an explanation of reverse engineering of software","answer_label":"The existing software is analyzed, and its specification and structure are clarified.","answer_id":53527},{"id":13820,"question":"According to PMBOK, which of the following is the description of scope creep?","answer_label":"The uncontrolled expansion to product or project scope without adjustments to time, cost, and resources","answer_id":53533},{"id":13821,"question":"A project with a development period of 10 months and the person-hours required for development as 200 person-months is planned. Which of the following is the number of staff members required during the peak time based on the distribution sheet shown below? Here, the number of staff members does not change from the start till the end of every process.\n","answer_label":"22","answer_id":53537},{"id":13822,"question":"Which of the following is the critical path of the project activities shown in the figure below?\n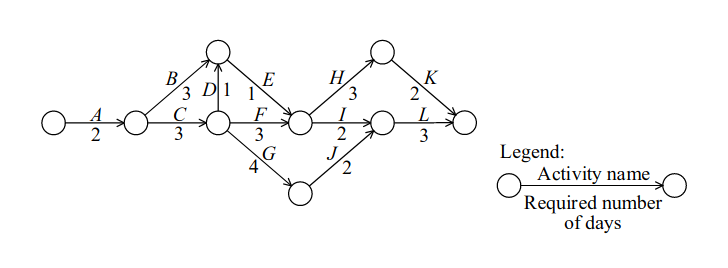","answer_label":"A→C→G→J→L","answer_id":53541},{"id":13823,"question":"Which of the following is an explanation of the function point method?","answer_label":"The development scale is estimated from the counts and characteristics of external inputs and outputs, internal logical files, external inquiries, and external interface files.","answer_id":53544},{"id":13824,"question":"In ITIL, the reduction in the index value expressing maintainability is cited as an example of a key performance index (KPI) in availability management. Which of the following corresponds to such an index?","answer_label":"Mean time to restore service","answer_id":53548},{"id":13825,"question":"In service management, which of the following is a requirement of service level management?","answer_label":"A service catalog and SLA are created for the service to be provided, and they are agreed upon with the customer.","answer_id":53551},{"id":13826,"question":"Which of the following is an effective means of protecting an information system from the damage from over-voltage that occurs because of alightning strike","answer_label":"Connecting the communication cable and the computer through a surge protection device (SPD)","answer_id":53554},{"id":13827,"question":"Among situations that are identified as results of performing an ISMS internal audit on the basis of ISO/IEC 27001:2013 (Information security management systems—Requirements), which of the following is a situation that the auditor should record in the audit report as a finding?","answer_label":"After a risk assessment was performed, risk acceptance criteria were determined.","answer_id":53558},{"id":13828,"question":"An information security audit was performed about the security when backup media that contain confidential information are handed over to a vendor for external storage. Among situations that are identified as a result of this audit, which of the following is a situation that the auditor should record in the audit report as a finding?","answer_label":"The person in charge at the outsourcer puts the backup media in a cardboard box and hands it over to the vendor.","answer_id":53563},{"id":13829,"question":"In the system design stage, which of the following is the point to be checked during the audit of control for reducing the risk of non-fulfillment of user requirements","answer_label":"The user department must participate in the review of the system design.","answer_id":53569},{"id":13830,"question":"Among the “four categories ” of enterprise architecture, which of the following is the remaining one after business architecture, technology architecture, and application architecture","answer_label":"Data architecture","answer_id":53571},{"id":13831,"question":"The weighted comprehensive evaluation method is used to integrate and quantify the evaluation scores of multiple items for quantitatively evaluating the effect of improvements. Which of the following is the improvement proposal that should be prioritized in the table below\n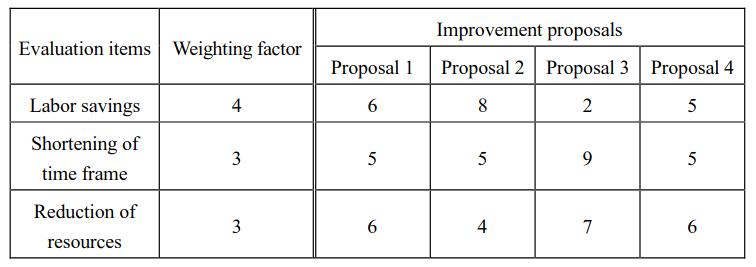","answer_label":"Proposal 2","answer_id":53575},{"id":13832,"question":"Which of the following descriptions corresponds to CSR procurement?","answer_label":"Indicating procurement standards that take the environment, human rights, etc. into account, and requiring suppliers to comply with these","answer_id":53580},{"id":13833,"question":"An RFP is presented to each vendor that has responded to an RFI. Which of the following should be done beforehand in order to proceed with future vendor selection processes fairly?","answer_label":"Establishing processes of selection, such as setting evaluation standards or weighting rules of conformity to the request items","answer_id":53583},{"id":13834,"question":"In a growth matrix proposed by Ansoff, which of the following is a strategy for an organization that tries to expand a business by introducing new products into new markets?","answer_label":"Diversification","answer_id":53586},{"id":13835,"question":"Which of the following is an external factor related to company’s products, identified by SWOT analysis?","answer_label":"Threats by new entrants","answer_id":53592},{"id":13836,"question":"Heskett classified customers into four categories and explained the importance of improving customer satisfaction. Which of the following types of customers is dissatisfied and, if given a chance, would encourage others to switch as well?","answer_label":"Terror","answer_id":53597},{"id":13837,"question":"Which of the following is a definition of Customer Relationship Management (CRM)?","answer_label":"A technology for managing all of a company’s relationships and interactions with customers and potential customers in order to improve business relationships","answer_id":53599},{"id":13838,"question":"Which of the following is an appropriate explanation of the technology S curve","answer_label":"It represents the process of technological progress. It shows that technology advances slowly at the beginning and then advances rapidly, and thereafter, slowly stagnates.","answer_id":53604},{"id":13839,"question":"Which of the following is one of the main characteristics of a blockchain?","answer_label":"A distributed ledger on a peer to peer network","answer_id":53608},{"id":13840,"question":"When a production plan is created, it is important to select an appropriate production system. Which of the following is a suitable production system for varied and flexible high-mix low-volume production by single or several operators in charge of all processes?","answer_label":"Cell production system","answer_id":53611},{"id":13841,"question":"Which of the following is a control method for a status of “a somewhat large number” or“slightly” ?","answer_label":"Fuzzy control","answer_id":53615},{"id":13842,"question":"Which of the following is an explanation of a matrix organization","answer_label":"An organization in which members usually belong both to a functional department and to a department that executes specified business","answer_id":53620},{"id":13843,"question":"Which of the following is an explanation of work sharing","answer_label":"An initiative for securing employment through shortening of work hours per employee and review of work assignments","answer_id":53625},{"id":13844,"question":"Which of the following is a process of discovering useful patterns and relationships by the analysis of large volume of data?","answer_label":"Data mining","answer_id":53627},{"id":13845,"question":"Break-even point (BEP) is a point where total costs and total revenue are equal. The table below shows the fixed costs, price per unit, variable costs per unit, and BEP in units for Company A and Company B. \n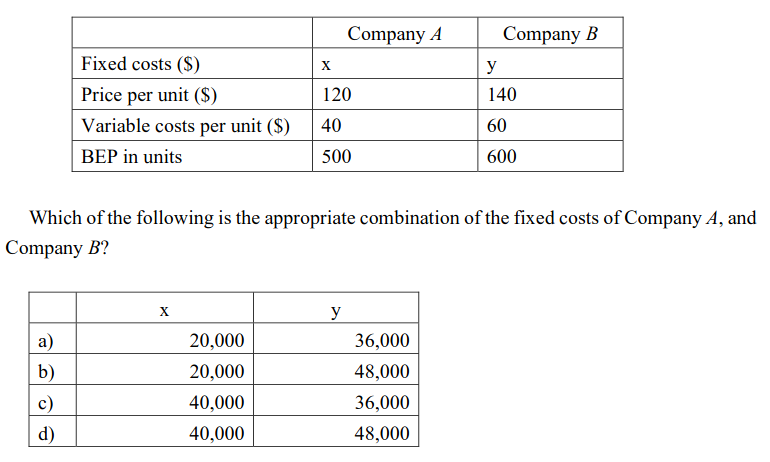","answer_label":"d","answer_id":53633},{"id":13846,"question":"An investor purchased property A for$500,000. Two years later, the investor sold the property for $1,000,000. Which of the following is the ROI of this investment (%)?","answer_label":"100","answer_id":53635},{"id":13847,"question":"Which of the following is software whose copyright is abandoned and that can be used free of charge?","answer_label":"Public Domain Software","answer_id":53640}]
const vi = [{"id":13324,"question":"Một thanh ghi lưu một giá trị số nguyên dưới dạng nhị phân. Cho x là số nguyên dương được lưu trữ trong thanh ghi, sau đó thực hiện các phép toán dưới đây.\n\n(1) Dịch chuyển nội dung của thanh ghi sang bên trái 2 bit\n\n(2) Cộng x vào thanh ghi\n\nGiá trị của thanh ghi lớn hơn bao nhiêu lần so với số nguyên x?","answer_label":"5","answer_id":51551},{"id":13326,"question":"Lựa chọn nào sau đây là giá trị thập phân tương đương với phân số thập lục phân 0.B1?!","answer_label":"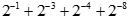","answer_id":51560},{"id":13327,"question":"Lựa chọn nào sau đây là lời giải cho biểu thức logic với biến X bên dưới? Ở đây, A, B và C là các hằng số logic; các toán tử “+”, “∙”, và “¯” biểu thị tương ứng OR logic, AND logic, và NEGATION.\n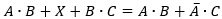","answer_label":"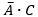","answer_id":51564},{"id":13328,"question":"Alice và Mary có một buổi thi toán. Xác suất đỗ tương ứng của Alice và Mary là 2/3 và 3/5. Đâu là xác suất để ít nhất một trong hai người đỗ?","answer_label":"13/15","answer_id":51568},{"id":13329,"question":"Tần suất tới trong mô hình hàng đợi M/M/1 là phân bố gì?","answer_label":"Phân bố Poisson","answer_id":51572},{"id":13330,"question":"Với phiên bản ngẫu nhiên của thuật toán sắp xếp nhanh, ở đó phần tử chốt được chọn ngẫu nhiên, lựa chọn nào sau đây cho biết các độ phức tạp trung bình và xấu nhất? Ở đây O( ) được dùng để biểu thị thứ tự của mức độ phức tạp.","answer_label":"","answer_id":51575},{"id":13332,"question":"Có một ngôn ngữ được định nghĩa bởi ngữ pháp phi-ngữ cảnh với các luật sinh như sau: \n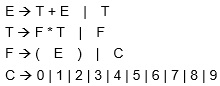\nTrong ngữ pháp này, các ký hiệu chưa kết thúc là E, T, F, và C; các ký hiệu kết thúc là dấu ngoặc, dấu cộng, dấu hoa thị, và các số; E là dấu hiệu bắt đầu. Lựa chọn nào sau đây cho biết rằng biểu thức 7 + 3 * (6 + 4) là một câu của ngôn ngữ này.","answer_label":"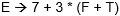","answer_id":51582},{"id":13333,"question":"Cho A là một mảng số nguyên kích thước 10, có phần tử thứ i được biểu diễn bởi A[i] với i=0 cho tới 9, và giá trị khởi tạo của mảng là 0. Đối với một số nguyên dương k, các luật bên dưới xác định phần tử lưu giá trị k. Khi các số nguyên 16, 43, 73, 24, và 85 được xử lý theo thứ tự này, giá trị cuối cùng 85 được lưu trong phần \r\ntử nào? Ở đây, x mod y là phần dư sau khi chia x cho y.\r\n[Các luật]\r\n(1) Nếu A[k mod 10] = 0, thì lưu k trong A[k mod 10].\r\n(2) Ngược lại, nếu A[(k + 1) mod 10] = 0, thì lưu k trong A[(k + 1) mod 10].\r\n(3) Ngược lại, Nếu A[(k + 4) mod 10] = 0, thì lưu k trong A[(k + 4) mod 10].\r\n(4) Ngược lại, loại bỏ k.","answer_label":"A[9]","answer_id":51589},{"id":13334,"question":"Đặc trưng của kiểu dữ liệu danh sách thường được biểu diễn theo hai cách là bằng mảng hoặc bằng con trỏ. Lựa chọn nào sau đây mô tả một đặc điểm của cách biểu diễn bằng mảng?","answer_label":"Bất kể số lượng thực sự các phần tử có trong danh sách, sẽ có một vài khoảng trống không được sử dụng mặc dù các khoảng trống này đã được cấp phát tối đa cho các phần tử","answer_id":51593},{"id":13335,"question":"Để các lưu đồ dưới đây là tương đương, sự kết hợp nào sau đây là thích hợp với các nhãn A và B? Ở đây, biểu thị phủ định của P.\n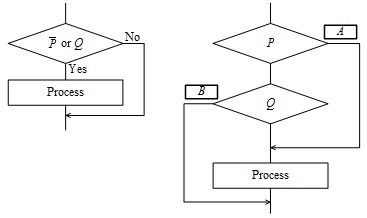","answer_label":"","answer_id":51594},{"id":13341,"question":"Một CPU với một đường ống bốn trạng thái gồm nạp, giải mã, thực thi, và ghi lại, mỗi trạng thái mất tương ứng 10, 6, 8, và 8 ns. Lựa chọn nào sau đây là thời gian thực thi lệnh trung bình tính theo nanô-giây (ns) của CPU? Ở đây, số lệnh được thực thi là đủ lớn. Ngoài ra, phụ phí của tiến trình pipeline là không đáng kể, và tác động gây trễ của tất cả các xung đột được bỏ qua.","answer_label":"10","answer_id":51616},{"id":13342,"question":"Giá trị nào là kết quả biểu thức toán học của việc duyệt trung-thứ-tự cây nhị phân bên dưới?\n","answer_label":"20","answer_id":51619},{"id":13343,"question":"Lựa chọn nào sau đây là kiến trúc máy tính ở đó một bộ xử lý thực thi cùng một lệnh trên nhiều dữ liệu?","answer_label":"SIMD","answer_id":51624},{"id":13344,"question":"Lựa chọn nào sau đây là phương thức đánh địa chỉ cung cấp offset cho nội dung bộ đếm chương trình (PC) để quyết định địa chỉ của toán hạng?","answer_label":"Phương thức đánh địa chỉ tương đối","answer_id":51629},{"id":13345,"question":"Lựa chọn nào sau đây được dùng để dịch địa chỉ logic được sinh ra bởi CPU thành một địa chỉ vật lý?","answer_label":"Memory Management Unit (MMU)","answer_id":51632},{"id":13346,"question":"Lựa chọn nào sau đây là mô tả thích hợp liên quan đến bộ nhớ cache?","answer_label":"Các bộ đa xử lý ở đó bộ nhớ cache cần để đồng bộ các giá trị bên trong cache để duy trì liên lạc","answer_id":51635},{"id":13347,"question":"Lựa chọn nào sau đây là kỹ thuật của việc phân đoạn và lưu trữ dữ liệu trên nhiều ổ đĩa cứng như trong hình minh họa? Ở đây b0 tới b15 thể hiện dãy mà trong đó dữ liệu được lưu trữ trên các đĩa dữ liệu theo từng bit một.\n","answer_label":"Phân dải (Striping)","answer_id":51641},{"id":13348,"question":"Lựa chọn nào sau đây là mô tả thích hợp về thông lượng?","answer_label":"Spooling, liên quan tới việc tạm thời tiết kiệm đầu ra cho một máy in trong một đĩa cứng, rất hữu ích trong việc cải thiện thông lượng.","answer_id":51644},{"id":13429,"question":"Lựa chọn nào sau đây là giá trị thời gian trung bình giữa các lỗi (MTBF) của toàn bộ hệ thống ở đó đơn vị A và đơn vị B được ghép nối tiếp và cả hai đơn vị hoạt động như một hệ thống? Giá trị MTBF của đơn vị A và đơn vị B lần lượt là 200 và 300 giờ.","answer_label":"250","answer_id":51967},{"id":13430,"question":"Khi hệ số nhân của việc xử lý được tăng lên trong bộ nhớ ảo của một hệ thống máy tính, các thao tác page-in và page-out xuất hiện thường xuyên, và tốc độ phản hồi của hệ thống giảm đột ngột. Hiện tượng này gọi là gì?","answer_label":"Thrashing","answer_id":51973},{"id":13431,"question":"Một công ty thực hiện sao lưu toàn bộ vào mỗi tối Chủ Nhật và sao lưu khác biệt vào mỗi tối khác ngoài tối Chủ Nhật. Nếu lỗi xuất hiện vào sáng thứ Tư, các sao lưu nào dưới đây là cần thiết ít nhất để khôi phục hệ thống?","answer_label":"Các sao lưu khác biệt mới nhất và sao lưu toàn bộ mới nhất từ thứ Ba.","answer_id":51976},{"id":13432,"question":"Lựa chọn nào sau đây là giải thích phù hợp về phương pháp lập lịch không ưu tiên?","answer_label":"Một tác vụ không thể di chuyển đến một trạng thái đang hoạt động cho đến khi một tác vụ khác trong trạng thái đang hoạt động hoặc tự nó chuyển sang trạng thái chờ đợi hoặc kết thúc.","answer_id":51978},{"id":13433,"question":"Có một hệ thống được tạo bởi hai (2) CPU, và CPU không dùng sẽ được gán cho một tác vụ mà đối với nó có một yêu cầu thực thi. Khi hai (2) tác vụ A và B chạy trên hệ thống này, các tác vụ này sử dụng duy nhất một tài nguyên chung R. Hình bên dưới cho thấy các giai đoạn sử dụng của các CPU và tài nguyên R với hai tác vụ A và B, và thứ tự các tác vụ này chạy. Khi việc thực thi cả hai tác vụ được bắt đầu đồng thời, mất bao nhiêu thời gian, tính theo mili-giây, cần thiết đến khi hoàn thành việc xử lý cả hai tác vụ? Ở đây, cả CPU và tài nguyên R đều sẵn dùng khi các tác vụ A và B bắt đầu.\n","answer_label":"140","answer_id":51983},{"id":13434,"question":"Theo Định nghĩa Phần mềm Mở của OSI (Open Source Initiative), lựa chọn nào sau đây là mô tả phù hợp liên quan đến giấy phép mã mở?","answer_label":"Giấy phép yêu cầu rằng mã nguồn của một chương trình phải được thực hiện sẵn sàng cho việc sử dụng miễn phí hoặc với một chi phí tái sản xuất hợp lý.","answer_id":51989},{"id":13435,"question":"","answer_label":"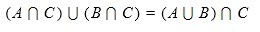","answer_id":51993},{"id":13436,"question":"Đối với hai biến logic X và Y, phép toán logic X NAND Y được định nghĩa là một phép toán tổng hợp NOT (X AND Y). Câu nào sau đây tương đương với phép toán logic X OR Y?","answer_label":"(X NAND X) NAND (Y NAND Y)","answer_id":51995},{"id":13437,"question":"Chuỗi bit nào dưới đây được chấp nhận bởi máy tự động được mô tả trong sơ đồ chuyển trạng thái dưới đây? Ở đây, mỗi chuỗi được xử lý mỗi lần một bit theo thứ tự từ bên trái.\n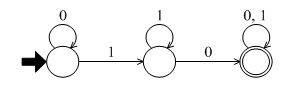","answer_label":"1010","answer_id":52000},{"id":13438,"question":"Lựa chọn nào sau đây là cây tìm kiếm nhị phân có các khóa được gán cho các nút theo thứ tự tự nhiên?","answer_label":"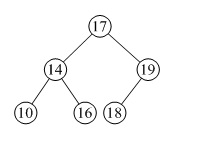","answer_id":52003},{"id":13439,"question":"Có một mảng số nguyên hai chiều A có phần tử (i, j) A[i, j] là 2 × i + j. Giá trị của phần tử A[A[1, 1] × 2, A[2, 2] + 1] là gì?","answer_label":"19","answer_id":52009},{"id":13440,"question":"Hàm F(n) là một hàm số nguyên được định nghĩa đệ quy để tính toán giai thừa của n cho bất kỳ số nguyên âm không n. Đáp án nào sau đây là một biểu thức thích hợp cho khoảng trắng A?\n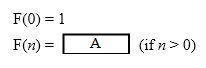","answer_label":"n × F(n - 1)","answer_id":52012},{"id":13441,"question":"Kết quả của thủ tục trong biểu đồ luồng dưới đây là gì, biết rằng x và y là số nguyên dương?\n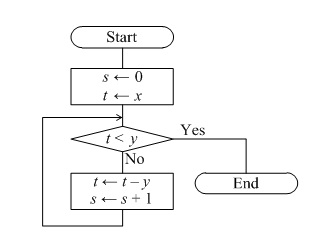","answer_label":"Giá trị của s: Thương của x ÷ y\n\nGiá trị của t: Số dư của x ÷ y","answer_id":52015},{"id":13442,"question":"Lựa chọn nào trong các phương thức đánh địa chỉ sau đây xác định địa chỉ có hiệu lực bằng cách thêm giá trị của thanh ghi địa chỉ lệnh (bộ đếm chương trình) vào giá trị được ghi trong phần địa chỉ của lệnh?","answer_label":"Địa chỉ tương đối","answer_id":52021},{"id":13443,"question":"Một máy tính có hai mức bộ nhớ, bộ nhớ cache và bộ nhớ chính, với thời gian truy cập là 0,01 μs và 0,1 μs tương ứng. Nếu tỷ lệ truy cập của bộ nhớ cache là 90%, lựa chọn nào sau đây là thời gian truy cập bộ nhớ trung bình cho hệ thống này? Trong trường hợp này, nếu dữ liệu nằm trong bộ nhớ cache, bộ xử lý sẽ truy cập dữ liệu trực tiếp với thời gian truy cập là 0,01 μs. Tuy nhiên, nếu truy cập bộ nhớ cache thất bại, trước tiên dữ liệu phải được chuyển từ bộ nhớ chính vào bộ nhớ cache, sau đó được truy cập từ bộ nhớ cache. Do đó, thời gian truy cập là 0.11 μs.","answer_label":"0,020 µs","answer_id":52024},{"id":13444,"question":"Thiết bị nào sau đây là thiết bị đầu ra cho máy tính?","answer_label":"Máy in","answer_id":52028},{"id":13445,"question":"Lựa chọn nào sau đây là độ trễ quay vòng trung bình của ổ cứng tính bằng mili giây khi tốc độ quay là 2000 vòng/phút?","answer_label":"15","answer_id":52031},{"id":13446,"question":"Điều nào sau đây là một phương pháp làm tăng tốc độ dữ liệu vào / ra bằng cách chia dữ liệu tuần tự logic và ghi dữ liệu được chia thành nhiều đĩa cứng?","answer_label":"Striping","answer_id":52036},{"id":13447,"question":"Điều nào sau đây là một đặc tính của cụm cấu hình HA (High Availability) dựa trên một phương pháp dự phòng nóng khi nó được so sánh với cụm cấu hình phân phối tải sử dụng bộ cân bằng tải?","answer_label":"Một máy chủ có cùng đặc điểm kỹ thuật là cần thiết như một máy chủ thứ cấp, nhưng vì các tiến trình được chuyển qua máy chủ thứ cấp trong trường hợp hỏng hóc chính nên thông lượng có thể được duy trì ngay cả trong trường hợp hỏng hóc.","answer_id":52038},{"id":13448,"question":"Câu nào sau đây là mô tả thích hợp liên quan đến độ sẵn sàng của hệ thống?","answer_label":"Nếu MTTR có thể được rút ngắn mà không thay đổi MTBF, độ sẵn sàng của hệ thống được cải thiện.","answer_id":52043},{"id":13449,"question":"Phương án nào sau đây là lỗi trang trong một hệ thống bộ nhớ ảo?","answer_label":"Truy cập vào một trang được ánh xạ trong bộ nhớ ảo, nhưng không được tải trong bộ nhớ vật lý","answer_id":52046},{"id":13450,"question":"Trong một tệp tin tổ chức trực tiếp có nhiều địa chỉ lưu trữ từ một (1) đến sáu (6), dữ liệu được lưu trữ dưới các điều kiện phía dưới đây. Giá trị khóa nào của dữ liệu được lưu trữ trong địa chỉ một (1)?\n\n[Điều kiện]\n\n(1) Dữ liệu được lưu trữ theo thứ tự các giá trị khóa ba (3), bốn (4), tám (8), 13, 14, và 18.\n\n(2) Địa chỉ lưu trữ là giá trị mà phần còn lại thu được bằng cách chia giá trị dữ liệu quan trọng cho năm (5) và sau đó thêm một (1) vào.\n\n(3) Nếu địa chỉ lưu trữ đã bị chiếm, dữ liệu được lưu trữ trong địa chỉ kế tiếp. Quá trình này được lặp lại cho đến khi dữ liệu được lưu trữ. Địa chỉ tiếp theo của địa chỉ cuối cùng là địa chỉ đầu tiên. \n\n(4) Trong trạng thái ban đầu, không có gì được lưu trữ trong tệp tin.","answer_label":"13","answer_id":52051},{"id":13451,"question":"Điều nào sau đây được phân loại như một chức năng của một công cụ kiểm tra tĩnh?","answer_label":"Phát hiện một lỗi trong chương trình bằng cách phân tích mã nguồn","answer_id":52055},{"id":13452,"question":"Với thủ tục chuyển giữa nhiều chương trình của các tiến trình thể hiện trong hình bên dưới, đáp án nào sau đây là sự kết hợp thích hợp của việc xử lý hệ điều hành từ A đến C?\n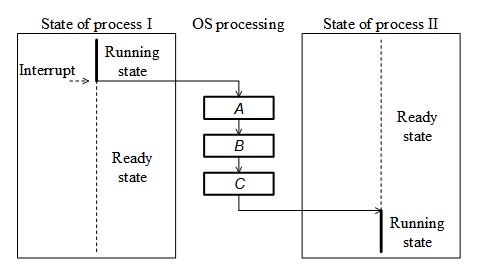","answer_label":"A: Lưu lại trạng thái chạy\r\nB: Lựa chọn tiến trình\r\nC: Phục hồi trạng thái chạy","answer_id":52060},{"id":13453,"question":"Điều nào sau đây là chức năng thích hợp của trình liên kết?","answer_label":"Tạo một mô-đun tải từ nhiều mô-đun đối tượng bằng cách thực hiện các hoạt động như phân giải chéo tham chiếu","answer_id":52062},{"id":13454,"question":"Một bộ chuyển đổi D/A với sự phân giải của 8 bit tạo ra một điện áp đầu ra 0 vôn cho một giá trị đầu vào số là 0, và điện áp đầu ra 2,5 vôn cho một giá trị đầu vào số 128. Khi bit 1 thấp nhất của giá trị đầu vào số được thay đổi, đáp án nào sau đây là sự thay đổi (tính bằng vôn) của điện áp đầu ra được tạo ra bởi bộ chuyển đổi D/A?","answer_label":"2.5/128","answer_id":52066},{"id":13455,"question":"Các mạch cộng bán phần trong sơ đồ dưới đây cộng hai (2) số nhị phân một chữ số x và y, và có z (số đầu tiên của tổng) và c (bit nhớ) là đầu ra. Đáp án nào sau đây là sự kết hợp thích hợp của các thiết bị cổng A và B?\n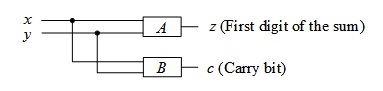","answer_label":"A: Exclusive logical sum (XOR)\r\nB: Logical product (AND)","answer_id":52070},{"id":13456,"question":"Mạch nào sau đây tương đương với mạch logic được hiển thị bên dưới?\n","answer_label":"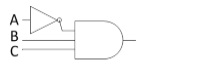","answer_id":52076},{"id":13457,"question":"Khi dữ liệu đặt hàng ở định dạng dưới đây được nhập, lựa chọn nào sau đây là một phép kiểm tra thích hợp để kiểm tra xem giá trị của trường Order date là vào ngày làm việc trùng hay trước ngày nhập?\n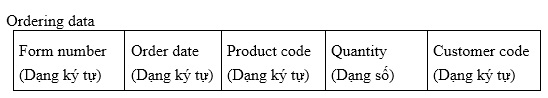","answer_label":"Kiểm tra logic","answer_id":52081},{"id":13458,"question":"Lựa chọn nào sau đây là một quá trình trong PCM để lấy các giá trị tương tự từ tín hiệu âm thanh trong một khoảng thời gian định kỳ?","answer_label":"Lấy mẫu","answer_id":52085},{"id":13459,"question":"Thuộc tính nào sau đây của giao dịch cơ sở dữ liệu đề cập đến khả năng hệ thống có thể khôi phục lại một giao dịch đã cam kết khi hệ thống hoặc phương tiện lưu trữ thất bại?","answer_label":"Độ bền","answer_id":52088},{"id":13460,"question":"Có một bảng “Delivery” có sáu (6) bản ghi. Điều nào sau đây là sự phụ thuộc chức năng mà bảng này thỏa mãn? Ở đây, “X → Y” chỉ ra rằng X quyết định chức năng Y.\n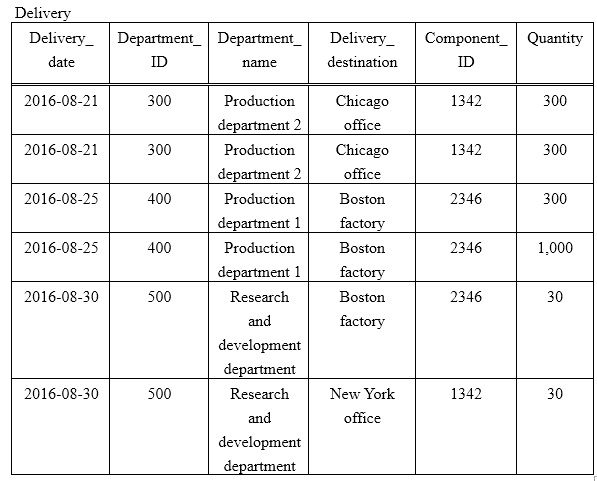","answer_label":"Delivery_destination → Component_ID","answer_id":52091},{"id":13461,"question":"Lựa chọn nào trong số các phương pháp kết hợp hai (2) bảng trong một RDBMS sau đây là mô tả của phương pháp nối hợp nhất sắp xếp?","answer_label":"Tất cả các hàng trong các bảng được sắp xếp lại theo các giá trị trong cột để được nối, và chúng được nối theo thứ tự từ trên xuống.","answer_id":52094},{"id":13462,"question":"Khi câu lệnh SQL được hiển thị bên dưới được thực hiện trên bảng “Employee” và bảng “Department” đáp án nào là kết quả của câu lệnh? \n\nSELECT COUNT(*) FROM Employee, Department\n\n WHERE Employee.Department = Department.Department_name AND \n\t\t\t\t\t \n Department.Floor = 2\n","answer_label":"3","answer_id":52100},{"id":13463,"question":"Trong một hệ thống cơ sở dữ liệu phân tán, lựa chọn nào sau đây là một phương pháp để hoàn thiện xử lý cập nhật khi một truy vấn được tạo cho nhiều trang thực hiện một chuỗi các xử lý giao dịch như việc hoàn thiện có khả thi hay không và việc hoàn thiện có thể thực hiện trên tất cả các trang hay không?","answer_label":"Xác nhận hai pha","answer_id":52105},{"id":13464,"question":"Giao thức TCP/IP nào sau đây được sử dụng để chỉ định địa chỉ IP động?","answer_label":"DHCP","answer_id":52107},{"id":13465,"question":"Trong mô hình phân cấp mạng TCP/IP, tên của Thiết bị A kết nối hai phân đoạn LAN ở tầng Internet là gì?\n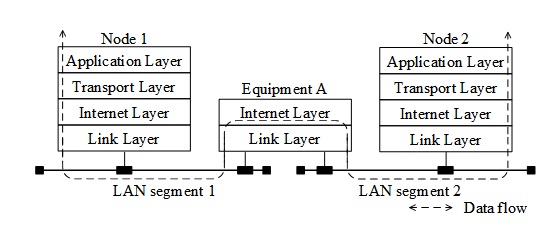","answer_label":"Router","answer_id":52112},{"id":13466,"question":"Lựa chọn nào sau đây là cặp địa chỉ IP thuộc cùng một subnet, khi mặt nạ mạng con là 255.255.255.240?","answer_label":"192.168.1.17 và 192.168.1.29","answer_id":52115},{"id":13467,"question":"Mô hình phân phối nào sau đây sử dụng ARP?","answer_label":"Unicast","answer_id":52121},{"id":13468,"question":"Một máy tính cá nhân và một máy chủ web đang giao tiếp qua HTTP. Khi một gói tin yêu cầu được gửi từ máy tính tới máy chủ web, lựa chọn nào sau đây là kết hợp số cổng của gói phản hồi. Ở đây, số của cổng nguồn và cổng đích của gói tin yêu cầu là 50001 và 80 tương ứng","answer_label":"Số của cổng nguồn (Máy chủ web): 80\n\nSố của cổng đích (Máy tính cá nhân): 50001","answer_id":52122},{"id":13469,"question":"Công nghệ nào sau đây là một công nghệ ngăn chặn việc nhập thông tin tự động từ một chương trình bằng cách yêu cầu nhập các ký tự từ một hình ảnh bị méo hoặc một hình ảnh mà một số phần của nó bị ẩn? Công nghệ này dựa trên sự khác biệt về nhận thức của những hình ảnh này giữa con người và các chương trình.","answer_label":"CAPTCHA","answer_id":52126},{"id":13470,"question":"Lựa chọn nào sau đây là một cuộc tấn công đe dọa đến tính “toàn vẹn” của thông tin?","answer_label":"Giả mạo một trang web","answer_id":52131},{"id":13471,"question":"Lựa chọn nào sau đây là tên của cuộc tấn công mà hành vi được thực hiện nhằm đặt một trang web độc hại lên đầu của kết quả tìm kiếm của một trang web?","answer_label":"Nhiễm độc SEO","answer_id":52136},{"id":13472,"question":"Lựa chọn nào dưới đây là giải thích thích hợp cho một cuộc tấn công SQL injection?","answer_label":"Một cuộc tấn công mà nếu có một lỗi trong cách thức gọi cơ sở dữ liệu từ một ứng dụng web, kẻ tấn công có thể thực hiện truy xuất trái phép, sửa đổi và xóa dữ liệu trong cơ sở dữ liệu bằng cách nhập một chuỗi ký tự độc hại bằng ngôn ngữ thao tác dữ liệu của lời gọi","answer_id":52140},{"id":13473,"question":"Trong một giao dịch thương mại điện tử sử dụng mật mã khoá công khai, vai trò của cơ quan chứng nhận (CA) là gì?","answer_label":"Cấp chứng thư số cho khoá công khai của các bên tham gia giao dịch","answer_id":52143},{"id":13474,"question":"Điều nào sau đây là mục đích thích hợp để sử dụng giá trị băm trong an ninh số?","answer_label":"Để chứng minh tính giống nhau giữa bản gốc và bản sao của dữ liệu có thể được sử dụng làm bằng chứng","answer_id":52147},{"id":13475,"question":"Lựa chọn nào sau đây là hoạt động thích hợp để xác thực người dùng sử dụng thẻ IC và mã PIN?","answer_label":"Khi phát hành thẻ IC, mã PIN không được đính kèm nhưng được thông báo cho người dùng thông qua kênh khác.","answer_id":52153},{"id":13476,"question":"Khi phần mềm độc hại đã xâm nhập thành công vào máy PC giao tiếp với máy chủ điều khiển và kiểm soát trên Internet, điều nào sau đây là lý do để sử dụng số cổng TCP 80 là cổng đích trong hầu hết các trường hợp?","answer_label":"Trong trường hợp cổng này được sử dụng để duyệt các trang web, khả năng cao là việc truyền thông sẽ được tường lửa cho phép.","answer_id":52154},{"id":13477,"question":"Khi một ổ đĩa cứng hoạt động bình thường của một máy tính mà trên đó các tập tin bí mật được lưu trữ được chuyển giao cho một nhà cung cấp chất thải công nghiệp, đáp án nào sau đây là một biện pháp đối phó thích hợp để chống rò rỉ thông tin?","answer_label":"Ghi đè lên tất cả các vùng trên đĩa cứng với một chuỗi bit ngẫu nhiên nhiều lần","answer_id":52161},{"id":13478,"question":"Lựa chọn nào sau đây là lý do VLAN được sử dụng?","answer_label":"Để giảm lưu lượng mạng","answer_id":52163},{"id":13479,"question":"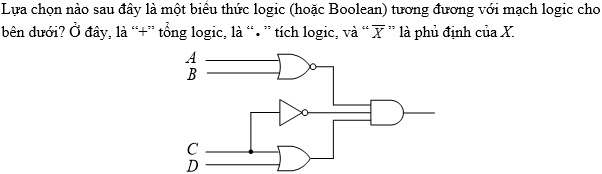","answer_label":"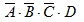","answer_id":52169},{"id":13480,"question":"Lựa chọn nào sau đây là một mạch tuần tự mà có hai (2) trạng thái ổn định?","answer_label":"Flip-flop","answer_id":52171},{"id":13481,"question":"Lựa chọn nào sau đây là đầu vào thích hợp đối với một màn hình bảy đoạn dương cực thông dụng để hiển thị ký tự được xem như đầu ra? Ở đây, A là bit có trọng số lớn nhất (MSB) và G là bit có trọng số nhỏ nhất (LSB).\n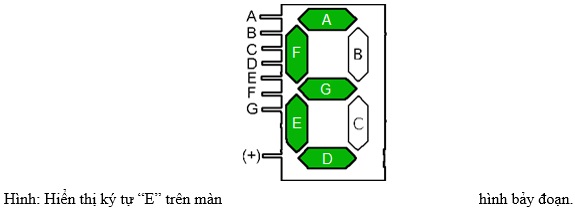","answer_label":"0110000","answer_id":52174},{"id":13482,"question":"Lựa chọn nào sau đây là thích hợp đối với các font outline hơn là các font bitmap?","answer_label":"Để làm lớn các ký tự theo một tỷ lệ cho trước","answer_id":52181},{"id":13483,"question":"Lựa chọn nào sau đây là giải thích về kỹ thuật tạo chất liệu?","answer_label":"Nó diễn tả các đặc điểm bề mặt nhờ việc dán một ảnh trên bề mặt của một vật thể ba chiều.","answer_id":52185},{"id":13484,"question":"Lựa chọn nào sau đây là mục đích thích hợp để chấp nhận một kiến trúc lược đồ ba-lớp của DBMS?","answer_label":"Để lấy được một bảng mới từ một bảng nguồn thông qua một thao tác quan hệ, nếu như bảng mới thực sự tồn tại","answer_id":52187},{"id":13485,"question":"Lựa chọn nào sau đây là một phương pháp phù hợp dùng để xóa bỏ dư thừa dữ liệu trong các hệ thống cơ sở dữ liệu quan hệ?","answer_label":"Chuẩn hóa","answer_id":52193},{"id":13486,"question":"Đâu là mức độ tham gia thích hợp của quan hệ “Register” giữa thực thể “Customer” và thực thể “Car” mà khớp với biểu đồ bên dưới? Ở đây, “A..B” và “C..D” tương ứng chỉ ra mức độ tham gia liên kết tối đa và tối thiểu vào quan hệ.","answer_label":"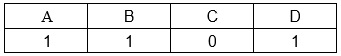","answer_id":52195},{"id":13487,"question":"Trong một lược đồ quan hệ R = (A, B, C, D, E), cho các phụ thuộc hàm như sau:\nA→ BC\nCD→ E\nB → D\nE → A\nLựa chọn nào sau đây là một sự kết hợp của hai khóa dự tuyển của R?","answer_label":"A và E","answer_id":52198},{"id":13488,"question":"Lựa chọn nào sau đây là mục tiêu chính của hỗ trợ giao tác trong một hệ quản trị cơ sở dữ liệu?","answer_label":"Để đảm bảo rằng hoặc là tất cả các cập nhật tương ứng với một giao tác cho trước được làm hoặc không cập nhật nào cả","answer_id":52202},{"id":13489,"question":"Lựa chọn nào sau đây là chức năng tầng liên kết dữ liệu mà cho phép bên nhận điều khiển lượng dữ liệu sẽ được nhận từ bên gửi?","answer_label":"Điều khiển luồng","answer_id":52208},{"id":13490,"question":"TCP/IP là một tập hợp được phân tầng của các giao thức truyền thông bao gồm tầng Giao tiếp mạng, tầng Internet, tầng Giao vận, và tầng Ứng dụng. Lựa chọn nào sau đây là một sự kết hợp của các giao thức tầng Giao vận?","answer_label":"TCP, UDP","answer_id":52213},{"id":13491,"question":"Lựa chọn nào sau đây chịu trách nhiệm chuyển một tên miền tới một địa chỉ IP tương ứng?","answer_label":"Máy chủ DNS","answer_id":52215},{"id":13492,"question":"Lựa chọn nào sau đây là một mô tả thích hợp của Giao thức điều khiển truyền (TCP)?","answer_label":"Nó đảm bảo độ tin cậy bằng cách truyền lại các phân đoạn dữ liệu nếu bất kỳ trong chúng bị mất.","answer_id":52218},{"id":13493,"question":"Trên Internet, đôi khi một người cố tải một trang Web bằng cách chỉ rõ một URL kiểu: http://www.jitec.ipa.go.jp/, trang không thể hiển thị và trang lỗi xuất hiện thay vào đó. Tuy nhiên, người dùng có thể duyệt đúng trang bằng cách chỉ rõ địa chỉ IP kiểu: http://118.151.146.137/. Tầng TCP/IP nào sau đây chịu trách nhiệm về vấn đề này?","answer_label":"Tầng Ứng dụng","answer_id":52222},{"id":13494,"question":"Lựa chọn nào sau đây là một phương pháp thích hợp của việc xác thực người dùng nhờ dùng một mật khẩu?","answer_label":"Mật khẩu được chuyển đổi thành một giá trị băm và được đăng ký, và mật khẩu được nhập trong quá trình xác thực được chuyển đổi bởi hàm băm và được so sánh","answer_id":52228},{"id":13495,"question":"Khi phần mềm độc hại mà thực hiện một xâm nhập thành công vào một máy tính giao tiếp với một máy chủ ra-lệnh-và-kiểm-soát trên Internet, lựa chọn nào sau đây là một lý do cho việc sử dụng cổng TCP 80 như là cổng đích cho hầu hết trường hợp?","answer_label":"Vì cổng này được sử dụng để duyệt các trang web, có một xác suất cao mà truyền thông được cho phép bởi tường lửa","answer_id":52230},{"id":13496,"question":"Lựa chọn nào sau đây là một kỹ thuật mà được phân loại như là kỹ nghệ lừa đảo qua mạng xã hội?","answer_label":"Thu được mật khẩu bằng cách gọi người dùng và giả vờ là một quản trị viên hệ thống","answer_id":52234},{"id":13497,"question":"Khi ông A, người có một chứng chỉ số, dùng một email để đặt hàng với cửa hàng B, ông ta dùng khóa riêng của mình và ký số email. Cửa hàng B sau đó dùng khóa công khai của ông A để xác nhận chữ ký. Lựa chọn nào sau đây có thể đạt được nhờ dùng phương pháp này? Ở đây, chỉ ông A có thể dùng khóa riêng của mình.","answer_label":"Nó được xác nhận rằng đơn hàng đang đến cửa hàng B là một đơn hàng từ ông A","answer_id":52239},{"id":13498,"question":"Lựa chọn nào sau đây là một mô tả thích hợp của đánh giá rủi ro?","answer_label":"Thứ tự ưu tiên của ứng phó với rủi ro được xác định bởi kích thước của các rủi ro dựa trên giá trị dự kiến bị mất và xác suất xảy ra","answer_id":52245},{"id":13499,"question":"Lựa chọn nào sau đây là một mô tả về các biện pháp chống rò rỉ thông tin?","answer_label":"Các nội dung của đĩa cứng của một máy tính xách tay được mã hóa","answer_id":52248},{"id":13500,"question":"Có một mạng mà được chia thành ba (3) phân đoạn, cụ thể là, phân đoạn bên ngoài, vùng phi quân sự (DMZ), và mạng nội bộ bên trong một (1) tường lửa. Trong mạng, khi một dịch vụ cho người dùng được công bố trên Internet bằng cách sử dụng một hệ thống gồm máy chủ web và máy chủ cơ sở dữ liệu (CSDL) có chứa dữ liệu quan trọng, lựa chọn nào sau đây là phương pháp cài đặt máy chủ thích hợp nhất để bảo vệ dữ liệu quan trọng khỏi việc truy cập trái phép từ Internet? Ở đây, chỉ có một giao thức cụ thể được tường lửa cho phép giao tiếp giữa các phân đoạn bên ngoài và DMZ, và giữa DMZ và mạng nội bộ, và giao tiếp giữa các phân đoạn bên ngoài và mạng nội bộ không được phép.","answer_label":"Máy chủ Web được cài đặt trong DMZ, và máy chủ CSDL được cài đặt trong một mạng bên trong","answer_id":52253},{"id":13501,"question":"Lựa chọn nào sau đây là một mục tiêu của việc sử dụng một WAF (Tường lửa ứng dụng Web)?","answer_label":"Một tấn công dựa trên một lỗ hổng gây cho một máy chủ Web và một ứng dụng Web bị khóa lại.","answer_id":52254},{"id":13502,"question":"Lựa chọn nào sau đây là một giải thích của phương pháp so khớp mẫu được sử dụng bởi phần mềm chống virus?","answer_label":"Một virus bị phát hiện thông qua việc so sánh với chữ ký của một virus đã được biết.","answer_id":52261},{"id":13503,"question":"Lựa chọn nào sau đây có thể được cài đặt với các chức năng của HTTPS (HTTP over SSL/TLS)?","answer_label":"Mã hóa giao tiếp giữa một máy chủ Web và một trình duyệt","answer_id":52263},{"id":13504,"question":"Theo tiêu chuẩn ISO/IEC 25010 (Hệ thống và công nghệ phần mềm – Hệ thống và Yêu cầu chất lượng phần mềm và Đánh giá (SQuaRE) – Hệ thống và các mô hình chất lượng phần mềm), lựa chọn nào sau đây là một đặc tính chất lượng thích hợp mà có nghĩa là mức độ mà một sản phẩm hoặc hệ thống cung cấp chức năng thỏa mãn các quy định và bao hàm cần thiết khi được sử dụng trong các điều kiện xác định?","answer_label":"Phù hợp chức năng","answer_id":52266},{"id":13505,"question":"Trong kiểm thử đơn vị, các hoạt động nào sau đây là bộ phận của “kiểm thử hộp trắng”?","answer_label":"Kiểm thử điều kiện","answer_id":52271},{"id":13506,"question":"Lựa chọn nào sau đây là một cơ chế cho phép một số lớp con có chung lớp cha mẹ được định nghĩa lại cùng một phương pháp với các hành vi khác nhau?","answer_label":"Đa hình","answer_id":52277},{"id":13507,"question":"Việc kiểm thử tích hợp đối với một phần mềm gồm các mô-đun bố trí theo cấu trúc phân cấp được tiến hành từ một mô-đun cấp thấp. Trong trường hợp đó, lựa chọn nào sau đây là mô đun kiểm thử được dùng thay thế cho một mô-đun cấp cao hơn?","answer_label":"Phần mềm điều khiển","answer_id":52278},{"id":13508,"question":"Mẫu thiết kế có cấu trúc nào sau đây cho phép các lớp có giao diện không tương thích làm việc với nhau và điều đó có thể thực hiện được trong cả hai dạng sơ đồ dưới đây?\n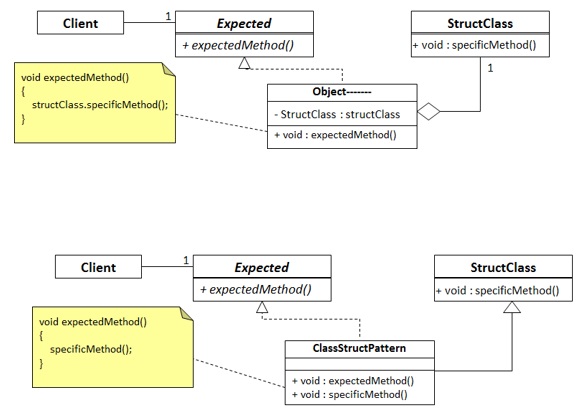","answer_label":"Adapter","answer_id":52282},{"id":13509,"question":"Thuật ngữ nào sau đây chỉ tiến trình tạo ra một sơ đồ lớp của UML từ một chương trình?","answer_label":"Kỹ thuật đảo ngược","answer_id":52289},{"id":13510,"question":"Lựa chọn nào sau đây là một hành động được thực hiện trong quá trình tạo cấu trúc phân chia công việc (WBS) quá trình tạo trong việc quản lý phạm vi quản lý?","answer_label":"Chia nhỏ công việc theo thứ bậc","answer_id":52293},{"id":13511,"question":"Biểu đồ mũi tên dưới đây cho thấy kế hoạch ban đầu của một dự án.\n","answer_label":"Ngày hoàn thành dự án không được sớm hơn cũng không bị chậm đi","answer_id":52297},{"id":13512,"question":"Một công ty đang lập kế hoạch phát triển công việc A. Người phát triển thứ nhất có thể thực hiện công việc này một mình trong 10 ngày. Hơn nữa, người phát triển thứ nhất có thể thực hiện công việc này trong 6 ngày với người phát triển thứ hai. Vậy người phát triển thứ hai cần bao nhiêu ngày để thực hiện công việc này một mình? Ở đây, vì phải giao tiếp, nên hiệu quả công việc của mỗi người phát triển bị giảm 10% và phần thập phân được làm tròn.","answer_label":"12","answer_id":52300},{"id":13513,"question":"Lựa chọn nào sau đây là câu mô tả phù hợp nhất về sự khác biệt giữa COCOMO trung gian và COCOMO II?","answer_label":"COCOMO trung gian gồm một mô hình tổng thể dựa trên các dòng lệnh, còn COCOMO II gồm ba mô hình khác nhau, tùy thuộc vào kiến thức đã có về sản phẩm sẽ xây dựng","answer_id":52302},{"id":13514,"question":"Theo tiêu chuẩn ISO/IEC 20000-1 (công nghệ thông tin - Quản lý dịch vụ - Phần 1: Các yêu cầu của Hệ thống quản lý dịch vụ), lựa chọn nào sau đây là mô tả phù hợp về quản lý vấn đề?","answer_label":"Đó là một quy trình được dùng để xác định nguyên nhân chính của sự cố, giảm thiểu các tác động tiêu cực của sự cố, và ngăn chặn nó xảy ra lần nữa","answer_id":52307},{"id":13515,"question":"Thuật ngữ nào sau đây chỉ lượng giao dịch dữ liệu có thể chấp nhận mất mát sau khi thời gian chết xảy ra?","answer_label":"Mục tiêu điểm phục hồi (RPO)","answer_id":52311},{"id":13516,"question":"Trong các Thư viện hạ tầng cơ sở công nghệ thông tin (ITIL), việc hạ thấp chỉ tiêu về tính duy trì đưa ra như một ví dụ về chỉ số thực hiện chính (KPI) đối với việc quản lý sự hiện hữu. Lựa chọn nào sau đây tương ứng với chỉ số này?","answer_label":"Thời gian trung bình để khôi phục dịch vụ","answer_id":52316},{"id":13517,"question":"Trong số các mục mà kiểm toán viên hệ thống ghi vào báo cáo kiểm toán, lựa chọn nào sau đây trệch khỏi phạm vi công việc của kiểm toán viên?","answer_label":"Ra lệnh cải tiến","answer_id":52319},{"id":13518,"question":"Khi kiểm toán việc quản lý tài sản phần mềm, điểm nào sau đây là điểm thích hợp nhất cần được kiểm tra?","answer_label":"Kiểm tra xem các chứng từ, như giấy phép phần mềm, có còn hợp thức không","answer_id":52323},{"id":13519,"question":"Lựa chọn nào sau đây là đối tượng kiểm toán hệ thống nhằm đánh giá và kiểm tra việc kiểm soát nội bộ liên quan đến CNTT?","answer_label":"Các phương pháp nhằm đảm bảo tính chính xác trong các quy trình đầu vào và cập nhật cơ sở dữ liệu do bộ phận bán hàng thực hiện","answer_id":52326},{"id":13520,"question":"Lựa chọn nào sau đây là một trình tự hợp lý của thủ tục lập mô hình kinh doanh?\n\tA.\tGắn quy trình nghiệp vụ với một tổ chức hiện tại\n\tB.\tLàm rõ quy trình nghiệp vụ\n\tC.\tGắn quy trình nghiệp vụ với một hệ thống thông tin\n\tD.\tLàm rõ lớp dữ liệu (mô hình thông tin)\n\tE.\tGắn quy trình nghiệp vụ với một lớp dữ liệu","answer_label":"B → D → E → C → A","answer_id":52331},{"id":13521,"question":"Lựa chọn nào sau đây là một mô tả thích hợp về điện toán đám mây?","answer_label":"Đó là một mô hình cho phép việc truy cập phổ biến, thuận tiện, theo yêu cầu vào một vùng chia sẻ chứa các tài nguyên máy tính có thể cấu hình được","answer_id":52336},{"id":13522,"question":"Lựa chọn nào sau đây gồm các tầng được quản lý bởi nhà cung cấp khi sử dụng IaaS?","answer_label":"Ảo hóa, Các máy phục vụ, Lưu trữ, Kết nối mạng","answer_id":52341},{"id":13523,"question":"Lựa chọn nào sau đây là công việc được thực hiện khi xác định các yêu cầu không liên quan đến chức năng?","answer_label":"Tạo ra các tiêu chí và tiêu chuẩn phát triển dựa trên ngôn ngữ lập trình được sử dụng trong phát triển hệ thống","answer_id":52343},{"id":13524,"question":"Lựa chọn nào sau đây là một lời giải thích hợp lý về sản phẩm dấu hỏi (?) trong ma trận quản lý danh mục sản phẩm (PPM)?","answer_label":"Nó cần đầu tư đáng kể để nuôi dưỡng do tỷ lệ thị phần nhỏ và tốc độ tăng trưởng thị trường cao","answer_id":52348},{"id":13525,"question":"Một công ty may mặc và bán hàng được đánh giá bằng cách phân tích chuỗi giá trị. Khi phân loại các hoạt động trong công ty thành nội vụ, sản xuất, ngoại vụ, bán hàng/ tiếp thị, và các dịch vụ, lựa chọn nào sau đây được phân loại như là các hoạt động nội vụ?","answer_label":"Hoạt động đặt hàng nguyên liệu, thanh tra và quản lý hàng tồn kho","answer_id":52351},{"id":13526,"question":"Lựa chọn nào sau đây là phương pháp thiết lập giá dựa trên việc định giá cộng thêm vào chi phí?","answer_label":"Trên cơ sở chi phí sản xuất và chi phí vận hành, giá cả được thiết lập bằng cách kết hợp biên lợi nhuận mong muốn.","answer_id":52355},{"id":13527,"question":"Lựa chọn nào sau đây là giải thích về phương tiện huy động thông tin từ khách hàng (CGM)?","answer_label":"Nó cho phép phân phối nội dung số do cá nhân người đọc tạo ra, và chia sẻ nội dung đó giữa các người dùng.","answer_id":52359},{"id":13528,"question":"Lựa chọn nào sau đây là lời giải thích về sàn giao dịch điện tử?","answer_label":"Đó là một phương pháp mà trong đó nhiều người bán và người mua gặp nhau ở chợ được thiết lập trên Internet và mua bán trực tiếp không qua phân phối trung gian","answer_id":52362},{"id":13529,"question":"Lựa chọn nào sau đây là lời giải thích về lưới thông minh?","answer_label":"Đó là một hệ thống nhằm sử dụng năng lượng có thể tái chế, cung ứng nguồn điện ổn định, và điều chỉnh nhu cầu tối ưu thông qua kiểm soát tích hợp việc phát điện và tiêu thụ điện dựa trên công nghệ truyền thông và xử lý thông tin.","answer_id":52366},{"id":13530,"question":"Sản phẩm A, B, C và D là được giới thiệu ra thị trường. Bảng dưới đây cho thấy lợi nhuận dự kiến cho từng sản phẩm với ba (3) dự báo bán hàng (cao, trung bình, và thấp) ước tính sẽ xảy ra với xác suất trong bảng. Sản phẩm nào sau đây là sản phẩm được kỳ vọng sẽ có lợi nhuận cao nhất theo nguyên tắc giá trị kỳ vọng?\n","answer_label":"B","answer_id":52371},{"id":13531,"question":"Lựa chọn nào sau đây là một biểu đồ Pareto thích hợp?","answer_label":"","answer_id":52375},{"id":13532,"question":"Với số lượng chuyển sang từ tháng trước và số lượng giao dịch hàng tồn kho của một sản phẩm được thể hiện như trong bảng dưới đây, đơn giá sản phẩm cho giai đoạn tiếp theo tính theo phương pháp bình quân định kỳ là bao nhiêu?\n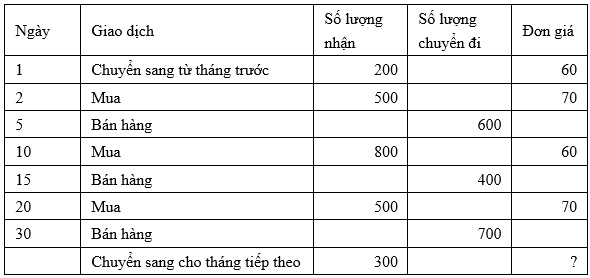","answer_label":"65,00","answer_id":52379},{"id":13533,"question":"Báo cáo kiểm kê kho của Công ty Bất động sản Build-Up mô tả tình trạng tồn kho từ đầu năm 2014. Nếu công ty này sử dụng phương pháp vào trước - ra trước (FIFO) để định giá tài sản kiểm kê, thì giá trị hàng tồn kho vào cuối năm 2014 là bao nhiêu?\n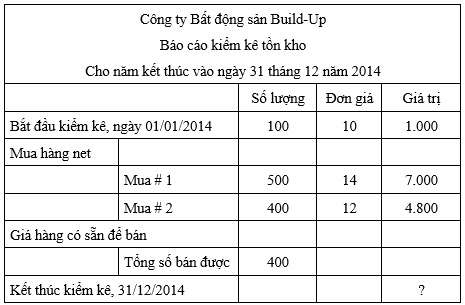","answer_label":"7600","answer_id":52383},{"id":13534,"question":"Một công ty có kế hoạch cung cấp một sản phẩm với chi phí cố định là 128.000 đôla, chi phí biến đổi trên một đơn vị sản phẩm là 48 đôla, và giá bán mỗi đơn vị sản phẩm là 80 đô. Vậy điểm hòa vốn là bao nhiêu?","answer_label":"320.000","answer_id":52387},{"id":13535,"question":"Lựa chọn nào sau đây là một hành vi phạm tội liên quan đến virus máy tính theo Công ước về tội phạm công nghệ?","answer_label":"Một người tìm thấy virus của một người lạ, lưu trữ virus đó nhằm mục đích sau này có thể chạy nó trên máy tính của người khác","answer_id":52392},{"id":13536,"question":"Điều nào sau đây phải được khách hàng chấp thuận khi thiết kế bên ngoài của một hệ thống được hoàn thành?","answer_label":"Bố trí màn hình","answer_id":52396},{"id":13537,"question":"Lựa chọn nào sau đây là sự kết hợp thích hợp của các khái niệm cơ bản về hướng đối tượng?","answer_label":"Trừu tượng, đóng gói, kế thừa, lớp","answer_id":52398},{"id":13538,"question":"Để tăng tính độc lập mô đun, mức độ khớp nối mô đun phải thấp. Phương pháp trao đổi thông tin giữa các mô đun nào sau đây có mức khớp nối mô đun thấp nhất?","answer_label":"Chỉ các mục dữ liệu cần thiết cho đầu vào và đầu ra được truyền như là đối số giữa các mô-đun","answer_id":52403},{"id":13539,"question":"Kiểm thử tích hợp cho phần mềm gồm các mô-đun được sắp xếp theo cấu trúc phân cấp được thực hiện từ một mô-đun cấp cao. Trong trường hợp như vậy, lựa chọn nào sau đây là một mô đun kiểm thử được sử dụng thay thế cho một mô-đun cấp thấp?","answer_label":"Stub","answer_id":52409},{"id":13540,"question":"Phương pháp nào dưới đây là phương pháp sử dụng công cụ mô hình hóa để tạo ra một tài liệu thiết kế được mô tả với sơ đồ E-R hoặc các biểu diễn khác từ thông tin định nghĩa trong cơ sở dữ liệu hoạt động?","answer_label":"Kỹ nghệ ngược","answer_id":52412},{"id":13541,"question":"Lựa chọn nào sau đây là mô tả thích hợp về Ma trận Phân công Trách nhiệm được sử dụng cho quản lý nguồn nhân lực dự án?","answer_label":"Phân bổ gói công việc cho những người chịu trách nhiệm về công việc dự án.","answer_id":52415},{"id":13542,"question":"Cấu trúc nào sau đây mô tả mối quan hệ giữa hoạt động dự án và các đơn vị của dự án sẽ thực hiện các hoạt động đó?","answer_label":"Cấu trúc phân loại tổ chức","answer_id":52418},{"id":13543,"question":"Theo Hướng dẫn của PMBOK - Ấn bản lần thứ 5, lựa chọn nào sau đây là một định nghĩa thích hợp của một bên liên quan đến dự án?","answer_label":"Một cá nhân, nhóm hoặc tổ chức có thể ảnh hưởng, bị ảnh hưởng hoặc nhận thấy bản thân bị ảnh hưởng bởi quyết định, hoạt động hoặc kết quả của một dự án.","answer_id":52423},{"id":13544,"question":"Lựa chọn nào sau đây là giải thích thích hợp về phương pháp Điểm chức năng được sử dụng để dự toán phát triển hệ thống?","answer_label":"Nó là một phương pháp để ước lượng quy mô của một hệ thống mà các chức năng của hệ thống được đo bằng số bằng cách sử dụng các phần tử như số lượng các mục nhập xuất dữ liệu và số lượng các tệp tin, và một điều chỉnh được thực hiện trên cơ sở độ phức tạp và đặc điểm riêng của ứng dụng.","answer_id":52429},{"id":13545,"question":"Theo ITIL ấn bản 2011, điều nào sau đây là một giai đoạn thích hợp của vòng đời dịch vụ mà một nhà cung cấp dịch vụ xây dựng và triển khai các dịch vụ mới hoặc dịch vụ được sửa đổi?","answer_label":"Chuyển tiếp dịch vụ","answer_id":52433},{"id":13546,"question":"ISO/IEC 20000-1:2011 đòi hỏi phải áp dụng phương pháp được gọi là “Plan-Do-Check-Act” (PDCA) cho tất cả các phần của Hệ thống Quản lý Dịch vụ (SMS) và các dịch vụ. Lựa chọn nào sau đây là hoạt động bao gồm kế hoạch trong SMS?","answer_label":"Tạo ra khuôn khổ quyền, trách nhiệm và vai trò quy trình","answer_id":52435},{"id":13547,"question":"Theo ISO/IEC 20000-1:2011, đáp án nào sau đây là quy trình kiểm soát bao gồm xác định, kiểm soát, ghi chép, theo dõi, báo cáo và xác minh CI và quản lý thông tin CI trong CMDB?","answer_label":"Quản lý cấu hình","answer_id":52440},{"id":13548,"question":"Điều nào sau đây là mục đích thích hợp nhất mà một kiểm định viên hệ thống trao đổi ý kiến với một bộ phận kiểm toán liên quan đến phiên bản dự thảo báo cáo kiểm toán?","answer_label":"Để xác nhận rằng không có lỗi thực tế trong các phát hiện và kiến nghị được mô tả trong báo cáo kiểm toán.","answer_id":52442},{"id":13549,"question":"Điểm nào sau đây là điểm kiểm tra để kiểm toán sự kiểm soát của nguy cơ rò rỉ thông tin, giả mạo, và sử dụng trái phép tài liệu liên quan đến một hệ thống?","answer_label":"Thực hiện các biện pháp bảo đảm tính bí mật của tài liệu","answer_id":52448},{"id":13550,"question":"Điều nào sau đây là mô tả thích hợp liên quan đến việc thực hiện kiểm toán hệ thống?","answer_label":"Để người yêu cầu kiểm toán ban hành các hướng dẫn cải tiến trên cơ sở báo cáo kiểm toán, kiểm toán viên hệ thống báo cáo kết quả kiểm toán cho người yêu cầu kiểm toán.","answer_id":52451},{"id":13551,"question":"Lựa chọn nào sau đây là kỹ thuật được sử dụng để thực hiện phân bổ nguồn lực tối ưu cho đầu tư máy tính hóa trong từng loại được phân loại dựa trên những điểm tương đồng về rủi ro và giá trị đầu tư?","answer_label":"Danh mục CNTT","answer_id":52457},{"id":13552,"question":"Lựa chọn nào sau đây đại diện cho một phần của tổng chi phí sở hữu (TCO) cho Phần mềm như một dịch vụ (SaaS)?","answer_label":"Chi phí di chuyển dữ liệu","answer_id":52459},{"id":13553,"question":"Lựa chọn nào sau đây là một biện pháp để đánh giá rủi ro của việc giảm chất lượng bảo trì và vận hành hệ thống trong quá trình gia công phần mềm của một dịch vụ CNTT?","answer_label":"Các hoạt động cải tiến chất lượng dịch vụ được tiến hành bằng cách đồng ý với mức chất lượng mong muốn với nhà thầu phụ bằng cách sử dụng các chỉ số chứng minh chất lượng dịch vụ.","answer_id":52465},{"id":13554,"question":"Lựa chọn nào sau đây là đặc điểm của dịch vụ lưu trữ?","answer_label":"Quyền sử dụng của một máy chủ do một nhà cung cấp dịch vụ chuẩn bị được cung cấp cho người sử dụng.","answer_id":52468},{"id":13555,"question":"Lựa chọn nào sau đây là lời giải thích cho BYOD (Mang thiết bị của riêng bạn)?","answer_label":"Sử dụng các thiết bị thông tin riêng của nhân viên để làm việc","answer_id":52472},{"id":13556,"question":"Công việc nào sau đây được thực hiện khi các yêu cầu phi chức năng được xác định?","answer_label":"Tạo ra các yêu cầu kỹ thuật cho các tiêu chí và tiêu chuẩn phát triển theo ngôn ngữ lập trình được sử dụng trong phát triển hệ thống","answer_id":52476},{"id":13557,"question":"Lựa chọn nào sau đây giải thích về khoảng cách số?","answer_label":"Nó đề cập đến khoảng cách kinh tế hoặc xã hội xảy ra do sự khác biệt về khả năng và cơ hội khi sử dụng máy tính và mạng truyền thông.","answer_id":52478},{"id":13558,"question":"Lựa chọn nào sau đây là mục đích phân tích kế hoạch kinh doanh và lợi thế cạnh tranh thông qua quản lý danh mục đầu tư sử dụng ma trận thể hiện trong hình?\n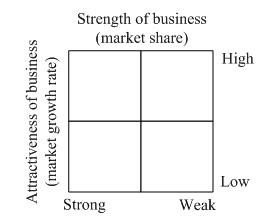","answer_label":"Để đánh giá vị trí kinh doanh của công ty làm cơ sở cho việc đặt ra một mục tiêu và ưu tiên phân bổ nguồn lực","answer_id":52485},{"id":13559,"question":"Lựa chọn nào sau đây giải thích về năng lực cốt lõi?","answer_label":"Khả năng vượt trội mà không thể bắt chước bởi các đối thủ cạnh tranh trong một lĩnh vực hoạt động của công ty","answer_id":52488},{"id":13560,"question":"Lựa chọn nào sau đây là chiến lược cơ bản của một ngách trong vị thế cạnh tranh?","answer_label":"Chiến lược chuyên môn nhằm vào sự chuyên môn hóa của sản phẩm và thị trường","answer_id":52493},{"id":13561,"question":"Hình dưới đây là thủ tục làm việc của MRP (Material Requirements Planning), một kỹ thuật của một hệ thống quản lý sản xuất. Những thông tin nào sau đây được chèn vào A trong hình bên dưới là cần thiết để tính các yêu cầu ròng?\n\n","answer_label":"Trạng thái tồn kho (lượng hàng tồn kho, đơn hàng còn lại, số lượng trong quá trình sản xuất)","answer_id":52495},{"id":13562,"question":"Lựa chọn nào sau đây mô tả một hệ thống RFID?","answer_label":"Đầu đọc/ghi RF tạo ra một trường điện từ cấp điện cho thẻ RF trong phạm vi cho phép truyền tải thông tin","answer_id":52499},{"id":13563,"question":"Lựa chọn nào sau đây là một tổ chức quản lý tạo ra một nhóm chức năng chéo giữa dự án và các tổ chức chức năng để linh hoạt đáp ứng với những thay đổi trong môi trường kinh doanh?","answer_label":"Tổ chức ma trận","answer_id":52504},{"id":13564,"question":"Lựa chọn nào sau đây là vai trò thích hợp của người hướng dẫn trong cuộc họp?","answer_label":"Khuyến khích những người tham gia cuộc họp đưa ra nhận xét và tổ chức luồng các cuộc thảo luận từ một vị trí trung lập và vô tư","answer_id":52507},{"id":13565,"question":"Lựa chọn nào sau đây là một lời giải thích cho sơ đồ tương đồng?","answer_label":"Đó là một phương pháp thu thập thông tin được thu thập trên cơ sở mối quan hệ lẫn nhau, và những vấn đề cần giải quyết được làm rõ.","answer_id":52512},{"id":13566,"question":"Lựa chọn nào sau đây là một ví dụ của CNTT Xanh?","answer_label":"Sử dụng hội thảo qua web thay vì di chuyển để gặp nhau","answer_id":52517},{"id":13567,"question":"Một nhà máy đã ghi lại số lần xuất hiện của sản phẩm bị lỗi theo nguyên nhân của khiếm khuyết. Dựa trên bản ghi này, biểu đồ nào sau đây là biểu đồ Pareto cho thấy các nguyên nhân hàng đầu của sự cố sản phẩm bị lỗi và tổng số phần trăm tích lũy?","answer_label":"","answer_id":52518},{"id":13568,"question":"Công ty A đặt mục tiêu kiếm được khoản lợi nhuận 36.000 đô la Mỹ theo các điều kiện được trình bày trong bảng dưới đây. Doanh thu bán hàng tối thiểu cho công ty để đạt được mục tiêu của nó là gì?\n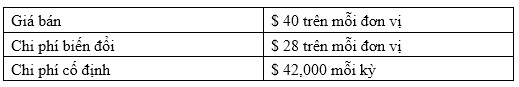","answer_label":"260.000","answer_id":52525},{"id":13569,"question":"Khi giá đơn vị hàng tồn kho được xác định bằng cách chia tổng số tiền mua cho tổng số lượng hàng đã mua, Lựa chọn nào sau đây là một phương pháp kiểm kê thích hợp được sử dụng?","answer_label":"Phương pháp định kỳ trung bình","answer_id":52527},{"id":13570,"question":"Lựa chọn nào sau đây là mô tả thích hợp về phạm vi bảo vệ phần mềm theo Hiệp định của WTO về Các khía cạnh liên quan đến Thương mại của Quyền sở hữu trí tuệ (TRIPS)?","answer_label":"Cả chương trình nguồn và các chương trình đối tượng được bảo vệ.","answer_id":52532},{"id":13848,"question":"Với một số nhị phân 8-bit, phương án nào sau đây sẽ biến đổi 4 bit ở giữa thành 1 và đảo ngược các bit còn lại?","answer_label":"Thực hiện phép NAND trên từng bit với 11000011","answer_id":53643},{"id":13849,"question":"Phương án nào dưới đây tương ứng logic với biểu thức sau? Ở đây A, B, C, và D là các số nguyên, ‘<’ là phép so sánh nhỏ hơn, và ‘≤’ là phép so sánh nhỏ hơn hoặc bằng.\n\nnot ((A ≤ B) or (C < D))","answer_label":"(B < A) and (D ≤ C)","answer_id":53648},{"id":13850,"question":"Có 16 tấm thẻ được đánh số từ 1 đến 16. Khi lựa chọn ra 4 tấm thẻ bất kỳ, phương án nào dưới đây là xác suất để cả 4 tấm thẻ là số lẻ?","answer_label":"1/26","answer_id":53650},{"id":13851,"question":"Khi hai tập hợp A và B có lực lượng 3 và 2, có bao nhiêu ánh xạ từ A sang B?","answer_label":"6","answer_id":53656},{"id":13852,"question":"Biểu thức dưới đây được ghi bằng ký hiệu tiền tố (ký pháp Ba Lan đảo ngược). Đâu là giá trị của biểu thức? Ở đây, các số được biểu diễn trong hệ thập phân, các ký hiệu ‘+’, ‘−’, ‘*’, và ‘/’ biểu diễn phép công, trừ, nhân và chia.\n\n 100 5 6 2 + * 12 4 / − − 36 −","answer_label":"27","answer_id":53660},{"id":13853,"question":"Trong cây nhị phân phía dưới, đâu là vị trí của nút mới có giá trị 17? Ở đây, mỗi vòng tròn biểu hiện một nút của cây và con số bên trong biểu thị giá trị của chúng.\n","answer_label":"Nút con bên trái của 18","answer_id":53663},{"id":13854,"question":"Phương án nào dưới đây là kết quả của lưu đồ thuật toán phía dưới?\n","answer_label":"10 8 6 4 2 0","answer_id":53668},{"id":13855,"question":"Với một mảng số nguyên hai chiều a, với a(i, j) có giá trị 2i + j, phương án nào là giá trị của a(a(1,1) × 2, a(2, 2) + 1)?","answer_label":"19","answer_id":53673},{"id":13856,"question":"Một hàm đệ quy f (n) được định nghĩa phía dưới cho mọi số tự nhiên n. Phương án nào là giá trị của f (5)?\n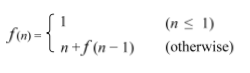","answer_label":"15","answer_id":53676},{"id":13857,"question":"Lựa chọn nào sau đây là phương thức đánh địa chỉ mà lệnh chứa địa chỉ đó và địa chỉ đó được thay đổi bởi giá trị từ thanh ghi khác?","answer_label":"Phương thức đánh địa chỉ chỉ số","answer_id":53679},{"id":13858,"question":"Phương án nào dưới đây là kiến trúc máy tính có bộ xử lý thực hiện nhiều luồng lệnh và nhiều luồng dữ liệu song song?","answer_label":"MIMD","answer_id":53682},{"id":13859,"question":"Phương án nào dưới đây là một giải thích thích hợp về việc chèn bộ nhớ?","answer_label":"Nó cho phép CPU truy cập các băng của bộ nhớ chính đồng thời","answer_id":53686},{"id":13860,"question":"Phương án nào sau đây thích hợp với vai trò của một bộ điều khiển thiết bị (device driver)?","answer_label":"Nó trực tiếp quản lý phần cứng theo các yêu cầu từ chương trình ứng dụng.","answer_id":53691},{"id":13861,"question":"Phương án nào dưới đây là từ thích hợp để mô tả hiện tượng khi các tệp được tạo ra trong quá trình lưu tệp nằm rải rác tại những phần khác nhau trên toàn bộ đĩa cứng chứ không liên tục trên các liên cung?","answer_label":"Phân mảnh","answer_id":53695},{"id":13862,"question":"Phương án nào sau đây là lời giải thích hợp lý về điện toán lưới?","answer_label":"Một tác vụ tính toán được phân chia cho một số máy tính trong mạng để đạt được năng lực tính toán cần thiết.","answer_id":53698},{"id":13863,"question":"Xem xét một hệ thống RAID 0 (tức là, phân chia cấp độ khối, không sử dụng chẵn lẻ hoặc phản chiếu) với hai đĩa; Khi dữ liệu được phân bố đều trên hai đĩa và cả hai đĩa đều có tỷ lệ lỗi là 0,1% thì tỷ lệ lỗi chung của hệ thống RAID là bao nhiêu? Ở đây, tỷ lệ thất bại tổng thể đề cập đến xác suất mà hệ thống không thể lấy được dữ liệu từ một trong hai đĩa.","answer_label":"0.1999","answer_id":53704},{"id":13864,"question":"Lựa chọn nào sau đây là mô tả thích hợp liên quan đến MTBF và MTTR?","answer_label":"MTBF của một hệ thống tăng lên thông qua bảo trì dự phòng.","answer_id":53708},{"id":13865,"question":"Round robin (với thời gian phân bổ 3 giây) được sử dụng làm phương pháp lập lịch cho ba tiến trình theo thứ tự P1, P2, và P3, thể hiện trong bảng dưới đây. Tổng thời gian chờ đợi (tính bằng giây) của P3 trước khi nó được thực hiện hoàn chỉnh là bao nhiêu? Ở đây, thời gian tới là thời gian mà tại đó một tiến trình nhập vào hàng đợi sẵn sàng.\n\n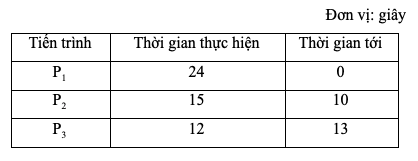","answer_label":"35","answer_id":53710},{"id":13866,"question":"Trong việc quản lý bộ nhớ ảo, phương pháp thay thế trang nào sau đây sẽ thay thế trang đã chiếm nhiều thời gian nhất kể từ lần sử dụng cuối cùng?","answer_label":"LRU","answer_id":53717},{"id":13867,"question":"Các phương pháp biểu diễn kết quả phân tích cú pháp trong trình biên dịch có định dạng bộ tứ.\n(Toán tử, Toán hạng 1, Toán hạng 2, Kết quả)\nĐịnh dạng này chỉ ra việc áp dụng Toán tử đối với Toán hạng 1 và Toán hạng 2 để cho ra Kết quả. Biểu thức nào sau đây là kết quả của chuỗi bộ tứ biểu diễn cho việc phân tích cú pháp? Ở đây, T1, T2, và T3 chỉ ra các biến tạm thời.\n\n\t\t\t(*,B,C,T1 )\n\t\t\t(/,T1 ,D,T2 )\n\t\t\t(+,A,T2 ,T3 )","answer_label":"A+B*C/D","answer_id":53718},{"id":13868,"question":"Công ty ABC áp dụng chính sách sao lưu ba thế hệ. Hệ thống của công ty ABC tự động thực hiện sao lưu toàn bộ vào ngày 10, 17 và 25 của mỗi tháng. Nếu bản sao lưu gần nhất được thực hiện vào ngày 17 tháng 9, đâu là ngày thông tin cũ nhất được sao lưu?","answer_label":"25 tháng 8","answer_id":53723},{"id":13869,"question":"Phương án nào dưới đây là một phương pháp thực hiện việc tích hợp các mô-đun cấu hình một chương trình trong thời gian thực thi chương trình?","answer_label":"Liên kết động","answer_id":53726},{"id":13870,"question":"Phương án nào dưới đây là đặc điểm của DRAM?","answer_label":"Cấu trúc các ô nhớ đơn giản, vì vậy có thể tích hợp cao để có được mức giá thấp cho mỗi bit","answer_id":53732},{"id":13871,"question":"Phương án nào sau đây là mạch logic tạo ra “1” là tín hiệu đầu ra Z, chỉ khi tín hiệu đầu vào X và Y có cùng giá trị?\n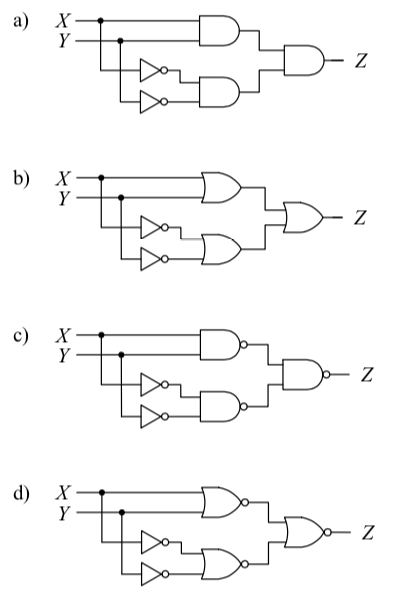","answer_label":"c","answer_id":53736},{"id":13872,"question":"Mạch nào trong các mạch logic sau đáp ứng các điều kiện được mô tả dưới đây?\n\n[Điều kiện]\nĐèn được bật và tắt bằng cách sử dụng các công tắc A và B ở đầu và cuối cầu thang. Đèn có thể được bật và tắt bằng cách sử dụng một công tắc, bất kể trạng thái của công tắc kia.\n\n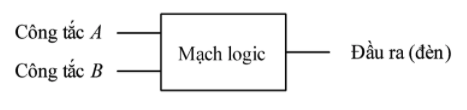","answer_label":"XOR","answer_id":53741},{"id":13873,"question":"Lựa chọn nào sau đây là một lời giải thích thích hợp về việc cắt ghép trong xử lý đồ họa 3D?","answer_label":"Đó là một phương pháp cho phép hoặc vô hiệu hóa một cách có chọn lọc các hoạt động dựng hình trong một vùng xác định.","answer_id":53742},{"id":13874,"question":"Cơ sở dữ liệu nào sau đây được thiết kế gồm nhiều bảng, với các dòng và các cột liên kết với nhau thông qua việc đối chiếu dữ liệu lưu trữ trong mỗi bảng?","answer_label":"Cơ sở dữ liệu quan hệ","answer_id":53749},{"id":13875,"question":"Lựa chọn nào sau đây là một lời giải thích hợp lý về giản đồ (schema) trong RDBMS?","answer_label":"Đó là một tập định nghĩa dữ liệu, chẳng hạn như bản chất của dữ liệu, định dạng của dữ liệu, và các mối quan hệ với dữ liệu khác.","answer_id":53752},{"id":13876,"question":"Lựa chọn nào sau đây là một dạng chuẩn hóa thích hợp (NF) được sử dụng trong cơ sở dữ liệu quan hệ trong đó mỗi thuộc tính không phải là khóa chỉ cần phụ thuộc vào khóa chính, và không có thuộc tính không phải là khóa nào phụ thuộc vào một thuộc tính không phải là khóa?","answer_label":"3NF","answer_id":53756},{"id":13877,"question":"Trong các giai đoạn thiết kế cơ sở dữ liệu, giai đoạn nào sau đây liên quan đến việc tạo ra một sơ đồ ER?","answer_label":"Giai đoạn thiết kế khái niệm cơ sở dữ liệu","answer_id":53758},{"id":13878,"question":"Câu lệnh SQL nào sau đây đối với bảng \"ShipmentRecord\" cho giá trị lớn nhất?\n","answer_label":"SELECT COUNT(*) FROM ShipmentRecord","answer_id":53763},{"id":13879,"question":"Lựa chọn nào sau đây là một địa chỉ IP định tuyến trên mạng Internet?","answer_label":"172.40.77.4","answer_id":53767},{"id":13880,"question":"Trong bảy tầng của mô hình tham chiếu cơ bản OSI, tầng nào chịu trách nhiệm chuyển tiếp các gói tin, bao gồm việc định tuyến chúng qua các router trung gian?","answer_label":"Tầng mạng","answer_id":53771},{"id":13881,"question":"Trong một mạng IPv4, lựa chọn nào sau đây là tổ hợp đúng của một lớp địa chỉ IP, dải địa chỉ IP của nó, và một subnet mask?\n\n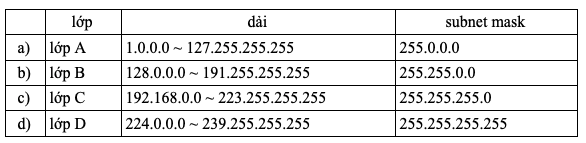","answer_label":"b","answer_id":53775},{"id":13882,"question":"Lựa chọn nào sau đây là dịch vụ Internet chuyển một tên miền như www.viblo.asia thành địa chỉ IP tương ứng của nó?","answer_label":"DNS","answer_id":53779},{"id":13883,"question":"Lựa chọn nào sau đây là một mô tả phù hợp về tiện ích netstat?","answer_label":"Nó hiển thị các kết nối TCP đang hoạt động.","answer_id":53782},{"id":13884,"question":"Alan muốn gửi một tin nhắn mã hóa cho Bob bằng cách sử dụng phương thức mã hóa không đồng bộ. Lựa chọn nào sau đây phải xảy ra trước khi Alan sẽ gửi tin nhắn mã hóa cho Bob? Ở đây, Alan đã chứng minh với Bob bằng chữ ký kỹ thuật số rằng Alan là người gửi tin nhắn cho Bob.","answer_label":"Bob cung cấp khóa công khai của mình cho Alan.","answer_id":53789},{"id":13885,"question":"Lựa chọn nào sau đây là một thuật ngữ thích hợp gắn với hành động gian lận mạo danh một người có thẩm quyền?","answer_label":"Giả mạo","answer_id":53792},{"id":13886,"question":"Một kẻ tấn công gọi tới bàn trợ giúp của công ty, giả mạo là một nhân viên đã bị mất mật khẩu của họ. Nhân viên trợ giúp thiết lập lại mật khẩu thành “password1” mặc định của công ty. Kẻ tấn công sau đó sử dụng mật khẩu này để truy cập vào mạng công ty và thông tin trong máy chủ. Kiểu tấn công này gọi là gì?","answer_label":"Kỹ nghệ xã hội","answer_id":53797},{"id":13887,"question":"Một cuộc tấn công trung gian xảy ra khi kẻ tấn công chặn đường liên lạc và giả mạo danh tính của một trong hai bên tham gia. Làm thế nào để có thể đề phòng hiệu quả với một cuộc tấn công như vậy?","answer_label":"Có thể đề phòng một cuộc tấn công như vậy bằng việc có sự chứng thực thông qua chữ ký số trước khi chấp nhận khóa công khai của ai đó.","answer_id":53799},{"id":13888,"question":"Bob và Alice mã hoá mọi cuộc liên lạc của họ với nhau. Do mức độ nhạy cảm cao của các thông tin chia sẻ, họ đã thực hiện một cơ chế mã hóa để bảo mật các thông điệp của mình. Tuy nhiên, vấn đề của việc mã hóa này là Bob hay Alice không thể chắc chắn 100% rằng họ đang giao tiếp với nhau, họ cũng không thể chắc chắn 100% về sự toàn vẹn của nội dung các thông điệp. Phương pháp mã hóa nào sau đây là phương pháp mà Bob và Alice sử dụng?","answer_label":"Mật mã sổ tay dùng một lần","answer_id":53804},{"id":13889,"question":"Một người dùng mới nhận được một tập tin có tên “image.jpg”. Khi kiểm tra chặt chẽ hơn, hóa ra tên tập tin thực sự là “image.jpg .exe”, với các khoảng trống ở giữa hậu tố giả là .jpg và hậu tố thực là .exe. Thuật ngữ nào sau đây được dùng thích hợp nhất để mô tả kiểu tấn công này","answer_label":"Trojan horse","answer_id":53807},{"id":13890,"question":"Một hệ thống sao lưu dữ liệu phải hỗ trợ khôi phục mọi giao dịch cho đến thời điểm 5 phút trước khi thảm họa xảy ra. Đây là kiểu mục tiêu gì?","answer_label":"Mục tiêu về thời điểm khôi phục","answer_id":53811},{"id":13891,"question":"Lựa chọn nào sau đây là một kiểm thử thích hợp để xác minh tính hiệu quả của các biện pháp an ninh bằng cách thử xâm nhập vào?","answer_label":"Kiểm thử thâm nhập","answer_id":53816},{"id":13892,"question":"Lựa chọn nào sau đây là một phương pháp thích hợp để ngăn chặn tấn công tràn bộ đệm?","answer_label":"Thực hiện việc kiểm tra ranh giới trên mọi biến chuỗi trong chương trình để khẳng định rằng chiều dài của chuỗi đầu vào không vượt quá kích thước của biến đích","answer_id":53821},{"id":13893,"question":"Các công ty thường cung cấp phương tiện cho lực lượng lao động di động của họ để truy cập vào mạng công ty một cách an toàn trên Internet thông qua các kênh không an toàn như mạng không dây mở tại khách sạn hoặc quán cà phê. Lựa chọn nào sau đây là công nghệ thích hợp có thể được sử dụng cho mục đích này?","answer_label":"VPN (Virtual Private Network)","answer_id":53825},{"id":13894,"question":"Lựa chọn nào sau đây là các thành phần của một sơ đồ trạng thái UML2.x (bao gồm 2.0 và các phiên bản sau)?","answer_label":"Trạng thái và Chuyển đổi","answer_id":53829},{"id":13895,"question":"Như thể hiện trong danh sách dưới đây, có ba loại kết nối. Lựa chọn nào sau đây là tổ hợp phù hợp nhất của các loại kết nối? \n\nKết nối A: Một mô-đun chuyển một yếu tố điều khiển tới mô-đun khác.\nKết nối B: Một mô-đun chuyển cấu trúc dữ liệu như một tham số cho mô-đun khác.\nKết nối C: Hai mô-đun có quyền truy cập vào cùng dữ liệu toàn cầu. \n\n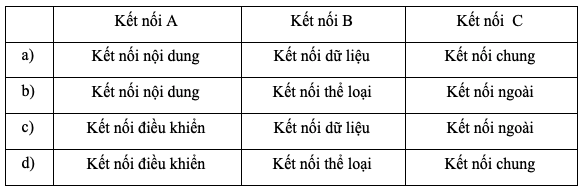","answer_label":"d","answer_id":53833},{"id":13896,"question":"Lựa chọn nào sau đây là một mô tả phù hợp liên quan đến dữ liệu kiểm thử cho kiểm thử hộp đen?","answer_label":"Dữ liệu kiểm thử được tạo ra theo đặc tả kỹ thuật bên ngoài.","answer_id":53836},{"id":13897,"question":"Khi kiểm thử một thành phần phần mềm, lựa chọn nào sau đây là một sự kết hợp phù hợp của X và Y?\n\n X: Nó gọi thành phần phần mềm sẽ được kiểm thử \n Y: Nó được gọi từ thành phần phần mềm sẽ được kiểm thử. \n","answer_label":"b","answer_id":53839},{"id":13898,"question":"Theo tiêu chuẩn Mô hình Năng lực Trưởng thành Tích hợp (CMMI), giai đoạn nào là giai đoạn cuối cùng và có mức trưởng thành cao nhất ?","answer_label":"Tối ưu hóa","answer_id":53844},{"id":13899,"question":"Theo PMBOK, tổ hợp quy trình nào sau đây liên quan đến quản lý tích hợp dự án?\n\nA. Kiểm soát chi phí\nB. Xây dựng bản tuyên bố về dự án \nC. Chỉ đạo và quản lý công việc dự án\nD. Xác định rủi ro\nE. Quản lý thông tin liên lạc\nF. Thực hiện kiểm soát thay đổi tích hợp","answer_label":"B, C, F","answer_id":53848},{"id":13900,"question":"Theo PMBOK, lựa chọn nào sau đây là một lời giải thích hợp lý liên quan đến việc làm phạm vi phình ra dự án trong quản lý phạm vi dự án?","answer_label":"Sự mở rộng không được kiểm soát về phạm vi sản phẩm hay dự án, mà không điều chỉnh thời gian, chi phí và nguồn lực.","answer_id":53853},{"id":13901,"question":"Như thể hiện trong sơ đồ mũi tên dưới đây, có một dự án bao gồm tám hoạt động từ A đến G. Lựa chọn nào sau đây là sự kết hợp thích hợp về thời gian kết thúc sớm nhất (EFT) và thời gian bắt đầu chậm nhất (LST) của hoạt động G?\n","answer_label":"c","answer_id":53856},{"id":13902,"question":"Theo EVM (Quản lý giá trị kiếm được), ngân sách của một dự án phát triển phần mềm là 10000$ và dự án được quy hoạch trong 10 tuần. Sau 4 tuần, phát hiện thấy rằng mới chỉ 30% công việc được hoàn tất với chi phí là 4200$. Chỉ số thực hiện về chi phí là bao nhiêu?","answer_label":"0.714","answer_id":53861},{"id":13903,"question":"Theo ISO/IEC 20000-1, lựa chọn nào sau đây là một quá trình cung cấp dịch vụ mà nhà cung cấp dịch vụ phải đồng ý về những dịch vụ cần cung cấp và phải đồng ý một danh mục dịch vụ với khách hàng?","answer_label":"Quản lý cấp độ dịch vụ","answer_id":53865},{"id":13904,"question":"Theo ITIL, điều nào sau đây là một hoạt động hay quá trình trong Chuyển đổi Dịch vụ?","answer_label":"Triển khai chiến lược như hội thảo web, bản tin, và trực quan hóa trong quá trình chuyển giao tri thức","answer_id":53869},{"id":13905,"question":"Lựa chọn nào sau đây là một mô tả phù hợp về mối quan hệ giữa bản ghi sự cố và bản ghi vấn đề trong quản lý dịch vụ CNTT?","answer_label":"Thông tin tham khảo chéo về sự cố nêu ở phần đầu của bản ghi vấn đề được bao gồm trong bản ghi vấn đề.","answer_id":53873},{"id":13906,"question":"Lựa chọn nào sau đây là một hoạt động thích hợp được thực hiện bởi một kiểm toán viên hệ thống người mà kiểm định việc kiểm soát truy nhập?","answer_label":"Xác nhận tình trạng quản lý kiểm soát truy cập liên quan đến dữ liệu.","answer_id":53874},{"id":13907,"question":"Lựa chọn nào sau đây là một điểm kiểm tra (checkpoint) trong quá trình kiểm định việc kiểm soát nhằm giảm nguy cơ của sự cố hệ thống khi áp dụng bản vá lỗi phần mềm?","answer_label":"Việc vận hành hệ thống được kiểm tra một cách thích đáng trước khi bắt đầu hoạt động trọn thời gian.","answer_id":53880},{"id":13908,"question":"Khi các biểu dữ liệu do bộ phận nghiệp vụ ban hành được nhập vào hệ thống trong bộ phận hệ thống thông tin, lựa chọn nào sau đây là một nhiệm vụ thích hợp được thực hiện bởi bộ phận hệ thống thông tin?","answer_label":"Để bộ phận nghiệp vụ có thể kiểm tra được kết quả xử lý từng biểu dữ liệu, danh sách kết quả xử lý được gửi đến bộ phận nghiệp vụ.","answer_id":53883},{"id":13909,"question":"Lựa chọn nào sau đây là sự đánh giá khả thi phù hợp khi kiểm tra liệu lợi ích suốt đời của hệ thống thông tin được đề xuất có lớn hơn chi phí suốt đời của nó?","answer_label":"Khả thi về kinh tế","answer_id":53886},{"id":13910,"question":"Lựa chọn nào sau đây là một kịch bản thông dụng để áp dụng UML, một kỹ thuật để trực quan hóa các quy trình nghiệp vụ?","answer_label":"Để thể hiện các quy trình theo nhiều quan điểm, một số phương pháp mô hình hóa theo mục đích cụ thể được sử dụng, và mỗi mô hình được mô tả bằng cách sử dụng quy tắc ký hiệu tiêu chuẩn cho việc mô hình hóa đối tượng.","answer_id":53892},{"id":13911,"question":"Trong “bốn loại’ cấu trúc doanh nghiệp, loại nào dưới đây hợp thành danh sách đầy đủ cùng với cấu trúc nghiệp vụ, cấu trúc công nghệ và cấu trúc ứng dụng?","answer_label":"Cấu trúc dữ liệu","answer_id":53895},{"id":13912,"question":"Lựa chọn nào sau đây là một lời giải thích thích hợp của EMS?","answer_label":"Nó đề cập đến việc sản xuất các thiết bị điện tử,... theo hợp đồng do các nhà sản xuất khác đặt hàng.","answer_id":53900},{"id":13913,"question":"Lựa chọn nào sau đây là giải thích về mua sắm xanh?","answer_label":"Nó không chỉ đề cập đến việc thực hiện các yêu cầu về chất lượng và giá cả, mà còn về việc mua ưu đãi các sản phẩm và dịch vụ ít gây tổn hại tới môi trường của các công ty làm việc hướng tới việc giảm gánh nặng về môi trường.","answer_id":53902},{"id":13914,"question":"Lựa chọn nào sau đây là mô tả thích hợp của RFI?","answer_label":"Đó là một tài liệu dùng để yêu cầu thông tin liên quan đến việc tin học hóa từ các nhà cung cấp tiềm năng, ví dụ như các nhà cung cấp hệ thống.","answer_id":53909},{"id":13915,"question":"Các công ty được phân loại dựa trên vị thế cạnh tranh của họ trên thị trường. Thường có bốn loại: dẫn đầu, thách thức, đi theo, và ngách. Lựa chọn nào sau đây là đặc tính thích hợp của chiến lược dẫn đầu?","answer_label":"Đề xuất sản phẩm mới và phương pháp sử dụng nó với người tiêu dùng để mở rộng nhu cầu tổng thể trong khi vẫn duy trì hoặc mở rộng thị phần","answer_id":53913},{"id":13916,"question":"Lựa chọn nào sau đây là một kỹ thuật marketing để tạo ra nhu cầu của người tiêu dùng bằng cách sử dụng quảng cáo nâng cao hình ảnh thương hiệu của công ty hoặc sản phẩm?","answer_label":"Chiến lược kéo","answer_id":53916},{"id":13917,"question":"Phân tích PEST được sử dụng để phân tích môi trường bên ngoài trong quá trình xác định chiến lược kinh doanh. Các yếu tố môi trường bên ngoài mà PEST phân tích là gì?","answer_label":"Chính trị, Kinh tế, Xã hội, Công nghệ","answer_id":53918},{"id":13918,"question":"Lựa chọn nào sau đây là giải thích về IoT (Internet vạn vật)?","answer_label":"Nó chỉ việc cài đặt tính năng giao tiếp tới các đối tượng khác nhau, ngoài các thông tin và thiết bị liên lạc, và cho phép tự động nhận dạng hoặc đo đạc từ xa bằng cách kết nối đối tượng này với Internet, để đạt được các dịch vụ ra quyết định cao cấp và tự động kiểm soát thông qua việc thu thập và phân tích khối lượng dữ liệu lớn.","answer_id":53925},{"id":13919,"question":"Lựa chọn nào sau đây là giải thích về kỹ thuật benchmarking được sử dụng để quản lý doanh nghiệp?","answer_label":"Nó đề cập tới sự hiểu biết về mặt định lượng và chất lượng các sản phẩm, dịch vụ và hoạt động của công ty qua so sánh những điều đó với những đối thủ cạnh tranh hoặc các công ty tiên tiến.","answer_id":53926},{"id":13920,"question":"Lựa chọn nào sau đây là giải thích về long tail?","answer_label":"Nó hiệu quả trong việc làm giảm nguy cơ mất cơ hội trong một cửa hàng trực tuyến trên Internet bằng cách sắp xếp một loạt mặt hàng, bao gồm cả những sản phẩm ít có cơ hội bán được.","answer_id":53933},{"id":13921,"question":"Lựa chọn nào sau đây sẽ thực hiện việc xử lý theo các bước từ (1) đến (3)?\n\n (1) Căn cứ vào kiểu loại và số lượng cũng như danh mục chi tiết những sản phẩm dự kiến sản xuất trong một giai đoạn cố định trong tương lai, tính ra số lượng thành phần yêu cầu.\n\n (2) Số lượng đặt hàng thuần của từng thành phần được tính từ số tồn kho có thể phân bổ.\n\n (3) Thời gian đặt hàng các thành phần được xác định khi xem xét thời gian sản xuất và thời gian mua sắm.","answer_label":"MRP (Hoạch định yêu cầu vật liệu","answer_id":53937},{"id":13922,"question":"Lựa chọn nào sau đây là quy trình mua sắm cho phép các nhà cung cấp chào giá cạnh tranh với nhau trên Internet để bán sản phẩm hay dịch vụ của họ theo những điều kiện do khách hàng xác định ?","answer_label":"Đấu giá ngược","answer_id":53940},{"id":13923,"question":"Lựa chọn nào sau đây là một tổ chức quản lý có cả đặc tính của dự án và của tổ chức dạng chức năng để linh hoạt ứng phó với những thay đổi trong môi trường kinh doanh?","answer_label":"Tổ chức kiểu ma trận","answer_id":53945},{"id":13924,"question":"Công ty A có hai kế hoạch truyền thông. Kế hoạch cho các quảng cáo 30 giây trên radio và kế hoạch cho các quảng cáo 60 giây trên truyền hình. Quảng cáo được đánh giá theo điểm. Công ty đang xem xét quảng cáo để đạt ít nhất 60 điểm trong thành phố và nhiều nhất 40 điểm bên ngoài thành phố. Bảng dưới đây cho thấy chi phí và quảng cáo cả truyền hình và radio. Lựa chọn nào sau đây là tập biểu thức có thể xác định số lượng quảng cáo trên phương tiện truyền thông để tổng chi phí là tối thiểu?\n\n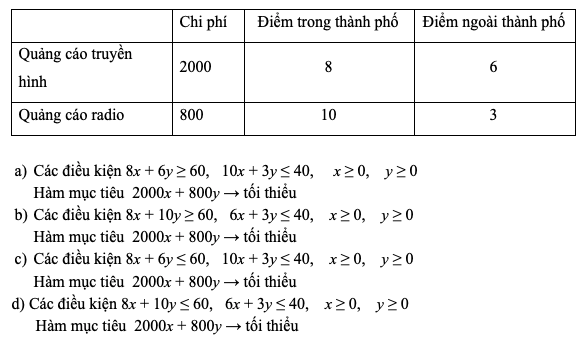","answer_label":"b","answer_id":53947},{"id":13925,"question":"Khi áp dụng phương pháp FIFO với bản ghi mua bán như hiển thị dưới đây, giá trị hàng tồn kho vào cuối tháng ba là bao nhiêu?\n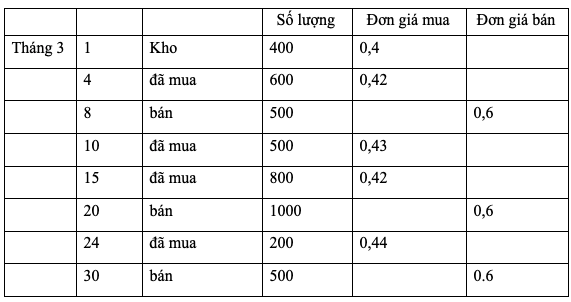","answer_label":"214","answer_id":53950},{"id":13926,"question":"Phương pháp nào sau đây là dùng để ra quyết định dựa trên tỷ lệ chiết khấu khi giá trị thu hồi vốn thuần hiện tại và số tiền đầu tư là bằng nhau?","answer_label":"Phương pháp Tỷ lệ hoàn vốn nội bộ","answer_id":53954},{"id":13927,"question":"Lựa chọn nào sau đây KHÔNG được bảo vệ bằng “bản quyền” theo Hiệp định của Tổ chức Thương mại Thế giới về các khía cạnh liên quan đến thương mại của Quyền Sở hữu trí tuệ (TRIPS)?","answer_label":"Ngôn ngữ lập trình và quy định của nó","answer_id":53960},{"id":13981,"question":"Số nào sau đây trong hệ bát phân tương ứng với số F1B0,C trong hệ thập lục phân?","answer_label":"170660,6","answer_id":54015},{"id":13982,"question":"Khi tung hai đồng xu cân đối và quay một con xúc sắc sáu mặt cân đối cũng một lúc, xác suất để có ít nhất một đồng xu cho ra mặt phía trên và con xúc sắc cho ra một số chẵn là bao nhiêu?","answer_label":"3/8","answer_id":54020},{"id":13983,"question":"Biểu thức nào sau đây dưới dạng ký pháp hậu tố tương đương với biểu thức 2 + 5 × 3 + 4 dưới dạng ký pháp trung tố? Ở đây, phép '×' có độ ưu tiên cao hơn phép ‘+’.","answer_label":"2 5 3 × + 4 +","answer_id":54026},{"id":13984,"question":"Dữ liệu âm thanh tương tự được lấy mẫu và chuyển đổi sang dữ liệu âm thanh kỹ thuật số 8-bit bằng cách sử dụng phương pháp PCM, sau đó truyền trong 64.000 bit mỗi giây. Khoảng cách mẫu tính theo micro giây là bao nhiêu?","answer_label":"125","answer_id":54029},{"id":13985,"question":"Lưu đồ thuật toán trong Hình 1 mô tả thủ tục để chuyển đổi ma trận A thành ma trận B. Khi lưu đồ này chuyển đổi ma trận A trong Hình 2 thành ma trận B trong Hình 3, điều nào sau đây cần được điền vào chỗ trống C ? Ở đây, A (i, j) và B (i, j) biểu diễn các phần tử thứ (i, j) của ma trận A và B . Trong Hình 1, các giới hạn vòng lặp “k : n, m” cho biết biến k thay đổi từ số nguyên n đến số nguyên m.\n","answer_label":"A (i, j) → B (j, 7-j)","answer_id":54034},{"id":13986,"question":"Khi thuật toán sắp xếp nổi bọt được sử dụng, cần bao nhiêu lần đổi chỗ để sắp xếp các số sau theo thứ tự tăng dần? \n\n9, 2, 13, 21, 3, 0","answer_label":"9","answer_id":54037},{"id":13987,"question":"Các giá trị từ 1 đến 10 được gán cho 10 nút trong cây nhị phân dưới đây để mỗi nút có một giá trị khác nhau. Trong phép gán này, giá trị của mỗi nút lớn hơn các giá trị của nút con bên trái và tất cả các nút hậu duệ của nó, và nhỏ hơn các giá trị của nút con phải và tất cả nút hậu duệ của nó. Điều nào sau đây là tổ hợp các giá trị được gán cho nút A và nút B ?\n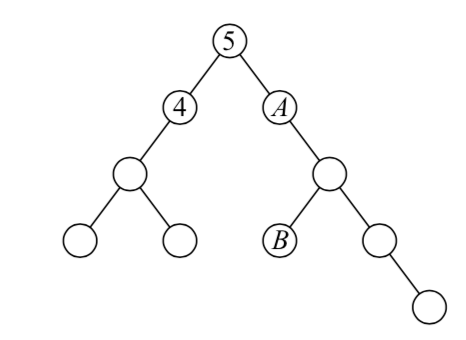","answer_label":"A = 6, B = 7","answer_id":54039},{"id":13988,"question":"Có hai hộp; hộp thứ nhất chứa hai quả bóng màu xanh lá cây và ba quả bóng màu đỏ; hộp thứ hai chứa ba quả bóng màu xanh lá cây và hai quả bóng màu đỏ. Một cậu bé chọn ngẫu nhiên một trong hai hộp, và sau đó chọn ngẫu nhiên một quả bóng từ hộp đó. Nếu quả bóng đó là màu đỏ, xác suất mà cậu bé đó chọn hộp đầu tiên là bao nhiêu?","answer_label":"3/20","answer_id":54043},{"id":13989,"question":"Phát biểu nào sau đây là một lời giải thích hợp lý về đa xử lý đối xứng (SMP)?","answer_label":"Một số lõi CPU có lịch trình cho các nhiệm vụ riêng của chúng, theo các mức độ ưu tiên truy nhập vào bộ nhớ và tài nguyên hệ thống như nhau do hệ điều hành quy định.","answer_id":54049},{"id":13990,"question":"Để xác định địa chỉ thực từ giá trị được ghi trong phần địa chỉ của lệnh, nhiều phương pháp đánh địa chỉ khác nhau được sử dụng. Phương pháp nào sau đây sử dụng giá trị của phần địa chỉ làm địa chỉ thực?","answer_label":"Đánh địa chỉ tuyệt đối","answer_id":54051},{"id":13991,"question":"Thiết bị nào sau đây là thiết bị bộ nhớ lưu các chương trình hoặc dữ liệu trong nhà máy, và chỉ có thao tác đọc những chương trình hoặc dữ liệu đã được lưu trữ?","answer_label":"Mask ROM","answer_id":54057},{"id":13992,"question":"Phát biểu nào sau đây là vai trò thích hợp của trình điều khiển thiết bị?","answer_label":"Nó trực tiếp điều khiển phần cứng theo yêu cầu từ chương trình ứng dụng.","answer_id":54060},{"id":13993,"question":"RAID nào sau đây có thể khôi phục dữ liệu từ ổ đĩa khác, với tối thiểu là cấu hình hai ổ đĩa?","answer_label":"RAID 1","answer_id":54064},{"id":13994,"question":"Một hệ thống gồm hai thiết bị xử lý. Sự khác nhau (hiệu số) về tính khả dụng giữa hệ thống có thể làm việc khi một trong hai thiết bị hoạt động bình thường, và hệ thống làm việc khi cả hai thiết bị hoạt động bình thường, là bao nhiêu? Ở đây, tính khả dụng của cả hai thiết bị là 0,9, và có thể bỏ qua những yếu tố khác ngoài các thiết bị xử ý.","answer_label":"0,18","answer_id":54069},{"id":13995,"question":"Điều nào sau đây là đặc tính thích hợp của một hệ thống web được triển khai trong cấu hình hệ thống máy khách/chủ ba lớp?","answer_label":"Quy trình nghiệp vụ được thực hiện ở phía máy chủ và phần mềm máy khách hiển thị kết quả trên màn hình theo mã HTML.","answer_id":54071},{"id":13996,"question":"","answer_label":"c","answer_id":54077},{"id":13997,"question":"Trong quản lý vào/ra, chức năng nào sau đây là chức năng thích hợp của bộ đệm","answer_label":"Giảm sự khác biệt về tốc độ xử lý bằng cách thiết lập một vùng nhớ đặc biệt giữa thiết bị vào/đầu ra và thiết bị xử lý","answer_id":54082},{"id":13998,"question":"Phương án nào sau đây là phương pháp sao lưu đòi hỏi thời gian sao lưu lâu nhất nhưng thời gian khôi phục ngắn nhất?","answer_label":"Full backu","answer_id":54084},{"id":13999,"question":"Trong UNIX, chức năng nào sau đây liên kết đầu ra chuẩn của một lệnh trực tiếp với đầu vào chuẩn của lệnh khác?","answer_label":"Ống","answer_id":54089},{"id":14000,"question":"Câu nào sau đây là giải thích phù hợp về việc tối ưu hóa trong trình biên dịch?","answer_label":"Phân tích mã nguồn và tạo ra mã đối tượng với hiệu suất xử lý thời gian chạy được nâng cao","answer_id":54091},{"id":14001,"question":"Tạo ra mã đối tượng hoạt động trong một máy tính có kiến trúc khác với máy tính mà trong đó trình biên dịch được thực hiện\n","answer_label":"d","answer_id":54098},{"id":14002,"question":"Phương án nào sau đây là tổ hợp cổng logic cho đầu ra là 1 khi cả hai đầu vào là 0?","answer_label":"NOR or XNOR","answer_id":54101},{"id":14003,"question":"Phương án nào sau đây sử dụng một mạch flip-flop trong ô nhớ?","answer_label":"SRAM","answer_id":54106},{"id":14004,"question":"Phương án nào sau đây được dùng để kiểm soát các kiểu giao diện của tài liệu HTML, như kích thước văn bản, màu sắc văn bản, hoặc bố trí trang?","answer_label":"CSS","answer_id":54108},{"id":14005,"question":"Trong hệ quản trị dữ liệu, chức năng nào sau đây quyết định giản đồ?","answer_label":"Chức năng định nghĩa","answer_id":54111},{"id":14006,"question":"Các thuộc tính của quan hệ “OrderRecord” có phụ thuộc hàm từ (1) đến (6) dưới đây. Việc chuẩn hóa được thực hiện với các phụ thuộc hàm này tới dạng chuẩn hóa bậc ba, và sự phân tách thành các mối quan hệ “Product”, “Customer”, “Order”, “OrderDetails” được thực hiện. Điều nào sau đây phù hợp với quan hệ “OrderDetails”? Ở đây, {X, Y} biểu diễn tổ hợp các thuộc tính X và Y, và X → Y thể hiện rằng X xác định Y theo kiểu hàm số. Thuộc tính được gạch chân thể hiện đó là khoá chính. \nOrderRecord\t(OrderNumber, OrderDate, CustomerNumber, CustomerName, ProductNumber, ProductName, Quantity, UnitSalesPrice)\n\n[Phụ thuộc hàm]\n(1)\tOrderNumber, → OrderDate\n(2) OrderNumber, → CustomerNumber\n(3)\tCustomerNumber → CustomerName\n(4) {OrderNumber, ProductNumber} → Quantity\n(5)\t{OrderNumber, ProductNumber} → UnitSalesPrice\n(6) ProductNumber → ProductName","answer_label":"OrderDetails (OrderNumber, ProductNumber, Quantity, UnitSalesPrice)","answer_id":54118},{"id":14007,"question":"Mô tả nào sau đây phù hợp với việc ánh xạ giữa mô hình quan hệ và cơ sở dữ liệu quan hệ khi triển khai?","answer_label":"Một quan hệ được ánh xạ thành một bảng.","answer_id":54120},{"id":14008,"question":"Khi vị trí lưu trữ được tính toán từ một giá trị khóa, phương pháp nào sau cho phép nhận được kết quả tính toán như nhau từ những giá trị khóa khác nhau?","answer_label":"Chỉ mục băm (Hash)","answer_id":54125},{"id":14009,"question":"Điều nào sau đây có thể thay đổi trạng thái bế tắc của giao dịch trở về trạng thái bình thường?","answer_label":"Rollback","answer_id":54129},{"id":14010,"question":"Tầng nào sau đây thuộc tầng 3 của mô hình tham chiếu cơ bản OSI, và thực hiện việc chọn đường và chuyển tiếp gói cho việc truyền thông từ đầu cuối tới đầu cuối?","answer_label":"Tầng mạng","answer_id":54132},{"id":14011,"question":"Khi máy tính cá nhân có kết nối với mạng LAN đang khởi động, giao thức nào sau đây được sử dụng để tự động gán một địa chỉ IP cho máy tính?","answer_label":"DHCP","answer_id":54135},{"id":14012,"question":"Điều nào sau đây mô tả một tính năng của IPv6 không có trong IPv4?","answer_label":"Phương pháp định địa chỉ 128-bit được đưa ra đối với không gian gian địa chỉ IP.","answer_id":54139},{"id":14013,"question":"Trong mạng TCP/IP, điều nào sau đây là tổ hợp thông tin xác định một kết nối TCP?","answer_label":"Địa chỉ IP, số của cổng","answer_id":54144},{"id":14014,"question":"Hình dưới đây cho thấy cơ chế cơ bản để đồng bộ đồng hồ bằng cách sử dụng NTP. Phản hồi từ máy chủ NTP có chứa Request Receive Time (Thời gian nhận yêu cầu) và Response Transmit Time (Thời gian truyền phản hồi). Máy tính sẽ tính toán sự khác biệt giữa đồng hồ trong máy tính và đồng hồ máy chủ NTP bốn thời gian như thể hiện trong hình. Đồng hồ trong máy tính khác với đồng hồ máy chủ NTP bao nhiêu? Ở đây, yêu cầu và phản hồi đòi hỏi thời gian truyền như nhau, và mỗi lần trong hình cho thấy thời gian trên đồng hồ trong máy tính hoặc máy chủ NTP. Trong biểu thức aa:bb:cc. dddddd, aa, bb, cc, và dddddd thể hiện giờ, phút, giây, một phần nhỏ của giây (micro giây), tương ứng. \n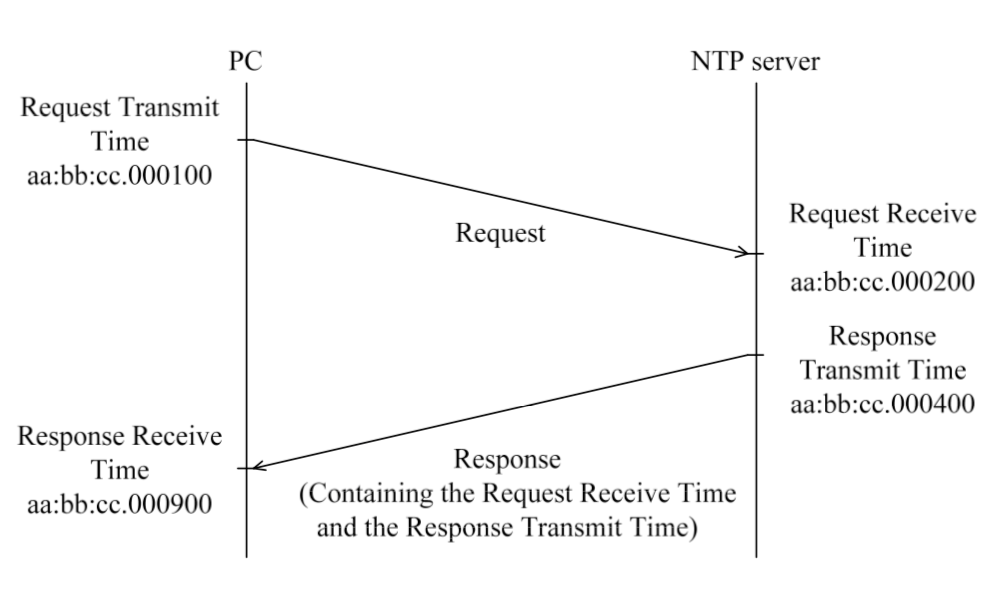","answer_label":"Nhanh 200 micro giây","answer_id":54148},{"id":14015,"question":"Loại nào sau đây là một dạng phần mềm độc hại yêu cầu máy chủ để truyền bá từ máy tính này sang máy tính khác?","answer_label":"Viruses","answer_id":54152},{"id":14016,"question":"Thuật ngữ nào sau đây được sử dụng để mô tả cuộc tấn công trong đó kẻ tấn công khai thác lỗ hổng của hệ thống máy tính trước khi có bản vá khắc phục lỗ hổng?","answer_label":"Tấn công Zero-day","answer_id":54158},{"id":14017,"question":"Điều nào sau đây là mô tả thích hợp về tấn công làm tràn bộ đệm?","answer_label":"Cuộc tấn công làm tràn vùng nhớ được đảm bảo bằng một chương trình liên tục gửi đi những chuỗi ký tự dài hoặc dữ liệu để chiếm quyền truy cập từ chương trình và gây ra sự cố","answer_id":54159},{"id":14018,"question":"Một ví dụ điển hình về các mối đe dọa an ninh cá nhân là rò rỉ thông tin. Phương án nào sau đây là biện pháp thích hợp nhất để ngăn chặn rò rỉ thông tin?","answer_label":"Dữ liệu chứa thông tin quan trọng được mã hóa bằng khóa công khai nhận được trước từ người nhận trước khi gửi nó tới người nhận qua email. Người nhận sẽ giải mã dữ liệu bằng khóa cá nhân mà người nhận đã tạo ra dưới dạng cặp khóa công khai/ cá nhân.","answer_id":54164},{"id":14019,"question":"Khi thực hiện tiến trình được thể hiện trong thủ tục dưới đây, ngoài việc phát hiện việc giả mạo thông điệp, điều nào sau đây là điều mà người nhận B có thể làm được? \n \n[Thủ tục] \nTiến trình của người gửi A\n(1)\tMột hàm băm được sử dụng để tạo ra một tóm tắt từ thông điệp. \n(2)\tTóm tắt được tạo ra trong bước (1) được mã hóa bằng khóa riêng với người gửi A để tạo ra chữ ký kỹ thuật số. \n(3) Thông điệp và chữ ký kỹ thuật số tạo ra trong bước (2) được gửi đến người nhận B. \n \nTiến trình của người nhận B \n(4)\tDùng chính hàm băm đã sử dụng trong tiến trình của gửi A để tạo ra một tóm tắt từ thông điệp nhận được. \n(5)\tChữ ký đã nhận được xác minh bằng cách so sánh tóm tắt được tạo ra trong bước (4) và tóm tắt được tạo ra nhờ việc giải mã chữ ký số đã nhận bằng khóa công khai của người gửi A mà người nhận B đã nhận trước từ người gửi A.","answer_label":"Xác nhận rằng thông điệp là từ người gửi A","answer_id":54167},{"id":14020,"question":"Trong số các kỹ thuật phá mã được đưa ra dưới đây, kỹ thuật nào sau đây được phân loại là tấn công brute force (tức kỹ thuật lấy mật khẩu bằng cách thử đúng sai)?","answer_label":"Đối với tập văn bản thuần túy và văn bản mã hóa đã cho, khóa được xác định bằng cách sử dụng tất cả các kết hợp có thể.","answer_id":54172},{"id":14021,"question":"Đâu là thuật ngữ phù hợp để mô tả hành vi tách biệt các tài liệu lấy từ những nguồn khác nhau?","answer_label":"Chính sách chung nguồn gốc","answer_id":54178},{"id":14022,"question":"Khi sử dụng cổng gương để cho phép phần mềm phân tích mạng LAN điều tra nguyên nhân gây sự cố mạng, đâu là điểm cần phải cân nhắc?","answer_label":"Vì phần mềm phân tích mạng LAN có thể hiển thị các gói tin đi qua mạng nên cần chú ý đến việc bị lợi dụng như là kẻ gian nghe lén.","answer_id":54181},{"id":14023,"question":"Đâu là thuật ngữ thích hợp dùng để mô tả một nhóm có tổ chức, có tay nghề cao, có nhiệm vụ liên tục theo dõi, cải tiến bảo mật của tổ chức, ngăn chặn, phát hiện, phân tích và khắc phục các sự cố an ninh với sự trợ giúp của công nghệ và các quy trình thủ tục đã được định nghĩa sẵn?","answer_label":"Trung tâm điều hành an ninh (SOC)","answer_id":54186},{"id":14024,"question":"Khi tường lửa lọc các gói tin dựa vào danh sách các luật, đâu là luật được áp dụng cho gói tin A và tác dụng của nó là gì? Biết rằng, tường lửa chỉ áp dụng các quy tắc từ 1 đến 4 đã được liệt kê ở bảng bên dưới và khi một quy tắc được áp dụng, các quy tắc khác sẽ không được áp dụng.\n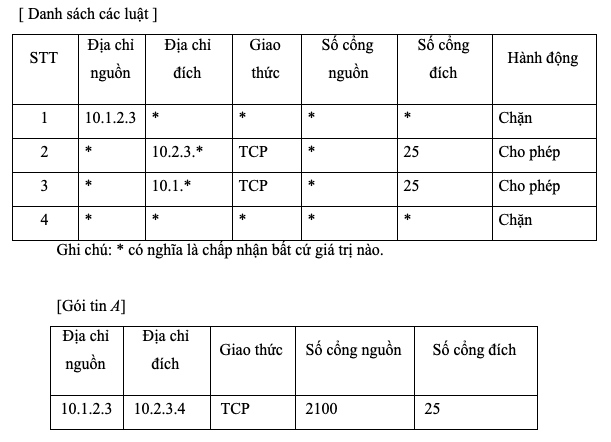","answer_label":"Sử dụng quy tắc 1 và bị chặn","answer_id":54187},{"id":14025,"question":"Đâu là mô tả phù hợp nhất cho khái niệm đa hình trong ngôn ngữ lập trình hướng đối tượng","answer_label":"Đa hình cung cấp giao diện đơn cho các thực thể thuộc nhiều loại khác nhau.","answer_id":54194},{"id":14026,"question":"Trong quy trình phát triển phần mềm, hoạt động nào dưới đây nên được thực hiện khi thiết kế kiến trúc phần mềm?","answer_label":"Chuyển đổi yêu cầu phần mềm thành kiến trúc để mô tả cấu trúc cấp cao và định nghĩa các thành phần của phần mềm.","answer_id":54198},{"id":14027,"question":"Mệnh đề nào dưới đây mô tả đúng nhất về việc lần dấu vết ngăn xếp (stack-trace) trong quá trình tìm lỗi chương trình?","answer_label":"Một dấu vết của việc gọi phương pháp/hàm/chương trình con của ngăn xếp.","answer_id":54199},{"id":14028,"question":"Câu nào dưới dây mô tả đúng nhất về kiểm thử chuyển tiếp trạng thái trong quá trình kiểm thử tích hợp hệ thống?","answer_label":"Là phương pháp kiểm tra liệu hệ thống có hoạt động đúng theo sự kết hợp của sự kiện và trạng thái bên trong mà đã được thiết kế.","answer_id":54204},{"id":14029,"question":"Lựa chọn nào sau đây là phương pháp dùng để phân tích mã nguồn và đối tượng, và trích xuất đặc tả chương trình và thông tin thiết kế?","answer_label":"Kỹ thuật dịch ngược","answer_id":54210},{"id":14030,"question":"Dựa theo ISO/IEC 12207 (Hệ thống và kỹ thuật phần mềm - quy trình vòng đời phần mềm (SLCP)), Quy trình Phát triển Phần mềm có các quy trình cấp thấp hơn như sau:\n1) Quy trình xây dựng\n2) Quy trình phân tích yêu cầu\n3) Quy trình thiết kế kiến trúc và thiết kế chi tiết\n4) Quy trình tích hợp và kiểm tra\n\nĐâu là thứ tự đúng của Quy trình Phát triển Phần mềm?","answer_label":"2) → 3) → 1) → 4)","answer_id":54212},{"id":14031,"question":"Theo PMBOK, trong các quy trình sau, quy trình nào thuộc Nhóm Quy trình Thực hiện (Executing Process Group)?","answer_label":"Quy trình kiểm soát yêu cầu chất lượng và kết quả từ các phép đo kiểm tra chất lượng để đảm bảo chất lượng, tiêu chuẩn và các định nghĩa hoạt động được thực hiện đúng.","answer_id":54215},{"id":14032,"question":"Đâu là mô tả phù hợp của mô tả quan hệ “Lead” trong quản lý thời gian dự án?","answer_label":"Đó là khoảng thời gian mà theo đó hoạt động của người kế tiếp có thể được nâng cao nhờ có người tiền nhiệm.","answer_id":54219},{"id":14033,"question":"Sơ đồ mũi tên dưới đây mô tả các hoạt động và các cột mốc của dự án. Dự án này có thể hoàn thành sau tối thiểu bao nhiêu thời gian? \n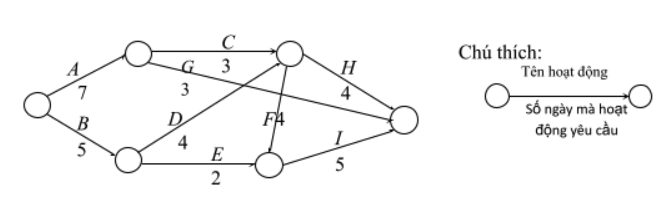","answer_label":"19","answer_id":54226},{"id":14034,"question":"Công ty A dự kiến sẽ ra mắt một sản phẩm phần mềm và đội ngũ bán hàng sẽ cần thuyết phục khách hàng mua sản phẩm đó. Nguy cơ là đội ngũ bán hàng không hiểu về sản phẩm nên không thể đưa ra những lý do thuyết phục tốt. Do đó, doanh số bán hàng sẽ giảm, doanh thu của công ty cũng sẽ bị giảm. Vì vậy, ban giám đốc quyết định đào tạo cho đội bán hàng. Lựa chọn nào sau đây là phương pháp tốt nhất cho quản lý rủi ro?","answer_label":"Giảm nhẹ rủi ro","answer_id":54229},{"id":14035,"question":"Tính điểm chức năng của chương trình có các chức năng và đặc điểm được mô tả như trong bảng dưới dây. Ở đây, hệ số hiệu chỉnh của độ phức tạp là 0,75.\n","answer_label":"18","answer_id":54231},{"id":14036,"question":"Đâu là mệnh đề phù hợp để mô tả mục đích của việc sử dụng Cấu trúc chia nhỏ công việc (WBS) trong dự án phát triển phần mềm?","answer_label":"Để phân chia một công việc phát triển thành những công việc nhỏ hơn, có kích thước dễ quản lý và sắp xếp chúng theo một thứ tự phân cấp.","answer_id":54236},{"id":14037,"question":"Lựa chọn nào sau đây là thiết bị được dùng để bảo vệ mạch cung cấp điện, thiết bị truyền thông hoặc các thiết bị khác khỏi điện áp quá tải hoặc dòng điện quá tải phát sinh từ điện áp quá tải?","answer_label":"SPD","answer_id":54241},{"id":14038,"question":"Lựa chọn nào sau đây là biện pháp phòng ngừa thích hợp để giám sát khả năng suất và hiệu suất sử dụng của một hệ thống trực tuyến trong quá trình quản lý năng suất của quản lý dịch vụ công nghệ thông tin?","answer_label":"Các chỉ số đo lường như thời gian phản hồi và sử dụng CPU được theo dõi thường xuyên.","answer_id":54244},{"id":14039,"question":"Theo ITIL, đâu là mô tả đúng về Service Desk ảo trong các đặc điểm của một tổ chức Service Desk?","answer_label":"Như người dùng có thể quan sát, bằng cách sử dụng công nghệ truyền thông, các dịch vụ có thể được cung cấp bởi Service Desk. Thậm chí, nhân viên của Service Desk còn có thể ở nhiều vùng khác nhau.","answer_id":54247},{"id":14040,"question":"Tại cuộc kiểm tra về bảo mật thông tin, lựa chọn nào sau đây là việc kiểm tra để xác nhận tính khả dụng?","answer_label":"Khoảng thời gian gián đoạn sẽ được quản lý sao cho đảm bảo được tiêu chuẩn SLA về thời gian gián đoạn.","answer_id":54252},{"id":14041,"question":"Lựa chọn nào sau đây được đánh giá là phù hợp khi tiến hành kiểm toán Kế hoạch Kinh doanh Liên tục (BCP)?","answer_label":"Danh sách liên lạc khẩn cấp của nhân viên sẽ được tạo và luôn được cập nhật phiên bản mới nhất.","answer_id":54256},{"id":14042,"question":"Lựa chọn nào sau đây là giải thích thích hợp về Kiến trúc Doanh nghiệp (EA)?","answer_label":"Nó là một kỹ thuật để phân tích từng hoạt động kinh doanh và hệ thống thông tin thông qua bốn (4) hệ thống kinh doanh, dữ liệu, ứng dụng, công nghệ và xem xét nó từ quan điểm của việc tối ưu hoá tổng thể","answer_id":54260},{"id":14043,"question":"Lựa chọn nào sau đây là giải thích phù hợp của tổ chức dự án?","answer_label":"Nó chỉ được hình thành trong khoảng thời gian nhất định để giải quyết một vấn đề nhất định và nó sẽ được giải thể khi vấn đề được giải quyết.","answer_id":54265},{"id":14044,"question":"Lựa chọn nào sau đây là mục đích của Quản lý Quy trình Kinh doanh (BPM) cho các hoạt động của công ty?","answer_label":"Liên tục cải tiến quy trình kinh doanh","answer_id":54269},{"id":14045,"question":"Việc mua hai thiết bị Công nghệ thông tin A và B đang được xem xét. Khoảng thời gian thanh toán được tính đến hết vòng đời của thiết bị. Lựa chọn nào sau đây là mô tả thích hợp về lợi nhuận tối thiểu hàng năm cần để thu hồi được số tiền đầu tư cho A và B. Ở đây lợi nhuận hàng năm sẽ được tính đều đặn và không tính lãi suất.\n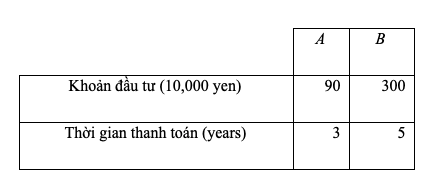","answer_label":"B cần có mức lợi nhuận hàng năm gấp đôi A.","answer_id":54274},{"id":14046,"question":"Phương pháp đánh giá tổng thể trọng số tích hợp với định lượng chấm điểm các hạng mục được sử dụng để đánh giá hiệu quả cải thiện bằng định lượng. Lựa chọn nào sau đây là đề xuất cải tiến nên được ưu tiên trong bảng dưới đây?\n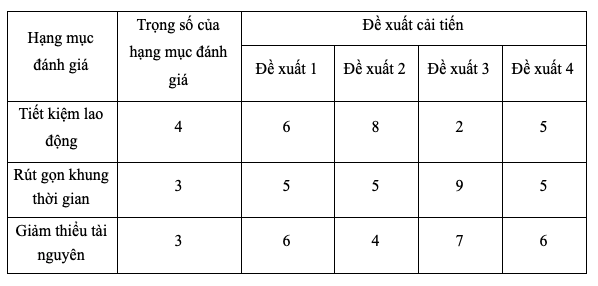","answer_label":"Đề xuất 2","answer_id":54276},{"id":14047,"question":"Miêu tả nào sau đây tương ứng với việc mua sắm CSR?","answer_label":"Chỉ ra các tiêu chuẩn mua sắm cần phải cân nhắc như môi trường, nhân quyền... và yêu cầu các nhà cung cấp phải thực hiện theo các tiêu chuẩn này.","answer_id":54281},{"id":14048,"question":"RFP được trình bày cho từng nhà cung cấp trả lời RFI. Điều nào sau đây cần được thực hiện trước để tiến trình lựa chọn nhà cung cấp trong tương lai được diễn ra công bằng?","answer_label":"Thiết lập quy trình lựa chọn như thiết lập các tiêu chuẩn hoặc các quy tắc trọng số phù hợp với các mục yêu cầu.","answer_id":54284},{"id":14049,"question":"Kỹ năng marketing nào dưới đây được sử dụng để tạo động cơ khuyến khích nhà phân phối áp dụng các điều kiện như trả hàng và giảm giá, tăng nhu cầu của người tiêu dùng?","answer_label":"Chiến lược đẩy","answer_id":54289},{"id":14050,"question":"Hình dưới minh họa mối quan hệ giữa bốn (4) P đề xuất từ quan điểm của người bán và bốn (4) C đề xuất từ quan điểm của người mua trong marketing hỗn hợp. Lựa chọn nào sau đây tương ứng với vị trí A trong hình bên dưới? Ở đây mỗi lựa chọn từ a) đến d) chỉ có thể điền vào một chỗ trống từ A đến D, không có ngoại lệ.\n","answer_label":"d","answer_id":54294},{"id":14051,"question":"Giá bán của một sản phẩm được quyết định dựa vào các phương pháp đặt giá bán hàng khác nhau. Cách tiếp cận nào dưới đây sẽ đặt ra được mức giá bán cao bằng cách sử dụng tâm lý người dùng là hàng có giá cao sẽ có chất lượng tốt?","answer_label":"Giá cả uy tín","answer_id":54298},{"id":14052,"question":"Lựa chọn nào sau đây là giải thích phù hợp cho công nghệ đường cong S?","answer_label":"Nó đại diện cho quá trình tiến bộ công nghệ. Nó cho thấy rằng tiến bộ công nghệ chậm ở giai đoạn đầu và sau đó tiến bộ nhanh chóng rồi tiến bộ chậm dần lại.","answer_id":54301},{"id":14053,"question":"Lựa chọn nào sau đây là ví dụ của Consumer Generated Media (CGM)?","answer_label":"Một trang web như một blog và SNS...thông qua đó một cá nhân tự truyền tải thông tin đến công chúng về đánh giá các sản phẩm mà người đó đã sử dụng.","answer_id":54306},{"id":14054,"question":"Lựa chọn nào sau đây chỉ ra phương pháp định giá dựa trên cách tiếp cận chi phí?","answer_label":"Quyết định giá bằng cách cộng lợi nhận mong muốn với chi phí sản xuất và chi phí kinh doanh.","answer_id":54308},{"id":14055,"question":"Hình dưới đây cho thấy mối quan hệ giữa các thành phần của sản phẩm A và số trong dấu ngoặc là số lượng các thành phần cần thiết để tạo thành một sản phẩm hoặc thành phần ở mức trên. Khi 10 sản phẩm A được sản xuất, cần đặt bao nhiêu thành phần C? Ở đây, hiện có năm đơn vị của thành phần C đang tồn kho và bắt buộc phải sử dụng cho sản xuất trước khi đặt hàng mới.\n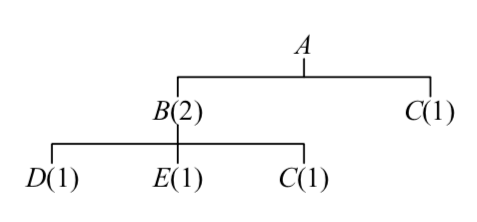","answer_label":"25","answer_id":54313},{"id":14056,"question":"Để đảm bảo tính minh bạch trong quản trị kinh doanh, đâu là khái niệm giám sát và quản lý hoạt động công ty từ góc độ các câu hỏi như công ty kinh doanh cho ai, cơ cấu ban lãnh lạo cấp cao như thế nào và liệu tổ chức có khả năng tự cải thiện không?","answer_label":"Quản trị doanh nghiệp","answer_id":54316},{"id":14057,"question":"Mục nào sau đây nên được đặt trong “Liabilities and Stockholder’s Equity” trong bảng cân đối kế toán?","answer_label":"Cổ phiếu phổ thông","answer_id":54320},{"id":14058,"question":"Kiểu báo cáo tài chính nào sau đây thể hiện tình hình tài chính của một doanh nghiệp tại một thời điểm cụ thể?","answer_label":"Bảng cân đối tài chính","answer_id":54323},{"id":14059,"question":"Lựa chọn nào sau đây là vai trò của CIO?","answer_label":"Xây dựng chiến lược tin học hoá từ góc độ doanh nghiệp và xác nhận, đánh giá sự phù hợp của nó với chiến lược kinh doanh","answer_id":54328},{"id":14060,"question":"Trục ngang và trục dọc của đường cong Đặc tính Hoạt động (OC) trong quản lý chất lượng lần lượt thể hiện phần trăm bị lỗi trên lô và tỉ lệ thành công trên lô. Mẫu có kích thước n được chiết xuất từ rất nhiều kích thước N và khi số lượng mẫu bị lỗi nhỏ hơn hoặc bằng mức đạt yêu cầu C, cả lô đó sẽ đạt yêu cầu, còn khi vượt quá C thì cả lô đó sẽ bị loại.\nBiểu đồ nào sau đây mô tả xu hướng thay đổi của đường cong OC khi N và n cố định, C lấy các giá trị 0, 1 và 2?\n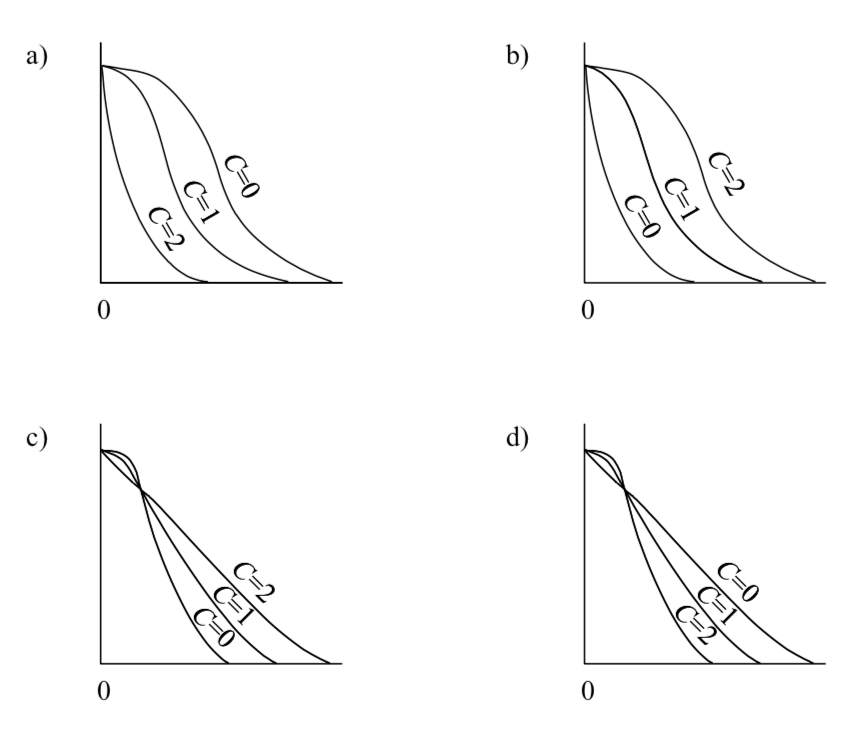","answer_label":"b","answer_id":54332},{"id":14069,"question":"Lựa chọn nào dưới đây là sự kết hợp phù hợp mà biểu diễn số thập phân “-19” trong bù nhị phân của nhị phân bù một 8-bit và nhị phân bù hai 8-bit?\n","answer_label":"d","answer_id":54353},{"id":14070,"question":"Lựa chọn nào dưới đây là phân số nhị phân thích hợp mà tương đương với giá trị thập phân 5,525? Ở đây, xâu nhị phân trong dấu ngoặc đơn được lặp lại vô hạn.","answer_label":"101,100(0011)","answer_id":54357},{"id":14071,"question":"Khi ba quả táo được lấy ra ngẫu nhiên từ một hộp mà chứa bốn quả táo màu xanh và tám quả táo màu đỏ, đâu là xác suất mà hai quả táo đầu tiên là màu xanh và quả thứ ba (hoặc cuối cùng) là màu đỏ? Ở đây, mỗi quả táo được lấy ra sẽ không bỏ lại vào hộp.","answer_label":"4/55","answer_id":54360},{"id":14072,"question":"Đối với một cây tìm kiếm nhị phân cân bằng, lựa chọn nào dưới đây là độ phức tạp thời gian tiệm cận của thao tác tìm kiếm đối với một tập “n2n” phần tử dữ liệu? Ở đây, “O( )” cho biết thứ tự về thời gian chạy của thuật toán, và “n” là đủ lớn.","answer_label":"O(n)","answer_id":54362},{"id":14073,"question":"Khi tình trạng và các kết luận được cho như bên dưới, lựa chọn nào là sự kết hợp phù hợp mà cho biết tính hợp lệ của hai kết luận? \nTình trạng: Nếu trời mưa, thì đường phố sẽ ướt.\nKết luận 1: Đường phố không ướt, và do đó trời đã không mưa. \nKết luận 2: Trời đã không mưa, và do đó, đường phố không ướt.\n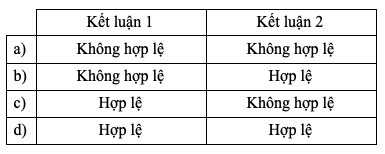","answer_label":"c","answer_id":54368},{"id":14074,"question":"Như thể hiện dưới đây, có một cây tìm kiếm nhị phân ở đó mỗi nút chứa một tên nước và được sắp thứ tự theo chữ cái theo đó Mongolia đi trước Philippines, Myanmar đi trước Philippines nhưng sau Mongolia, và cứ như vậy. Lựa chọn nào sau đây là thứ tự thích hợp của các tên nước mà có thể tạo ra cây tìm kiếm nhị phân này bằng việc chèn mỗi tên nước vào một cây trống? \n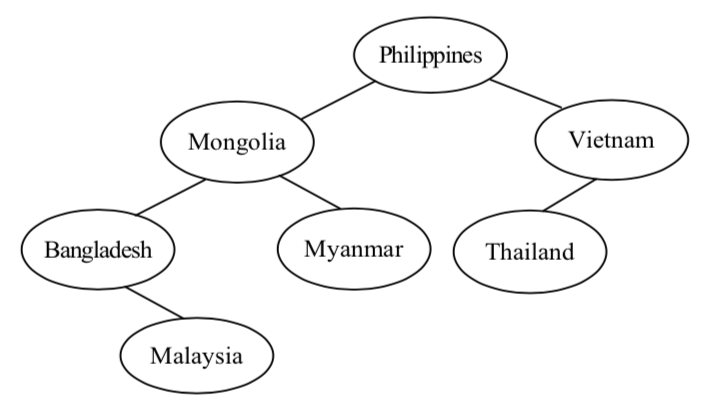","answer_label":"Philippines, Vietnam, Mongolia, Thailand, Bangladesh, Myanmar, Malaysia","answer_id":54373},{"id":14075,"question":"Trong một hệ thống thời gian thực, lựa chọn nào sau đây là cấu trúc dữ liệu thích hợp nhất đối với việc lập lịch nhiều nhiệm vụ với các mức độ ưu tiên khác nhau?","answer_label":"Danh sách liên kết","answer_id":54376},{"id":14076,"question":"Khi hàm số M(n) được định nghĩa như dưới đây, đâu là giá trị của M(97)?\n","answer_label":"91","answer_id":54380},{"id":14077,"question":"Như được cho trong bảng bên dưới, có năm đồ vật từ A đến F. Mỗi đồ vật không thể được chia thành các phần nhỏ hơn. Khi một túi đựng với khối lượng tối đa 7 đơn vị sẵn sàng để chứa các đồ vật, lựa chọn nào dưới đây là một tập hợp các đồ vật sẽ được đóng gói trong túi đựng mà tổng mức giá có thể được tối đa hóa?\n","answer_label":"B, E","answer_id":54384},{"id":14078,"question":"Như được cho trong bảng bên dưới, có tổng cộng 86 đồng tiền được tạo ra bởi năm loại tiền. Trong số 86 đồng tiền, 60 đồng được lấy ra sao cho có thể có được giá trị tối đa. Đâu là tổng giá trị tính theo đô-la? Ở đây, 100 xu tương đương với một đô-la\n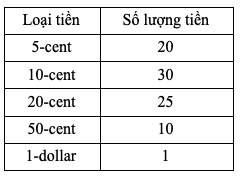","answer_label":"13.4","answer_id":54389},{"id":14079,"question":"Như đã cho trong hình và bảng bên dưới, có hai kiểu CPU X và Y mà có cùng cấu hình ngoại trừ việc thời gian truy cập bộ nhớ cache và bộ nhớ chính là khác nhau. Mọi điều kiện khác của hai CPU này là như nhau.\nKhi một chương trình được thực thi bởi cả hai CPU X và Y, thời gian xử lý của mỗi CPU là như nhau. Dưới những điều kiện này, đâu là tỷ lệ thả trúng của bộ nhớ cache? Ở đây, không có ảnh hưởng gì khác ngoài việc xử lý CPU.\n","answer_label":"0.9","answer_id":54391},{"id":14080,"question":"Có tồn tại một hệ thống mà yêu cầu việc thực hiện 800.000 lệnh trên mỗi giao tác. Khi hiệu năng bộ xử lý là 200 MIPS và tỷ lệ hiệu dụng của bộ xử lý là 80%, đâu là công suất xử lý theo số giao tác mỗi giây?","answer_label":"200","answer_id":54395},{"id":14081,"question":"Lựa chọn nào sau đây là mục đích phù hợp của kiểm tra chẵn lẻ của một mô-đun bộ nhớ?","answer_label":"Để phát hiện sự xuất hiện của một lỗi trong khi đọc","answer_id":54399},{"id":14082,"question":"Lựa chọn nào sau đây là mô tả thích hợp của bảng cảm ứng điện dung?","answer_label":"Một trường điện được hình thành trên bề mặt của bảng điều khiển cảm ứng, và vị trí chạm được phát hiện bằng cách bắt sự thay đổi của điện tích bề mặt.","answer_id":54402},{"id":14083,"question":"Lựa chọn nào sau đây là phương thức phù hợp nhất cho việc cài đặt một hệ thống chịu lỗi?","answer_label":"Hệ thống được ghép nối với hai hoặc nhiều hơn các máy tính thay vì dùng một máy tính đơn lẻ.","answer_id":54408},{"id":14084,"question":"Lựa chọn nào sau đây là giải thích phù hợp nhất của một kiểm tra điểm chuẩn đối với một hệ thống máy tính?","answer_label":"Hiệu năng xử lý của một hệ thống được so sánh với các hệ thống khác về các điểm số nhận được nhờ việc thực hiện phần mềm cho việc đo kiểm.","answer_id":54412},{"id":14085,"question":"Có tồn tại hai thiết bị giống nhau, mỗi thiết bị có MTBF là 45 giờ và MTTR là 5 giờ. Đâu là mức độ sẵn dùng của một hệ thống mà kết nối tuần tự hai thiết bị này?","answer_label":"0.81","answer_id":54414},{"id":14086,"question":"Trong các mô tả liên quan tới việc lập lịch tiến trình, lựa chọn nào sau đây là một giải thích phù hợp về phương pháp xoay vòng?","answer_label":"Các tài nguyên CPU được cấp phát cho tiến trình có thể thực thi đầu tiên trong hàng đợi khi một ngắt theo khoảng thời gian được tạo ra.","answer_id":54420},{"id":14087,"question":"Khi SRT (Thời gian còn lại ngắn nhất), cũng được biết đến là SRTF (Thời gian còn lại ngắn nhất trước tiên), được dùng như một phương pháp lập lịch đối với ba tiến trình từ P1 tới P3 được cho trong bảng dưới đây, đâu là tổng thời gian chờ (tính theo giây) đã qua của P2 trước khi nó hoàn tất việc thực thi của mình?\n","answer_label":"15","answer_id":54424},{"id":14088,"question":"Lựa chọn nào sau đây là giải thích về chức năng của bộ lưu trữ mà là một trong các công cụ quản lý dữ liệu?","answer_label":"Là việc gộp vài tệp vào trong một tệp, hoặc trả một tệp về điều kiện ban đầu của nó để thực hiện việc sao lưu và phân phối dữ liệu","answer_id":54426},{"id":14089,"question":"Lựa chọn nào sau đây là một giải thích phù hợp của việc tối ưu trong một bộ biên dịch?","answer_label":"Việc sinh ra một mã đối tượng với hiệu quả quá trình chạy được cải tiến nhờ việc phân tích mã nguồn","answer_id":54433},{"id":14090,"question":"Lựa chọn nào dưới đây được phân loại như chức năng của công cụ kiểm thử tĩnh?","answer_label":"Phát hiện một lỗi trong một chương trình nhờ việc phân tích mã nguồn","answer_id":54435},{"id":14091,"question":"Mạch logic dưới đây cho biết một mạch lật JK. Lựa chọn nào sau đây là bảng chân lý phù hợp đối với mạch lật JK. Ở đây, trạng thái của mỗi tín hiệu đầu ra bị ảnh hưởng chỉ khi tín hiệu đồng hồ CLK thay đổi từ 0 sang 1. “Không đổi” nghĩa là mỗi tín hiệu đầu ra duy trì trạng thái trước đó của nó, và “Chuyển” nghĩa là mỗi tín hiệu đầu ra thay đổi (hoặc chuyển đổi) trạng thái của nó “từ 0 sang 1” hoặc “từ 1 sang 0.”\n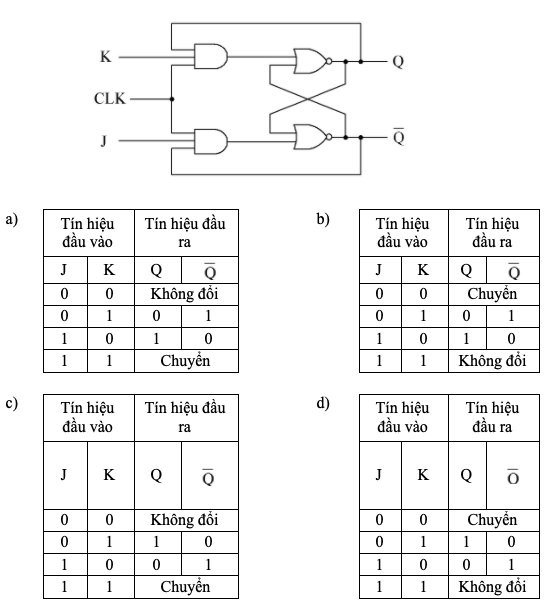","answer_label":"a","answer_id":54438},{"id":14092,"question":"Một bộ chuyển đổi D/A (số-sang-tương-tự) với một độ phân giải 8 bit sinh ra điện áp đầu ra 0 vôn đối với giá trị đầu vào số 0, và điện áp đầu ra 2,5 vôn đối với giá trị đầu vào số 128. Khi một bit thấp nhất của giá trị đầu vào số được thay đổi, lựa chọn nào sau đây là sự thay đổi (tính theo vôn) của điện áp đầu ra mà được sinh ra bởi bộ chuyển đổi D/A?","answer_label":"2.5/128","answer_id":54442},{"id":14093,"question":"Lựa chọn nào sau đây là một mô-đun bộ nhớ mà dùng một mạch lật trong một ô nhớ?","answer_label":"SRAM","answer_id":54449},{"id":14094,"question":"Lựa chọn nào sau đây là chức năng của một giao diện người dùng được dùng cho việc giảm bớt số thao tác của một người dùng mà thường thực hiện công việc theo thói quen?","answer_label":"Một hàm macro nhờ đó một chuỗi các lệnh được nhóm lại cùng nhau","answer_id":54453},{"id":14095,"question":"Lựa chọn nào sau đây là một tệp ảnh rất linh hoạt dựa-trên-thẻ mà có thể là không mất mát hoặc mất mát, và được dùng rộng rãi cho việc trao đổi dữ liệu ảnh kỹ thuật số giữa các nghệ sĩ đồ họa, nhiếp ảnh gia, và công nghiệp xuất bản?","answer_label":"TIFF","answer_id":54457},{"id":14096,"question":"Trong một bảng cơ sở dữ liệu quan hệ, lựa chọn nào sau đây là một cột hoặc một sự kết hợp các cột mà những giá trị của nó được định nghĩa bởi khóa chính của một bảng khác để duy trì toàn vẹn tham chiếu trong cơ sở dữ liệu?","answer_label":"Khóa ngoại","answer_id":54459},{"id":14097,"question":"Cho bản ghi bao gồm tám thuộc tính từ a đến h như hiển thị bên dưới. Khóa chính của bản ghi là sự kết hợp của các thuộc tính a và b. Các thuộc tính h, c, và f có thể được xác định bởi các thuộc tính a, b, và e tương ứng. Lựa chọn nào sau đây là dạng chuẩn ba của bản ghi này?\n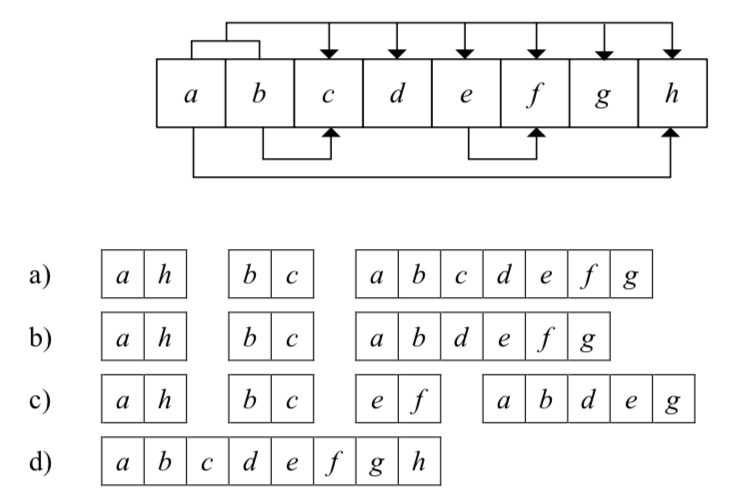","answer_label":"c","answer_id":54464},{"id":14098,"question":"Lựa chọn nào dưới đây là một mô tả thích hợp của các thuộc tính ACID (Atomicity, Consistency, Isolation, và Durability) mà được xem như là các tính năng xử lý giao tác chính của một hệ thống quản trị cơ sở dữ liệu (DBMS)?","answer_label":"Durability (Tính bền chặt) nói đến việc đảm bảo rằng mỗi khi người dùng đã nhận được thông báo thành công, các giao tác tiếp tục và không được làm lại.","answer_id":54468},{"id":14099,"question":"Khi hai bảng cơ sở dữ liệu quan hệ A và B được cho như bên dưới, lựa chọn nào sau đây là bảng thích hợp mà cho biết kết quả của thao tác quan hệ A ÷ B?\n","answer_label":"b","answer_id":54471},{"id":14100,"question":"Đối với bảng “Product” được cho bên dưới, một giao tác mà thực hiện lệnh SQL bên dưới kết thúc bất thường bởi vì sự xuất hiện của một deadlock (khóa chết)? Lựa chọn nào sau đây là bảng “Product” sau khi kết thúc bất thường? Ở đây, các giao tác khác dùng bảng “Product” như là tham chiếu nhưng không cập nhật nó.\n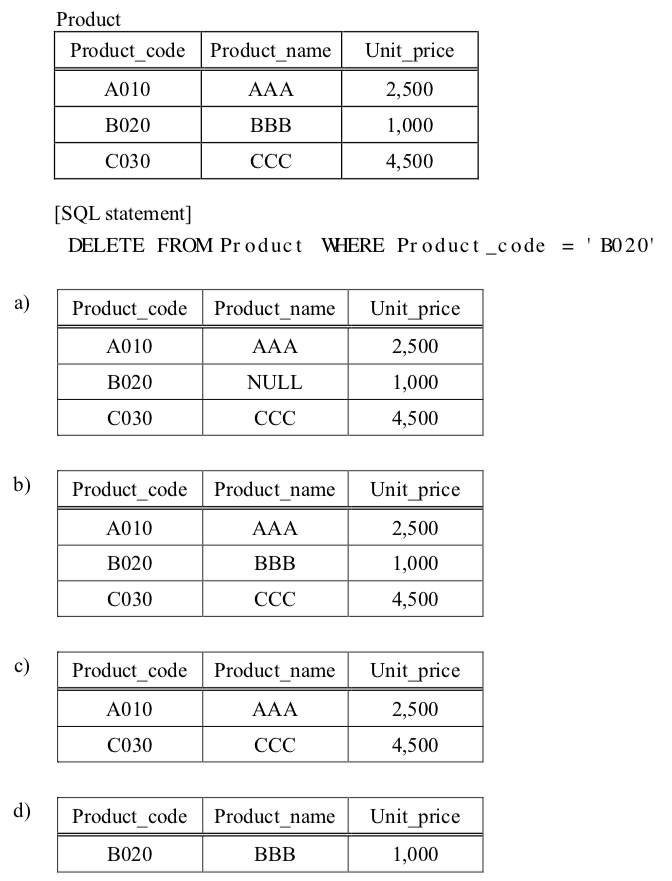","answer_label":"b","answer_id":54475},{"id":14101,"question":"Trong môi trường Internet, một máy tính có thể gửi lệnh ping “ping 11.22.33.44” tới server Web (ví dụ www.xyz.com) của một Công ty XYZ và rồi nhận thành công một thông điệp echo reply (trả lời lại). Thêm nữa, máy tính có thể duyệt website theo URL “http://11.22.33.44”, nhưng không thể duyệt dùng website đó bởi “http://www.xyz.com”. Trong mô hình tham chiếu cơ bản OSI, lựa chọn nào sau đây là tầng mà có khả năng nhất chịu trách nhiệm cho vấn đề như vậy?","answer_label":"Tầng Ứng dụng","answer_id":54478},{"id":14102,"question":"Trong lược đồ đánh địa chỉ IPv4, khi mặt nạ mạng con “255.255.255.224” được dùng cho Lớp C, lựa chọn nào sau đây là số lượng tối đa máy hiệu dụng trên mỗi mạng con, ngoại trừ các địa chỉ mạng và địa chỉ quảng bá?","answer_label":"30","answer_id":54483},{"id":14103,"question":"Lựa chọn nào sau đây là vai trò của một giao thức ICMP mà được dùng như một giao thức tầng Mạng của mô hình tham chiếu cơ bản OSI?","answer_label":"Nó được sử dụng cho các tin nhắn được sinh ra và được gửi lại máy nguồn để chỉ ra những lỗi như không thể tới các đích đến, vượt quá giới hạn thời gian, và các vấn đề tham số, và cũng được dùng bởi các ứng dụng như lệnh ping cho các mục đích chẩn đoán.","answer_id":54487},{"id":14104,"question":"Một quản trị viên hệ thống có một kế hoạch giám sát một mạng để đánh giá nhân viên nào đang sử dụng vượt quá lượng băng thông trên các dịch vụ chia sẻ ngang hàng. Lựa chọn nào sau đây là kỹ thuật thích hợp nhất để đạt được mục đích như vậy?","answer_label":"Dò gói tin","answer_id":54491},{"id":14105,"question":"Lựa chọn nào sau đây là một mô tả thích hợp liên quan đến “HTTP cookie”?","answer_label":"HTTP cookie được dùng để chứa dữ liệu được gửi từ một server Web như một văn bản thuần túy.","answer_id":54495},{"id":14106,"question":"Trong phần về an toàn thông tin được định nghĩa bởi ISO/IEC 27001, lựa chọn nào sau đây là thuộc tính của việc bảo vệ tính chính xác và đầy đủ của các tài sản thông tin?","answer_label":"Toàn vẹn","answer_id":54501},{"id":14107,"question":"Lựa chọn nào sau đây là một đặc điểm thích hợp của MAC (Mã xác thực thông điệp) mà được dùng để xác thực một thông điệp và cung cấp tính toàn vẹn của nó trong mã hóa?","answer_label":"Nó được xây dựng từ các hàm băm mật mã","answer_id":54503},{"id":14108,"question":"Lựa chọn nào sau đây là một đặc điểm của hàm băm mà được dùng cho một chữ ký số?","answer_label":"Là khó khăn để khôi phục lại thông điệp gốc từ bản tóm tắt thông điệp.","answer_id":54507},{"id":14109,"question":"Điều nào sau đây là kỹ thuật salami được sử dụng trong tội phạm máy tính?","answer_label":"Nó là một kỹ thuật mà trong đó trộm cắp được thực hiện trong từng bước nhỏ từ nhiều tài sản để hành vi lừa đảo này không bị phát hiện.","answer_id":54513},{"id":14110,"question":"Ông X gửi một e-mail cho ông Y bằng cách sử dụng Internet. Các nội dung của e-mail phải được giữ bí mật, vì vậy ông X sử dụng mật mã khóa công khai để mã hóa e-mail. Điều nào sau đây là chìa khóa được sử dụng để mã hóa các nội dung của e-mail?","answer_label":"Khoá công khai của ông Y","answer_id":54517},{"id":14111,"question":"Điều nào sau đây là cuộc tấn công vào bảo mật được sử dụng để xâm nhập bất hợp pháp lôi kéo mọi người trong tổ chức tiết lộ mật khẩu và các thông tin bí mật với cớ là khẩn cấp","answer_label":"Kỹ thuật xã hội","answer_id":54519},{"id":14112,"question":"Điều nào sau đây là một tính năng được kết hợp bởi một kẻ tấn công để vào mạng hoặc máy chủ của một công ty?","answer_label":"Cửa sau (Back door)","answer_id":54522},{"id":14113,"question":"Điều nào sau đây là một lời giải thích của BYOD (Bring Your Own Device)?","answer_label":"Một nhân viên mang thiết bị đầu cuối cá nhân của riêng mình đến văn phòng để sử dụng cho công việc, điều đó làm gia tăng những rủi ro bảo mật như nhiễm vi rút do thiết lập bảo mật không đầy đủ.","answer_id":54527},{"id":14114,"question":"Điều nào sau đây là một cơ chế mà theo đó một công ty hay tổ chức quản lý tập trung các trạng thái sử dụng của điện thoại thông minh hoặc các thiết bị khác cho nhân viên mượn bằng những cài đặt tích hợp theo chính sách bảo mật, hoặc bằng cách cung cấp các ứng dụng nghiệp vụ?","answer_label":"MDM (Mobile Device Management)","answer_id":54533},{"id":14115,"question":"Điều nào sau đây là một biện pháp phòng ngừa thích hợp chống lại phần mềm độc hại được đưa vào một máy khách?","answer_label":"Để không virus nào khai thác lỗ hổng và nhiễm vào máy tính thì các mô-đun phần mềm đã sửa đổi hoặc các bản vá lỗi được áp dụng một cách phù hợp với hệ điều hành và các ứng dụng.","answer_id":54537},{"id":14116,"question":"Trong sơ đồ UML hiển thị dưới đây điều nào sau đây được mô tả trong ô trống hình chữ nhật ?\n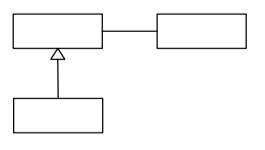","answer_label":"Tên lớp","answer_id":54540},{"id":14117,"question":"Trong phát triển hướng đối tượng, có thể làm những thiết lập mà không ảnh hưởng tới người dùng, ngay cả khi cấu trúc bên trong của một đối tượng bị thay đổi. Vì vậy, có thể tạo ra tình huống mà trong đó người dùng đối tượng không nhất thiết phải biết cấu trúc bên trong của đối tượng. Điều nào sau đây là thuật ngữ biểu diễn khái niệm về việc thực hiện kiểu phát triển như vậy?","answer_label":"Đóng gói","answer_id":54543},{"id":14118,"question":"Trong phát triển phần mềm, điều nào sau đây là một lời giải thích hợp lý về một kiểm thử có sử dụng các giả lập?","answer_label":"Khi thực hiện một kiểm thử từ trên xuống, một mô-đun giả ở cấp thấp hơn được mô-đun cấp cao hơn gọi đến được chuẩn bị sẵn sàng để thay thế cho một phần chưa hoàn thành của chương trình.","answer_id":54548},{"id":14119,"question":"Điều nào sau đây là một lời giải thích hợp lý về sơ đồ chuyển trạng thái được sử dụng để phân tích yêu cầu và thiết kế trong phát triển hệ thống?","answer_label":"Các kích tố thay đổi trạng thái, chẳng hạn thời gian trôi qua và sự thay đổi trong tín hiệu điều khiển, và các thao tác thực hiện sau đó, được mô tả.","answer_id":54553},{"id":14120,"question":"Trong các hoạt động phát triển phần mềm, điều nào mà sau đây là một lời giải thích về tái bố cục (refactoring)?","answer_label":"Để cải thiện khả năng bảo trì của một chương trình, cấu trúc bên trong của nó được sửa đổi mà không có bất kỳ thay đổi nào trong các đặc tả kỹ thuật bên ngoài.","answer_id":54554},{"id":14121,"question":"Mỗi chữ (tức là P, D, C, và A) của chu kỳ \"PDCA\" được sử dụng để quản lý tiến độ phát triển hệ thống và quản lý chất lượng phần mềm đều là chữ cái đầu tiên của từ tương ứng. Từ nào sau đây là từ được biểu diễn bởi chữ thứ ba \"C\"?","answer_label":"Check","answer_id":54560},{"id":14122,"question":"Đường nào sau đây là đường găng của các hoạt động dự án được thể hiện trong sơ đồ mũi tên dưới đây?\n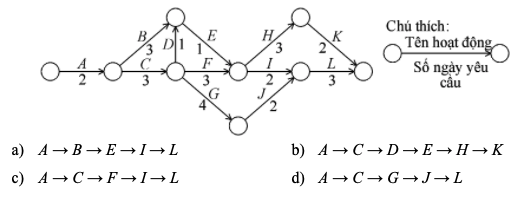","answer_label":"d","answer_id":54565},{"id":14123,"question":"Theo ITIL (IT Infrastructure Library – Thư viện hạ tầng CNTT), CSA (Configuration Status Accounting - Kế toán trạng thái cấu hình) là việc ghi chép và báo cáo mọi dữ liệu hiện tại và lịch sử có liên quan tới mỗi CI (Configuration Item- Mục cấu hình) trong suốt vòng đời của nó. Điều nào sau đây là một hoạt động thích hợp được thực hiện như một phần của CSA?","answer_label":"Thực hiện việc kiểm soát thay đổi tích hợp","answer_id":54569},{"id":14124,"question":"Theo tài liệu \"Hướng dẫn Khung kiến thức về Quản lý dự án\" (PMBOK), điều nào sau đây là lĩnh vực kiến thức bao gồm các quá trình và các hoạt động để nhận diện, xác định, kết hợp, thống nhất và phối hợp các quá trình khác nhau và các hoạt động quản lý dự án trong Các nhóm quá trình quản lý dự án?","answer_label":"Quản lý tích hợp dự án","answer_id":54571},{"id":14125,"question":"Điều nào sau đây là đặc điểm thích hợp nhất của phương pháp di chuyển kiểu \"big bang\" - một trong những phương pháp di chuyển hệ thống?","answer_label":"Các vấn đề xảy ra trong quá trình di chuyển sang hệ thống mới có một tác động lớn.","answer_id":54577},{"id":14126,"question":"Điều nào sau đây là một lời giải thích của một \"lỗi đã biết\" trong việc quản lý dịch vụ CNTT?","answer_label":"Một vấn đề mà nguyên nhân sâu xa của nó đã được xác định hoặc tồn tại một cách giải quyết cho nó rồi","answer_id":54579},{"id":14127,"question":"Điều nào sau đây là một biểu đồ thích hợp cho phí sử dụng một hệ thống máy tính trong một dịch vụ CNTT dựa trên sự suy giảm phương pháp tỷ lệ đồng hồ đo: \n","answer_label":"c","answer_id":54584},{"id":14128,"question":"Điều nào sau đây là một lời giải thích thích hợp về một tài liệu làm việc của kiểm toán?","answer_label":"Nó là một hồ sơ triển khai thủ tục kiểm toán được thực hiện bởi kiểm toán viên, tạo ra cơ sở cho những ý kiến kiểm toán","answer_id":54589},{"id":14129,"question":"Điều nào sau đây là một mô tả thích hợp liên quan đến cấu trúc thực hiện kiểm toán hệ thống?","answer_label":"Để giúp người yêu cầu kiểm toán có thể đưa ra các hướng dẫn cải tiến dựa trên báo cáo kiểm toán, kiểm toán viên hệ thống báo cáo kết quả kiểm toán cho người yêu cầu kiểm toán.","answer_id":54590},{"id":14130,"question":"Trong giai đoạn thiết kế hệ thống, điều nào sau đây là điều cần được kiểm tra trong quá trình kiểm toán việc kiểm soát giảm thiểu nguy cơ không thực hiện được yêu cầu của người dùng?","answer_label":"Bộ phận người dùng nên tham gia vào việc xem xét thiết kế hệ thống.","answer_id":54597},{"id":14131,"question":"Điều nào sau đây là một lời giải thích của SOA?","answer_label":"SOA tạo điều kiện đáp ứng với những thay đổi nghiệp vụ bằng cách xây dựng phần mềm từ các thành phần được gọi là dịch vụ.","answer_id":54599},{"id":14132,"question":"Điều nào sau đây là một mô tả thích hợp của BPR ((Business Process Reengineering)?","answer_label":"BPR là một kỹ thuật quản lý được sử dụng để thiết kế lại và tái cơ cấu các quá trình tạo ra giá trị trong một tổ chức nhằm đạt được lợi ích đáng kể về năng suất, lợi nhuận, dịch vụ và chất lượng thông qua việc tối đa tiềm năng của các cá nhân và nhóm.","answer_id":54605},{"id":14133,"question":"Trong việc lập kế hoạch đầu tư tin học hóa, điều nào sau đây là một lời giải thích của ROI - một chỉ số đánh giá về giá trị đầu tư?","answer_label":"ROI là một số đo được tính bằng cách chia lợi nhuận, được tạo ra thông qua các yếu tố, chẳng hạn như tăng doanh thu và giảm chi phí, cho số tiền đầu tư","answer_id":54607},{"id":14134,"question":"Điều nào sau đây là hành động thích hợp nhất cần được thực hiện để loại bỏ \"khoảng cách số\"?","answer_label":"Tăng cường các cơ hội học tập kiến thức thông tin, và chuẩn bị một môi trường để tạo điều kiện thuận lợi hơn cho việc sử dụng thiết bị thông tin và viễn thông cùng với các dịch vụ thông tin","answer_id":54611},{"id":14135,"question":"Theo \"Chiến lược cạnh tranh\" do Philip Kotler đề xuất, công ty kiểu nào sau đây là loại công ty có thị phần nhỏ, nhưng có mục tiêu chiến lược là tăng thu nhập và có được một vị trí độc tôn bằng cách tập trung các nguồn lực quản lý cho các sản phẩm và dịch vụ cụ thể:","answer_label":"Thị trường ngách","answer_id":54617},{"id":14136,"question":"Khi hiệu quả của việc cải tiến được đánh giá một cách định lượng, việc đánh giá tổng thể có trọng số được sử dụng như là một phương pháp tích hợp và định lượng những kết quả đánh giá của nhiều mục. Đề xuất nào sau đây là đề xuất cải tiến cần được ưu tiên trong bảng dưới đây?\n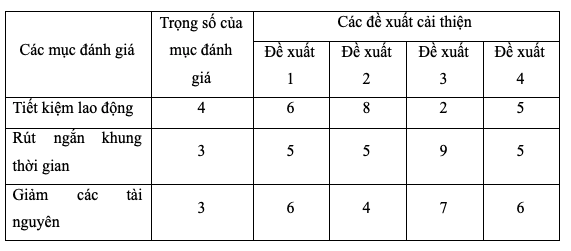","answer_label":"Đề xuất 2","answer_id":54619},{"id":14137,"question":"Điều nào sau đây là kỹ thuật quản lý kinh doanh được sử dụng để phát triển các mục tiêu và biện pháp để thực hiện một chiến lược đã được quy hoạch, có xem xét đến các mối quan hệ phù hợp lẫn nhau giữa bốn khía cạnh (đó là tài chính, khách hàng, quy trình nghiệp vụ nội bộ và học hỏi và tăng trưởng)?","answer_label":"Thẻ điểm cân bằng","answer_id":54622},{"id":14138,"question":"Điều nào sau đây là lời giải thích về “cái đuôi dài”?","answer_label":"Các đuôi dài đề cập đến tình huống mà trong đó phần trăm doanh số bán hàng đối với một nhóm sản phẩm bán chậm không thể bỏ qua trong tổng doanh số mua sắm trên Internet.","answer_id":54629},{"id":14139,"question":"Điều nào sau đây là mục đích của SCM?","answer_label":"Để giảm chi phí và rút ngắn thời gian giao hàng thông qua việc quản lý tích hợp thông tin giữa nhiều công ty hoặc tổ chức từ thu mua đến bán hàng","answer_id":54633},{"id":14140,"question":"Hình dưới đây cho thấy mô hình giao dịch của một dịch vụ bảo lãnh được sử dụng trên một trang web đấu giá hoặc giao dịch khác như thế. Điều nào sau đây là hành động tương ứng với (5) trong hình này? Ở đây, các mục từ (1) đến (6) chỉ ra trình tự giao dịch, và mỗi mục từ (3) đến (6) tương ứng với một phương án từ a) đến d).\n","answer_label":"Thông báo đã nhận sản phẩm","answer_id":54635},{"id":14141,"question":"Điều nào sau đây là một lời giải thích của RFID?","answer_label":"RFID là một tổ hợp của một mạch tích hợp cực kỳ nhỏ và một ăng-ten, được sử dụng cho một thẻ điện tử cho phép nhận diện và định vị một đối tượng bằng cách sử dụng kỹ thuật nhận dạng tự động không dây.","answer_id":54638},{"id":14142,"question":"Điều nào sau đây là một biểu đồ hoặc sơ đồ được sử dụng để phân tích các mối quan hệ giữa hai biến và bao gồm một trục ngang chứa các giá trị đo được của một biến và một trục dọc biểu diễn số đo của biến kia?","answer_label":"Sơ đồ phân tán","answer_id":54645},{"id":14143,"question":"Khi mối quan hệ giữa giá niêm yết của một sản phẩm và nhu cầu sản phẩm được định nghĩa như là một biểu thức tuyến tính, số nào sau đây là giá trị số thích hợp để chèn vào ô trống A dưới đây?\n(1) Khi bảng giá niêm yết được đặt là 30 đô la, nhu cầu là 0 đơn vị.\n(2) Khi giá niêm yết được đặt là 10 đô la, nhu cầu là 60.000 đơn vị.\n(3) Khi giá niêm yết được đặt là 15 đô la, nhu cầu là ( A ) đơn vị.","answer_label":"45,000","answer_id":54649},{"id":14144,"question":"Điều nào sau đây là kỹ thuật dự báo thực hiện thủ tục dưới đây để giải quyết những vấn đề khó dự báo tương lai thực hiện được nếu sử dụng các kỹ thuật khác?\n[Thủ tục]\n(1)\tChọn một số chuyên gia như là những người trả lời các câu hỏi.\n(2)\tTổng hợp các câu trả lời những câu hỏi để dùng trong việc phản hồi, và hỏi lại một lần nữa.\n(3)\tXử lý thống kê các câu trả lời, và trình bày các câu trả cùng với phân phối của chúng.","answer_label":"Phương pháp Delphi","answer_id":54652},{"id":14145,"question":"Như được thể hiện trong bảng dưới đây, một nhà máy sản xuất ba loại sản phẩm: X, Y, Z. Lợi nhuận tối đa có thể là bao nhiêu đô la? Ở đây, có một giới hạn trên về nhu cầu hàng tháng đối với từng sản phẩm. Ngoài ra, nhà máy có thể được sử dụng tới 200 giờ mỗi tháng để lắp ráp sản phẩm, nhưng không thể lắp ráp song song nhiều sản phẩm.\n","answer_label":"33,000","answer_id":54657},{"id":14146,"question":"Điều nào sau đây là hình thức tổ chức có các đặc điểm từ (1) đến (4) được mô tả dưới đây?\n(1)\tTổ chức được thành lập bằng cách tập hợp các chuyên gia cần thiết từ tất cả các bộ phận để đạt được mục tiêu chiến lược.\n(2)\tTổ chức này là một tổ chức chiến lược để ứng phó với những thay đổi trong môi trường, và độc lập với các phòng ban chức năng.\n(3)\tTổ chức có tính mềm dẻo để giải tán nếu các mục tiêu dự kiến đã đạt được.\n(4)\tMột đội đặc nhiệm thuộc về hình thức tổ chức này.","answer_label":"Tổ chức dự án","answer_id":54661},{"id":14147,"question":"Mối quan hệ giữa giá trị \"x\"của một yếu tố nào đó trong việc sản xuất một sản phẩm và giá trị\"y\" của một đặc tính chất lượng sản phẩm được vẽ như thể hiện trong hình dưới đây. Lựa chọn nào sau đây có thể được hiểu từ hình này?\n","answer_label":"Hệ số tương quan của x và y là âm.","answer_id":54663},{"id":14148,"question":"Điều nào sau đây KHÔNG được bảo vệ bằng \"bản quyền\" theo Hiệp định của WTO về các khía cạnh liên quan thương mại của quyền sở hữu trí tuệ (TRIPS)?","answer_label":"Ngôn ngữ lập trình và quy ước của nó","answer_id":54668},{"id":14390,"question":"Điều nào sau đây cung cấp chức năng ánh xạ giữa tên miền và địa chỉ IP trong mạng TCP / IP?","answer_label":"DNS","answer_id":55596},{"id":14391,"question":"Cái nào dưới đây là một mục đích thích hợp của việc cài đặt tường lửa trong mạng máy tính?","answer_label":"Để chặn và cho phép dữ liệu traffic","answer_id":55600},{"id":14392,"question":"Điều nào sau đây được mô tả bằng đồ thị bằng sơ đồ E-R?","answer_label":"Thực thể và mối quan hệ giữa các thực thể","answer_id":55605},{"id":14393,"question":"Bạn đang xây dựng một cơ sở dữ liệu mới cho một công ty có 10 bộ phận. Mỗi bộ phận chứa nhiều nhân viên. Ngoài ra, mỗi nhân viên có thể làm việc cho một số bộ phận. Bạn nên lập mô hình hợp lý mối quan hệ giữa thực thể bộ phận và thực thể nhân viên như thế nào?","answer_label":"Tạo một entry mới, tạo một quan hệ một-nhiều từ nhân viên đến entry mới và tạo một quan hệ một-nhiều từ mục nhập bộ phận đến entry mới.","answer_id":55608},{"id":14394,"question":"Người dùng A đưa ra lệnh như sau:\n\nUPDATE cust_orders\nSET id = 200\nWHERE id = 1\n\nSau đó, người dùng B đưa ra lệnh này như sau:\n\nUPDATE cust_orders\nĐẶT id = 300\nWHERE id = 1\n\nNgười dùng B thông báo cho bạn rằng câu lệnh Update của anh ấy/cô ấy dường như bị treo. sau đây là một giải pháp khả thi mà bạn có thể tìm thấy?","answer_label":"Yêu cầu người dùng A thực hiện transaction.","answer_id":55611},{"id":14395,"question":"Trong quản lý khôi phục cơ sở dữ liệu, điều nào sau đây giải thích thích hợp incremental logging với deferred update?","answer_label":"Giá trị mới của mục cập nhật được lưu trong log.","answer_id":55617},{"id":14396,"question":"Việc gắn chữ ký số vào software đóng g trên Internet nhằm mục đích gì?","answer_label":"Để đảm bảo rằng nội dung phần mềm không bị giả mạo","answer_id":55619},{"id":14397,"question":"Điều nào sau đây có thể được thực hiện bằng cách sử dụng chức năng lọc gói tin của tường lửa?","answer_label":"Để chỉ cho phép các gói có số cổng TCP cụ thể truyền từ Internet vào mạng nội bộ","answer_id":55623},{"id":14398,"question":"Bảy công cụ kiểm soát chất lượng cơ bản, truyền thống bao gồm Phiếu kiểm tra chất lượng (Check sheet), Biểu đồ Pareto (Pareto chart), Phân tầng (Stratification), Biểu đồ phân tán (Scatter Diagram), Biểu đồ tần suất (Histogram), và Biểu đồ kiểm soát (Control Chart). Cái cuối cùng (hoặc thứ 7) là gì?","answer_label":"Biểu đồ nguyên nhân- ảnh hưởng (Cause and effect diagram)","answer_id":55628},{"id":14626,"question":"Trong những lựa chọn dưới đây, đâu là tiêu chuẩn quốc tế xác định giải thuật mã hóa được sử dụng để nén dữ liệu ảnh tĩnh?","answer_label":"JPEG","answer_id":56463},{"id":14630,"question":"Khi sử dụng SELECT để join 2 bảng T1 và T2 như hình ảnh bên dưới, vậy bảng được tạo ra sẽ là?\n","answer_label":"d","answer_id":56478},{"id":14636,"question":"Câu lệnh SQL nào có thể sử dụng để hoàn tác những thay đổi trong cơ sở dữ liệu kể từ commit cuối?","answer_label":"Rollback","answer_id":56501},{"id":14638,"question":"Mục đích chính của việc khóa tài nguyên trong hệ quản trị cơ sở dữ liệu là gì?","answer_label":"Để duy trì tính toàn vẹn của dữ liệu","answer_id":56507},{"id":14671,"question":"Đâu là tập hợp các đặc điểm của kho dữ liệu khi so sánh với cơ sở dữ liệu truyền thống?","answer_label":"Tích hợp, hướng đối tượng, không dễ thay đổi, và biến đổi theo thời gian (Integrated, subject-oriented, non-volatile, and time-variant)","answer_id":56614},{"id":14678,"question":"Đâu là địa chỉ MAC được sử dụng bởi nhiều giao thức, ví dụ như ARP (Address Resolution Protocol) và RIP (Routing Information Protocol) để truyền dữ liệu đến tất cả các máy chủ trong mạng con cục bộ?","answer_label":"FF-FF-FF-FF-FF-FF","answer_id":56643},{"id":14686,"question":"Trong môi trường IPv4, khi subnet mask \"255.255.255.224\" được sử dụng cho mạng lớp C, có bao nhiêu địa chỉ IP (bao gồm cả địa chỉ dành riêng hoặc địa chỉ vô hiệu) có thể được gán cho các mạng con và máy chủ của mỗi mạng con tương ứng?\n","answer_label":"a","answer_id":56667},{"id":14689,"question":"Đâu là một lớp của mô hình tham chiếu cơ bản OSI cung cấp RPC (Remote Procedure Call)hỗ trợ, duy trì tính toàn vẹn của kết nối giữa các nút và kiểm soát trao đổi dữ liệu?","answer_label":"Lớp Session","answer_id":56679},{"id":14691,"question":"Đâu là giao thức không kết nối sử dụng tốc độ và chi phí thấp làm lợi thế chính trong lớp truyền tải của mô hình tham chiếu cơ bản OSI?","answer_label":"UDP","answer_id":56686},{"id":14694,"question":"Giao thức nào sau đây được lệnh \"ping\" sử dụng để xác minh liên kết giao tiếp giữa nguồn và đích đang hoạt động trên môi trường mạng TCP/IP?","answer_label":"ICMP","answer_id":56695},{"id":14703,"question":"Đâu là tập hợp thông tin mà máy chủ DHCP cung cấp động cho máy khách để tham gia vào mạng TCP/IP?","answer_label":"Địa chỉ IP, subnet mask, địa chỉ gateway mặc định, địa chỉ máy chủ DNS","answer_id":56731},{"id":14708,"question":"Đâu là sự kết hợp được dùng để xác định địa chỉ socket trong môi trường mạng TCP/IP?","answer_label":"Địa chỉ IP và số cổng","answer_id":56747},{"id":14715,"question":"Bạn nhận được một tin nhắn có chữ ký điện tử được gửi qua e-mail. Bạn có thể kiểm tra được điều gì bằng cách xác minh chữ ký số của tin nhắn đó?","answer_label":"Tin nhắn không bị làm sai lệch","answer_id":56775},{"id":14722,"question":"Khi Mr.A gửi thông điệp bí mật cho Mr.B bằng cách sử dụng mã hóa public key như hình bên dưới thì khóa K thích hợp được sử dụng để mã hóa là:\n","answer_label":"Public key của Mr.B","answer_id":56804},{"id":14727,"question":"Đâu là một kỹ thuật để thu thập những dữ liệu nhạy cảm, bí mật bằng cách tìm kiếm dữ liệu còn sót lại trong máy tính hoặc bằng cách kiểm tra phương tiện bị bỏ đi/đánh cắp như là giấy in, băng, đĩa?","answer_label":"Scavenging","answer_id":56817},{"id":14731,"question":"Tập hợp những máy tính bị xâm nhập mà người chủ không nhận ra, bị điều khiển từ xa bởi kẻ tấn công nhằm mục đích gửi thư rác hoặc tấn công những máy tính khác gọi là gì?","answer_label":"Botnet","answer_id":56831},{"id":14736,"question":"Một tưởng lửa kiểu lọc gói tin được cài đặt tại điểm kết nối giữa một mạng nội bộ và mạng Internet. Khi tường lửa có thể truy cập đến máy chủ web (cổng 80) trên Internet từ máy tính cá nhân trong mạng nội bộ thì đâu là quy tắc lọc gói tin cho phép?\n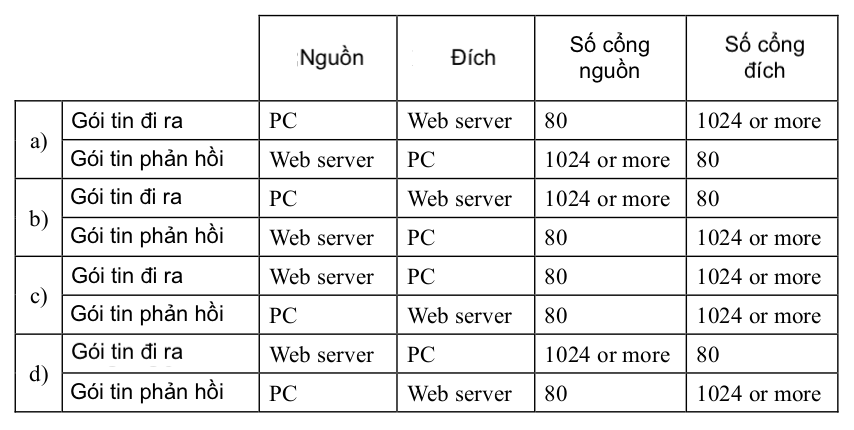","answer_label":"b","answer_id":56851},{"id":14740,"question":"Kỹ thuật xử lý ảnh nào sau đây sử dụng để dán một hình ảnh 2 chiều (ví dụ như mẫu hoặc thiết kế) lên bề mặt của đối tượng được mô hình hóa?","answer_label":"Texture mapping","answer_id":56869},{"id":14742,"question":"Khái niệm nào sau đây đã bao gồm cả lược đồ E-R và E-R nâng cao?","answer_label":"Lực lượng (Cardinality)","answer_id":56872},{"id":14748,"question":"Đâu là mô tả chính xác nhất về honeypots?","answer_label":"Hệ thống máy tính được thiết kế để phát hiện hoặc chống lại những truy cập trái phép","answer_id":56897},{"id":14753,"question":"Mô hình dữ liệu trong sơ đồ dưới đây được thực hiện với 3 bảng. Mô hình dữ liệu được mô tả bởi UML. Đâu là giá trị của A và B trong bảng \"Transfer\" chứa bản ghi chỉ ra rằng \"500$ doanh số của công ty X được chuyển vào tài khoản trong ngày 04/04/2017\">\n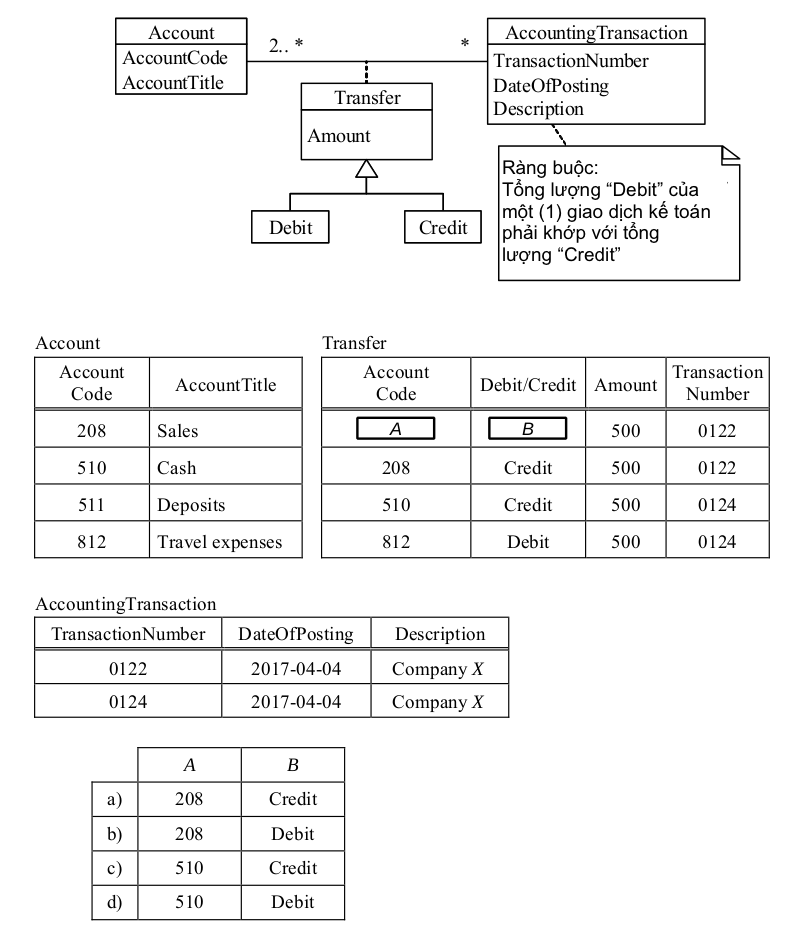","answer_label":"d","answer_id":56918},{"id":14809,"question":"Sau khi relation X và Y được join với nhau thì đâu là phép toán đại số quan hệ để thu được relation Z?\n","answer_label":"Phép chiếu và phép chọn (Projection and selection)","answer_id":57135},{"id":14811,"question":"Trong một hệ quản trị cơ sở dữ liệu, khi nhiều chương trình giao dịch đồng thời cập nhật cùng một cơ sở dữ liệu thì công nghệ nào được sử dụng để ngăn chặn những mâu thuẫn về logic?","answer_label":"Kiểm soát loại trừ (Exclusive control)","answer_id":57141},{"id":14814,"question":"Ví dụ về việc sử dụng \"big data\", quy trình nào sau đây sử dụng phương pháp thống kê hoặc các phương pháp khác để thu được kiến thức mới (chẳng hạn như xu hướng và mẫu) từ một lượng dữ liệu rất lớn?","answer_label":"Data mining","answer_id":57153},{"id":14817,"question":"Thông tin nào sau đây giúp cho bộ định tuyến (router) xác định đích của gói tin gửi đến?","answer_label":"Địa chỉ IP đích","answer_id":57164},{"id":14820,"question":"Trong mô hình tham chiếu cơ bản OSI, đâu là lớp có các cầu hoạt động?","answer_label":"Lớp Datalink","answer_id":57178},{"id":14823,"question":"Trong TCP/IP, giao thức nào cho phép máy chủ tự động cấu hình máy khách của nó với thông tin mạng như địa chỉ IP, subnetmask và địa chỉ gateway mặc định?","answer_label":"DHCP","answer_id":57189},{"id":14826,"question":"SDN (Software-Defined Networking) sử dụng OpenFlow được định nghĩa là:","answer_label":"Là một công nghệ mạng phân tách các chức năng để truyền dữ liệu và định tuyến, được thực hiện với sự kết hợp của các thiết bị mạng chuyên dụng để truyền dữ liệu và định tuyến dựa trên phần mềm","answer_id":57201},{"id":14997,"question":"Khi việc sản xuất (production) được lập kế hoạch dựa trên công thức tính toán và bảng dưới đây, giá trị của kế hoạch sản xuất C (production plan C) là bao nhiêu? Ở đây, hàng tồn kho được chuyển tiếp (carry-over inventory) vào ngày 1/4 bằng 400 phần hàng tồn kho thực tế (actual inventory) vào ngày 31/3.\n","answer_label":"4,850","answer_id":57932},{"id":15050,"question":"Đâu là giải thích đúng của BCP (Business Continuity Plan)?","answer_label":"Để tránh rủi ro gián đoạn kinh doanh hoặc khắc phục kịp thời sau các thiệt hại, một chính sách hoặc một quy trình hoạt động được chuẩn bị trước.","answer_id":58307},{"id":15052,"question":"Tổ chức nào sau đây là một tổ chức được thành lập trong một khoảng thời gian giới hạn nhất định để giải quyết một vấn đề và bị giải tán khi vấn đề được giải quyết?","answer_label":"Tổ chức dự án (Project organization)","answer_id":58322},{"id":15053,"question":"Biểu đồ nào sau đây là biểu đồ hai lớp bao gồm biểu đồ thanh hiển thị các mục kiểm soát được sắp xếp theo thứ tự tần suất giảm dần và biểu đồ đường thể hiện phần trăm tích lũy của từng mục?","answer_label":"Biểu đồ Patero","answer_id":58329},{"id":15054,"question":"Báo cáo tài chính nào sau đây thể hiện tài sản, nợ phải trả và tài sản ròng của một công ty tại một thời điểm nhất định và cho biết điều kiện tài chính của công ty?","answer_label":"Bảng cân đối kế toán","answer_id":58334},{"id":15057,"question":"Khi biên tập viên chính của nhà xuất bản bỏ qua một phần trong bản thảo của tác giả mà không được sự đồng ý của tác giả, điều nào sau đây bị vi phạm theo điều ước quốc tế được gọi là Công ước Berne về bảo hộ tác phẩm văn học và nghệ thuật?","answer_label":"Quyền nhân thân","answer_id":58349},{"id":15058,"question":"Trong phát triển phần mềm sử dụng mô hình thác nước, mô tả nào sau đây là mô tả thích hợp liên quan đến chi phí sửa lỗi được phát hiện trong quá trình kiểm tra hoạt động?","answer_label":"Các lỗi thiết kế bên ngoài không chỉ ảnh hưởng đến chương trình mà còn ảnh hưởng đến hướng dẫn sử dụng và các tài liệu khác, do đó, những lỗi đó sẽ tốn nhiều chi phí sửa hơn so với lỗi mã hóa.","answer_id":58361},{"id":15060,"question":"Biểu đồ nào sau đây là biểu đồ hoặc đồ thị thể hiện chất lượng của sản phẩm theo thứ tự thời gian và được sử dụng để xác định liệu quá trình sản xuất có ở trạng thái ổn định trong giới hạn kiểm soát hay không?","answer_label":"Biểu đồ kiểm soát","answer_id":58373},{"id":15062,"question":"Khi áp dụng phương pháp tỷ lệ tính theo đồng hồ giảm dần cho tổng phí sử dụng hệ thống máy tính, phí trên một đơn vị sử dụng sẽ giảm khi mức sử dụng hệ thống tăng lên.\nBiểu đồ nào sau đây là biểu đồ thể hiện phương pháp này?\nTrục Y: Total charge, tức tổng chi phí\nTrục X: time, tức thời gian\n","answer_label":"c","answer_id":58386},{"id":15063,"question":"Mô tả nào sau đây là mô tả thích hợp liên quan đến bảo trì ứng dụng?","answer_label":"Việc hoàn thành bảo trì được ghi lại để ngăn chặn các hoạt động bảo trì bị bỏ dở.","answer_id":58391},{"id":15066,"question":"Trong số các đặc điểm của cơ cấu tổ chức bàn phục vụ, đặc điểm nào sau đây là đặc điểm của bàn phục vụ cục bộ?","answer_label":"Bằng cách đặt bàn dịch vụ gần người dùng, các dịch vụ chuyên sâu được cung cấp cho những người dùng có ngôn ngữ và văn hóa khác nhau hoặc cho khách VIP bởi các nhân viên dịch vụ chuyên biệt.","answer_id":58409},{"id":15069,"question":"Trong giai đoạn thiết kế hệ thống, khi thực hiện đánh giá đối với việc kiểm soát nhằm giảm rủi ro mà các yêu cầu của người sử dụng không được đáp ứng, thì điểm nào sau đây cần được kiểm tra?","answer_label":"Kiểm tra xem bộ phận người dùng có tham gia xem xét các tài liệu thiết kế hệ thống hay không","answer_id":58424},{"id":15072,"question":"Khi kiểm soát CNTT được phân loại thành kiểm soát phòng ngừa và kiểm soát thám tử, điều nào sau đây được áp dụng cho kiểm soát thám tử?","answer_label":"Một danh sách kết quả từ việc nhập dữ liệu được kiểm tra chéo với biểu mẫu đầu vào.","answer_id":58436},{"id":15077,"question":"Điều nào sau đây là giải thích về Biểu đồ tương đồng (affinity diagram)?","answer_label":"Đó là một phương pháp mà thông tin thu thập được được nhóm lại theo mối quan hệ tương hỗ và các vấn đề cần giải quyết được làm rõ.","answer_id":58451},{"id":15078,"question":"Từ quan điểm quản lý doanh nghiệp, điều nào sau đây là giải thích về BPM?","answer_label":"Chu trình quản lý phân tích, thiết kế, thực hiện và cải tiến được kết hợp vào các quy trình kinh doanh để các quy trình kinh doanh có thể liên tục được xem xét để cải tiến và tích hợp với các quy trình tối ưu.","answer_id":58466},{"id":15083,"question":"Điều nào sau đây là giải thích về SOA (Service-Oriented Architecture)?","answer_label":"Đó là một khái niệm mà các chức năng của phần mềm được coi như các thành phần được gọi là dịch vụ, và các dịch vụ này được kết hợp với nhau để tạo nên một hệ thống.","answer_id":58494},{"id":15086,"question":"Điều nào sau đây là giải thích của SCM?","answer_label":"Một loạt hoạt động kinh doanh bao gồm mua, sản xuất, bán và phân phối được xem xét trên quan điểm tối ưu hóa tổng thể giữa các công ty nhằm giảm thời gian giao hàng và hàng tồn kho.","answer_id":58496},{"id":15093,"question":"Điều nào sau đây tương ứng với ví dụ về các yêu cầu \"phi chức năng\"?","answer_label":"Lựa chọn các tiêu chuẩn phát triển dựa trên ngôn ngữ được sử dụng trong phát triển hệ thống","answer_id":58527},{"id":15095,"question":"Khi sản phẩm của chính công ty được phân tích bằng cách sử dụng phân tích SWOT, yếu tố nào sau đây được phân loại là yếu tố bên ngoài?","answer_label":"Mối đe dọa của các đối thủ cạnh tranh mới","answer_id":58541},{"id":15097,"question":"Mục đích của CRM là gì?","answer_label":"Để có được lòng trung thành của khách hàng và tối đa hóa giá trị lâu dài của khách hàng","answer_id":58542},{"id":15099,"question":"Điều nào sau đây là giải thích về phương tiện truyền thông xã hội?","answer_label":"Nó cung cấp một cơ chế thúc đẩy sự kết nối giữa những người dùng để thông tin do một người dùng đăng trên Internet được truyền tải rộng rãi đến một số lượng lớn người dùng.","answer_id":58556},{"id":15105,"question":"Nội dung nào sau đây là giải thích về năng lực cốt lõi được áp dụng trong quản trị kinh doanh?","answer_label":"Nó đề cập đến một nhóm các kỹ năng và công nghệ độc đáo của một công ty là nguồn gốc của ưu thế cạnh tranh và vượt trội hơn so với các đối thủ cạnh tranh.","answer_id":58569},{"id":15106,"question":"Quy trình mua sắm nào sau đây cho phép các nhà cung cấp đấu thầu với nhau trên Internet để bán sản phẩm hoặc dịch vụ của họ theo các điều kiện do khách hàng chung quy định?","answer_label":"Đấu giá ngược","answer_id":58586},{"id":15111,"question":"Giải thích nào sau đây về quản lý tri thức?","answer_label":"Hoạt động kinh doanh được tiến hành nhằm nâng cao khả năng giải quyết vấn đề của toàn bộ lực lượng lao động bằng cách chia sẻ thông tin, kỹ năng và hiểu biết phân tán trong một công ty.","answer_id":58607},{"id":15335,"question":"Mô tả nào sau đây là phù hợp liên quan đến kiểm tra hộp đen?","answer_label":"Ngay cả khi chương trình được kiểm tra có chứa mã dư thừa, loại mã đó không thể được phát hiện.","answer_id":59484},{"id":15336,"question":"Điều nào sau đây là hạng mục bảo trì hệ thống thích hợp được thực hiện với mục đích thêm các tính năng mới vào hệ thống hiện có hoặc nâng cao các tính năng hiện có?","answer_label":"Bảo trì hoàn hảo","answer_id":59501},{"id":15337,"question":"Điều nào sau đây là giải thích phù hợp về phương thức phát triển phần mềm Agile?","answer_label":"Một mô hình dành riêng cho một nhóm các phương pháp phát triển thích ứng, lặp đi lặp lại và gia tăng, chẳng hạn như XP và Scrum, đồng thời tập trung vào sự hợp tác và phản ứng với những thay đổi trong khoảng thời gian ngắn nhất một cách bền vững","answer_id":59513},{"id":15342,"question":"Thứ tự mà các hoạt động từ A đến F được thực hiện trong quy trình phát triển hệ thống sử dụng mô hình thác nước được thực hiện theo thứ tự nào sau đây?\n[Mô tả các hoạt động]\nA: Điều tra và phân tích các vấn đề hiện tại và xác định các yêu cầu đối với hệ thống mục tiêu\nB: Phân chia các chức năng cần thiết cho hệ thống thành các chương trình và làm rõ quy trình xử lý\nC: Thiết kế các thủ tục chi tiết và viết mã\nD: Thực hiện các bài kiểm tra\nE: Thiết kế cấu trúc bên trong của mỗi chương trình\nF: Xác định các chức năng cần thiết như hệ thống trên cơ sở các đặc tả yêu cầu hệ thống","answer_label":"A , F , B , E , C , D","answer_id":59531},{"id":15344,"question":"Trong quá trình phát triển, hoạt động nào sau đây là hoạt động cần được thực hiện trong thiết kế kiến trúc phần mềm?","answer_label":"Quyết định cách triển khai các yêu cầu phần mềm đã được xác định","answer_id":59543},{"id":15345,"question":"Hoạt động nào sau đây được thực hiện trong quá trình tạo WBS trong quản lý phạm vi dự án?","answer_label":"Phân chia các hoạt động dự án theo thứ bậc thành các phần nhỏ","answer_id":59559},{"id":16171,"question":"Đâu là đặc tính của hệ thống máy khách/máy chủ (client/server)?","answer_label":"Máy chủ cung cấp chức năng như một dịch vụ cho máy khách và thực thi ứng dụng với sự hợp tác của máy khách","answer_id":63709},{"id":16196,"question":"Trong hệ tống máy khách/máy chủ, đâu là ưu điểm phù hợp nhất của việc sử dụng \"store procedures\" có sẵn cho tất cả các máy khách và không cần sao chép với mỗi máy khách?","answer_label":"Có thể giảm thiểu lưu lượng dữ liệu giữa máy khách và máy chủ","answer_id":63814},{"id":16207,"question":"Cấu hình RAID nào sau đây cung cấp dải đĩa ở mức khối (block) thay vì mức byte và dự trữ một đĩa cho thông tin ngang hàng?","answer_label":"RAID4","answer_id":63895},{"id":16230,"question":"Trong hệ thống trực tuyến thời gian thực, các giao dịch (transactions) xảy ra với tần xuất 20 lần/giây. Mỗi giao dịch được hoàn thành sau khi nó thực hiện xử lý CPU 1 lần và xử lý I/O trên đĩa cứng 4 lần. Thời gian xử lý của địa cứng là 40 mili giây cho mỗi I/O và thời gian xử lý của CPU là rất nhỏ. Khi mỗi đĩa cứng được truy cập đồng thời, cần ít nhất bao nhiêu đĩa cứng cho quá trình xử lý giao dịch này?","answer_label":"4","answer_id":64009},{"id":16249,"question":"Trong quản lý bộ nhớ cho các hệ thống thời gian thực sử dụng tài nguyên bộ nhớ có kích thước khác nhau, đâu là đặc điểm của phương thức độ dài cố định (fixed-length medhotd) so với phương thức độ dài thay đổi (variable-length method)?","answer_label":"Hiệu suất bộ nhớ thấp, tốc độ xử lý cấp phát hoặc giải phóng bộ nhớ nhanh và không đổi","answer_id":64101},{"id":16260,"question":"Đâu là phương pháp cải thiện thông lượng (throughput) của toàn bộ hệ thống bằng cách truyền dữ liệu từ bộ nhớ chính sang thiết bị đầu ra (output device) tốc độ thấp thông qua thiết bị lưu trữ phụ tốc độ cao?","answer_label":"Spooling","answer_id":64170},{"id":16268,"question":"Đâu là mô tả thích hợp liên quan đến việc sử dụng ứng dụng trên máy tính có bộ nhớ ảo?","answer_label":"Bộ nhớ chính không đủ gây ra lỗi trong quá trình chạy ứng dụng và làm giảm thông lượng (throughput) của hệ thống","answer_id":64228},{"id":16308,"question":"Một hệ thống máy tính chạy trong môi trường đa lập trình (multi-programming environment) sử dụng thuật toán không ưu tiên. Hai tiến trình A và B được lưu trữ trong hàng đợi và A có mức độ ưu tiên cao hơn B. Bảng dưới đây cho thấy thời gian thực hiện ước tính cho mỗi tiến trình. Ví dụ: A sử dụng CPU, I/O và CPU theo tuần tự trong 30, 60 và 30 mili giây. Thời gian ước tính (mili giây) để hoàn thành cả A và B là bao nhiêu? (CPU và I/O có thể thực thi đồng thời, nhưng I/O của A và B thì không thể)\n","answer_label":"135","answer_id":64429},{"id":16319,"question":"Công cụ nào sau đây được chuẩn bị đặc biệt cho các giai đoạn phát triển phần mềm bao gồm thiết kế chương trình, lập trình và kiểm thử?","answer_label":"Lower CASE tool","answer_id":64485},{"id":16336,"question":"Đâu là bộ xử lý ngôn ngữ có thể dùng để tạo ra chương trình phù hợp với mục tiêu xử lý, dựa trên các điều kiện cần thiết, ví dụ như input, process và output, được chỉ định bởi các tham số?","answer_label":"Generator","answer_id":64574},{"id":16345,"question":"Đâu là mạch logic thích hợp với hai đầu vào (input) và một đầu ra (output) trong đó X chỉ bằng 0 khi hai đầu vào A và B đều là 1s?\n","answer_label":"Mạch NAND","answer_id":64634},{"id":16360,"question":"Trên mạch chiếu sáng LED 7 đoạn như minh họa bên dưới, khi 6D ở hệ thập lục phân được ghi ra cổng đầu ra, giá trị nào sau đây sẽ được hiển thị? Ở đây, P7 là MSB-Most Significant Bit và P0 là LSB-Least Significant Bit. Khi 1 được ghi vào cổng, đoạn LED tương ứng sẽ được bất.\n","answer_label":"c","answer_id":64740},{"id":16384,"question":"Đâu là giải thích phù hợp nhất về bộ nhớ flash?","answer_label":"Dx liệu được ghi hoặc xóa bằng điện (electrically) và xóa tất cả cùng một lúc hoặc xóa theo khối","answer_id":64854},{"id":16392,"question":"Chế độ địa chỉ nào sau đây tham chiếu đến dữ liệu trong bộ nhớ chính như ảnh minh họa bên dưới?\n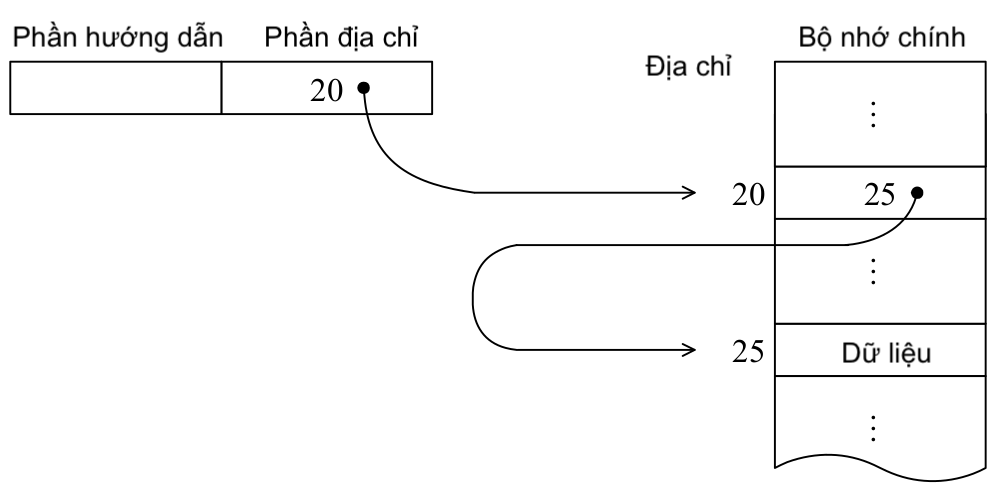","answer_label":"Dẫn địa chỉ gián tiếp (Indirect addressing)","answer_id":64895},{"id":16404,"question":"Khi một bộ nhớ 1 megabute được kết nối với MPU như hình bên dưới, số lượng đường tín hiệu tối thiểu (biểu diễn là n) mà các bus địa chỉ yêu cầu là bao nhiêu? Ở đây, bộ nhớ được truy cập theo đơn vị byte, 1 megabyte = 1024 kilobyte, 1 kilobyte = 1024 byte.\n","answer_label":"20","answer_id":64950},{"id":16433,"question":"Đâu là lời giải thích phù hợp về USB 3.0?","answer_label":"Nó sử dụng giao diện nối tiếp có chế độ truyền dữ liệu 5 Gbps gọi là siêu tốc độ.","answer_id":65110},{"id":16453,"question":"Đâu là mô tả phù hợp nhất về tác dụng của bộ nhớ đệm (cache)?","answer_label":"Bằng cách đọc dữ liệu từ bộ nhớ chính và lưu vào bộ nhớ đệm, khi CPU đọc lại cùng một dữ liệu thì tốc độ thực thi sẽ cao hơn","answer_id":65231},{"id":16493,"question":"Đâu là lời giải thích phù hợp về benchmark test?","answer_label":"Nó thực thi một chương trình chuẩn được chọn phù hợp với mục đích sử dụng và đo lường hiệu suất xử lý của hệ thống.","answer_id":65429},{"id":16522,"question":"Theo như hình bên dưới, một (1) máy chủ , ba (3) máy khách và hai (2) máy in được kết nối qua mạng LAN. Hệ thống này in dữ liệu nằm trên máy chủ theo hướng dẫn từ máy khách. Khi mức độ sẵn sàng của mỗi thiết bị như trong bảng dưới đây, biểu thưc nào sau đây thể hiện mức độ sẵn sàng của hệ thống? Ở đây, hệ thống được coi là khả dụng khi máy chủ, 1/3 máy khách và 1/2 máy in đang chạy.\n","answer_label":"a(1-(1-b)³)(1-(1-c)²)","answer_id":65605},{"id":16561,"question":"Theo như hình bên dưới, có một tập hợp quy trình, với độ dài của thời gian CPU-burst được tính bằng mili giây và các quy trình đến theo thứ tự P1, P2, P3, P4 và P5 với thời gian đến của tất cả các quy trình là t = 0.\n\n\nThời gian quay vòng trung bình của 5 quy trình từ P1 đến P5 là bao nhiêu với thuật toán FCFS (first-come first-served)?","answer_label":"25","answer_id":65774},{"id":16580,"question":"Khi nào thì method lập lịch dựa trên mức độ ưu tiên (priority-based preemptive scheduling) được sử dụng trong hệ điều hành nhúng thời gian thực (embedded real-time operating system)?","answer_label":"Nó được sử dụng khi các nhiệm vụ được xử lý theo mức độ quan trọng và khẩn cấp.","answer_id":65870},{"id":16604,"question":"Trong bộ nhớ ảo của hệ thống phân trang, đâu là nguyên nhân làm tăng số lần lỗi trang?","answer_label":"Tăng quyền truy cập vào một trang không tồn tại trong bộ nhớ chính","answer_id":65979},{"id":16879,"question":"Đâu là tiêu chí để thay thế một trang trong thuật toán Least Recently Used (LRU)?","answer_label":"Lần tham chiếu cuối cùng","answer_id":67075},{"id":16895,"question":"Cho một mạch logic như hình bên dưới. Khi nhập giá trị đầu vào A = 1, B = 0, C = 1, giá trị của E và Y lần lượt là?\n","answer_label":"E = 1, Y = 1","answer_id":67151},{"id":16925,"question":"Bằng cách sử dụng một cảm biến phát hiện thay đổi hình dạng, tình trạng của cơ sở hạ tầng mà đường cao tốc trên cao có thể được theo dõi và bảo trì. Đâu là bộ cảm biến được sử dụng cho mục đích này?","answer_label":"Strain gage","answer_id":67299},{"id":16943,"question":"Trong mạch chiếu sáng của đèn LED loại chung anode (anode-common type) có 7 đoạn, khi 92 trong hệ thập lục phân được ghi ra cổng output, giá trị nào sẽ được hiển thị? ở đay P7 là MSB-most significant bit, P0 là LSB-least significant bit và đèn LED sáng khi đầu ra cổng là 0.\n","answer_label":"c","answer_id":67428},{"id":16969,"question":"Hiện tại, số lượng khách hàng là 8000 với tỷ lệ tăng hàng năm là 20%. Bằng cách chỉ định một mã độ dài cố định sử dụng 26 chữ cái viết hoa (A - Z) cho mỗi khách ahngf, độ dài mã tối thiểu cần thiết để đáp ứng tất cả các khách hàng trong 3 năm tới là bao nhiêu?","answer_label":"3","answer_id":67555},{"id":16994,"question":"Một tín hiệu âm thanh được lấy mẫu 11000 lần mỗi giây trong khi mỗi mẫu được ghi lại dưới dạng dữ liệu 8 bit. Khi sử dụng bộ nhớ flash dung lượng 512 × 10⁶byte, số phút tối đa để ghi dữ liệu đó là bao nhiêu?","answer_label":"775","answer_id":67694},{"id":17006,"question":"Đối với quy trình chuyển đổi đa chương trình của các quy trình được hiển thị như hình bên dưới, quy trình nào sau đây là sự kết hợp của xử lý hệ điều hành cho A thông qua C?\n","answer_label":"c","answer_id":67750},{"id":17021,"question":"Hai thư mục A, B được quản lý theo cấu trúc như hình bên dưới. Trường hợp nào sau đây mà thư mục hiện tại được di chuyển để “\\ B \\ A \\ B” là thư mục hiện tại? Ở đây, phương thức chỉ định thư mục được giải thích phía dưới và → cho biết thứ tự di chuyển.\n\n[Phương thức chỉ định thư mục]\n(1) Một thư mục được tham chiếu là “tên thư mục \\ ··· \\ tên thư mục”, trong đó các thư mục trên đường dẫn được căn chỉnh và phân cách bằng “\\” theo thứ tự, theo sau là “\\” và tên thư mục.\n(2) Thư mục hiện tại được biểu thị bằng “.” (một dấu chấm).\n(3) Thư mục cấp một (1) thứ bậc ở trên được biểu thị bằng “..” (hai dấu chấm).\n(4) Khi một tham chiếu bắt đầu bằng “\\”, giả sử rằng thư mục gốc bị bỏ qua ở vị trí ngoài cùng bên trái của tham chiếu. \n(5) Khi một tham chiếu không bắt đầu bằng “\\”, “.” Hoặc “..”, thì giả định rằng “. \\” Bị bỏ qua ở vị trí ngoài cùng bên trái của tham chiếu.\n","answer_label":"\\A → ..\\B → .\\A\\B","answer_id":67824},{"id":17078,"question":"Cần 36 ngày để Mr. A hoàn thành một công việc nhất định, và 18 ngày để Mr. B hoàn thành công việc tương tự. Khi Mr.A và Mr. B cùng thực hiện công việc đó thì mất bao lâu? Biết rằng, công việc có thể chia ra thực hiện song song, và trong khi hợp tác, cả A và B đều đạt được hiệu suất làm việc trung bình là 90%.","answer_label":"14","answer_id":68062},{"id":17092,"question":"Số lượng chương trình tạo ra hệ thống và số ngày nhận công cần thiết để hoàn thành mỗi chương trình được thể hiện trong bảng dưới đây, số lượng nhân viên tối thiểu cần thiết để phát triển hệ thống trong 95 ngày là bao nhiều? Biết rằng ngoài việc code, các hoạt động thiết kế và kiêm thử hệ thống yêu cầu số ngày công gấp 8 lần so với việc code.\n","answer_label":"9","answer_id":68123},{"id":17116,"question":"Theo như ISO / IEC 20000-1: 2011 (Công nghệ thông tin - Quản lý dịch vụ - Phần 1: Yêu cầu hệ thống quản lý dịch vụ), điều nào sau đây đề cập đến sự gián đoạn không có kế hoạch đối với một dịch vụ, giảm chất lượng của dịch vụ hoặc sự kiện chưa ảnh hưởng đến dịch vụ cho khách hàng?","answer_label":"Sự cố (Incident)","answer_id":68220},{"id":17125,"question":"Một dịch vụ IT được cung cấp theo các điều kiện được mô tả dưới đây. Để đáp ứng SLA, thời gian ngừng hoạt động cho phép tối đa phải ít hơn bao nhiêu giờ trong giờ dịch vụ ( service hours) mỗi tháng? Ở đây, số ngày làm việc trong một tháng là 30.\n\n[Điều kiện của SLA] \n- Service hours: 7 giờ sáng đến 9 giờ tối (tức là 14 giờ mỗi ngày) vào mỗi ngày làm việc \n- Tính khả dụng: 99,5% trở lên","answer_label":"2","answer_id":68269},{"id":17138,"question":"Công ty A cấp một ID ở định đạng như bên dưới khi đăng ký thành viên. Bảng dưới đây cho thấy sự chuyển đổi số lượng ID được cấp vào cuối mỗi năm tài chính. Khi xu hướng này được giả định sẽ tiếp tục trong tương lai, thì năm tài chính nào Công ty A dự kiến sẽ hết ID ở định dạng này? Tại đây, ID của các thành viên đã từ chức được quản lý dưới dạng số trống và không được sử dụng lại.\n\n[Định dạng của ID] \nXXNNN (ví dụ: AZ059):\n- X là ký tự chữ cái viết hoa (A đến Z). \n- N là một chữ số số (0 đến 9).\n\n[Sự chuyển đổi số lượng ID tích lũy được cấp vào cuối mỗi năm tài chính]\n","answer_label":"Fiscal year 2013","answer_id":68328},{"id":17147,"question":"Khi một cuộc điều trần được tiến hành trong quá trình đánh giá hệ thống, hành động thích hợp mà người đánh giá hệ thống phải thực hiện là gì?","answer_label":"Khi phát hiện ra vấn đề do kết quả của phiên điều trần, dữ liệu dự phòng sẽ được thu thập và tiến hành điều tra tại chỗ.","answer_id":68384},{"id":17156,"question":"Giải thích nào là chính xác về giấy tờ công việc kiểm toán (audit work papers)?","answer_label":"Đây là hồ sơ thực hiện thủ tục kiểm toán do kiểm toán viên thực hiện và nó là cơ sở cho ý kiến kiểm toán","answer_id":68451},{"id":17179,"question":"Khi bộ phận phát triển và bộ phận vận hành của một hệ thống được tổ chức riêng biệt, để tiến hành thuận lợi và hiệu quả việc thiết kế và phát triển một dịch vụ mới cần phát triển hệ thống thì phương pháp cần thực hiện là gì?","answer_label":"Bộ phận vận hành cũng tham gia tích cực vào việc trích xuất các yêu cầu liên quan đến hoạt động của hệ thống","answer_id":68564},{"id":17192,"question":"Trong quản lý dịch vụ IT, tổ chức chức năng nào sau đây cung cấp một điểm liên hệ duy nhất và cố gắng khôi phục nhanh chóng các hoạt động dịch vụ bình thường cho người dùng?","answer_label":"Service desk","answer_id":68625},{"id":17207,"question":"Đâu là phương tiện hữu hiệu để bảo vệ hệ thống thông tin khỏi thiệt hại do quá điện áp xảy ra do sét đánh?","answer_label":"Kết nối cáp giao tiếp và máy tính thông qua thiết bị chống sét lan truyền (SPD)","answer_id":68701},{"id":17213,"question":"Trong số các trạng thái được tìm thấy thông qua kiểm toán hoạt động quản lý vận hành hệ thống, điều nào sau đây phải được mô tả trong báo cáo kiểm toán như một phát hiện?","answer_label":"Người điều hành quyết định kế hoạch hoạt động hàng ngày và tự mình phê duyệt.","answer_id":68746},{"id":17226,"question":"Mô tả nào sau đây là phù hợp nhất liên quan đến cuộc phỏng vấn do một người đánh giá hệ thống thực hiện?","answer_label":"Người đánh giá của hệ thống cố gắng thu thập các tài liệu và hồ sơ hỗ trợ thông tin thu được từ bộ phận được kiểm toán trong cuộc phỏng vấn.","answer_id":68832}]
/* eslint-disable no-var */
// Example URL: https://learn.viblo.asia/en/courses/fundamental-information-technology-engineer-examination-fe-VolejRejNm/exams/15/en/attempt?question=10
var lang = document.location.href.split("/")[8];
if (lang !== "en" && lang !== "vi") {
lang = document.location.href.split("/")[7]; // in case language locale is omitted
if (lang !== "en" && lang !== "vi") {
console.error("có lỗi gì đó rồi đại ca")
}
}
var timeout = 1000;
var shouldAutoClick = true;
var fetchQuestions = async () => {
try {
const data = await fetch(
`${
lang === "en"
? "https://firebasestorage.googleapis.com/v0/b/get-started-b0608.appspot.com/o/fe-questions-full-en.json?alt=media&token=cc8f0281-bf06-4a41-892c-4bfdf63c1597"
: "https://firebasestorage.googleapis.com/v0/b/get-started-b0608.appspot.com/o/fe-questions-full-vi.json?alt=media&token=cc8f0281-bf06-4a41-892c-4bfdf63c1597"
}`,
{
headers: {
accept: "application/json, text/plain, */*",
},
method: "GET",
}
).then(async (r) => {
if (r.ok) {
return await r.json();
}
return lang === "en" ? en : vi;
});
return data;
} catch (err) {
console.log(err.message);
console.log("Đừng lo đại ca, em có backup")
return lang === "en" ? en : vi;
}
};
async function run() {
console.log("bat dau vui nay :D");
const allQuestions = [];
const fetchRes = await fetchQuestions();
allQuestions.push(...fetchRes);
const questionNumberList =
document.querySelector("div.question-list").children;
var fromComponentQuestions = [];
var xTag = document.querySelector("div.flex.test-view.w-full");
var reactInternalInstanceKey = Object.keys(xTag).find((key) =>
key.startsWith("__reactInternalInstance$")
);
xTag[reactInternalInstanceKey].return.memoizedProps.questions.forEach(
(ques) => {
const obj = Object.fromEntries(Array.from(ques));
const choices = [];
obj.choices.forEach((c) =>
choices.push(Object.fromEntries(Array.from(c)))
);
obj.choices = choices;
fromComponentQuestions.push(obj);
}
);
if (questionNumberList.length !== fromComponentQuestions.length) {
console.log(
"Questions don't match: ",
"provided: ",
questionNumberList.length,
", ",
"fetched: ",
fromComponentQuestions.length
);
return;
}
var wait = () => {
return new Promise((resolve, reject) => {
setTimeout(() => {
resolve();
}, timeout);
});
};
for (const questionNumber of questionNumberList) {
// questionNumber.querySelector("a").click();
const oldHandler = questionNumber.querySelector("a").onclick;
questionNumber.querySelector("a").onclick = null;
questionNumber.querySelector("a").addEventListener("click", (t) => {
const providedAnswers = document.querySelector(
"div.question-answers div.ant-radio-group-outline"
).children;
const questionHeading = document.querySelector("div.question-heading");
const substr = questionHeading.innerText.split(" ");
console.log(substr[substr.length - 1] - 1);
const question =
fromComponentQuestions[Number(substr[substr.length - 1]) - 1];
const questionID = question.id;
const ans = allQuestions.find((q) => String(q.id) === String(questionID));
if (!ans) {
console.log(
`There's no answer for question ${substr[substr.length - 1]}`
);
} else {
const ans_order = question.choices.findIndex(
(item) => item.id === ans.answer_id
);
console.log(
`Answer for question ${substr[substr.length - 1]}: ${ans_order}`
);
// if (timeout) {
// await wait();
// }
if (shouldAutoClick) {
providedAnswers[ans_order].querySelector("input").click();
}
}
});
questionNumber.querySelector("a").addEventListener("click", oldHandler);
}
if (!shouldAutoClick) {
for (const questionNumber of questionNumberList) {
questionNumber
.querySelector("a div.question-item")
.classList.remove("not-answer-bg");
}
}
}
// var cusor = document.createElement("div");
// cusor.style = "position: fixed; top: 0; right: 0; z-index:9999";
// cusor.innerHTML = `<img id="cursor" src="https://media.geeksforgeeks.org/wp-content/uploads/20200319212118/cursor2.png" width="15" height="20" />`;
// document.body.appendChild(cusor);
var div = document.createElement("div");
div.style =
"position: fixed; top: 0; left: 0; z-index:9999; min-width:100px; min-height:100px";
div.onclick = () => {
run();
};
document.body.appendChild(div);